The Cybersecurity and Infrastructure Security Agency (CISA) issued the Binding Operational Directive (BOD) 23-02 to mitigate the risks of internet-exposed management interfaces. For federal civilian agencies particularly, complying with this directive is not merely an operational necessity; it's a strategic imperative for securing their information systems.
Keep reading to fully understand the CISA’s BOD 23-02 implications, and learn how InvGate Asset Management can help you comply with it.
What does CISA’s BOD 23-02 say?
CISA’s BOD 23-02 requires federal civilian agencies to remove specific networked management interfaces from the public-facing internet. It also mandates the need to implement Zero Trust Architecture capabilities that enforce access control to the interface within 14 days of discovery.
Apart from this, agencies have to ensure that all management interfaces on existing and newly added devices have at least one of the following protections in place:
- The interface is removed from the internet by making it only accessible from an internal enterprise network.
- The interface is protected by capabilities, as part of a Zero Trust Architecture, that enforces access control to the interface through a policy enforcement point separate from the interface itself.
“Networked management interfaces” refer to all dedicated device interfaces that are accessible by network protocols. They are built exclusively for authorized users to perform administrative activities on a device, a group of devices, or the network itself. Some examples are routers, switches, firewalls, VPN concentrators, and proxies, among others.
The reason for this new requirement is that Government agencies are among the most targeted sectors by cyber attacks. In this scenario, device management interfaces that are directly connected to the public-facing internet are the most risky, and thus CISA’s BOD 23-02 aims to reduce this attack surface.
Mitigating the risk of internet-exposed management interfaces
InvGate Asset Management comes with Discovery, inventory, and reporting features that allow you to have comprehensive visibility into your agency's network infrastructure. Specifically, it allows you to identify devices with internet-exposed management interfaces that fall under the directive's purview.
Let’s see how you can do it.
1. Identify network-connected devices
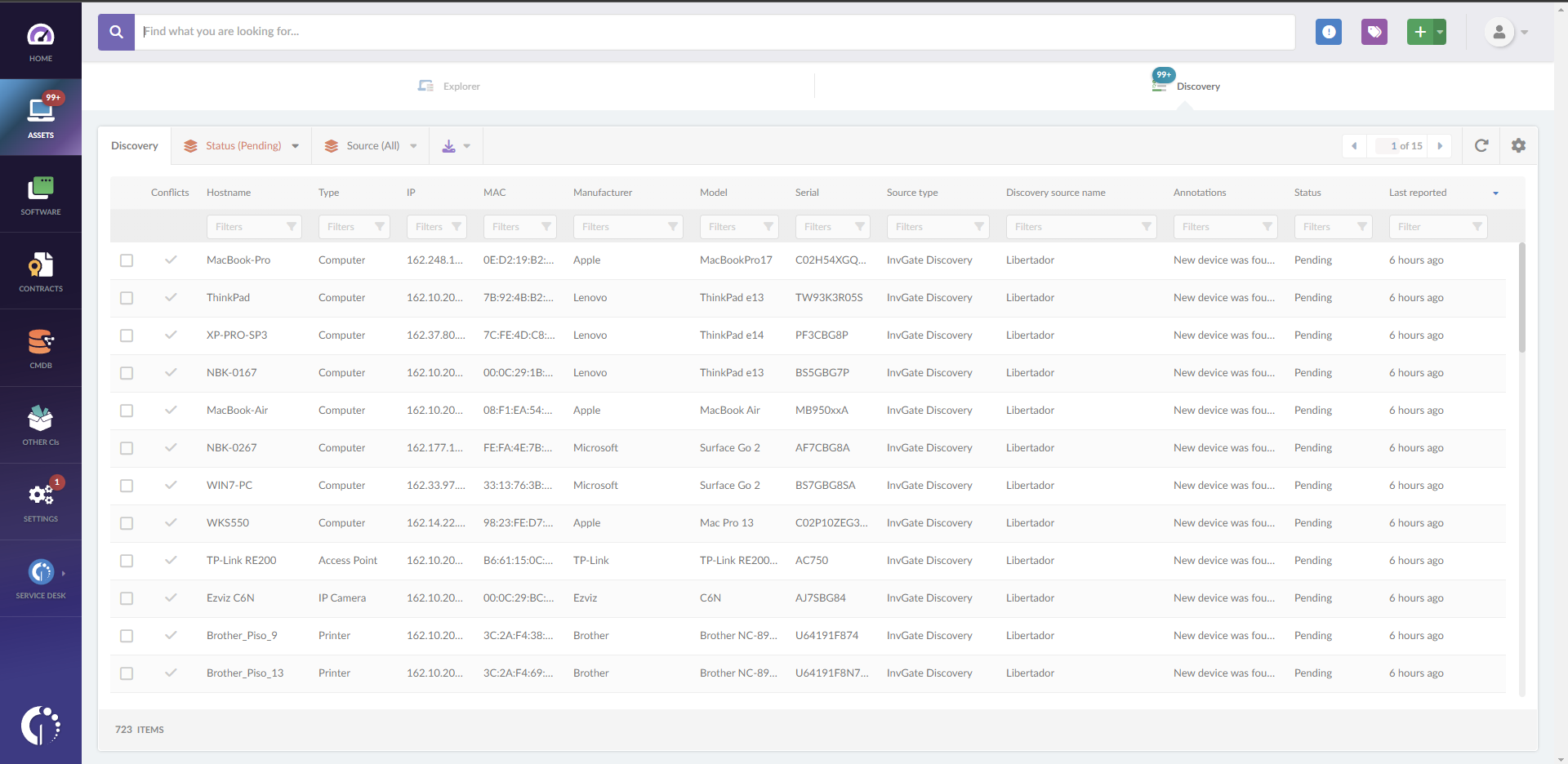
Before taking action, you need to identify which devices fall under the domain of the directive. To do this, InvGate Asset Management’s Network Device Discovery scans all networked devices within your IT infrastructure. This includes routers, firewalls, proxies, and load balancers.
