One of the biggest causes of concern to IT departments across the globe is shadow IT. Uncontained, it can cause duplication, unnecessary costs, and compliance issues. To manage and mitigate risks, IT managers need to understand what shadow IT is, its risks, and how organizations can proactively address them.
In this regard, IT Asset Management solutions incorporate capabilities that help organizations implement protection measures and build a culture of cybersecurity. Here we will explore what shadow IT is, how to develop a policy to manage it, and how InvGate Asset Management can make a significant difference when doing so.
Ready? Let's get started.

What is shadow IT?
So, let's start with the basics - what exactly is shadow IT? Let's go straight to the experts. Garner defines it as follows: “Shadow IT refers to IT devices, software, and services outside the ownership or control of IT.”
In other words, shadow IT refers to systems, software, applications, SaaS services, hardware, or mobile devices used within an organization without the IT department's explicit approval, oversight, support, or knowledge.
Shadow IT solutions are often adopted and implemented by colleagues or departments to address specific needs or solve immediate problems without going through formal IT service requests, procurement, and approval processes to save time or process blockers.
Initially, it started focusing on hardware assets, but it has evolved to include SaaS applications (aka SaaS sprawl). The ease and convenience of SaaS solutions make it easy for individuals to spin up instances of SaaS services, leading to uncontrolled usage and risks to compliance, data protection, and financial needs.
Five examples of shadow IT
What does this look like in real life? Here are some shadow IT examples:
- Using services like Dropbox, Google Drive, or USB flash drives to share data instead of using the methods approved by your organization.
- The use of personal mobile devices (Bring Your Own Device policy) to carry out work-related tasks without the support of the IT department.
- Cloud services, including collaboration tools, Project Management software, and instant messaging solutions.
- Colleagues downloading and installing software applications on their work computers without IT's knowledge can lead to compatibility issues and security risks.
- Using personal email accounts or third-party email services for work-related communication instead of the corporate email system.
Benefits and risks associated with shadow IT
As we mentioned above, shadow IT isn't all bad - it has some associated benefits . Some of them include:
- Flexibility and agility: Shadow IT allows colleagues to quickly implement services that will solve problems or fulfill a specific business need without going through a lengthy procurement process. This can lead to greater agility in adapting to changing business needs.
- Innovation: Colleagues can use shadow IT to experiment with new technologies to improve processes and functional outcomes. This can lead to innovation and more efficient working practices.
However, this shouldn’t outweigh the significant dangers associated with it. The main risks of shadow IT are:
- Security risks: Nonstandard services may not adhere to the organization's security policies and standards, potentially exposing the organization to external threats or cyber attacks.
- Increased threat landscape: With every instance of Shadow IT, the organization's attack surface is expanded. Since shadow IT services are not visible to the IT or information security teams, they are not protected by the corporate security measures in place.
- Compliance issues: Shadow IT can lead to non-compliance with industry regulations and internal policies, which may result in legal, financial, and reputational damage.
- Lack of control: The IT department will have limited visibility, and control will overshadow IT resources, making it difficult to manage and support these systems effectively.
- IT support challenges: If IT support teams aren't aware of a service, they won't be able to support it effectively as they won't have the appropriate knowledge, documentation, or escalation processes.
- Data fragmentation: Information is spread across various platforms and services, making managing and accessing data consistently challenging.
- Inefficiencies and duplication: Because shadow IT isn't controlled centrally, there is the potential for duplication and rework, as colleagues could buy similar but different services.
Managing shadow IT with InvGate Asset Management
Shadow IT is unlikely going to go away, so it's essential to have a robust plan in place to address it. The trick here lies in finding those devices or systems that have got lost in the shuffle and incorporating them into your area of domain.
For this, InvGate Asset Management combines agent and agentless methods to automate the IT asset inventory process. The agent works by monitoring and reporting on all the devices it has been installed on, including valuable data about their software licenses and applications. This way, if somebody is running an unauthorized system it will be brought up in the report for you to take action on.
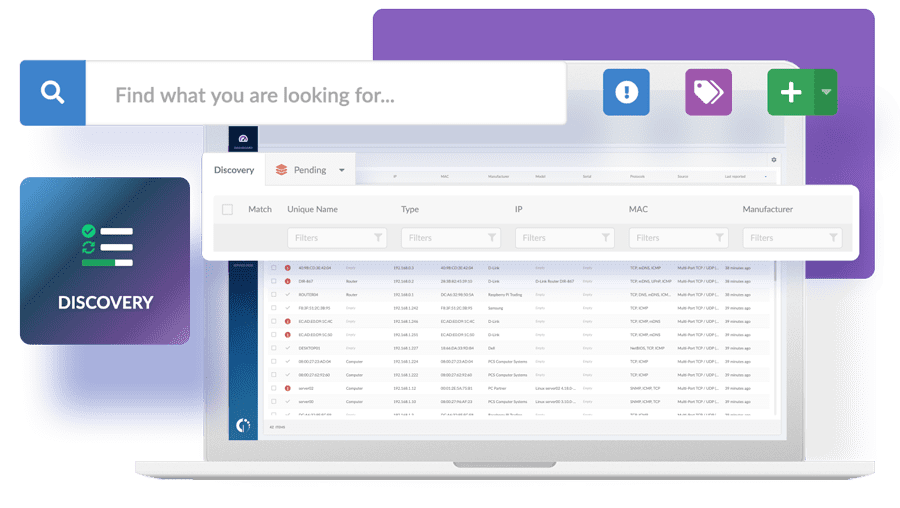
To complement this, InvGate Asset Management’s Discovery feature periodically scans your whole IT environment to find and audit on the devices found in your network. It can detect network-connected devices on which the agent does or can not run, such as printers, switches, routers, and IP phones. Once they have been detected, you can make the choice to incorporate them into your inventory or not.
