IT asset discovery is a process organizations use to identify, catalog, and document all their IT assets. By keeping an accurate inventory of every technology resource that adds value to the business, teams can ensure visibility, control, and compliance.
As cloud adoption and remote work expand, IT asset discovery has become a core IT Asset Management (ITAM) practice. It’s no longer just about financial tracking, but also about maintaining cybersecurity, reducing blind spots, and meeting regulatory requirements. This is why discovery must be continuous rather than a one-time activity: dynamic environments require a dynamic approach.
In this article, we’ll explore key approaches and best practices for achieving continuous IT asset discovery.
Updated: February 2026
What is IT asset discovery?
IT asset discovery is the process organizations use to identify, classify, and document their technology assets within a centralized system. This includes hardware, software, SaaS applications, cloud resources, and any other IT asset that delivers value to the business.
The primary goal of IT asset discovery is to provide complete visibility into the IT environment while keeping asset data accurate as the environment evolves. Because modern infrastructures constantly change, discovery is not just about knowing what exists, but about ensuring those changes are continuously reflected.
There are multiple ways to approach IT asset discovery, and the right method always depends on the organization’s technical landscape, operational needs, and available resources. In the following sections, we’ll explore the most common approaches and how they work together.
Agent vs. agentless discovery: pros and cons
There are two main approaches to IT asset discovery: agent-based and agentless. Both aim to provide visibility across your organization’s IT environment, but they do it in different ways.
While agent-based discovery offers deeper, continuous insight into devices and services, agentless discovery enables fast coverage without installation requirements. In most cases, organizations combine both methods to achieve a balanced, accurate view of their assets.
Agent-based discovery
Agent-based discovery relies on lightweight software agents installed on each device. These agents collect detailed data about hardware, software, configurations, and running services, then send it back to the ITAM platform.
Agent-based discovery pros:
- Provides detailed visibility into device status and configuration.
- Works even when devices are off-network (e.g., remote workers).
- Enables proactive management.
Agent-based discovery cons:
- Requires agent deployment and maintenance.
- Some devices may not support agents.
Agent-based discovery is best suited for environments that prioritize data accuracy, ongoing monitoring, and control, such as hybrid workplaces or highly regulated industries.
When agent-based discovery makes the most sense
Agent-based discovery is ideal when organizations need deep, continuously updated asset intelligence rather than simple detection. It becomes especially valuable in environments where devices frequently change state, location, or configuration.
You should typically prioritize agent-based discovery when:
- Remote or hybrid work is common – Devices may operate outside the corporate network for long periods.
- High data accuracy is required – Detailed telemetry, software usage, and configuration tracking are critical.
- Continuous monitoring is a priority – The organization needs real-time change detection, not periodic snapshots.
Agentless discovery
Agentless discovery (also known as network scanning) detects assets across the network without installing software on each device. It uses protocols like SNMP, WMI, SSH, or API calls to collect information remotely.
Agentless discovery pros:
- Offers faster setup and immediate visibility across connected devices.
- Reduces administrative overhead since no agents are required.
- Ideal for networked infrastructure (servers, routers, switches, printers).
Agentless discovery cons:
- Provides less granular data compared to agent-based methods.
- Only works for devices reachable through the network.
- May require credential management to access certain systems.
Agentless discovery is often chosen for organizations that need broad visibility with minimal setup, especially in stable, on-premises environments.
When agentless discovery is the right fit
Agentless discovery is most effective when speed of deployment and broad network visibility are more important than highly granular endpoint data. It works well in environments with stable, well-defined network boundaries.
Agentless discovery is usually a strong choice when:
- Rapid visibility is needed – Teams want immediate insight without coordinating agent rollouts.
- The infrastructure is mostly on-network – Assets are consistently connected and reachable.
- Administrative simplicity is preferred – Minimizing endpoint management overhead is a key concern.
Hybrid approach by use case
In practice, most organizations adopt a hybrid discovery strategy. They use agent-based discovery for critical endpoints and mobile assets, while agentless scanning covers servers, network devices, and other connected equipment.
This combined approach offers the best of both worlds: continuous visibility, minimal blind spots, and flexibility to adapt to different infrastructure types.
Common scenarios where a hybrid approach works particularly well include:
- Hybrid workforce environments – Laptops and user devices rely on agents for continuous tracking, while office network infrastructure is discovered through agentless scanning.
- Controlled data center policies – Servers may follow stricter deployment rules where agents are limited or standardized, making agentless methods preferable depending on governance or security policies.
- Distributed network ecosystems – Network devices, printers, and appliances are efficiently detected via scanning, while business-critical endpoints require deeper, agent-level telemetry.
