We don’t want you to panic (yet), and this is probably something you already know, but risks are everywhere. From operational hiccups to cyber threats and surprise market shifts, organizations are constantly dealing with uncertainties that could derail their goals. That’s why Risk Management isn’t just another task on the to-do list—it’s the foundation for staying on track. And in 2025, there’s a game-changer in the field: Risk Management automation.
Here’s why it matters. According to the Cost of a Data Breach report, the average cost of a data breach has soared by 10% in 2024, now hitting a staggering $4.88 million. This is where Risk Management automation steps in. By streamlining processes, minimizing manual errors, and delivering real-time responses to threats, it empowers organizations to stay ahead of the curve.
And we're certain that you've already automated quite a lot of your IT Asset Management (ITAM) processes – we're just not sure if you’ve sorted this one out yet. For that reason, we're about to show you how to use certain features on InvGate Asset Management in your favor to close some gaps and avoid risking the safety of your devices.
In this article, we’ll explore how automating your Risk Management efforts can transform the way you identify, analyze, and mitigate risks. Ready to see how it works? Let’s jump in!
What is automation in Risk Management?
Risk Management automation is the use of advanced software and algorithms to simplify how organizations identify, analyze, and mitigate risks in real time. Instead of relying on manual, time-consuming tasks, automation streamlines risk processes, providing instant insights into potential threats and vulnerabilities.
It’s all about proactive support and staying ahead of the game by automating tasks like data collection, risk analysis, and reporting—saving your team from tedious work and helping your organization avoid costly disruptions. Think of it as your secret weapon for smarter, faster, and more efficient Risk Management.

5 benefits of automating Risk Management
Adopting Risk Management automation offers a wide range of benefits that can transform your organization’s approach to mitigating risks. These benefits aren’t just theoretical—they’re transformative in practice.
By automating your Risk Management processes, your organization can streamline risk identification, minimize vulnerabilities, and empower your team to tackle the most pressing Risk Management needs effectively. Here’s how automation can make a difference:
#1: Continuous monitoring and proactive responses
Automated systems work around the clock to monitor risks in real time and send alerts for immediate action. Whether it’s flagging non-compliant software, outdated firewalls, or devices without antivirus protection, these systems help identify potential risks before they escalate. With continuous monitoring, your organization can stay one step ahead of emerging threats and maintain a strong security posture.
#2: Minimized human error
Manual processes are prone to mistakes caused by fatigue, oversight, or inconsistencies. Automation eliminates these risks by streamlining tasks like data collection, risk analysis, and reporting. By reducing human error, your team can focus on strategic risk mitigation strategies without worrying about inaccuracies.
#3: Enhanced alignment with modern risk strategies
In today’s risk landscape, automation is a cornerstone of modern cybersecurity and compliance processes. Automated systems not only detect vulnerabilities but also align with proactive approaches like real-time risk assessments and predictive modeling to address potential threats before they become issues. This ensures that your organization keeps pace with emerging risks and stays compliant.
#4: Scalability for complex risk scenarios
Managing risk in large, dynamic environments is no small feat, especially when dealing with a growing number of devices, systems, and business processes. Automation provides the scalability to handle complex risk scenarios efficiently, reducing workloads for Risk Management teams and allowing for better prioritization of key risk indicators.
#5: Operational efficiency with human oversight
Not every risk can (or should) be handled automatically. Automated systems excel at identifying and addressing routine risks, but when larger, more complex threats arise, they can escalate the issue to risk professionals for further assessment. This ensures a balance between operational efficiency and the critical human intervention needed for effective Risk Management automation.

Standardized automated Risk Management process
Automating Risk Management follows a logical sequence of steps to ensure that risks are effectively identified, assessed, prioritized, and mitigated. These steps align with widely recognized frameworks such as ISO 31000, the NIST Risk Management Framework, and COBIT, making them applicable to any organization regardless of size or industry.
Step 1: Identify potential risks
The first step in Risk Management is understanding your organization’s risk landscape. This involves identifying risks associated with your IT infrastructure, business processes, and operational activities. Key activities include:
- Conducting a risk assessment to identify vulnerabilities.
