The connected world we live in has both transformed our workplaces and raised the cybersecurity challenges. On top of this, remote work and the growing reliance on cloud services and SaaS apps can also make it more difficult for cybersecurity teams to keep track of all the potential threats.
This is why, today more than ever, learning how to reduce IT security risk with IT Asset Management (ITAM) can be a game changer to keep your workplace protected. And the good news is that you can address this with InvGate Asset Management as your single ITAM tool.
So, stay tuned to learn how to do it!

What is the risk of poor Asset Management?
Poor Asset Management can quickly expose your organization to a multiplicity of (rather unnecessary) security risks. On the one hand, you have those associated with the loss of critical assets – either because of misplacement or theft.
These types of risks most likely affect physical devices, and oftentimes cause other associated dangers, such as the loss of intellectual property and money associated with the replacement of equipment. Basically, for these cases, with poor ITAM you don’t have a map of what you own, who owns it, and what the implications of the loss are.
On the other hand, organizations are also exposed to cybersecurity risks. Cyber threats are growing by the dozen – and some industries are more vulnerable than others. Examples of cybersecurity risks include malware, code injection, and ransomware. Whatever the case, your organization might face data loss, extortion, or sniffing.
And how does ITAM relate with this? The answer is pretty simple: with an Asset Management strategy in place, you can monitor your company devices to spot unauthorized hardware and software, outdated software versions, and illegal licenses – all being sources that can open the door to unwanted risks.
7 ways to reduce IT security risk with IT Asset Management
Now that we have gone through the significance of a robust ITAM strategy, let’s explore real-life scenarios in which this practice can help you mitigate company risks.
