Is your organization looking to up its IT audit game? Conducting it successfully will help you ensure that your IT systems and processes are secure, they comply with relevant regulations and standards, and are aligned with your overall goals and objectives.
This practice lies at the core of your IT Asset Management (ITAM) strategy, guaranteeing a robust, safe, and well-managed IT environment across your operations. And, it’s the perfect time to ensure you’re doing it right, as an increase in software audits was included in the ITAM trends for 2025.
In the following article, we have put together a thorough guide on how to conduct an IT audit in 2025, including two general audit process checklists free to download and insights into how InvGate Asset Management can help you streamline key activities.
Table of contents
- What is an IT audit
- Who needs an audit for IT – and why?
- 8 key benefits of IT audits
- Types of IT audits
- How to conduct an audit: the IT audit process
- Download: A general IT audit process checklist
- How can InvGate Asset Management help you conduct an IT audit
- IT audit best practices

What is an IT audit?
An IT audit evaluates an organization’s information technology infrastructure, policies, and operations, examining the management controls within its IT infrastructure and business operations.
In essence, an IT audit will help ensure that IT environments are managed and controlled effectively to safeguard an organization’s assets, maintain data integrity, and operate in alignment with the organization’s goals and objectives.
There are many flavors of audits, with each focusing on a specific IT management area. It typically focuses on areas such as:
- Governance and management – Evaluating IT governance structures, roles, and responsibilities and assessing the alignment of IT strategy with organizational objectives.
- Compliance – Checking whether IT processes and systems comply with applicable laws, regulations, and standards to ensure proper controls are in place for data privacy and protection.
- Operations – Reviewing the management of IT assets and resources and evaluating the performance, reliability, and availability of IT systems and services.
- System and data security – Assessing the effectiveness of firewalls, encryption, and other security measures and evaluating the vulnerability to various security threats such as malware, phishing, and hacking.
- Data integrity and accuracy – Evaluating the measures in place for ensuring the accuracy and integrity of data and checking the controls over data input, processing, and output.
- Physical security – Reviewing the protection of IT assets from physical threats such as theft or damage.
- Disaster recovery and business continuity – Assessing an organization’s preparedness for unexpected events like natural disasters or cyberattacks and evaluating the effectiveness of disaster recovery plans and business continuity strategies.

The purpose of IT audits
The purpose of an IT audit can be viewed from four key perspectives:
- Risk Management – Identifying and assessing risks to the confidentiality, integrity, and availability of information assets.
- Assurance – Providing assurance to stakeholders that IT is managed effectively and securely.
- Accountability – Ensuring accountability and adherence to organizational policies and industry best practices
- Continual improvement – Identifying areas for improvement in IT management processes and procedures.
What an IT audit entails
An IT audit can include different steps depending on the purpose and scope of it. There are usually common elements to IT audits that may include some of the following depending on the focus:
- Objective and scope setting.
- Risk assessment.
- Data collection.
- Control and system testing.
- Security review.
- Compliance review.
- Operational practices review.
- Performance review.
- Audit reporting.
- Audit review and follow-up.
Who needs an audit for IT – and why?
An IT audit is crucial to any organization because it helps maintain the integrity and reliability of an IT infrastructure and data. It considers corporate functions such as risk assessment, data integrity, compliance, security assessment, and aid to business continuity and disaster recovery.
Without regular IT audits, an organization is not only potentially inefficient and ineffective, but it might also be vulnerable to cybersecurity threats and the adverse business impacts these bring.
Let’s take a look at some IT audit examples to see the different areas of business a regular practice can help streamline.
IT audit example #1 – Identifying and mitigating IT risks
IT audits help organizations identify and manage risks, including system failures, cyberattacks, and data breaches. Example audit findings include the following:
- Any databases storing customer information were not adequately encrypted.
- Weaknesses in user access controls where some employees have access unnecessary for their roles.
- Outdated incident response plan, lacking clear procedures for certain types of cybersecurity incidents.
IT audit example #2 – Ensuring compliance with laws and regulations
Most industries are subject to laws and regulations that govern their IT systems and Data Management. With IT audits, organizations stay compliant with these requirements. Example audit findings include the following:
- Some transmitted electronic protected health information (ePHI) was not adequately encrypted.