By combining both methods, you can tackle the different types of components that can fall under the risks of shadow IT. However, this isn’t all a robust ITAM strategy can do to reduce security risks; book a quick call with our experts to see how InvGate Asset Management can further enhance your organization’s protection measures.
Developing a shadow IT policy: 12 best practices
Creating a shadow IT policy is essential for managing and mitigating the risks associated with nonstandard technology usage within your organization.
Here are steps to help you make it effective:
- Define the purpose and scope - The first thing you should do is create an introduction that sets out what the policy is for and what it covers. Explain clearly that the goal is to manage and control shadow IT services.
- Include links to other supporting policies - It’s important to make the IT security policy and acceptable usage policy available, if appropriate.
- Identify the main stakeholders - These will be involved in creating, enforcing, and communicating the policy. Incorporate IT, HR, Procurement, Legal, and Governance, Risk and Compliance business unit colleagues.
- Set out roles and responsibilities - All team members must know what they are responsible for and what is expected from them. Create colleague awareness by describing the training and awareness programs in place to communicate the policy.
- Define how to access IT support - It’s also important for your whole organization to be aware of the correct mechanisms to request new services appropriately. For instance, if you have a help desk solution, make sure everybody is aware of the guidelines to use it and implement measures to encourage user adoption.
- Define unauthorized assets and technologies - Apart from this, it should be clear to all colleagues what is and isn't acceptable when downloading and installing new IT software and hardware.
- Have a provision from Bring Your Own Device - If your organization supports BYOD, include guidelines and policies for using personal devices for work-related tasks. Specify security measures, acceptable use, and data protection requirements for personal devices.
- Set out information security guidelines - Specify how data and information should be handled, stored, and transmitted when it's involved in nonstandard IT services.
- Define IT monitoring methods - Define how the organization will monitor network activity and usage to detect unauthorized software and hardware instances. As we saw above, an ITAM solution is the best way to streamline this process.
- Build in access control measures - Lockdown corporate devices to restrict the installation and usage of unauthorized software.
- Conduct regular audits and assessments of your organization's IT environment to identify and address instances of shadow IT. This may involve checking for unauthorized software installations, cloud service usage, or unapproved devices.
- Make help available - Have a section for colleagues to access information or to go to if they have questions about shadow IT. You can write a knowledge base article on the topic and incorporate it into your help desk.
In summary
Shadow IT is any technology outside the ownership or control of IT support. Although it can bring greater agility and faster access to new technology, it also encompasses significant dangers such as security risks, compliance issues, lack of control, and a more difficult support provision.
To address this, designing a clear policy will set out the do’s and don'ts so everyone knows what is expected of them. However, spotting those shadowed devices manually can be very difficult, so incorporating a tool designed to automate the monitoring process can be a real changer.
To see how all of this works in practice, you can book a free trial and navigate through InvGate Asset Management in your own time. No strings attached!
Frequently Asked Questions
Is shadow IT bad?
It depends. Shadow IT isn't all inherently dangerous, but certain features like file sharing can result in accidentally sharing sensitive data, nonstandard devices are more complicated to support, and nonstandard applications could cause security issues, so care must be taken to protect your organization and its data.
What are the most common shadow IT apps?
There are many shadow IT apps, but some of the most commonly used ones are Dropbox, Google Suite, WhatsApp, and Gmail.
How do you tackle shadow IT?
In short, you have to make sure your ITAM strategy is robust and that it is easy for the business to communicate with IT. For instance, ensure all available services are advertised via the service catalog and that your help desk makes it quick and easy to request new products and services via the Request Management practice.
What are the statistics for shadow IT?
It's increasing. A recent study from Gartner found that by 2027, 75% of employees will acquire, modify, or create technology outside IT's visibility – up from 41% in 2022.
How does shadow IT relate to cloud computing?
Cloud computing has contributed to the increase in Shadow IT because of the SaaS spiral. Because SaaS products are so easy to obtain and use, it's become easy for colleagues to buy new ones without going to the service desk and IT procurement practices.
How to avoid shadow IT?
Have an open and honest relationship with the rest of the business. IT should be an enabler, so if your people are resorting to shadow IT to get the job done, then you are doing IT wrong!