By implementing these tips and tricks, you can proactively address a range of security risks associated with IT assets. And, luckily, all of these operations can be streamlined on InvGate Asset Management – which will shoulder the load.
1. Keep a unified inventory
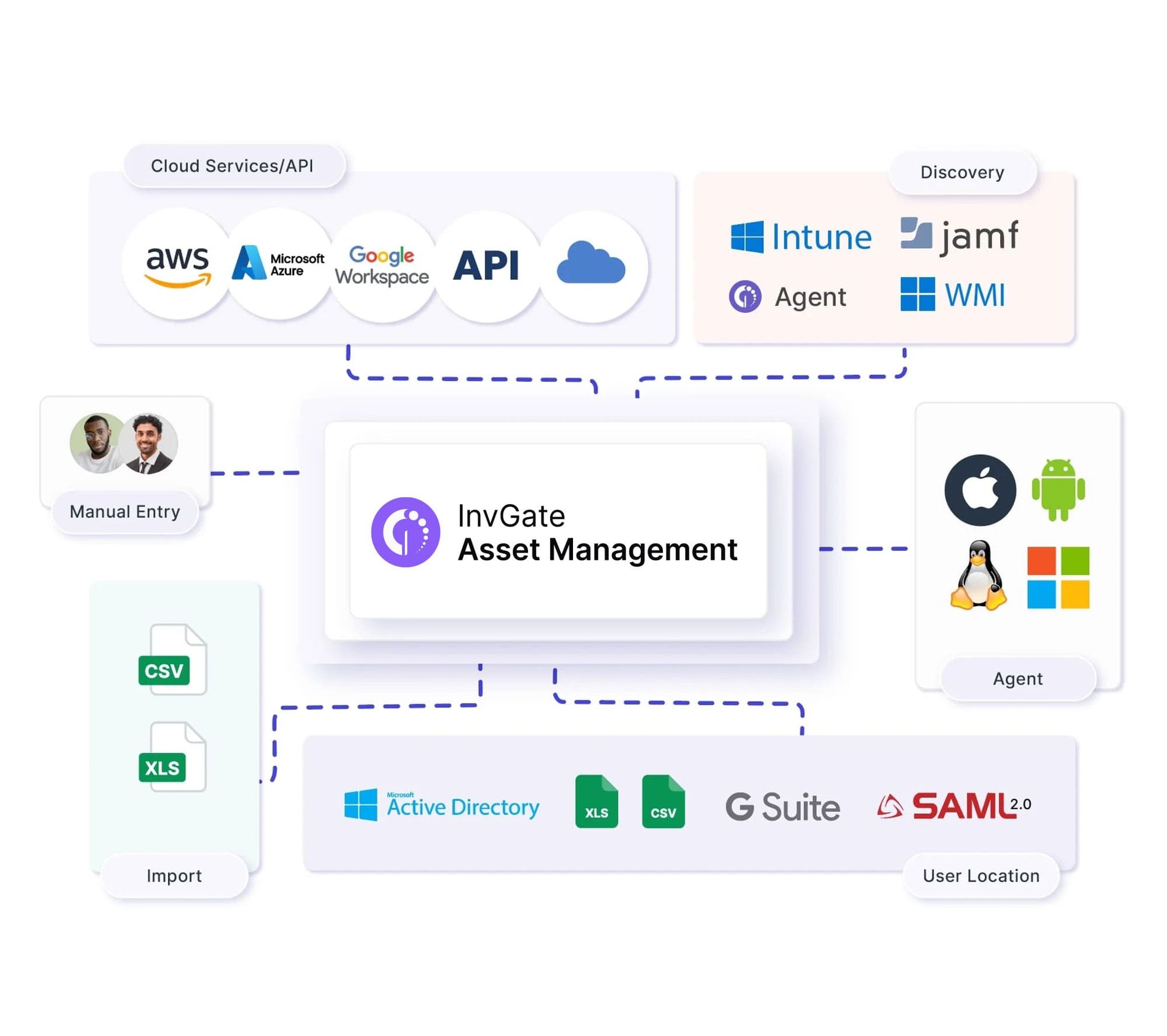
In order to maintain your assets secure, you must have a unified inventory. This doesn’t only include having all your Configuration Items (CIs) on it but also building the relationships between them to understand your IT infrastructure and dependencies.
Once you have your inventory built, you’ll be able to monitor your assets, analyze their risks, and leverage the rest of InvGate Asset Management’s capabilities, which we’ll explore in the next sections.
2. Install an agent in your devices for monitoring
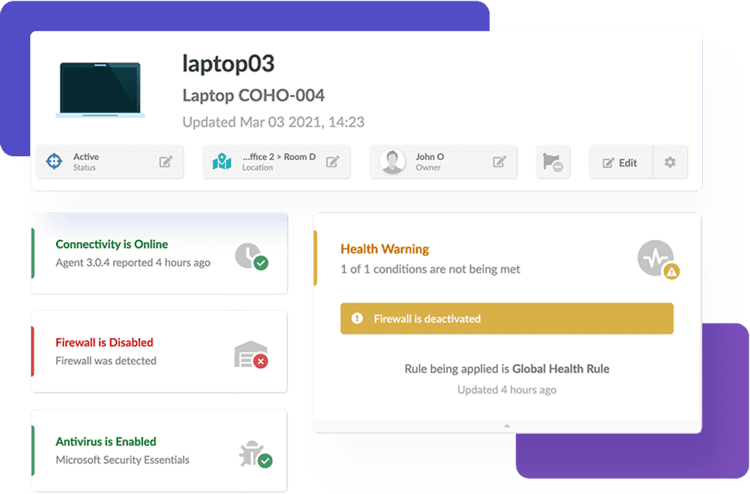
With multiple assets simultaneously operating in your IT environment, monitoring them without missing any potential threats or weaknesses can pose a challenge.
To do this, install InvGate’s Agent on your assets. Then, they will automatically start reporting to your instance and you can get valuable data from it:
- OS version.
- Antivirus.
- Firewall.
- Installed software.
- Hardware components.
- And more!
3. Validate asset status to ensure they are protected and controlled
ITAM practices also look to monitor the assets' health status throughout their lifecycle. For instance, it’s quite common for firewalls and antivirus to be disabled or not installed on computers, and you might not even know it, leading to vulnerable devices.
Here, you can customize health rules on InvGate Asset Management to track if they are “safe”, “warning”, or “critical”. Then, by implementing automation rules your agents will be notified whenever an asset changes its status. For example, they will receive a “warning” message if their antivirus is disabled or “critical” if it’s not even yet been installed.
This type of behavior helps your team foster a proactive ITAM strategy and prevent major risks from occurring and causing bigger damage.
