Attack Surface Management (ASM) has become an essential aspect of cybersecurity. With the increasing number of cyber attacks, ASM is critical in identifying, evaluating, and managing vulnerabilities in an organization's systems and networks.But what exactly is Attack Surface Management? In this article, we'll discuss its definition, value, and how it works.
What is Attack Surface Management?
Let's start by defining the attack surface. This is the sum of all potential points where an unauthorized user could attempt to gain access to a company’s systems and data. It includes everything from web applications and network devices to cloud services and IoT devices.
Attack Surface Management (ASM) is the process of identifying, monitoring, and managing all external and internal assets for potential attack vectors and exposures. ASM helps organizations improve their security posture, reduce the risk of cyberattacks, and enhance their overall cyber resiliency.
Why is attack surface management important? Because it helps organizations identify, monitor, and mitigate vulnerabilities across their entire digital environment. It helps identify and address vulnerabilities and minimizes the risk of cyberattacks and data breaches.

The attack surface and its challenges
The entire attack surface is dynamic and ever-evolving, making it difficult to pin down. Digital transformation initiatives, such as the adoption of cloud services, the proliferation of IoT devices, and the integration of third-party applications, continuously expand and alter the attack surface.
Additionally, the interconnected nature of modern IT environments means that a vulnerability in one part of the system can potentially affect others, further complicating the task of defining and managing the attack surface.
Types of attack surfaces:
The attack surface is the sum of all points where an attacker could attempt to gain access to a company’s systems and data. These points can be physical or digital:
-
Cloud Attack Surface: Includes all cloud-based services and applications.
-
On-Premises Attack Surface: Refers to physical servers, workstations, and network devices within the organization's premises.
-
IoT Attack Surface: Encompasses all Internet of Things devices connected to the network.
Attack vectors
Attack vectors are the methods used by attackers to exploit vulnerabilities. Common attack vectors include:
-
Phishing: Deceptive emails or messages designed to trick users into revealing sensitive information.
-
Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to a computer system.
-
Social engineering: Manipulating individuals into divulging confidential information.
-
Network attacks: Attacks targeting network infrastructure, such as DDoS attacks.
-
Zero-day exploits: Exploits that take advantage of unknown vulnerabilities in software.
-
Web application vulnerabilities: Flaws in web applications that can be exploited by attackers.
-
Cloud misconfigurations: Errors in cloud settings that can expose data or systems.
-
Supply chain attacks: Attacks targeting third-party vendors or suppliers to gain access to the main target.
-
Insider threats: Threats posed by employees or contractors with authorized access.
-
Physical attacks: Attacks that involve physical access to systems or facilities.
Threat actors
Threat actors include various individuals and groups that can exploit vulnerabilities in an organization’s attack surface to gain unauthorized access to systems and data.
-
Hackers and cybercriminals: Individuals or groups motivated by financial gain or personal challenge.
-
Nation-state actors: Government-sponsored hackers with political or strategic objectives.
-
Insiders: Employees or contractors with authorized access who may act maliciously.
-
Hacktivists: Individuals or groups motivated by political or social causes.
-
Other malicious actors: This can include competitors, disgruntled former employees, and opportunistic attackers.

Impact of digital transformation
Digital transformation has led to an expansion and evolution of potential points of vulnerability that malicious actors can exploit. Increased connectivity, cloud adoption, IoT adoption, mobile workforces, and third-party integrations have all contributed to the growth of the attack surface.
Factors contributing to the growth of the attack surface:
-
Increased connectivity: More devices and systems are connected to the internet, creating additional entry points for attackers.
-
Cloud adoption: The widespread use of cloud services has introduced new risks related to misconfigurations and data breaches.
-
IoT adoption: The proliferation of IoT devices has created numerous entry points that can be exploited by attackers.
-
Mobile workforces: The rise of remote work has increased the number of endpoints that need to be secured.
-
Third-party integrations: The integration of third-party applications and services can introduce vulnerabilities if not properly managed.

Adapting to new risks
Organizations must adapt their Vulnerability Management and attack surface management strategies to address these new risks. This includes implementing robust security measures for cloud environments, securing IoT devices, and ensuring that third-party integrations are properly vetted and monitored.
External attack surface management is critical to adapting to these new risks. It involves the continuous identification, monitoring, and management of internet-facing assets to detect and mitigate vulnerabilities. These assets are often the first line of defense and can be the easiest targets for attackers.

