Imagine walking into a company office where every door is equipped with a state-of-the-art lock, but a few old keys still lurk in forgotten drawers. These keys, left behind by former employees, can easily fall into the wrong hands, putting the entire organization at risk.This scenario is not just a figment of imagination but a stark reality in the digital world, where orphan accounts serve as these forgotten keys, granting access to sensitive systems and data long after their rightful owners have left. So, understanding and managing orphan accounts is crucial to safeguarding your organization's security and integrity.
In this comprehensive guide, we will dive deep into the concept of orphan accounts, exploring how they occur, the significant risks they pose, and the best practices for identifying and eliminating them. Whether you’re an IT professional striving to tighten security protocols or a business leader aiming to protect your assets, this article will equip you with the knowledge and tools needed to tackle orphan accounts effectively.
So, read on to fortify your defenses and ensure your organization's digital doors are securely locked against potential threats.

Orphan account meaning
Let's begin from the start: The orphan account meaning. In a nutshell, an orphan account is a user account that remains active despite its owner no longer being part of the organization. This situation often arises when employees leave without their access being properly revoked. Orphan accounts can also occur through system migrations or when roles change within an organization without corresponding updates to user permissions.
Orphan accounts pose significant security risks. They can be exploited by malicious actors to gain unauthorized access to systems and data.
This threat is especially severe in industries dealing with sensitive information, such as healthcare, finance, and government sectors. In addition, orphan accounts can lead to regulatory compliance issues, where organizations may face hefty fines and legal repercussions for failing to safeguard sensitive data properly.
Managing orphan accounts is essential for maintaining a secure IT environment and ensuring compliance with security policies and regulations. Organizations need to implement robust Identity and Access Management (IAM) practices to detect and mitigate the risks associated with orphan accounts.
Regular audits, automated IAM solutions, and clear communication channels between Human Resources and IT departments are crucial for effective orphan account management.
How do orphan accounts occur?
Orphan accounts can occur due to several reasons. One common cause is inadequate offboarding processes. When employees leave, their accounts are not always promptly deactivated, leading to potential security vulnerabilities. Often, the offboarding process lacks a systematic approach, resulting in gaps that allow accounts to remain active long after the user has left.

Another reason is mergers and acquisitions. During these events, user accounts from different systems must be integrated. If this process is not meticulously managed, it can result in orphan accounts. The complexity of merging systems, combined with differing IT practices and cultures, can lead to oversights where certain accounts are forgotten or improperly configured.
Lastly, poor Identity and Access Management (IAM) practices can lead to orphan accounts. Organizations that do not regularly audit and update their user permissions and accounts are more likely to have orphan accounts lurking in their systems. Without continuous monitoring and review, it's easy for accounts to slip through the cracks, especially in large organizations with numerous employees and access points.
Moreover, organizational changes such as restructuring, departmental shifts, or changes in employee roles can also contribute to the creation of orphan accounts. When roles and responsibilities are modified, associated access permissions should be updated accordingly. However, without a robust process in place, these changes can result in orphan accounts that pose significant security risks.
How does an account become an orphan account?
An account becomes an orphan account when its user leaves the organization, and their access credentials remain active. This can happen due to oversight during the offboarding process. HR and IT departments must coordinate to ensure that departing employees' access is promptly revoked. Failing to do so leaves a loophole that can be exploited by unauthorized individuals.
Accounts can also become orphaned if there is a lack of communication between different departments. For instance, if IT is not informed about role changes or terminations, accounts might remain active unnecessarily.
Regular audits and clear communication channels can prevent these lapses. Additionally, automated IAM systems can help by flagging accounts that show no activity for extended periods, prompting a review.
Another way accounts become orphaned is through system migrations or upgrades. During these processes, some accounts might not be correctly transferred or might be duplicated, leading to orphaned accounts. Ensuring meticulous planning and execution during system migrations can help prevent such occurrences.
Furthermore, contractors or temporary employees often contribute to the creation of orphan accounts. When their contracts end, and there is no process to deactivate their accounts, these accounts become orphaned. Organizations must have clear procedures for managing the accounts of non-permanent staff to mitigate this risk.
What are the risks of orphan accounts? Top 8 risks
Orphan accounts pose numerous risks to an organization. Here are the top eight:
- Unauthorized access: orphan accounts can be exploited by attackers to gain unauthorized access to sensitive data and systems.
- Data breaches: Active orphan accounts increase the likelihood of data breaches, compromising confidential information.
- Regulatory non-compliance: Orphan accounts can lead to non-compliance with data protection regulations, resulting in fines and legal issues.
- Insider threats: Former employees with active accounts can intentionally or unintentionally cause harm to the organization.
- Resource drain: Maintaining orphan accounts consumes IT resources that could be better utilized elsewhere.