4 Tag unauthorized applications to avoid pirated licenses
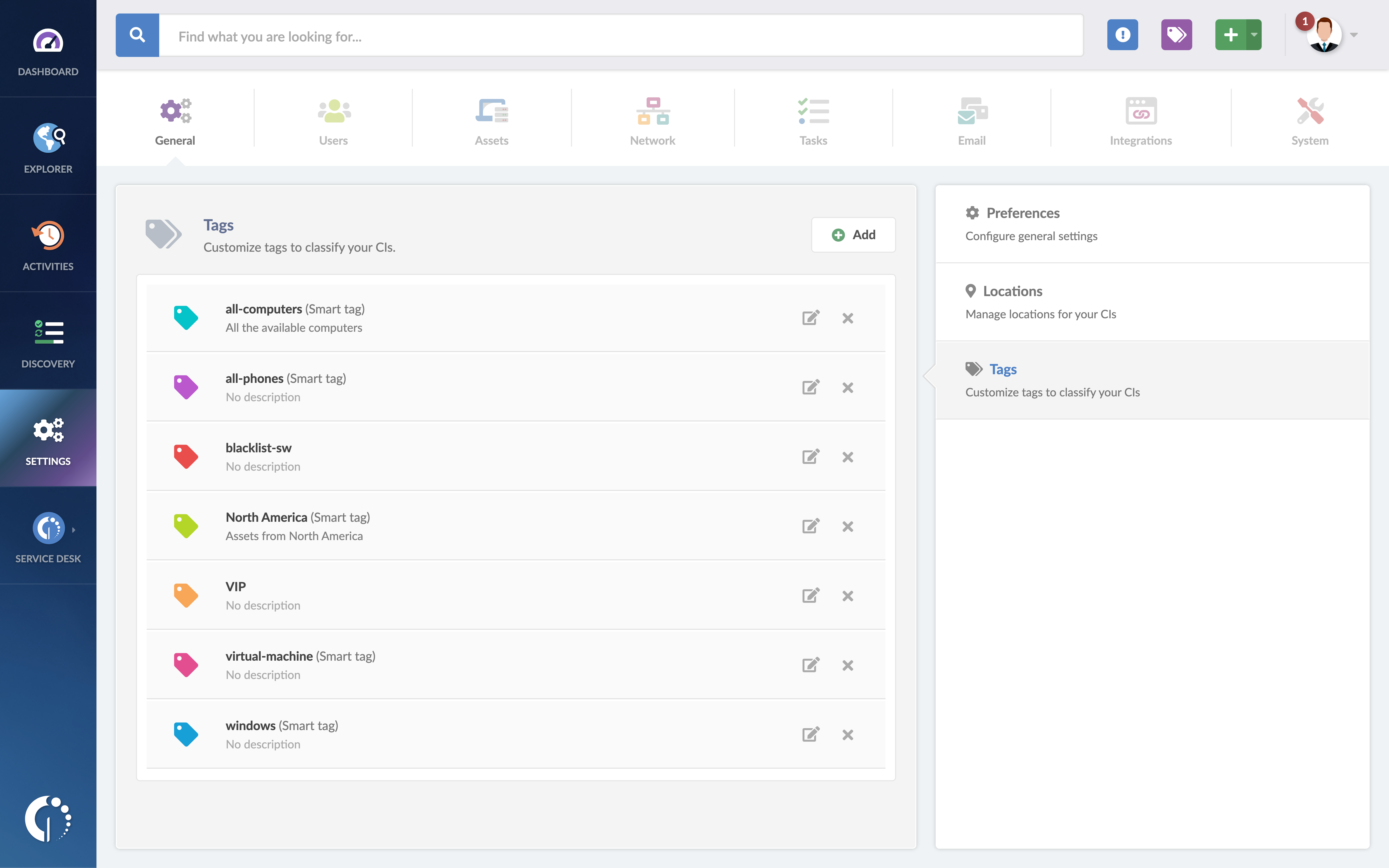
Another frequent situation is that users install applications on their computers for personal use. More often than not, this unauthorized software can lead to copyright infringement, legal liabilities, and potential security vulnerabilities.
Luckily, ITAM also has an answer for this. By configuring a smart tag on InvGate Asset Management you can filter these programs and flag troublesome apps, easily spotting devices with Steam, uTorrent, or other unauthorized software.