Continuous asset discovery vs. periodic scans
IT asset discovery can run continuously or through periodic scans. The difference lies in how often and automatically assets are updated.
Continuous discovery works in real time, using agents, integrations, and update triggers - automatic events that refresh asset data when something changes, such as a new device joining the network or a software update being installed.
For discovery to be truly continuous, organizations typically need:
- Frequent update mechanisms – Asset data should refresh based on events or short reporting cycles rather than long scanning intervals.
- Multiple data sources – Agents, network scanning, and cloud or SaaS integrations work together to reduce visibility gaps.
- Change detection and alerts – The system should recognize and surface meaningful deviations, not just collect raw data.
- Asset reconciliation logic – Discovery must prevent duplicates and correctly merge or update existing asset records.
Periodic scans happen at fixed intervals, like daily or weekly. They’re easier to manage but may miss short-term changes in fast-moving environments.
Most organizations combine both, using continuous discovery for real-time accuracy and periodic scans for scheduled validation.
Hardware and software inventory: Standardization and normalization
Once assets are discovered, the next step is ensuring the data is consistent and reliable. This is where data standardization and data normalization become essential. Standardization defines how asset data should be structured, while normalization applies those rules to eliminate variations and inconsistencies.
In practice, normalization unifies equivalent values. For example, “Dell Inc.”, “DELL”, and “Dell Technologies” are consolidated under a single manufacturer name, preventing fragmented or misleading records.
Many ITAM frameworks also reference reconciliation, sometimes as a separate step and sometimes as part of normalization. While normalization focuses on data consistency, reconciliation resolves asset identity, determining whether multiple records represent the same asset and preventing duplicates.
Modern ITAM platforms typically automate these processes using catalogs, matching rules, and correlation logic, transforming raw discovery data into a trustworthy inventory.
CMDB discovery and inventory integration
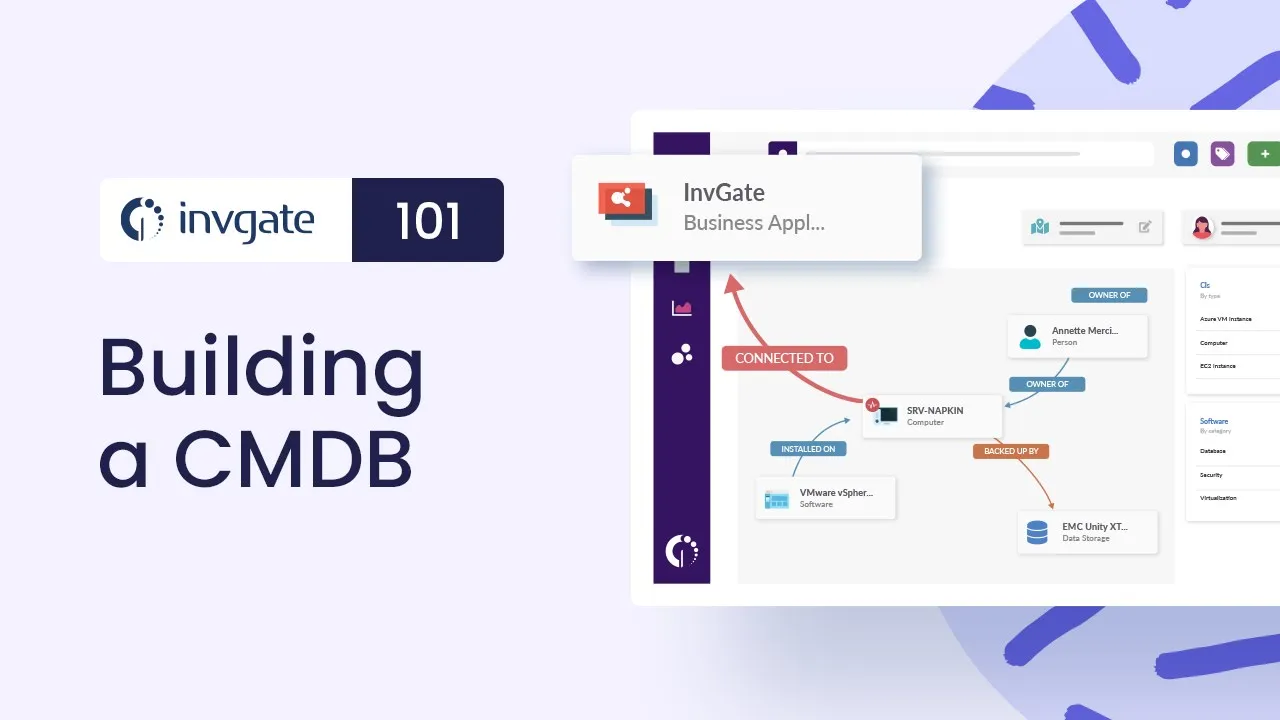
Integrating IT asset discovery and inventory data with a Configuration Management Database (CMDB) is an important step for organizations seeking greater visibility of their IT environment or tighter control over service dependencies and changes.
