Cybersecurity requires more than just protecting data from threats—you have to manage risks, comply with regulations, and ensure your organization stays resilient in the face of attacks. ...
Rogue devices are sneaky intruders that can threaten your network...
When it comes to running a tight ship, Governance, Risk, and Compliance...
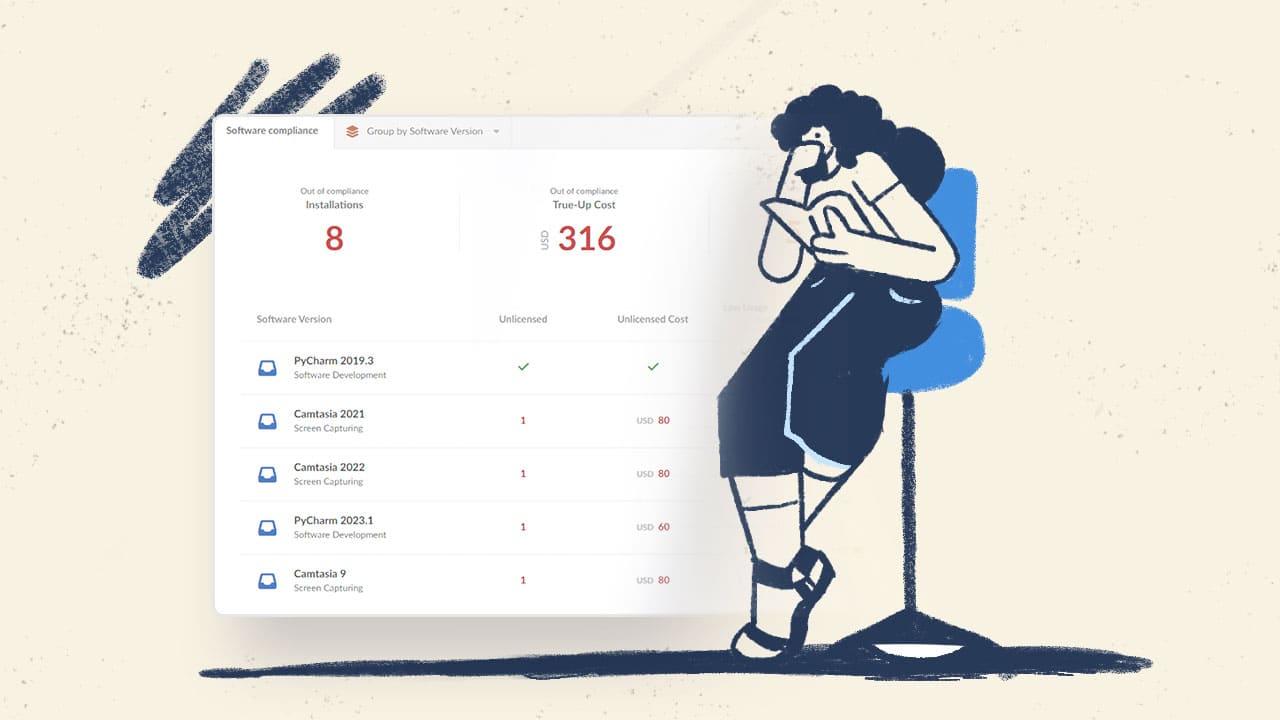
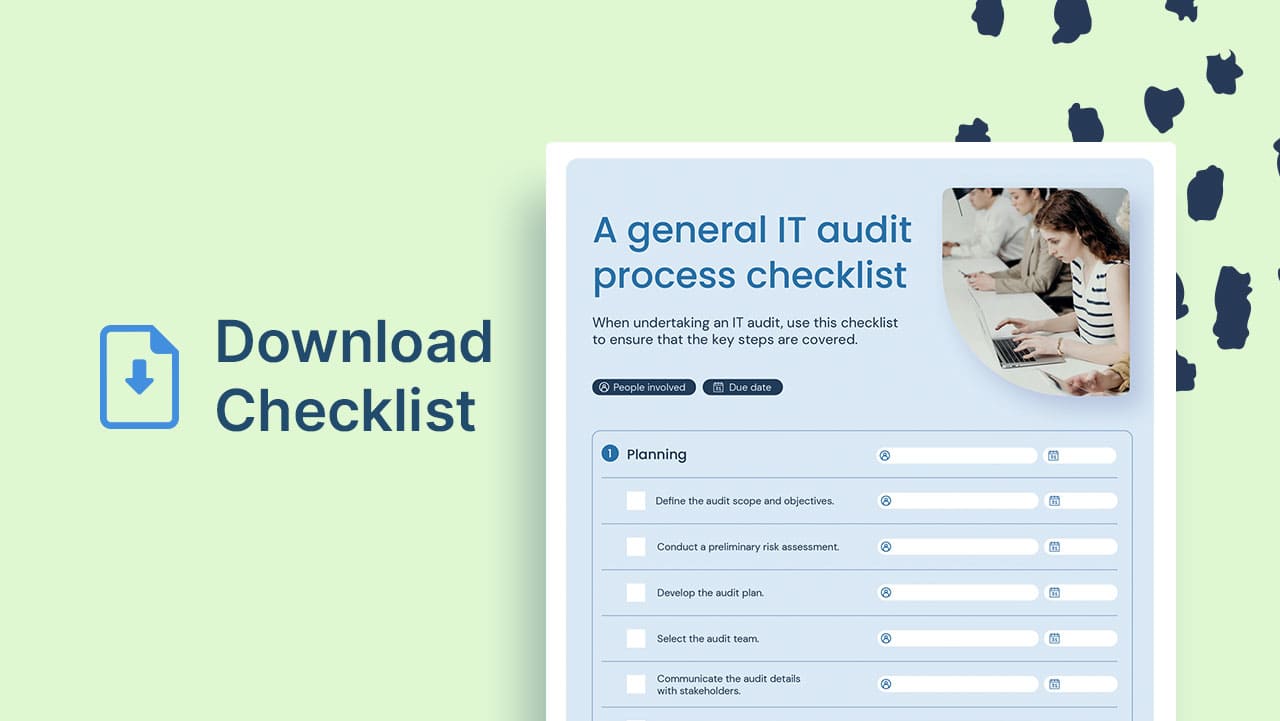
Is your organization looking to up its IT audit game? Conducting it...
Most organizations (if not all) have needs related to IT audits to stay...
The United States government has recently banned Kaspersky, Inc. from...
As networks continue to grow in complexity, investing in robust IP Address...
Let’s be honest. Keeping up with cybersecurity regulations and directives,...
If your IT department works for a financial institution operating in...
Keeping up with Governance, Risk, and Compliance (GRC) requirements within...