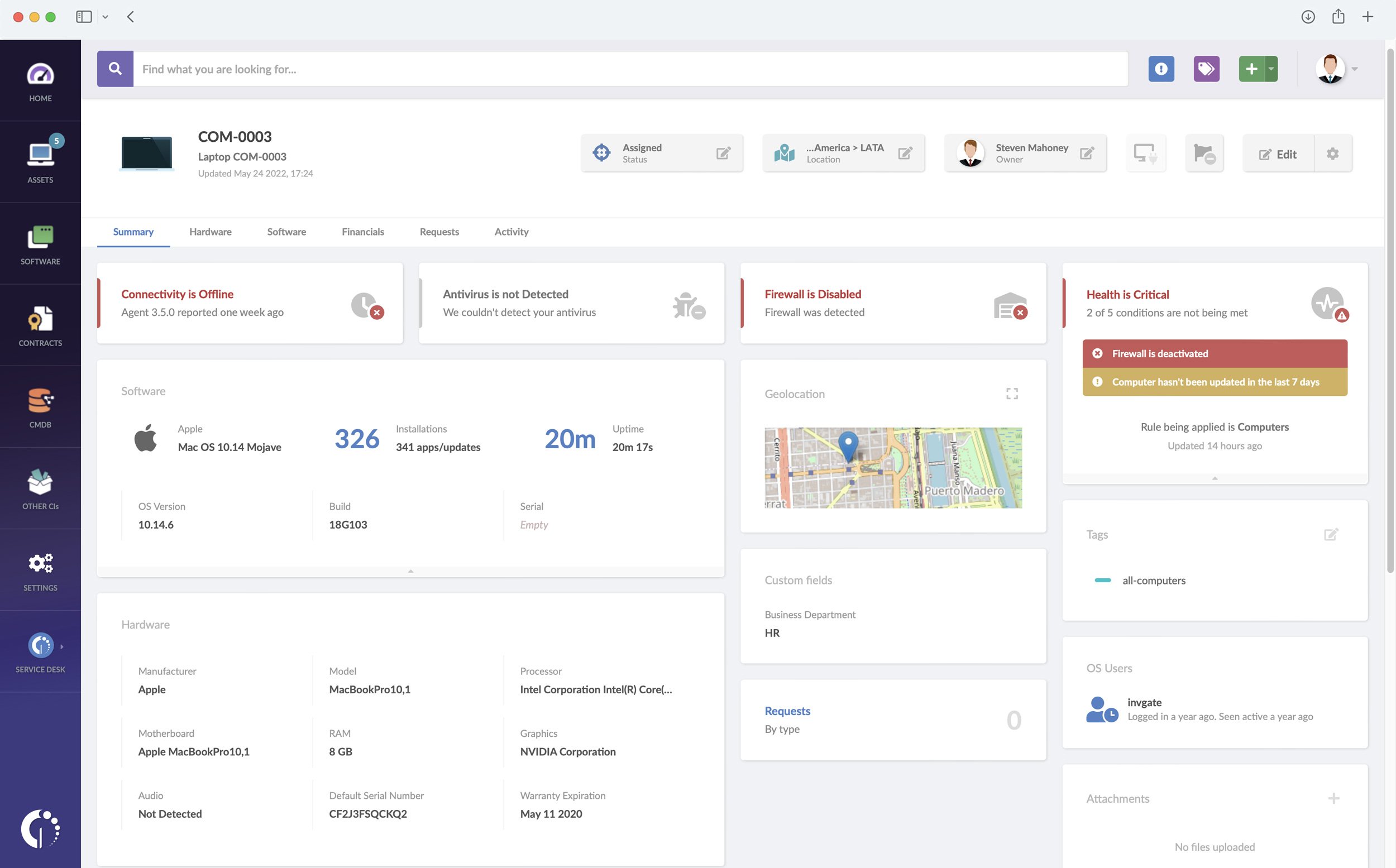
5. Use geolocation to prevent lost devices
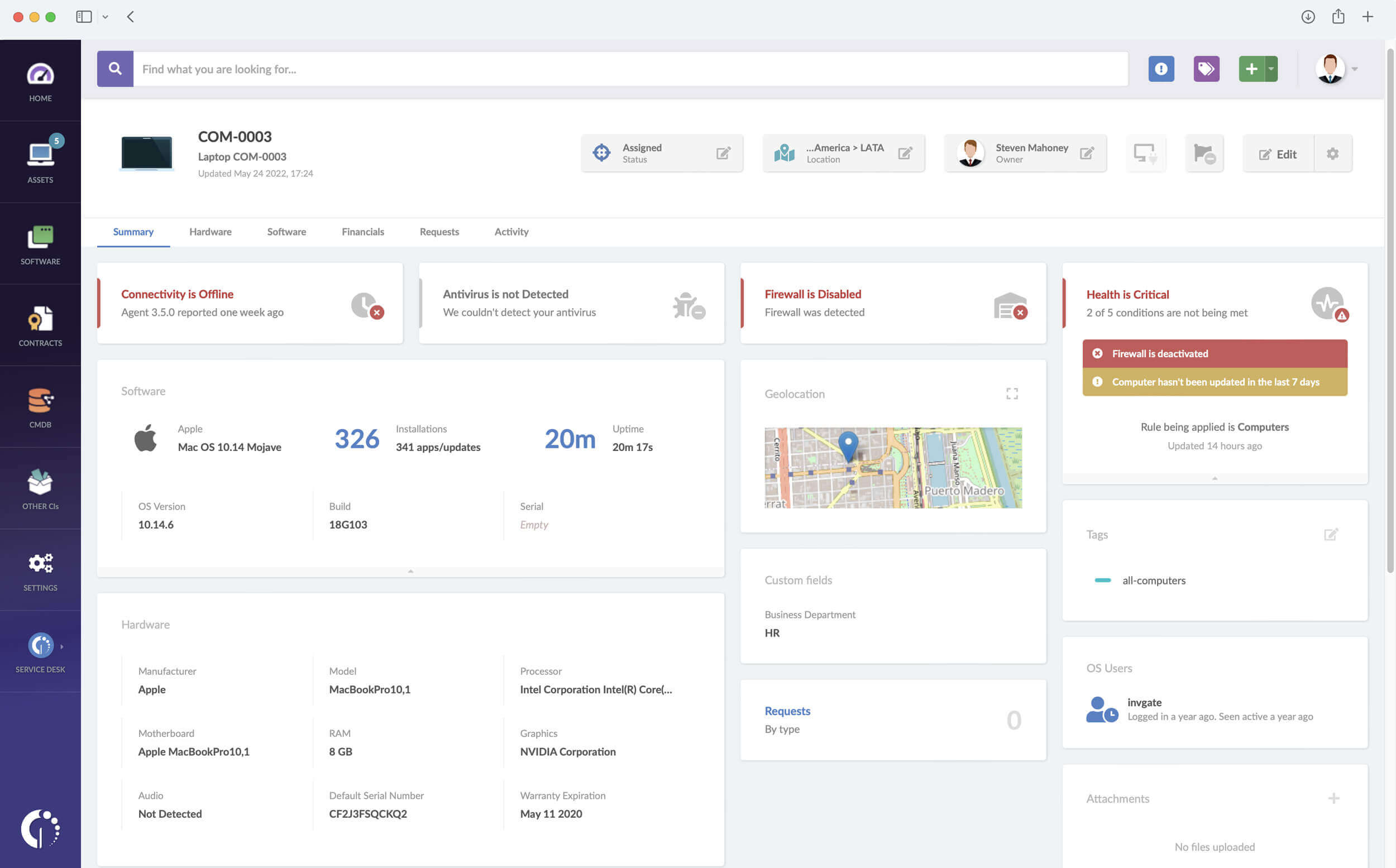
Security risks are not only linked to cyber attacks. As we mentioned before, lost or misplaced assets can also pose a considerable danger since they can be found and accessed by someone external to the organization.
This particular risk can be decreased if your ITAM software tracks the location of IT devices. It’s quite simple: if you know where they are, you have a much bigger chance of retrieving them as soon as they’re reported missing. On InvGate Asset Management, you can access this information directly through the asset’s profile.