This connection creates a reliable source of truth that links assets to the services they support, improving impact analysis, incident resolution, and overall data consistency.
In practice, this relationship often follows a simple model: a hardware or software asset supports an application, which in turn enables a business service. For example, a server hosts a CRM application, and that application supports the sales service.
A practical starting point for CMDB integration is focusing on business-critical services. Mapping dependencies for high-impact services first helps organizations deliver immediate operational value while progressively expanding CMDB coverage.
SaaS discovery and shadow IT: Close the gaps
SaaS discovery is a key part of IT asset discovery that focuses on identifying all cloud-based applications used within an organization (both approved and unapproved). This practice helps uncover and control shadow IT, reducing security and compliance risks.
Modern solutions use Identity Providers (IdP), Single Sign-On (SSO) integrations, Cloud Access Security Brokers (CASB), and API connections to SaaS platforms to detect usage and collect metadata. Some organizations also rely on spend analysis or internal surveys to reveal hidden subscriptions and user activity.
By combining these methods, IT teams can close visibility gaps, protect sensitive data, and optimize SaaS spending - ensuring every cloud application is accounted for and securely managed.
IT asset inventory metrics that prove value
Tracking the right metrics helps demonstrate the impact of your IT asset discovery and inventory efforts. These indicators show how complete, current, and reliable your asset data really is.
- Coverage – Measures how much of your environment is actually discovered and tracked. High coverage means fewer blind spots and stronger visibility across all assets.
- Freshness – Reflects how up to date your asset information is. Monitoring how frequently data is refreshed helps ensure your inventory remains accurate over time.
- Accuracy – Evaluates the quality and consistency of your records by comparing discovery data with audits or reconciled sources. Reliable data supports better financial, security, and compliance decisions.
- Mean Time to Inventory (MTTI) – Tracks the average time between when a new asset is introduced and when it appears in the inventory. A lower MTTI means faster discovery and tighter control.
- Change detection rate – Indicates the percentage of changes automatically detected by discovery before manual intervention. It’s a great way to assess how responsive and automated your system really is.
Together, these metrics highlight the value of maintaining a complete, accurate, and continuously updated asset inventory.
Common pitfalls in IT asset discovery (and how to avoid them)
Even with the right tools, IT asset discovery can fall short if the process isn’t consistent or well managed. Here are some common mistakes organizations make and how to avoid them.
- Treating discovery as a one-time snapshot – Running occasional scans quickly leads to outdated data and blind spots, so discovery should be established as a continuous operational process rather than a periodic task.
- Lack of ownership – Without clear accountability, discovery data often becomes fragmented or unreliable, which makes it essential to define explicit ownership through governance or inventory policies.
- Missing normalization – Raw discovery data is frequently inconsistent or duplicated, so ITAM platforms should enforce automated normalization to maintain data quality and asset identity.
- Ignoring SaaS and remote assets – Discovery strategies that focus only on on-premise devices create major visibility gaps, requiring organizations to expand their scope to include cloud, SaaS, and off-network assets.
- Poor integration with other systems – Discovery loses much of its value when data remains siloed, making integrations with ITAM, CMDB, and security tools critical for maintaining consistency across systems.
Automate IT asset discovery with InvGate Asset Management

InvGate Asset Management is an ITAM software that helps you build a unified inventory of all your organization’s technology resources - including hardware, software, cloud assets, and any other components that support your operations. It can even extend beyond IT, allowing you to track non-IT assets for complete visibility.
You can combine different discovery methods to keep your inventory accurate and up to date. The InvGate Asset Management Agent collects detailed information directly from devices, while the InvGate Discovery features identify connected assets across your network, ensuring nothing goes unnoticed.
A practical approach to implementing automated discovery with InvGate Asset Management typically follows a simple sequence:
- Define the discovery scope – Determine which assets, networks, and environments should be covered to avoid partial or misleading visibility.
- Execute discovery and enrich assets – Deploy agents and discovery mechanisms while capturing the richest possible asset data.
- Consolidate and normalize the inventory – Use built-in normalization to eliminate inconsistencies and maintain a clean dataset.
- Monitor and visualize continuously – Create dashboards and reports to sustain inventory accuracy and quickly understand changes.
Ready to see how simple IT asset discovery can be? Start your free 30-day trial of InvGate Asset Management and gain complete visibility of your IT environment.















