Configuration Items or CIs are the building blocks that make up business services. Managing them effectively is a key activity of the Configuration Management process, which looks to make sure these components are accounted for and reliable information on them is available. It lays the groundwork for trustworthy service operations.
The most widespread practice to do this is by building a Configuration Management Database (CMDB) that sets out your CIs and their relationships. So, join us as we define the full scope of Configuration Items and explain how to manage them effectively on InvGate Asset Management.
Ready to learn more about CIs? Let's get started.
What is a Configuration Item (CI)?
The Configuration Management practice has a lot of terminology, so let's start with the basics. ITIL defines a Configuration Item (CI) as any component which needs to be managed in order to deliver an IT service.
In simpler terms, it can be thought of as any identifiable and manageable element that contributes to the functioning of an organization's IT environment.
This can include a mayor or minor hardware component, software, network equipment, buildings, suppliers, and documentation – that is, anything that can make up part of an IT entire service.
Asset vs. Configuration Item
Assets and Configuration Items are dealt with in the ITIL framework. They are both key components that must be kept under your radar and help you efficiently manage your IT environment. However, there are key differences between the two to consider. Let’s take a look.
-
A Configuration Item is a building block within an organization's IT infrastructure and includes any components that need to be managed and controlled to ensure the delivery of IT services. The focus of Configuration Items is on their impact on delivering stable IT services and their relationships and dependencies with other CIs throughout an organization. The Configuration Management Database stores and manages information about CIs and their relationships.
-
An asset refers to any item that has value to an organization and can contribute to its financial status. The focus of assets is on their monetary value and management and IT Asset Management (ITAM) involves the lifecycle of the financial aspects of IT assets, such as procurement costs, maintenance, depreciation, and disposal.

Configuration Item types (and subtypes)
We’ve set out the criteria to define what a CI is in each organization, but you might still be wondering what this looks like exactly in real life. So, some typical CI categories and examples include:
Hardware CIs:
- Servers (both physical and virtual)
- Storage devices (disk arrays, storage area networks)
- IoT devices
- Network devices (routers, switches, and hubs)
- Voice equipment (PBXs and IVR systems)
- Printers and scanners
- End-user devices (laptops, desktops, mobile devices)
Software CIs:
- Operating Systems
- Business applications such as your Office suite
- Custom software applications
- Software licenses
- Middleware
- Utilities such as system backup tools and anti-virus software
Network CIs:
- IP addresses and subnets
- LAN, WAN, and VLAN information
- Firewalls
- Gateways
- Wireless access points
- Network bridges
- Network segments
- DNS (Domain Name System) configurations
Documentation CIs:
- User Manuals
- Design Specifications
- Configuration and Installation Guides
- Network Diagrams
- Process Documentation
- SLAs, OLAs, and XLAs
Facility Configuration Items:
- Data centers, comms rooms, and server rooms
- HVAC (Heating, Ventilation, and Air Conditioning) Systems
- Battery and backup systems, for example, UPS details
- Power Distribution Units (PDUs)
- Physical security systems
Supplier CIs:
- Vendor contracts and agreements
- Supplier information and contact details
- Information from your supplier and contracts database (if you have one)
Technical service CIs:
- Internal CIs (i.e., project assets)
- External CIs (i.e., customer agreements)
- Interface CIs (i.e., details how an end-to-end service is delivered through APIs and service provider interfaces)
Configuration item attributes
CI attributes are the characteristics that describe and define a specific CI within your IT infrastructure. Attributes provide details about the CI, its specifications, what makes it part of the service provision, and the relationships between them.
By clearly defining them in a CMDB, you have access to a map of how everything operates and relates with each other in your environment. This provides valuable information to support your IT functions.
Some common types of CI attributes include:
- Unique Identifier
- Name or label of the CI
- Brief description of the CIs purpose
- Type, for example, hardware, software, documentation
- Subtype, for instance. Server, finance application, network documentation
- Model or version number
- Support Details
- Vendor Details
- Owner
- Relationship to other CIs and services, for example, parent and child relationships
- Location (physical and logical)
- Status
- Cost and financial information
- Warranty information
- Security requirements, if appropriate
- CI abbreviations or acronyms

Configuration item lifecycle
The CI lifecycle refers to the stages a CI goes through within an organization's IT environment. Effective management ensures that CIs are properly managed, controlled, and maintained throughout their lifecycle in line with corporate requirements.
The process typically includes the following stages:
- Planning and design - Identifying the need for a new CI is the main part of the requirements-gathering exercise that kicks off the process.