- Employee training programs related to SOC2 compliance were insufficient.
- Delayed process for removing access rights for terminated employees, leaving a window of vulnerability.

IT audit example #3 – Improving the efficiency of IT operations
IT audits help identify areas where IT operations can improve, resulting in cost savings and improvement in overall business performance. Example audit findings include the following:
- Outdated hardware causing slow system performance and occasional downtime.
- Multiple redundant IT processes, leading to wasted time and resources. For instance, the Change Management process required unnecessary approval from staff who were unaware of what they were approving.
- Inconsistent data backup and recovery practices, posing a risk of data loss.
IT audit example #4 – Protecting corporate assets
As we mentioned, audits are a fundamental pillar of your ITAM initiative. In this sense, by using IT audits to identify the vulnerabilities they are exposed to, organizations can protect their IT assets from unauthorized access, use, and destruction. Example audit findings include the following:
- Expensive manufacturing equipment that is not adequately accounted for in the asset inventory.
- Weaknesses in network security that can expose sensitive company data to potential external attacks.
- Inadequate destruction process and documentation making data assets vulnerable to unauthorized access or theft.
For this, a competent ITAM tool is key in order to monitor your IT environment, automate certain control operations, perform internal audits, and be alerted if anything comes up to act on it promptly. But more on this later, we promise.

IT audit example #5 – Ensuring the integrity of data
IT audits help ensure that databases are accurate, updated, and reliable. This helps support business decisions and also with regulatory compliance. Example audit findings include:
- Inconsistencies between data entry interfaces and actual stored data, leading to potential inaccuracies.
- A lack of comprehensive data validation rules, allowing the entry of inconsistent or inaccurate data.
- Audit logs that are not adequately maintained, making it difficult to trace and rectify data integrity issues.
8 key benefits of IT audits
The main benefits of conducting IT audits are very much aligned with the stated purpose areas, including the following:
- Enhanced security – Identifying vulnerabilities and preventing unauthorized access.
- Improved regulatory compliance – Ensuring legal compliance and avoiding penalties.
- Better Risk Management – Assessing risks and formulating risk mitigation strategies.
- Improved data integrity – Ensuring accuracy and reliability and preventing data loss.
- More-optimized IT operations – Increasing efficiency and enhancing productivity.
- Informed decision-making – Providing valuable insights and facilitating strategic planning and improvements.
- Effective business continuity capabilities – Evaluating disaster recovery plans and minimizing downtime through quick recovery from disruptions.
- Increased stakeholder confidence – Building trust and attracting greater investment in technological capabilities.
Types of IT audits
First of all, IT audits can be internal or external. The first is conducted by an organization's internal audit department or team in order to evaluate and improve controls, security, and overall IT governance and prepare for when the external auditor comes. The second is carried out by independent third-party audit firms or regulatory bodies external to the organization and provides an objective evaluation of an organization's IT systems, processes, and controls.
There are also various types of IT audits, defined by their specific focus and purpose, such as:
- Systems and applications audits – These ensure that systems and applications are appropriate, efficient, and secure based on the evaluation of controls related to software acquisition or development, implementation, and maintenance.
- Information processing facilities audits – These evaluate facilities, such as data centers, to ensure their physical security, environmental controls, and access controls.
- Systems development audits – These evaluate the systems under development, looking at Project Management practices, system specifications, and development processes.
- “Management of IT” audits – These assess whether the management of IT meets business objectives, including IT governance, strategy, and alignment with business goals.
- Enterprise architecture audits – These assess whether an organization’s enterprise architecture capabilities meet business objectives.
- Client/server and telecommunications audits – These evaluate the infrastructure used in these technologies to ensure they meet organizational needs.
- Business continuity and disaster recovery audits – These assess an organization’s preparedness for unexpected disruptive events, including backup plans, emergency procedures (and their testing), and recovery strategies.
- Cybersecurity audits – these assess the effectiveness of an organization’s cybersecurity posture and resilience against cyber threats, including threat prevention, detection, and response mechanisms.
- Data governance audits – These ensure that data is accurate, available, and secure, with a focus on Data Management policies, data quality, and privacy.
- Compliance audits – These assess whether an organization’s IT systems comply with specific regulations and standards, such as GDPR and SOC2, focusing on legal obligations, industry standards, and compliance processes.