How Attack Surface Management works
ASM involves several steps, including:
Asset discovery - Asset mapping - Vulnerability assessment - Risk analysis -Remediation- Continuous monitoring
Let's take a closer look at each of them:
1. Asset discovery
The first step in ASM is to identify all the assets that an organization owns, including network infrastructure, software, and hardware.
Asset discovery is foundational to ASM because you can't protect what you don't know exists. Organizations often accumulate assets over time, and some unmanaged or unknown assets can be overlooked without a systematic approach to tracking them. This is particularly true in large enterprises with complex IT environments.
Challenges:
-
Shadow IT: Employees may use unauthorized software or devices, creating assets that are not officially recognized by the IT department.
-
Legacy systems: Older systems that are still in use but not well-documented can be easily forgotten.
-
Dynamic environments: In environments where assets are frequently added, removed, or modified, keeping an up-to-date inventory can be challenging.
To do this quickly and automatically, you can use InvGate Asset Management's Network Discovery feature, enabling you to scan the network, populate your IT asset inventory, and receive all the information to monitor your organization’s assets and act on potential threats.
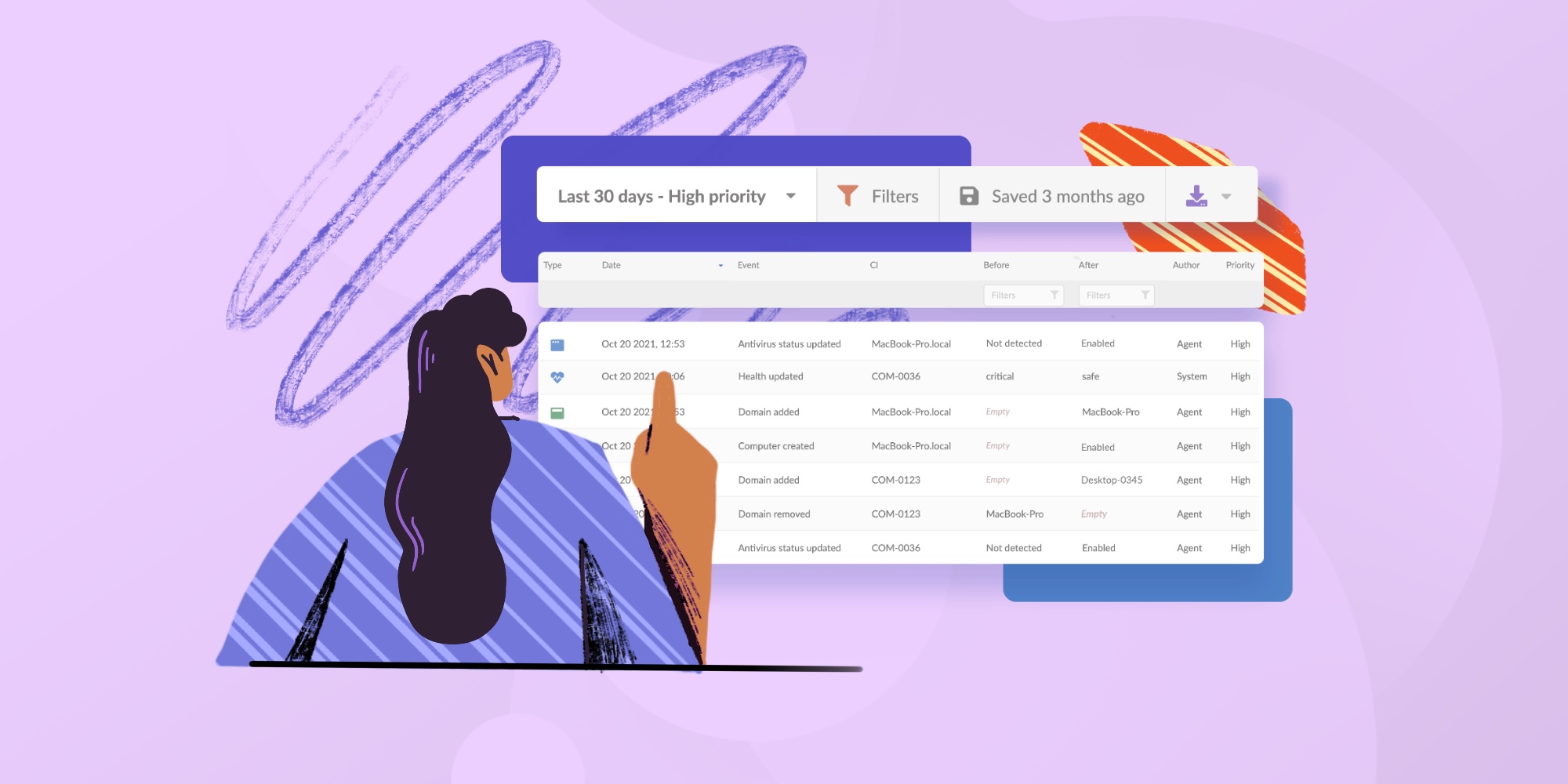
2. Asset mapping
Attack surface mapping involves identifying all the potential ways an attacker could access an asset. This can include external assets, such as websites and mobile applications, and internal-facing assets, such as employee workstations and servers. Asset mapping lets security teams visually represent these assets and their interconnections.
Understanding the interconnections between assets is essential for identifying potential attack vectors. An attacker may exploit one asset to gain access to another, more critical asset.
Challenges:
-
Complexity: Modern IT environments are highly interconnected, making it difficult to map all potential attack paths.
-
Dynamic changes: Assets and their relationships can change frequently, requiring continuous updates to the map.
-
Visibility: Some assets, particularly those in cloud environments or third-party services, may not be fully visible to the organization.
3. Vulnerability assessment
After mapping the attack surface, the security team conducts a vulnerability assessment to identify vulnerabilities and weaknesses in the security controls for each asset.
Identifying vulnerabilities is a critical step in understanding the risks associated with each asset. Vulnerabilities can exist in software, hardware, or configurations, and they provide potential entry points for attackers.
Challenges:
-
Volume: The sheer number of assets and potential vulnerabilities can be overwhelming.
-
Accuracy: Ensuring that the vulnerability assessment is comprehensive and accurate requires expertise and up-to-date knowledge of threats.
-
Prioritization: Not all vulnerabilities are equally critical, and determining which ones to address first can be challenging.