- Collecting data from assets, processes, and systems to uncover potential threats.
- Leveraging tools to monitor and log emerging risks, such as cyber threats or compliance gaps.
Step 2: Monitor continuously
Risks aren’t static—they evolve with new technologies, regulations, and operational changes. Continuous monitoring ensures that emerging threats are caught early and addressed promptly. Key activities include:
- Setting up systems for continuous monitoring of key risk indicators (KRIs).
- Using automation tools to track changes and generate alerts in real time.
- Keeping an eye on historical data to identify trends and patterns.
Step 3: Prioritize and evaluate risks
Not all risks carry the same level of urgency. Prioritizing risks based on their likelihood and potential impact helps focus resources where they’re needed most. Key activities include:
- Assigning risk scores based on severity and probability.
- Using advanced analytics to predict the consequences of specific risks.
- Developing a risk matrix to categorize and rank risks.
Step 4: Act on identified risks
Once risks are prioritized, the next step is mitigation. This involves creating and implementing risk mitigation strategies tailored to the nature and scale of the threat. Key activities include:
- Automating routine mitigation actions, such as patching vulnerabilities or updating configurations.
- Escalating complex risk scenarios to human teams for further assessment.
- Developing clear incident response plans for high-priority threats.
Step 5: Review and refine the process
Risk Management is not a one-time activity. Regular reviews ensure that processes adapt to emerging threats, changes in the business environment, and lessons learned from past incidents. Key activities include:
- Conducting regular risk assessments to reassess priorities.
- Reviewing the performance of automated systems to ensure accuracy.
- Updating processes to reflect the current risk landscape.
How to use InvGate Asset Management as your automated Risk Management tool
By now, it’s clear that automating Risk Management practices is essential for safeguarding your organization against potential risks. InvGate Asset Management provides two powerful tools—Health Rules and smart tags—that simplify monitoring, categorization, and response to risks.
These features, combined with robust IT asset monitoring and alerting capabilities, ensure you can identify and mitigate risks efficiently.
Health Rules
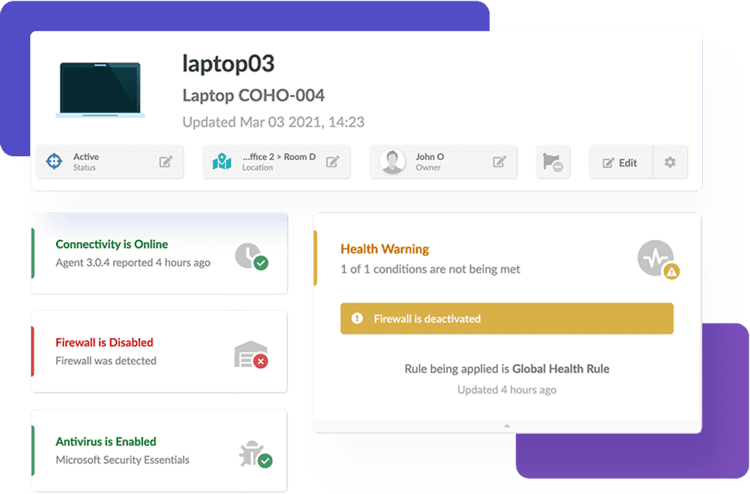
Health Rules enable automated assessments of your assets’ compliance and operational health. They monitor critical risk factors such as:
- Firewall and antivirus status.
- Disk space availability.
- Encryption settings.
- Warranty expiration.
- Time since the last OS update.
These rules operate based on customizable parameters and use a color-coded system to visually represent an asset's status:
- Green: Assets are compliant and functioning properly.
- Yellow: A warning indicates potential risk.
- Red: Immediate action is needed due to a critical issue.
Additionally, Health Rules are seamlessly integrated into InvGate’s alerting system. When an asset breaches a predefined threshold, automated alerts notify your team instantly. These notifications can be customized to your organization’s requirements, ensuring the right people are informed at the right time.