- Acquisition and procurement - Procuring or creating the CI according to the design specifications.
- Identification and registration - Assigning the CI a unique identifier and registering it in the CMDB.
- In test environment - Ensuring that it functions as required and meets quality standards.
- Deployment - Releasing it to the production environment and made available to end users.
- Early life support - The warranty or settling-in period may include enhancing support levels and response times when a CI has been recently deployed to the live environment.
- Production environment - Performing the monitoring, management, maintenance, and updates required to keep the CI running effectively and efficiently.
- Retirement and disposal - When the CI is no longer needed, the retirement and disposal process involves ensuring any data is removed, redeploying any related software licenses and recycling or disposing any hardware components.
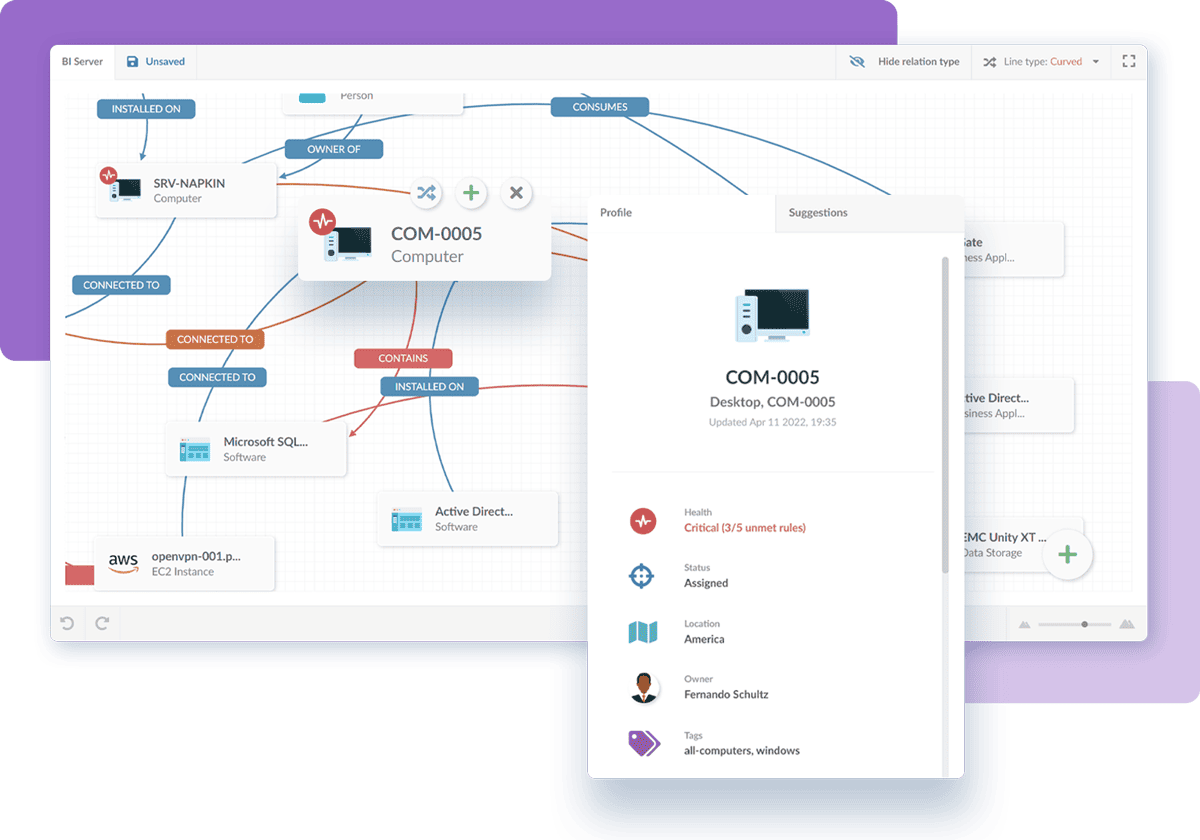
Configuration Item Management
It's time for more terminology! As we mentioned, the best way to stay on top of your practice is to incorporate a robust tool with specific Configuration Management features.
In this sense, CIs are managed most effectively in a CMDB or CMS environment, so let's take a minute to understand how this works:
- The CMDB is a database that stores configuration records throughout their lifecycle; which also maintains the relationships between configuration records. In other words, it captures the CIs that makeup IT systems and how they work together to deliver business services.
- The CMS is a set of tools, data, and information for Service Configuration Management. It can be made up of multiple CMDBs, asset databases, and knowledge information.