- Inaccurate audits: Orphan accounts can skew audit results, making it difficult to accurately assess security posture.
- Operational inefficiency: Orphan accounts clutter the system, making it harder to manage and maintain.
- Financial losses: Data breaches and regulatory fines resulting from orphan accounts can lead to significant financial losses.
1. Unauthorized access
Orphan accounts are a gateway for unauthorized access. Attackers can exploit these accounts to infiltrate systems and access sensitive information without detection. Since these accounts often go unnoticed, they provide a covert entry point for malicious activities, making it difficult for security teams to detect and respond to breaches promptly.
Moreover, once inside the system, attackers can escalate privileges, move laterally within the network, and access even more critical resources. This can lead to a widespread compromise, affecting various parts of the organization. The consequences of unauthorized access through orphan accounts can be devastating, leading to significant data loss and operational disruptions.
To mitigate this risk, organizations should implement stringent access control measures, regularly review and update user permissions, and employ advanced threat detection mechanisms. Continuous monitoring and proactive management of user accounts are essential to prevent unauthorized access through orphan accounts.
2. Data breaches
With orphan accounts active, the risk of data breaches escalates. These accounts can be used to extract confidential data, leading to significant security incidents. Data breaches can result in the exposure of sensitive information such as customer data, financial records, and proprietary business information, causing irreparable damage to the organization’s reputation and trust.
The cost of a data breach extends beyond immediate financial losses. Organizations may face regulatory fines, legal actions, and loss of customer confidence. Recovering from a data breach involves not only financial expenditures but also extensive efforts to rebuild trust and secure systems.
To reduce the risk of data breaches, organizations should prioritize the identification and elimination of orphan accounts. Implementing robust encryption, access controls, and regular security audits can help safeguard sensitive information from unauthorized access and potential breaches.
3. Regulatory non-compliance
Orphan accounts can result in regulatory non-compliance. Data protection laws mandate strict access controls, and failure to manage orphan accounts can lead to hefty fines and legal challenges. Regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA) require organizations to ensure the security and confidentiality of personal data.
Non-compliance with these regulations can have severe consequences, including financial penalties and damage to the organization’s reputation. Regulatory bodies impose stringent requirements on data access management, and orphan accounts pose a significant compliance risk if not properly managed.
To achieve compliance, organizations must establish comprehensive access management policies, conduct regular audits, and implement automated solutions to identify and eliminate orphan accounts.
Ensuring compliance with data protection regulations is not only a legal obligation but also a critical aspect of maintaining customer trust and business integrity.

4. Insider threats
Orphan accounts can be exploited by former employees to gain access to organizational resources. This insider threat can result in data theft or sabotage. Disgruntled ex-employees with active accounts can intentionally cause harm, while others might inadvertently misuse access, leading to security incidents.
Insider threats are particularly challenging to detect and mitigate because they originate from individuals who were once trusted members of the organization. Orphan accounts provide a convenient entry point for such threats, allowing insiders to bypass security measures and access sensitive information.
To mitigate insider threats, organizations should implement strict offboarding procedures, conduct thorough background checks, and employ behavioral analytics to detect unusual activities. Regularly reviewing and deactivating orphan accounts is crucial to preventing insider threats and protecting organizational assets.
5. Resource drain
Maintaining orphan accounts unnecessarily consumes IT resources. These accounts require monitoring and management, diverting resources from more critical tasks. IT teams must spend valuable time and effort tracking, auditing, and securing these accounts, which could otherwise be directed towards strategic initiatives and improving overall system performance.
Orphan accounts also contribute to system clutter, making it harder to manage and maintain user accounts. This clutter can lead to inefficiencies in user provisioning, access control, and overall IT operations. Reducing the number of orphan accounts streamlines user management processes and allows IT teams to focus on more impactful activities.
To address this issue, organizations should invest in automated identity and Access Management solutions that can identify and deactivate orphan accounts efficiently. Streamlining Account Management processes improves operational efficiency and frees up resources for more strategic endeavors.
6. Inaccurate audits
Orphan accounts can distort audit results. Their presence can make it challenging to get an accurate picture of the organization’s security posture. Auditors rely on accurate data to assess the effectiveness of security controls and identify potential vulnerabilities.
Orphan accounts introduce discrepancies in audit trails, making it difficult to track user activities and access patterns. This can lead to false positives or negatives during security assessments, undermining the reliability of audit findings.
To ensure accurate audits, organizations should conduct regular reviews of user accounts, update access permissions, and eliminate orphan accounts. Maintaining a clean and well-documented account management system is essential for reliable audits and effective security assessments.