6. Monitor cloud services to ensure proper usage
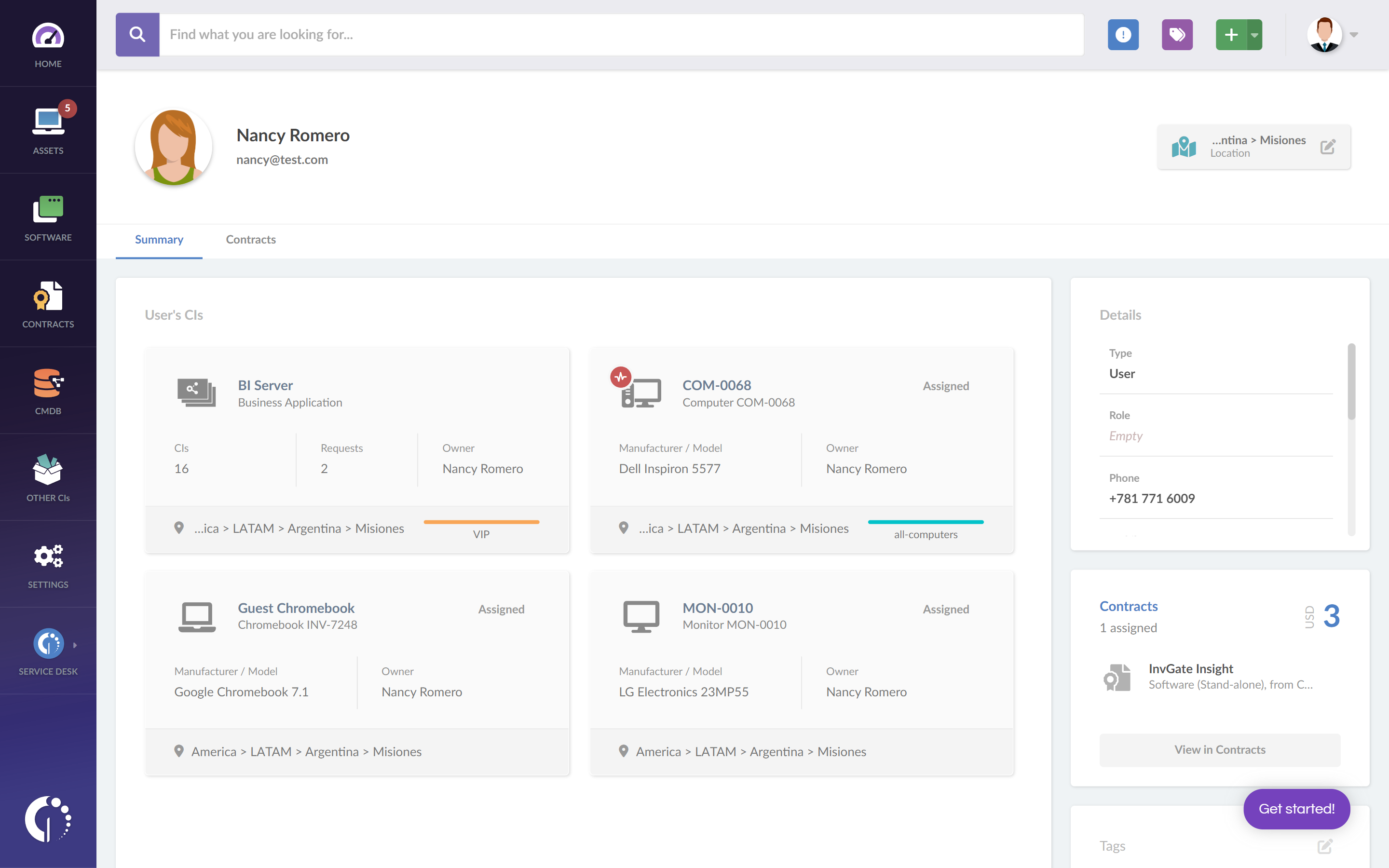
Another important backdoor we can’t overlook are cloud services that allocate critical and sensitive data. So, you must make sure they are properly configured and operated to avoid data leaks, unauthorized access, and increased cloud costs.
A simple way to keep them under your radar is to add them to your IT inventory. You can do so by using InvGate Asset Management’s API . Once they have been incorporated, you can add them to your CMDB, monitor them, track their usage, and more.
