You can take a wide range of actions to nurture a culture of cybersecurity in your organization. Some of them can be directed to your employees — and include initiatives like password management and phishing training — and others are related to the strategy to adopt towards cybersecurity risk. That's where the NIST cybersecurity framework comes in (as well as other best practices such as CIS controls).
In short, the NIST framework consists of a set of voluntary guidelines for organizations to manage cybersecurity risks. First published in 2014, it provides a risk-based approach for organizations to identify, assess, and mitigate cyber attacks.
Though it's not mandatory, many companies use it as a guide for their cybersecurity efforts. And its relevance has been updated since the White House instructed agencies to better protect government systems through more secure software. Thus, we're about to explore its benefits, scope, and best practices.
What is the NIST cybersecurity framework?
NIST is the National Institute of Standards and Technology, a non-regulatory agency of the United States Department of Commerce. Its mission is to promote innovation and industrial competitiveness by advancing measurement science, standards, and technology in ways that enhance economic security and improve our quality of life.
Back in 2014, in response to an Executive Order from President Obama that called for the development of a cybersecurity framework, it released the first version of the NIST CSF, which was later revised and re-released in 2018.
Basically, it provides a risk-based approach for organizations to identify, assess, and mitigate cybersecurity risks and is intended to be used by organizations of all sizes and industries. Although it's voluntary, it has been adopted by many organizations (including Fortune 500 companies) as a way to improve their cybersecurity posture.
The NIST framework is based on existing standards, guidelines, and practices and has three main components:
- The Framework Core - This NIST component consists of a set of desired cybersecurity activities and outcomes in plain language to guide organizations towards the management (and consequent reduction) of cybersecurity risks.
- The Framework Implementation Tiers - The tiers provide context to organizations so that they consider the appropriate level of rigor for their cybersecurity program.
- The Framework Profiles - The last component is helpful to identify and prioritize opportunities for improving cybersecurity based on the organization's alignment to objectives, requirements, and resources when compared to the desired outcomes set in component 1.
Let's take a look at each NIST framework component in detail.
NIST CSF functions: the 5 elements of the Framework Core
The NIST Cybersecurity Framework Core consists of five high-level functions: Identify, Protect, Detect, Respond, and Recover. Its main goal is to act as a translation layer so that multi-disciplinary teams can communicate without the need of understanding jargon and is continuously evolving in response to changes in the cybersecurity landscape.

1. Identify
The first element of the National Institute of Standards and Technology's cybersecurity framework is "Identify." This refers to the process of identifying assets, vulnerabilities, and threats to prioritize and mitigate risks.
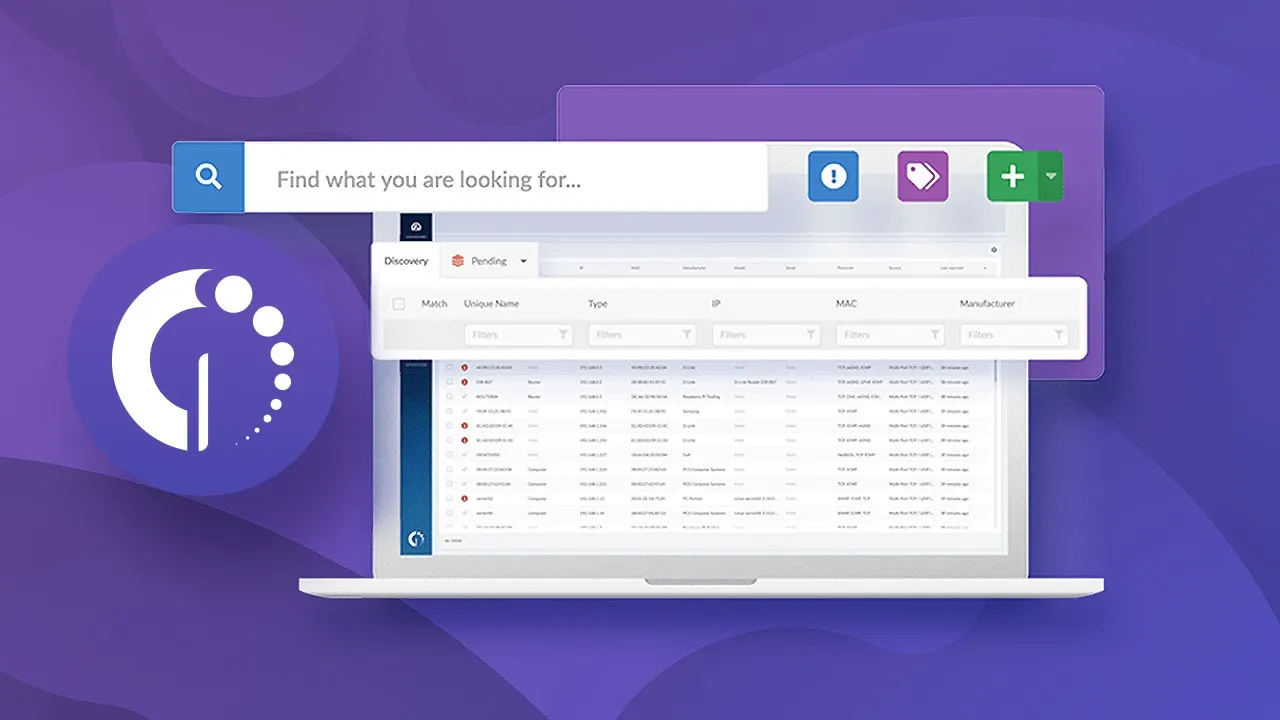