Smart Tags
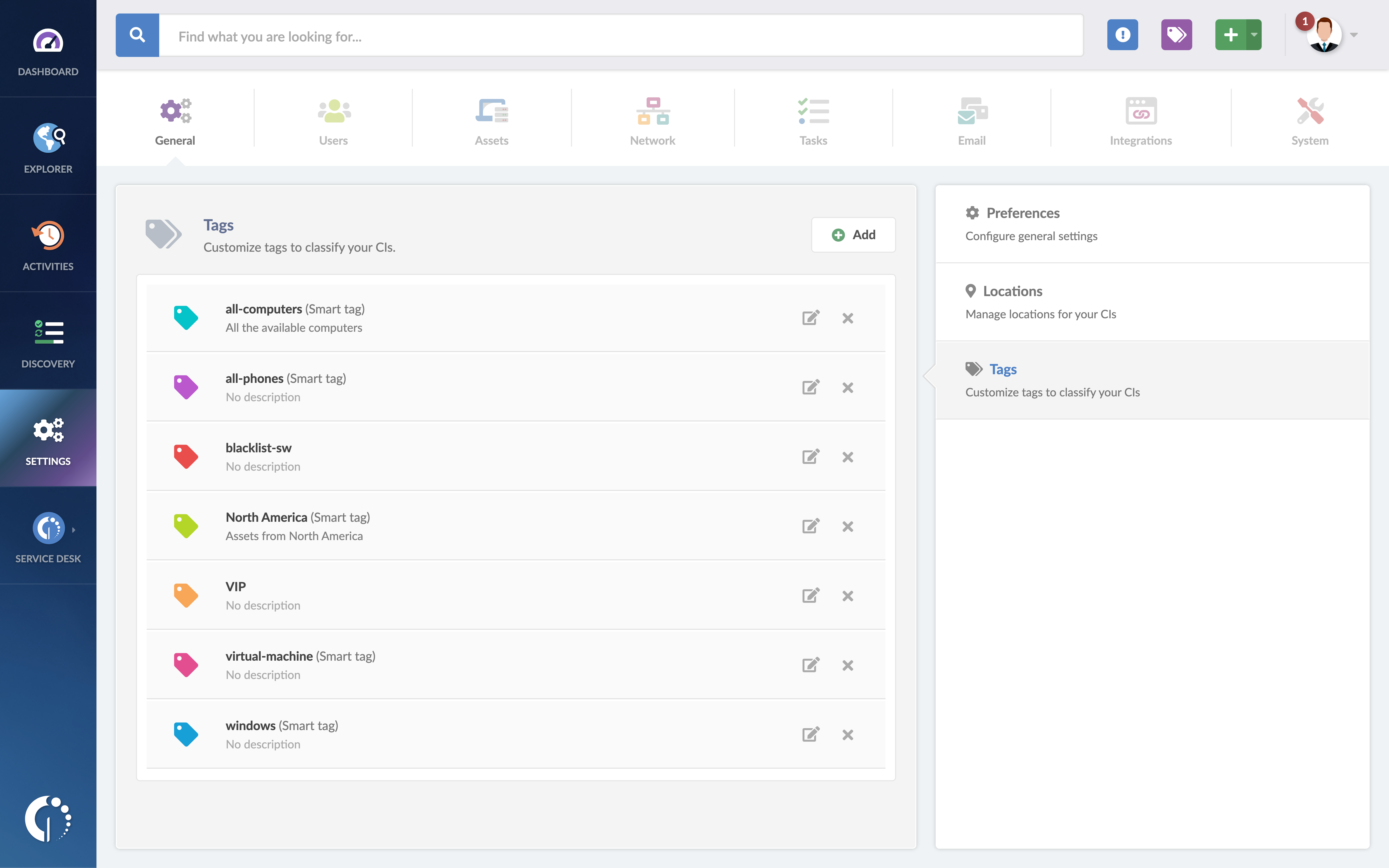
Smart tags automatically label and categorize Configuration Items (CIs)—including devices, users, and software—based on risk-related criteria. Once you configure these labels (which can be personalized to your needs), you can quickly search them in your inventory to see all the assets that match the selected criteria. With segmented information, it's easy to understand what's in danger, and what actions are required.