A CMDB or CMS is only as good as the data it contains, so it is good practice to create checkpoints within your Configuration Management activities to ensure your CI information is up to date and accurately reflects your IT environment. Some examples include:
- Ask your service desk analysts to categorize incidents and service requests using the CMDB. They can also update incorrect CI data when logging tickets.
- Ask support teams to raise changes with the impacted services flagged into the database.
- Ask your Change Enablement teams to impact assess change against the service information in the CMDB. You can also request success criteria that support Configuration Management; for example, a change can only be closed off as successful when the service information or CI is updated.
- Ask your Release Management teams to deploy releases based on CI information and check for accuracy.
- Ask your Problem Management team to use the CMDB to support problem and known error analysis.
- Ask your service catalog teams if the CMDB would be useful in identifying IT services.
- Work with your security teams to ensure that any security incidents are automatically linked to a CI so they can be managed more effectively.
- Automate what you can. With automation, CMDB processes ensure ongoing results through the automatic detection of changes on assets, configurations, and dependencies.
As you can see, building a CMDB is not a task you complete and then leave behind. On the contrary, it requires constant reviews and updates. During episode 68 of Ticket Volume - IT Podcast, Allex Dixon, an ITIL-trained professional with over two decades of IT experience across diverse industries, put it this way:
|
|
"A good CMDB isn’t static; it needs to rediscover, revalidate, and recapture data consistently. Manual methods are obsolete — automation is the only way to keep up with today’s dynamic IT environments." Allen Dixon |
What is a Configuration Management process?
A Configuration Management process involves identifying, recording, and maintaining information about the Configuration Items required to deliver IT services. The primary goal is to ensure that accurate and reliable information about CIs is available when needed.
This process is vital for maintaining service quality, managing changes effectively, and reducing risks associated with IT service disruptions. Configuration Management processes include activities such as:
-
Identification: Determining which items should be considered CIs and documenting them.
-
Control: Ensuring only authorized and identifiable CIs are accepted and recorded.
-
Status accounting: Tracking the status and history of each CI throughout its lifecycle.
-
Verification and audit: Regularly checking that CIs are recorded accurately and their configuration details reflect the actual state of the IT environment.
By implementing a robust Configuration Management process, organizations can achieve better oversight, facilitate efficient Incident Management, and support strategic decision-making.
What is a Configuration manager?
A Configuration manager is responsible for overseeing the Configuration Management process within an organization. This role involves ensuring that all CIs are identified, recorded, and maintained accurately to support IT Service Management.
The Configuration manager plays a crucial role in maintaining the integrity of the IT infrastructure and ensuring that configuration data is available and reliable.
Key responsibilities of a Configuration manager include:
-
Developing and implementing policies: Creating policies and procedures for Configuration Management to ensure consistency and compliance.
-
Managing the CMDB: Overseeing the Configuration Management Database to ensure it contains accurate and up-to-date information about all CIs.
-
Coordinating with other teams: Collaborating with IT, service desk, change management, and other teams to ensure that configuration data is used effectively and kept current.
-
Conducting audits and reviews: Regularly auditing the CMDB and Configuration Management process to identify discrepancies and areas for improvement.
-
Providing training and support: Educating team members about Configuration Management practices and the importance of accurate CI data.
The role of a Configuration manager is vital in maintaining the stability and efficiency of IT services, enabling better Risk Management, and supporting organizational growth.