The first item on the list is perhaps the easiest one since  does it for you. With its Discovery feature, you can detect all the assets in your company's network with just a few clicks and map the software and hardware you own (along with its main characteristics, location, and owners).
does it for you. With its Discovery feature, you can detect all the assets in your company's network with just a few clicks and map the software and hardware you own (along with its main characteristics, location, and owners).
As for identifying vulnerabilities and threats, first, you'll need to understand your business' goals and objectives. Once you clear that out, the next step is to assess your current cybersecurity posture to identify any gaps (you can do it with tactics like red teaming) and develop a plan to address and mitigate them.
2. Protect
The "Protect" element of the NIST framework focuses on protecting against threats and vulnerabilities. In other words, it's what you do to ensure that critical systems and data are protected from exploitation.
This includes implementing security controls and countermeasures to protect information and systems from unauthorized access, use, disclosure, or destruction. In addition, you should create incident response plans to quickly and effectively respond to any incidents that do occur.
3. Detect
Detection is also an essential element of the NIST cybersecurity framework, and it refers to the ability to identify, investigate, and respond to cybersecurity events. And to be able to do so, you need to have visibility into your company's networks and systems.
Once again, this is something that software can do for you. In addition to creating a software and hardware inventory, InvGate Asset Management can monitor in real-time your organization's assets and alert you when something's wrong.
For instance, you can easily detect if there are unauthorized devices or software in your network (a practice known as shadow IT), keeping your IT perimeter under control.
It's worth mentioning that effective detection requires timely and accurate information about security events. Furthermore, this data must be promptly shared with the appropriate personnel so that they can take action. Detection must be tailored to the specific environment and needs of an organization to be effective.
4. Respond
Following a cybersecurity incident, organizations must rapidly assess the damage and take steps to limit the impact, and this is what "Respond" is all about. Reacting to a security issue includes steps such as identifying the incident, containing it, eradicating it, and recovering from it.
The goal here is to minimize the damage caused by the incident and to get the organization back up and running as quickly as possible. And this may include actions such as notifying law enforcement, issuing public statements, and activating business continuity plans.
To be effective, a response plan must be in place before an incident occurs. It should be regularly tested and updated to ensure that it remains relevant.
5. Recover
The fifth and final element of the NIST CSF is "Recover." This element focuses on the ability to bounce back from an incident and return to normal operations.
This includes having a plan in place for how to deal with an incident, as well as having the resources and capabilities in place to execute that plan. It also includes assessing the impact of an incident and taking steps to prevent similar incidents from happening in the future.