- IT governance audits – these evaluate the effectiveness of IT governance structures and processes, with a focus on IT decision-making, policies, and organizational structures.
- IT Project Management audits – These assess the management of IT projects for effectiveness and alignment with organizational objectives, including project planning, execution, and monitoring processes.
- Third-party and vendor audits – These assess the risks and controls associated with third-party services, such as cloud providers or vendors; the focus includes Vendor Management, service agreements, and Risk Management.
How to conduct an audit: the IT audit process
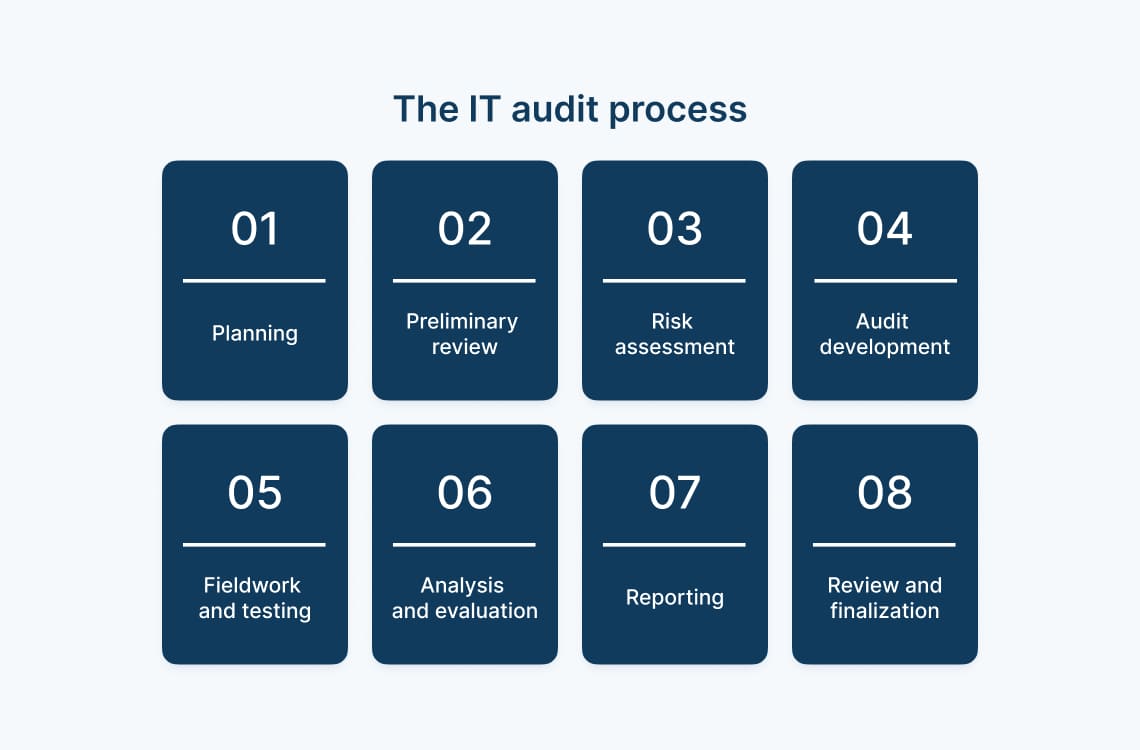
A generic IT audit process involves various steps to evaluate the management, security, and effectiveness of an IT environment. These should be tailored to suit the needs of the IT audit and your organization, but baseline steps include:
- Planning – Including the objectives and scope of the audit (based on risk assessment, organizational goals, and regulatory requirements) and resource allocation.
- Preliminary review – To understand the current systems, processes, and controls that are running and how.
- Risk assessment – Identifying potential risks and vulnerabilities and analyzing and prioritizing them based on likelihood and impact. For this, defining incident severity levels can be useful.
- Audit development – Designing audit tests to evaluate controls and defining criteria to evaluate the effectiveness of controls.
- Fieldwork and testing – Executing audit tests and gathering evidence through interviews, observations, and document reviews.
- Analysis and evaluation – Assessing whether IT controls are effective and identifying weaknesses, non-compliance, and areas for improvement.
- Reporting – Preparing and presenting an audit report that summarizes the audit findings, conclusions, and recommendations.