7. Scan your network periodically to detect shadow IT
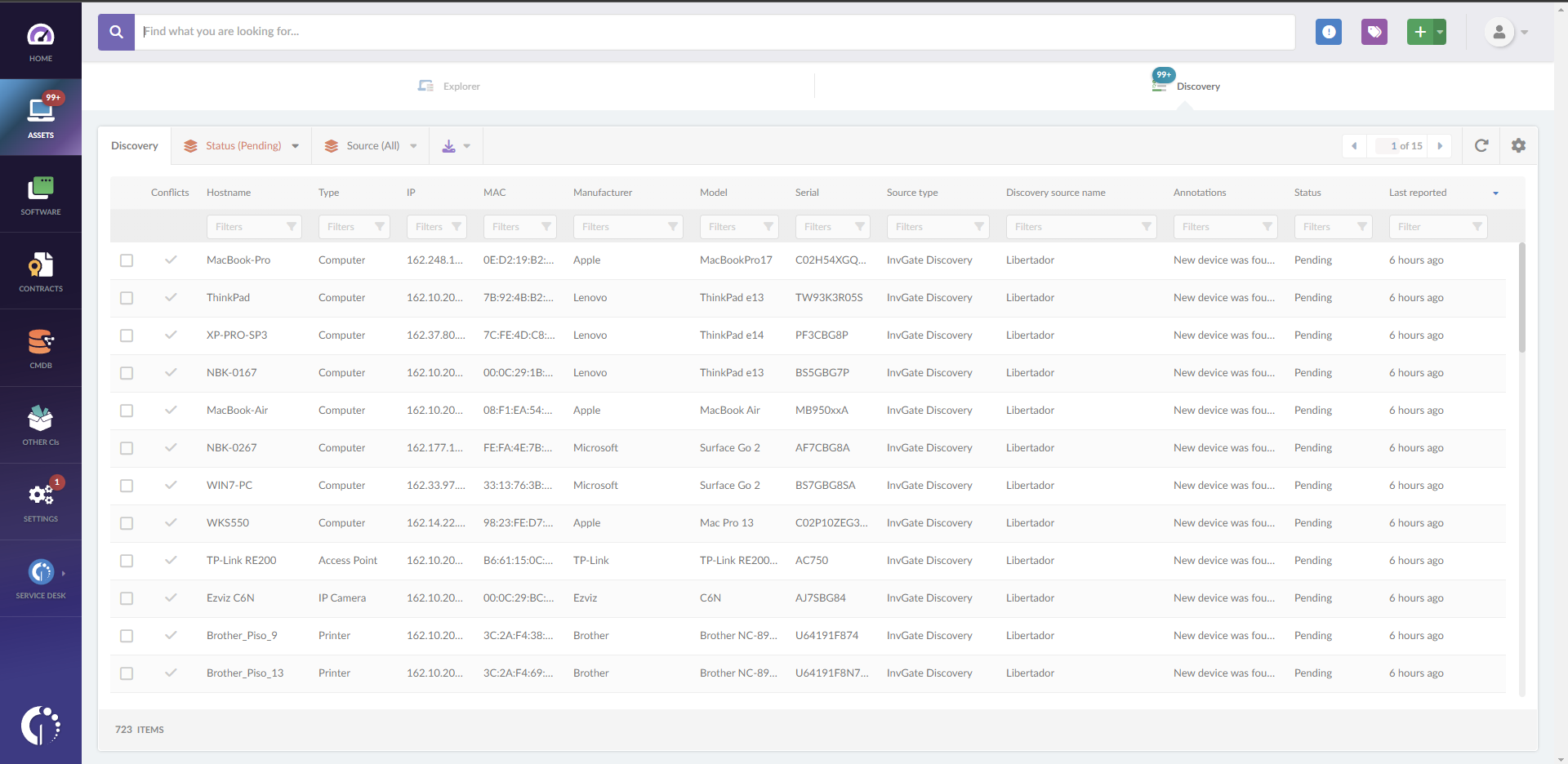
Shadow IT can introduce security vulnerabilities and potential entry points for cyber attacks. But luckily, nothing that can’t be addressed with proper ITAM. To identify these unauthorized assets, you can monitor them through your network with the Discovery feature.
If you run a periodic Discovery on InvGate Asset Management, you’ll be able to see everything that’s connected to a certain IP range, thus contributing to the detection of unwanted devices.