NIST Framework Implementation Tiers
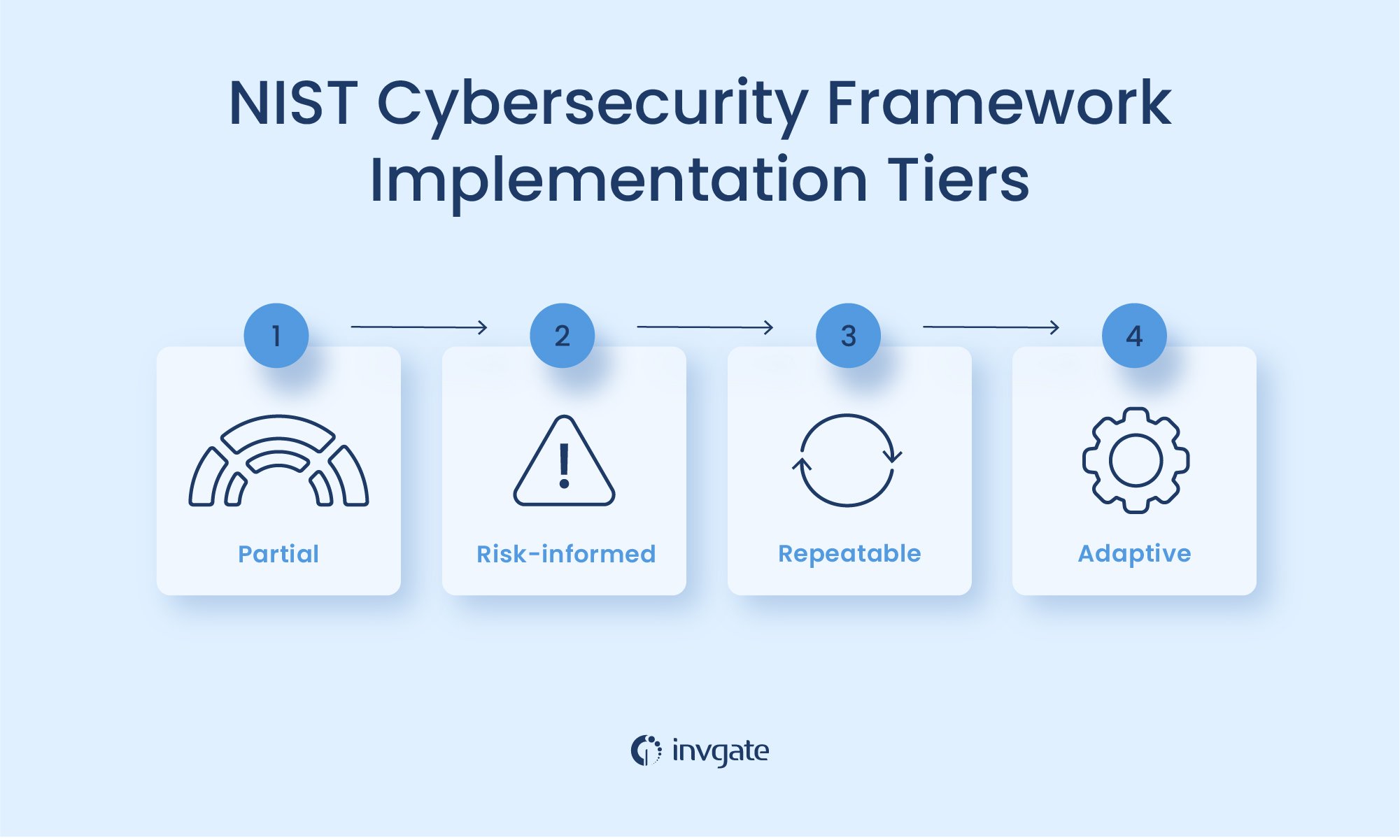
Now that we've gone over the five core elements of the NIST cybersecurity framework, it's time to take a look at its implementation tiers. In order to be flexible and customizable to fit the needs of any organization, NIST used a tiered approach that starts with a basic level of protection and moves up to a more comprehensive level. At this point, it's relevant to clarify that they don't aim to represent maturity levels but framework adoption instead.