- Review and finalization – Finalizing the audit report based on the feedback received from stakeholders.
Following these primary IT audit steps, an organization will make focused improvements and likely conduct a repeat audit to assess progress.
Download: Two general IT audit process checklist
The following document contains two general IT audit checklists that will guide you through the main stages of the process, making sure you cover the most important points. However, keep in mind that it’s important to adapt them based on your organization, industry, and the objective of the IT audit.
While the first structures it throughout the main activities to be carried out, the second one provides a set of general questions that you should be asking yourself in every stage of the audit.
How can InvGate Asset Management help you conduct an IT audit
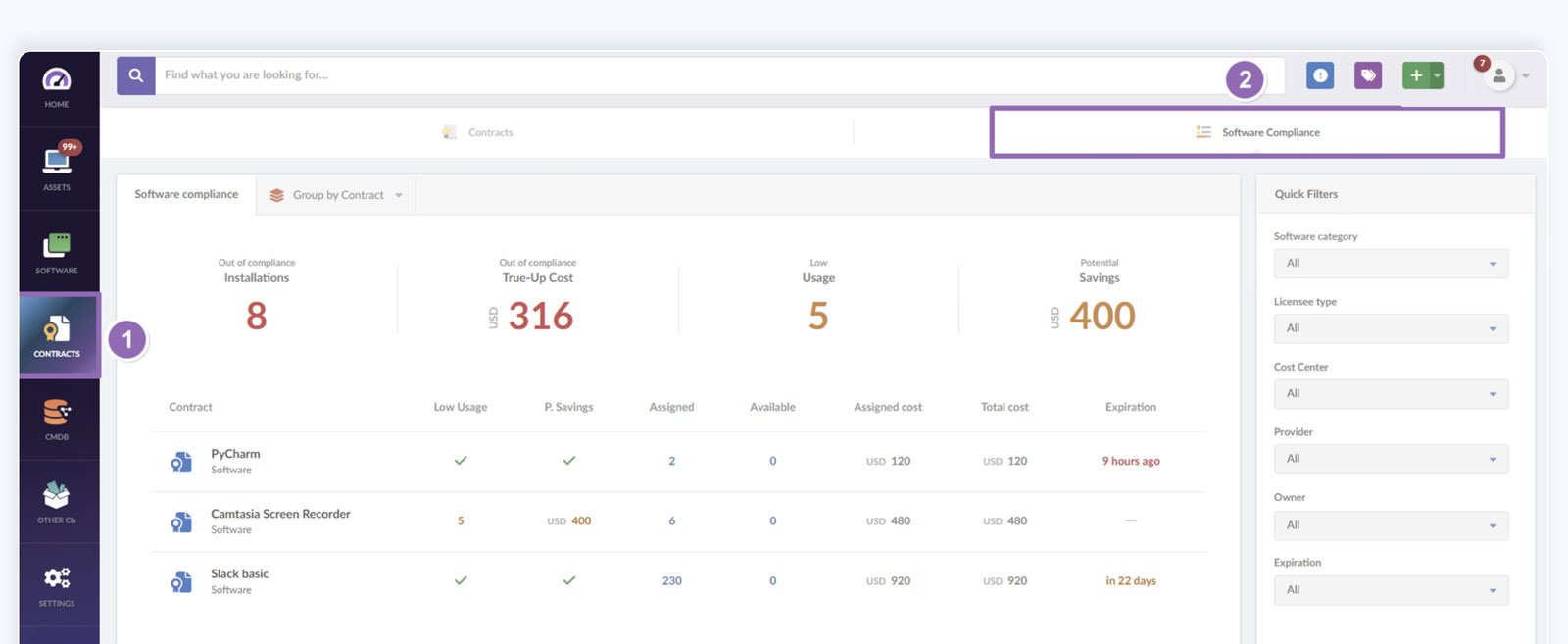
IT audits are extensive processes that require orchestrating a range of practices and simultaneously keeping your eye on different aspects of your IT infrastructure. For this, after building your complete IT asset inventory on the tool, InvGate Asset Management supports your internal auditing process by monitoring your environment and alerting you of anything that needs to be improved or adjusted.
For instance, the software compliance module crosses information from your logged contracts with the reported software usage in your environment providing you with information on out of compliance installations and low usage licenses. This way, you can take notice and act on them before the external auditor does.