This feature enables:
- Asset segmentation: Organize assets by categories like “missing antivirus” or “outdated software” to identify problem areas quickly.
- Streamlined queries: Easily locate groups of high-risk assets and prioritize mitigation efforts.
- Custom parameters: Define specific conditions to ensure tags reflect the most up-to-date information.
Setting up smart tags is simple:
- Navigate to Settings >> General >> Tags to create a new tag.
- Fill in the required fields (name, description, and color) for easy identification.
- Set the parameters that will automatically trigger the tag.
Once configured, smart tags dynamically update, helping you focus your efforts where they matter most.
3 Risk Management automation examples
Risk Management automation processes cover a wide range of tasks and potential issues. If you’re new to this or if you just want to see a few extra ideas, these three examples of Risk Management automation in action can come in handy:
Endpoint Management
By automating Endpoint Management, you can establish a baseline for what is considered "risky" behavior on workstations and equipment used by teams on a daily basis to keep an eye on it.
You can set InvGate Asset Management’s Health Rules to continuously monitor factors such as installed applications, firewall settings, antivirus status, and warranty status, among others. This way you can proactively detect and respond to potential risks and deviations from established security protocols.
Compliance Management
Furthermore, InvGate Asset Management offers robust capabilities for managing compliance standards. You can automate the tagging of devices that must adhere to specific compliance requirements, such as the Payment Card Industry Data Security Standard (PCI DSS).
InvGate Asset Management enables automated tracking and verification of factors including security configurations, encryption, and software versions, ensuring ongoing compliance and facilitating streamlined auditing processes.
Network tracking
In the realm of network tracking, InvGate Asset Management monitors and analyzes device connectivity to your organization’s network infrastructure, including Virtual Private Networks (VPNs).
By automatically capturing and analyzing IP addresses and associated device information, your team can maintain visibility into network connections. Suspicious or unauthorized devices attempting to connect can be quickly identified and investigated, enabling timely response to potential security threats or policy violations.
To sum up
Risk Management automation is no longer optional—it's essential for effectively mitigating risks and protecting your IT assets. By adopting automation, you can identify vulnerabilities, streamline processes, and proactively address risks before they escalate into costly issues.
With InvGate Asset Management, you have a powerful ally to tackle this challenge. Its customizable tools, like Health Rules and Smart Tags, offer:
- Real-time monitoring to ensure your assets remain healthy and compliant.
- Effortless classification of Configuration Items (CIs) based on predefined parameters.
- Proactive alerts to notify your team about risks requiring immediate action.
Whether you're managing endpoints, ensuring compliance, or monitoring network activity, InvGate Asset Management empowers you to take charge of your organization's risk landscape.
So, to start implementing Risk Management automation, ask for InvGate Asset Management’s 30-day free trial!
Frequently Asked Questions
1. How does automation affect Risk Management?
Automation improves Risk Management by increasing efficiency, accuracy, and real-time monitoring, enabling proactive risk mitigation and reducing human error.
2. What are automated risk tools?
Automated risk tools are software solutions that streamline Risk Management processes, such as data analysis, reporting, compliance tracking, and decision support, enhancing overall risk assessment and mitigation capabilities.
3. Can risk assessment be automated?
Yes, risk assessment can be automated using advanced software tools. These tools streamline data collection, identify potential threats, analyze vulnerabilities, and assign risk scores in real time. Automation reduces human error and provides continuous monitoring to ensure risks are assessed as they evolve.
4. What is the best Risk Management software?
The best Risk Management software depends on your organization’s needs. For IT Asset Management and Risk Management automation, InvGate Asset Management is a top choice. It offers tools like Health Rules for compliance monitoring and Smart Tags for asset categorization, making it easier to manage risks proactively. Request a demo to see how it can fit into your organization.