4. Risk analysis
Once the security team has identified the vulnerabilities, they perform a risk analysis to determine the likelihood of a successful attack and the potential impact of such an attack.
Risk analysis helps organizations prioritize their remediation efforts by evaluating the severity and potential impact of each vulnerability. This ensures that the most critical security issues are addressed first.
Challenges:
-
Subjectivity: Risk analysis often involves subjective judgments about the likelihood and impact of attacks.
-
Data availability: Accurate risk analysis requires comprehensive data about assets, vulnerabilities, and potential threats, which may not always be available.
5. Remediation
Based on the results of the risk analysis, the security team initiates remediation activities to address the identified vulnerabilities. This may include implementing security patches, upgrading software, or reconfiguring the organization's network and infrastructure.
Remediation is the actionable step that reduces the risk of cyberattacks.
Challenges:
-
Resource constraints: Remediation can be resource-intensive, requiring time, expertise, and financial investment.
-
Downtime: Applying patches or making configuration changes can sometimes require taking systems offline, which can disrupt operations.
-
Complexity: Some vulnerabilities may be deeply embedded in the system, making them difficult to remediate without affecting other components.
6. Continuous monitoring
ASM is an ongoing process that requires continuous monitoring and updating of an organization's digital assets. It ensures that any new vulnerabilities are identified and addressed in a timely manner.
Challenges:
-
Alert fatigue: Continuous monitoring can generate a large volume of alerts, leading to alert fatigue and the risk of missing critical issues.
-
Resource intensity: Continuous monitoring requires dedicated resources and can be resource-intensive.
Tools to approach Attack Surface Management
A robust Attack Surface Management strategy starts with a suite of tools designed to provide a comprehensive view of an organization’s attack surface and help identify potential security risks. These tools work together to ensure that all assets and security operations are accounted for, monitored, and protected.
Key tools and components:
-
Asset discovery, inventory, and classification: These tools help organizations identify all their assets, including those that might have been overlooked or forgotten.
-
Risk scoring and security ratings: These tools quantitatively measure an organization’s security posture.
-
Automated scanning: Automated tools, like vulnerability scanners, can be used to check the network and systems and identify risks. They can also provide real-time insights into the security posture of the organization.
-
Real-time monitoring: Real-time monitoring tools offer immediate alerts and notifications about potential threats, enabling organizations to respond quickly to security incidents.
Benefits of Attack Surface Management
Businesses face an ever-increasing threat of cyber attacks (and, in fact, some industries are more prone to security breaches than others). With the growing number of devices and services that people use, it's becoming more challenging to maintain a strong cybersecurity posture. That is when an attack surface management solution comes into play.
ASM enables organizations to gain visibility into their digital footprint, including all the systems, devices, applications, and services they use. Why is ASM important? Because it helps organizations to:
-
Identify and evaluate potential risks: ASM helps to identify and assess the potential vulnerabilities to which an organization's digital assets are exposed. It allows businesses to prioritize their cybersecurity efforts and allocate resources to the most vulnerable areas.
-
Reduce the probability of successful attacks: ASM helps identify and address vulnerabilities before attackers can exploit them. It reduces the likelihood of successful attacks and minimizes the impact of any successful attacks that do occur.
-
Improve overall cybersecurity posture: By identifying and addressing vulnerabilities, ASM enhances an organization's overall cybersecurity posture. As a result, it can help build trust with customers, partners, and other stakeholders.
-
Meet regulatory and compliance requirements: ASM is often a requirement for compliance with various regulatory frameworks, such as the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), and the General Data Protection Regulation (GDPR).
Conclusion
Organizations are constantly witnessing how their attack surface grows, and they must adopt a proactive approach to mitigate cyber risks effectively.
Attack Surface Management solutions can help security teams stay ahead of emerging threats and ensure that malicious or rogue assets do not go unnoticed. These solutions provide a holistic view of the attack surface, enabling organizations to prioritize their security efforts and respond more effectively to security incidents.
Undoubtedly, cyber risks are becoming increasingly complex and frequent, and a well-executed attack surface management process is essential for safeguarding critical assets and sensitive data.