The NIST Implementation Tiers are as follows:
- Tier 1: Partial - In Tier 1 organizations, there's no plan or strategy in place, and their approach to risk management is reactive and on a case-by-case basis.
- Tier 2: Risk-informed - Tier 2 businesses recognize that cybersecurity risks exist and that they need to be managed. However, they lack standard procedures and company-wide awareness of threats.
- Tier 3: Repeatable - Tier 3 organizations have developed and implemented procedures for managing cybersecurity risks. This includes incident response plans, security awareness training, and regular security assessments.
- Tier 4: Adaptive - Continuously improving the organization's approach to managing cybersecurity risks. This includes making changes in response to incidents, new threats, and changing business needs.
Keep in mind that you can implement the NIST framework at any of these levels, depending on your needs. And you can move up the tiers over time as your company's needs evolve.
NIST Framework Profiles
The whole point of Cybersecurity Framework Profiles is to optimize the NIST guidelines to adapt to your organization. In this sense, a profile is a collection of security controls that are tailored to the specific needs of an organization.
To create a profile, you start by identifying your business goals and objectives. Then, you have to map out your current security posture and identify any gaps. Once that's done, it's time to select the security controls that are most relevant to your organization and implement them.
From the comparison between this map of your company's current security measures and the desired outcomes outlined in the five functions of the Framework Core, you can identify opportunities to improve the company's cybersecurity efforts. Furthermore, you can build a prioritized implementation plan based on your most urgent requirements, budget, and resources.
Though there's no unique way to build a profile, NIST provides the following example:
"One way of approaching profiles is for an organization to map their cybersecurity requirements, mission objectives, and operating methodologies, along with current practices against the subcategories of the Framework Core to create a Current-State Profile. These requirements and objectives can be compared against the current operating state of the organization to gain an understanding of the gaps between the two."
5 benefits of the NIST framework
As we mentioned above, though this is not a mandatory framework, it has been widely adopted by businesses and organizations across the United States, which speaks highly of it.
By adopting and adapting to the NIST framework, companies can benefit in many ways:
- It provides a flexible and cost-effective approach to managing cybersecurity risks.
- It improves security awareness and best practices in the organization.
- It gives companies a proactive approach to cybersecurity risk management.
- It's flexible enough to be tailored to the specific needs of any organization.
- It enhances communication and collaboration between different departments within the business (and also between different organizations).
Nonetheless, all that glitters is not gold, and the NIST CSF compliance has some disadvantages as well. For once, the framework is voluntary, so businesses may not be motivated to implement it unless they are required to do so by law or regulation. Additionally, it's complex and may be difficult to understand and implement without specialized knowledge or training.
In short
The NIST Cybersecurity Framework is a set of best practices that businesses can use to manage cybersecurity incidents. It's flexible, adaptable, and cost-effective and it can be tailored to the specific needs of any organization. So, it would be a smart addition to your vulnerability management practice.
Thanks to its tier approach, its efforts to avoid technisisms and encourage plain language, and its comprehensive view of cyber security, it has been adopted by many companies in the United States, despite being voluntary. Additionally, many government agencies and regulators encourage or require the use of the NIST cybersecurity framework by organizations that do business with them.
Organizations that use the NIST cybersecurity framework typically follow these steps:
- Use the cybersecurity framework self-assessment tool to assess their current state of cyber readiness.
- Develop a roadmap for improvement based on their assessment results.
- Implement improvements.
- Monitor their progress and revise their roadmap as needed.
- Repeat steps 2-5 on an ongoing basis as their business evolves and as new threats emerge.
There are many resources out there for you to implement it - including templates, checklists, training modules, case studies, webinars, etc. Plus, you can also automate several parts of the process — such as software inventory, asset tracking, and periodic reporting — with InvGate Asset Management. You can try it today at no cost: request our 30-day free trial and start protecting against cybersecurity risks today.