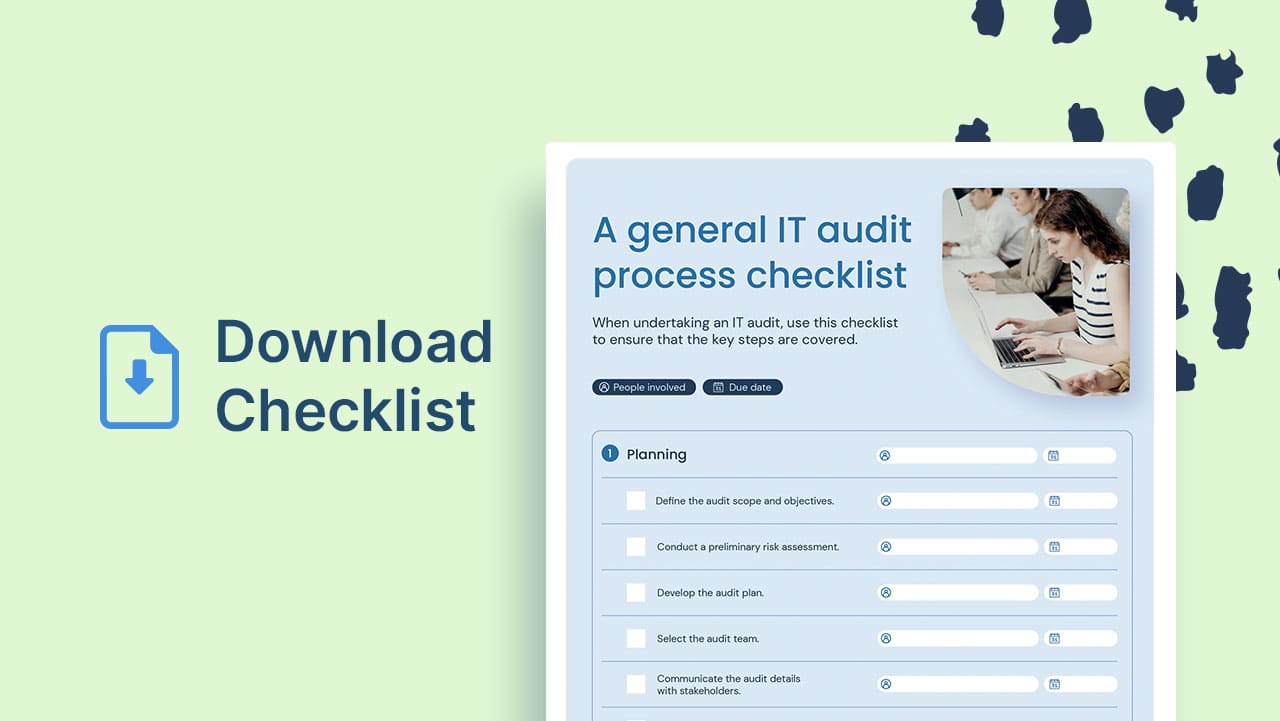
7. Operational inefficiency
Orphan accounts contribute to system clutter. This clutter complicates user management and can lead to inefficiencies in IT operations. With numerous inactive accounts lingering in the system, IT teams face challenges in managing user access, provisioning new accounts, and maintaining overall system integrity.
Operational inefficiencies resulting from orphan accounts can slow down business processes, delay project timelines, and increase the risk of errors. Streamlining user account management processes enhances operational efficiency and ensures that IT resources are used effectively.
Implementing Automated Account Management solutions and conducting regular audits can help identify and eliminate orphan accounts, reducing system clutter and improving overall operational efficiency. A well-organized and streamlined Account management System supports smoother IT operations and enhances organizational productivity.
8. Financial losses
Orphan accounts can lead to financial losses. Data breaches, regulatory fines, and operational inefficiencies can all translate into significant costs for the organization. The financial impact of security incidents involving orphan accounts can be substantial, affecting the organization’s bottom line and long-term viability.
In addition to direct financial losses, organizations may incur costs related to incident response, legal actions, and remediation efforts. The reputation damage resulting from security breaches can also lead to a loss of customers and revenue.
To mitigate financial losses, organizations must prioritize the identification and elimination of orphan accounts. Implementing robust security measures, conducting regular audits, and investing in advanced IAM solutions can help prevent security incidents and minimize financial risks.
Anonymous vs orphan account: What's the difference?
An anonymous account is a user account that does not require user identification or credentials for access. These accounts are often used for guest access or public resources. While convenient, anonymous accounts can pose security risks if not properly managed.
Anonymous accounts allow users to access certain resources without the need to authenticate themselves. This can be useful in scenarios where access needs to be granted to a wide audience without individual user management. However, the lack of user identification makes it challenging to track activities and enforce security policies.
In contrast, an orphan account is tied to a specific user who is no longer part of the organization. Unlike anonymous accounts, orphan accounts have a direct association with an individual's former role and permissions. This makes them particularly dangerous if not deactivated.