2. Manage your inventory

Once you have detected the devices in your network, it’s time to effectively add them to your IT inventory (and, thus, keep them under your vigilance). This allows you to track and manage the networked devices and their associated configurations, providing a holistic view of the assets within your control.
This is critical to spot any misconfigurations or insecure settings that may pose security risks, enabling immediate action and remedy. To do this, you can set Risk Management Automation tools, such as Smart Tags and Health Rules. They will notify you when assets are not in compliance with the directive.
Basically, a precise inventory of your networked devices (that includes an updated status of your devices) will make sure you have a clear understanding of which devices need securing or protecting. This way, you can act as soon as possible, mitigating the consequences.
3. Create reports
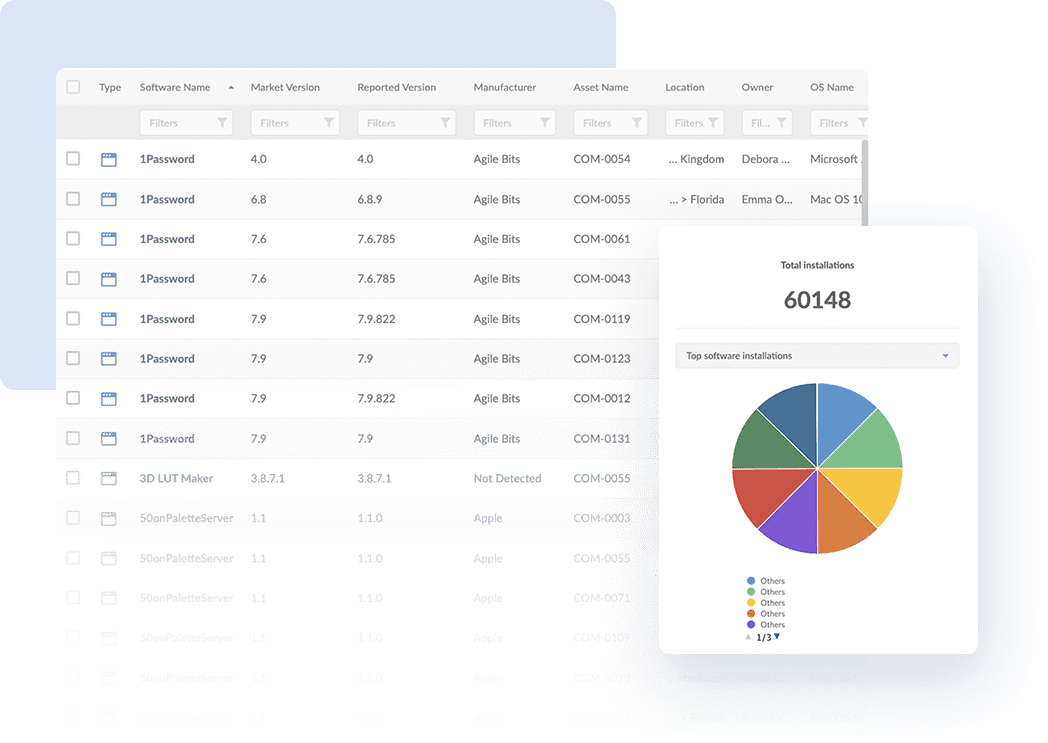
Finally, robust reporting and analytics capabilities generate comprehensive reports on device status, compliance, vulnerabilities, and remediation efforts. Once you have implemented the corresponding protectors, create reports to get a clear overview of the agency's cybersecurity posture.
How can ITAM software help federal civilian agencies to stay compliant
InvGate Asset Management was created as a complete IT Asset Management (ITAM) tool. Hence, it will provide you with much more than what we just covered. In particular, you’ll be adding the following capabilities:
- Unified IT infrastructure visibility - An up-to-date inventory of all your assets on a single platform gives you a deeper understanding of how your systems and processes integrate, enabling optimization of operations, and reducing downtime.
- Hardware and Software License Management - Licenses offer full visibility of usage and assigned licenses, aiding in informed purchasing decisions, and security and compliance Risk Management.
- Streamlined Contract Management - The platform simplifies contract management by keeping an organized record of your organization's IT contracts. This aids IT budgeting, decision-making on renewals and future investments, and compliance with contractual obligations.
- Enhanced CMDB - This is key for you to map relationships between assets and business services with a visual CMDB data model, giving a clear view of your Configuration Items (CIs) and their interconnections.
In short
From now on, federal civilian agencies are compelled to reduce the risks of internet-exposed management interfaces within a 14-day timeframe to stay in compliance with CISA’s BOD 23-02. To that end, you can leverage ITAM software. This can be done by removing specific networked management interfaces from the public-facing internet or implementing Zero Trust Architecture capabilities.
In the same way as InvGate Asset Management helped U.S. agencies to comply with the White House's executive order on Inventory Management, this time, its Discovery, inventory, and reporting features are helpful to address CISA’s BOD 23-02 and, at the same time, enhance overall IT governance. After all, a safe environment means both external compliance and streamlined and uninterrupted operations for your organization.
Book a meeting with our team today to schedule a personalized demo. Our experts are ready to walk you through how our tool can improve your ITAM processes, ensure regulatory compliance, and deliver value across your organization.