This is not it, if you want to see everything the tool can do to help you conduct thorough internal IT audits (and therefore arrive prepared for external ones), don’t hesitate to book a call with our experts who will show you round the solution and all its possibilities.
IT audit best practices
There are many IT audit best practices that organizations can employ to make the process more efficient and effective. These include:
- Conducting IT audits at regular intervals to continually assess and improve the IT environment.
- Leveraging both internal and external auditors to keep costs low while also protecting audit value.
- Spending sufficient time in the planning phase to define the audit scope, objectives, and methodology clearly.
- Adopting a risk-based approach to focus audit efforts on areas that are most critical and vulnerable.
- Regularly updating the risk assessment to reflect changes in the IT environment, business processes, and emerging threats.
- Maintaining open communication with all relevant stakeholders.
- Keeping detailed and organized records of the audit process, findings, and recommendations.
- Implementing a structured follow-up process to monitor the progress of action items and recommendations.
- After each audit, conduct a review to identify lessons learned and any areas for improvement in the IT audit process.
Conclusion
Here we have explored the main aspects to consider when conducting an IT audit in your organization, including the different types, benefits and best practices, and the main steps of the process. While various IT audit types can follow similar approaches, it’s essential to ensure that the planned process and its execution are tailored to your specific needs and goals.
Also, IT audits and a robust IT Asset Management strategy work closely together to ensure that organizations are fully protected and in compliance with regulations. In this sense, leveraging a tool to help monitor your environment and support your internal audit can make a big difference in terms of efficiency and effectiveness.
If you want to explore how InvGate Asset Management can help you through your auditing process, remember you can book a free 30 day trial and explore it for yourself!
Frequently Asked Questions
What software is used in auditing?
The type of software used in IT audits will depend on the audit focus. ITAM tools can help you monitor your IT environment and be alerted of securities and vulnerabilities to act on. But also, for example, IT general controls audits will need different software solutions from those required for network security audits.
So, when defining what software is used in IT auditing, there’s a need to differentiate the various use cases.
IT general controls audits – which likely have the broadest scope – will benefit from:
- IT Asset Management tools
- Audit Management and workflow tools
- Data analytics tools
- Risk assessment tools
- Access and Identity Management tools
- Security and vulnerability assessment tools
- Log Management and monitoring tools
- Network security tools.
Whereas network security audits will employ a variety of network-focused tools, including:
- Network mapping and visualization tools
- Network scanners and analyzers
- Vulnerability assessment tools
- Network performance and bandwidth monitors
- Security and Intrusion Detection Systems (IDS)
- Firewall and policy management tools
- Wireless network analysis tools
- Log and event management tools
- Password and access control tools.
How much does an IT systems audit cost?
You may as well ask, “How long is a piece of string?” because the cost of an IT systems audit can vary widely based on factors such as:
- The audit scope – More complex IT environments will mean higher audit costs, as will the audit’s objectives.
- The size of the organization being audited – As you would expect, larger organizations typically have more extensive IT infrastructures, leading to more comprehensive and costly audits.
- Industry factors – For example, organizations in certain industries with stringent regulations, such as finance and healthcare, may require specialized audits at higher costs.
- Company location and geographical spread – Regional pricing differences and the need for travel will affect audit pricing.
- Tools and other resources – The use of fit-for-purpose audit technology will both add costs and remove costs.
- External vs. internal audits – Being audited by independent third parties will cost more than internal audits.
So, it ultimately depends on what’s needed in the IT audit. For example, a security audit is estimated to cost between $1,500 and $20,000, but it could cost far more depending on the above factors.
What is the role of an IT auditor?
The role of an IT auditor is somewhat aligned with the IT audit process outlined earlier, such that their primary roles and responsibilities include:
- Planning and designing the audit – Defining the audit objectives.
- Conducting the audit – Collecting data and validating controls.
- Evaluating IT governance – Assessing policies and procedures and reviewing management practices.
- Assessing security – Evaluating security measures and assessing access controls.
- Reviewing compliance – This can be regulatory compliance or policy compliance.
- Reporting and making recommendations – Documenting and communicating the audit findings and recommendations related to improvements and best practices.
- Audit follow-up and monitoring – Tracking remediation efforts and continual improvement success.