How to manage CIs on InvGate Asset Management
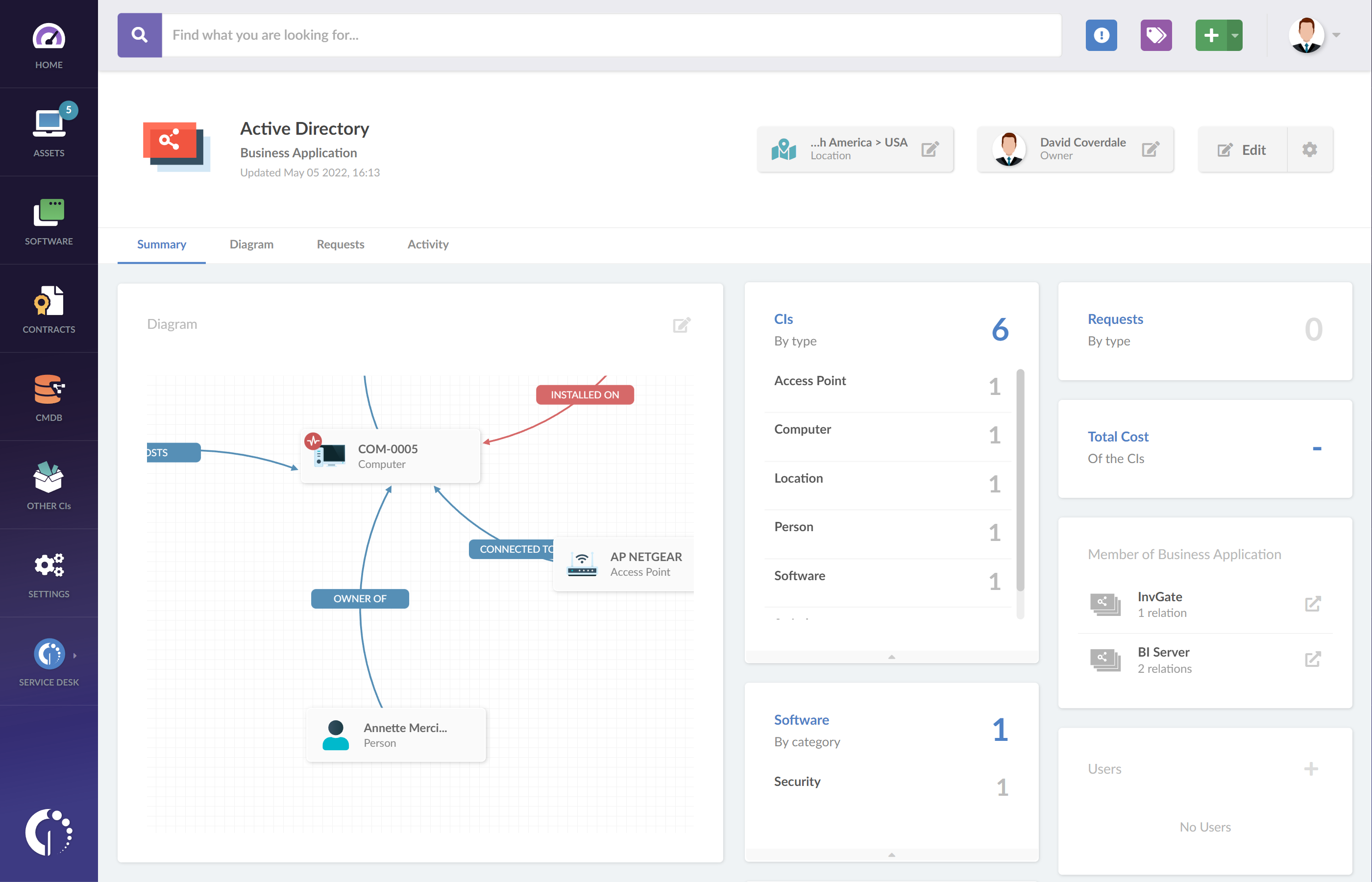
So, let’s see how ITAM software can streamline this process. On InvGate Asset Management, Configuration Items are tracked and managed through the CMDB feature.
The first thing you have to do is incorporate your CIs into the system. This can take the following formats:
- Assets: Installing an Agent, through the Network Discovery feature, or by uploading a .csv file.
- Users: Creating them in Settings >> General >> Users or by integrating the tool with Active Directory or Microsoft Entra ID (formerly Azure Active Directory).
- Locations: Creating them in Settings >> General >> Locations.
- Contracts: Creating them in New CI >> Contract >> Assets.
Apart from the individual CIs that make up your environment, you can also map out their relationships by creating Business Applications. These are groups of related CIs that serve a purpose together. InvGate Asset Management provides you with an intuitive diagram editor to visually represent them on your instance.
And there you go. In the CMDB section you will find all the relevant information regarding your CIs, including a comprehensive map with statistics and activity information.

In short
Each organization defines its own Configuration Items depending on what they consider necessary to run their IT services successfully. This includes assets, but also locations, users, documentation, suppliers or any other relevant IT information.
These components are usually managed in the CMDB that maps out the CIs and their relationships to make sure you can keep track of them throughout their lifecycle. But you can’t do this without the right tool that incorporates Configuration Management processes.
So, if you’re ready to level up your IT Management, you can try InvGate Asset Management’s 30 day free trial (no strings attached) and see it for yourself.
Frequently Asked Questions (FAQs)
What information does the CMDB contain for Configuration Items?
The attributes and relationship information comprise the services that deliver value to the organization.
Can people be a configuration item?
Yes - people and roles can be CIs.
What is an example of a Configuration Item?
Hardware, software, or network equipment.