Orphan accounts retain the access permissions and privileges of the former user, allowing potential misuse by unauthorized individuals. The specific association with a user and their role makes orphan accounts a more targeted security risk compared to anonymous accounts.
Understanding the distinction between these account types is crucial for effective IT Security Management. Both require different handling and mitigation strategies to ensure organizational security. While anonymous accounts need controlled access and monitoring, orphan accounts require prompt identification and deactivation to prevent unauthorized access and security breaches.
How to discover orphan accounts
Discovering orphan accounts requires a systematic approach. Start with regular audits of all user accounts across the organization. Identify accounts that have not been accessed for extended periods and verify their status with the respective departments.
Utilize automated tools for identity and access management (IAM). These tools can help track user activity and flag accounts that might be orphaned. Automated solutions streamline the discovery process and reduce the likelihood of human error. Implementing IAM solutions with machine learning capabilities can enhance the accuracy and efficiency of identifying orphan accounts.
Engage in thorough communication with HR and departmental managers. Ensure that IT is promptly informed of any employee departures or role changes. This proactive approach helps identify orphan accounts before they become a security risk. Regularly updating the HR and IT databases with accurate information about employee status and roles is essential for effective account management.
Consider implementing a formal offboarding process that includes a checklist of actions to be taken when an employee leaves the organization. This checklist should include account deactivation, removal of access privileges, and updating relevant systems to reflect the change. Regularly review and update the offboarding process to ensure it remains effective and aligned with organizational needs.
How to eliminate orphan accounts
Eliminating orphan accounts involves several steps. Begin with a comprehensive audit to identify all orphan accounts. Cross-reference these accounts with HR records to confirm their orphan status. Ensure that the audit process includes both current and historical user accounts to capture all potential orphan accounts.
Once identified, promptly deactivate or delete these accounts. Ensure that all associated permissions and access rights are revoked. This prevents unauthorized access through these accounts. Consider implementing automated workflows to streamline the deactivation process and reduce the risk of human error.
Implement a robust offboarding process. Coordinate between HR and IT to ensure that all departing employees’ accounts are deactivated immediately. Regularly review and update this process to adapt to any organizational changes. Including periodic training sessions for HR and IT staff can help reinforce the importance of timely account deactivation and ensure consistent application of the offboarding process.
In addition to deactivating accounts, consider implementing policies for the regular review and recertification of user access permissions. This involves periodically verifying that active accounts still require the access privileges they have been granted. Implementing this practice can help identify and eliminate orphan accounts and other potential security risks.

Final thoughts
Orphan accounts represent a significant security risk that organizations cannot afford to ignore. By understanding how these accounts occur and the risks they pose, organizations can take proactive steps to mitigate potential threats.
Regular audits, effective communication, and automated tools are essential in discovering and managing orphan accounts. By incorporating these practices, organizations can enhance their security posture and ensure compliance with regulatory standards.
Taking a proactive approach to orphan account management not only strengthens security but also improves operational efficiency. It’s a vital aspect of maintaining a secure and resilient IT environment. By addressing the issue of orphan accounts, organizations can protect their sensitive data, maintain regulatory compliance, and minimize the risk of costly security incidents.
In summary, managing orphan accounts is a critical component of an organization’s overall cybersecurity strategy. Implementing robust IAM practices, conducting regular audits, and fostering a culture of security awareness are essential steps in mitigating the risks associated with orphan accounts. By prioritizing the identification and elimination of orphan accounts, organizations can create a safer and more secure IT environment for their employees, customers, and stakeholders.
Frequently Asked Questions (FAQ's)
1. What is an orphan account?
An orphan account is an active user account whose owner is no longer part of the organization, posing potential security risks.
2. How do orphan accounts occur?
Orphan accounts occur due to inadequate offboarding processes, mergers and acquisitions, and poor identity and access management practices.
3. What are the risks associated with orphan accounts?
Orphan accounts can lead to unauthorized access, data breaches, regulatory non-compliance, insider threats, resource drain, inaccurate audits, operational inefficiency, and financial losses.
4. How can organizations manage orphan accounts effectively?
Organizations can manage orphan accounts through regular audits, automated identity and access management tools, effective offboarding processes, and clear communication between HR and IT departments.
5. Why is it important to eliminate orphan accounts?
Eliminating orphan accounts is crucial to prevent unauthorized access, protect sensitive data, ensure regulatory compliance, and maintain operational efficiency.
6. What tools can help in identifying and managing orphan accounts?
Automated identity and access management (IAM) solutions, regular audits, and communication between HR and IT departments are effective tools for identifying and managing orphan accounts.
By implementing these strategies, organizations can mitigate the risks associated with orphan accounts and maintain a secure IT environment.