8. Conduct regular audits to mitigate blind spots in risk
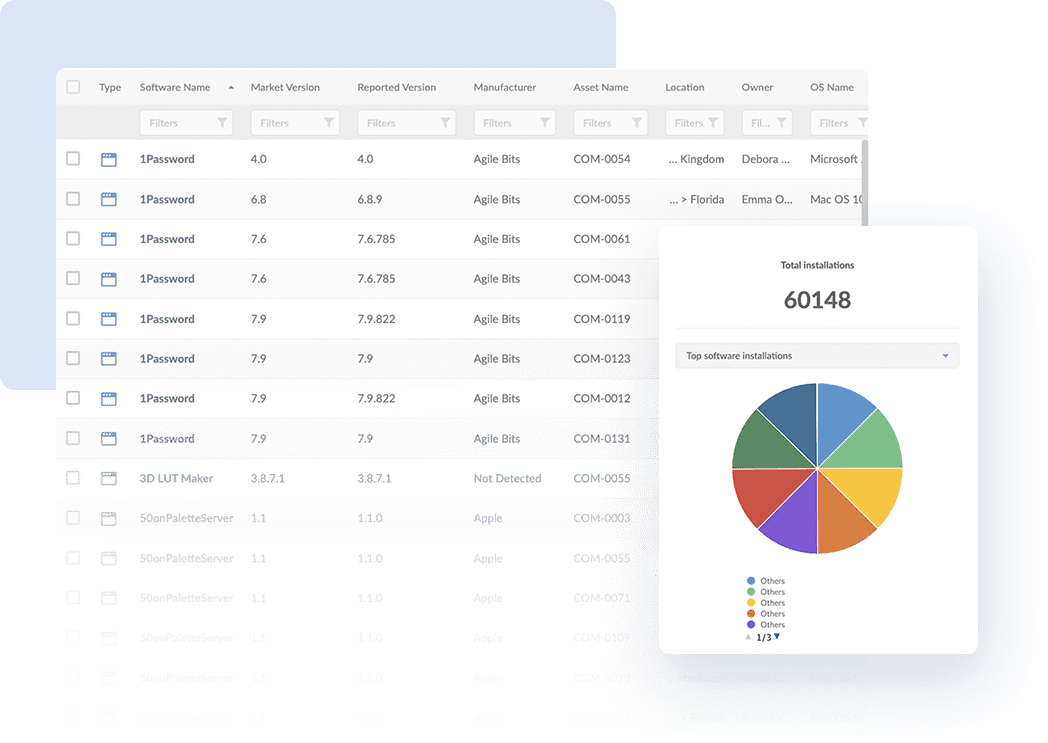
Finally, a central ITAM practice is conducting regular audits. It might sound like a big job, but it’s key to avoid any blind spots in your Risk Management.
To approach this, InvGate Asset Management incorporates customizable dashboards that provide you a clear bird’s eye into your IT infrastructure. You can make them as specific as you need, so you can have easy access to the data you need to analyze. By keeping a real-time record of your asset’s status and changes, you can identify discrepancies and take proactive measures to address them
Conclusion
Amongst its objectives, IT Asset Management practices come together to guarantee organizations stay on top of their potential threats and attacks. Keeping them safe means avoiding data leaks, interruptions, and unnecessary fines and costs.
Nevertheless, you should remember that reducing IT security risks is an ongoing commitment to adapting, refining, and innovating your strategies to match the ever-shifting threat landscape. And having the right tool to automate key tasks will help you focus on exactly this.
So, ask for InvGate Asset Management’s 30-day free trial and embark on a journey to a safer, more secure, and resilient ITAM!
Frequently Asked Questions
How can we reduce the risk of IT security?
Implement robust cybersecurity measures, conduct regular audits, educate employees on best practices, and leverage IT asset management for comprehensive risk mitigation.
What are the risks for information security related to Asset Management?
Risks include untracked assets leading to data breaches, non-compliance with software licensing, and unauthorized device access, all of which can compromise security.
How do IT assets help management in risk analysis?
IT assets provide data for assessing vulnerabilities, identifying potential threats, and evaluating the impact of security breaches, enabling informed risk management decisions.
What are the top 3 risks to IT security?
Common top risks are cyberattacks (e.g., ransomware), insider threats (unauthorized access), and data breaches (loss of sensitive information).
Why is Asset Management important in cybersecurity?
Asset Management ensures proper tracking, security, and compliance of IT assets, reducing vulnerabilities and improving overall cybersecurity posture.