CVE-2023-28252, a critical vulnerability in the Windows Common Log File System (CLFS), has recently caught the attention of the cybersecurity community. This vulnerability, when exploited, allows attackers to gain SYSTEM privileges on targeted machines, posing a significant risk to organizational security.
In this article, we’ll explore the implications of CVE-2023-28252, the importance of addressing it promptly, and how InvGate Asset Management can simplify the Patch Management process to safeguard your organization's infrastructure effectively.
Don't miss out on this essential information to discover how to defend against potential cyber threats.
About CVE-2023-28252
Microsoft has recently released patches for several vulnerabilities, including one actively exploited zero-day vulnerability: CVE-2023-28252. This exploit, which is part of the list of known vulnerabilities exploited in 2023, affects the Windows Common Log File System (CLFS) and allows attackers to gain SYSTEM privileges on targeted machines. The discovery of this vulnerability marks the second CLFS elevation of privilege zero-day exploit found in the wild this year, following the patching of CVE-2023-23376 in February. It is also the fourth CLFS zero-day exploit discovered within the past two years.
The significance of CVE-2023-28252
The exploitation of CVE-2023-28252 by a sophisticated cybercrime group highlights the critical nature of this vulnerability. This group has been attempting to deliver the Nokoyawa ransomware using a series of similar but unique exploits targeting the CLFS driver. These exploits are believed to be the work of a single author, with at least five different exploits identified since June 2022.
The affected industries include retail, wholesale, energy, manufacturing, healthcare, and software development, among others. The consistent use of CLFS exploits by this group underscores the urgency for organizations to address this vulnerability and ensure their systems are protected.
Security experts have advised organizations to quickly test and deploy the patch provided by Microsoft, as this type of exploit is often accompanied by a code execution bug, which could lead to the spread of malware or ransomware.
How to find devices exposed to CVE-2023-28252 with InvGate Asset Management
To safeguard systems from the risks posed by CVE-2023-28252, organizations should apply the patch provided by Microsoft promptly.
InvGate Asset Management offers a range of robust functionalities aimed at helping you easily identify the devices within your organization that require urgent attention. To make the most of these capabilities, follow the provided instructions:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows”.
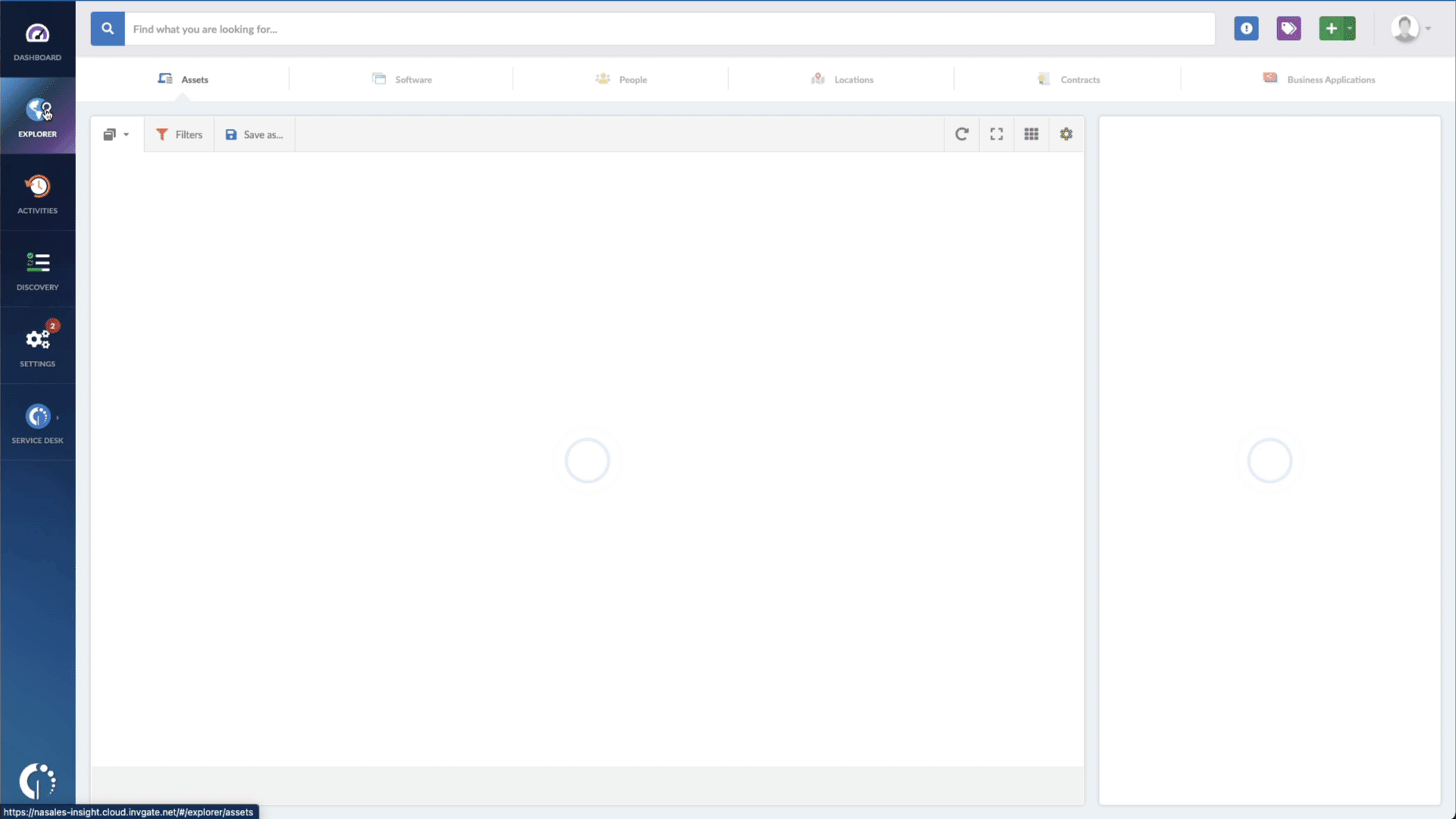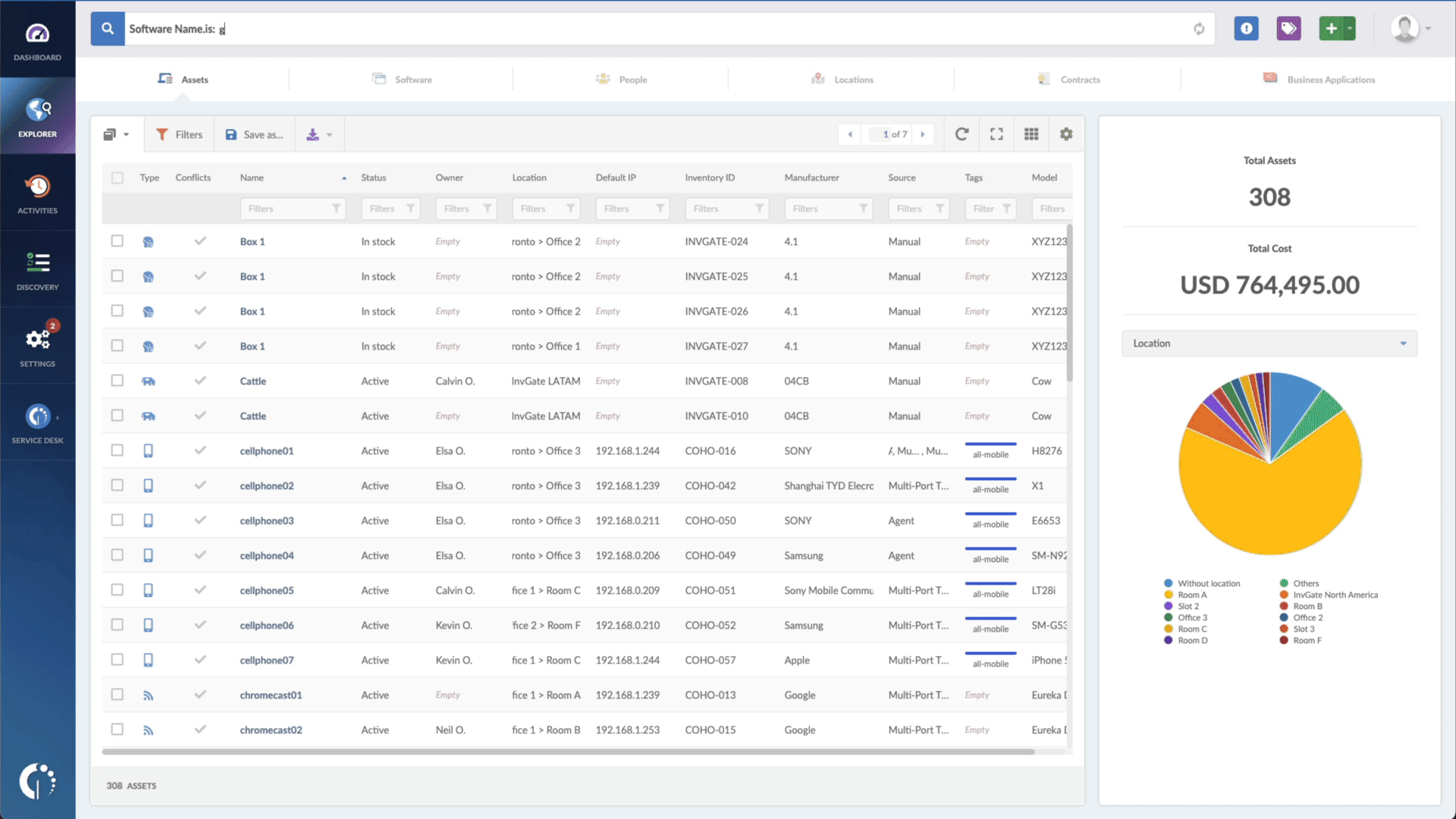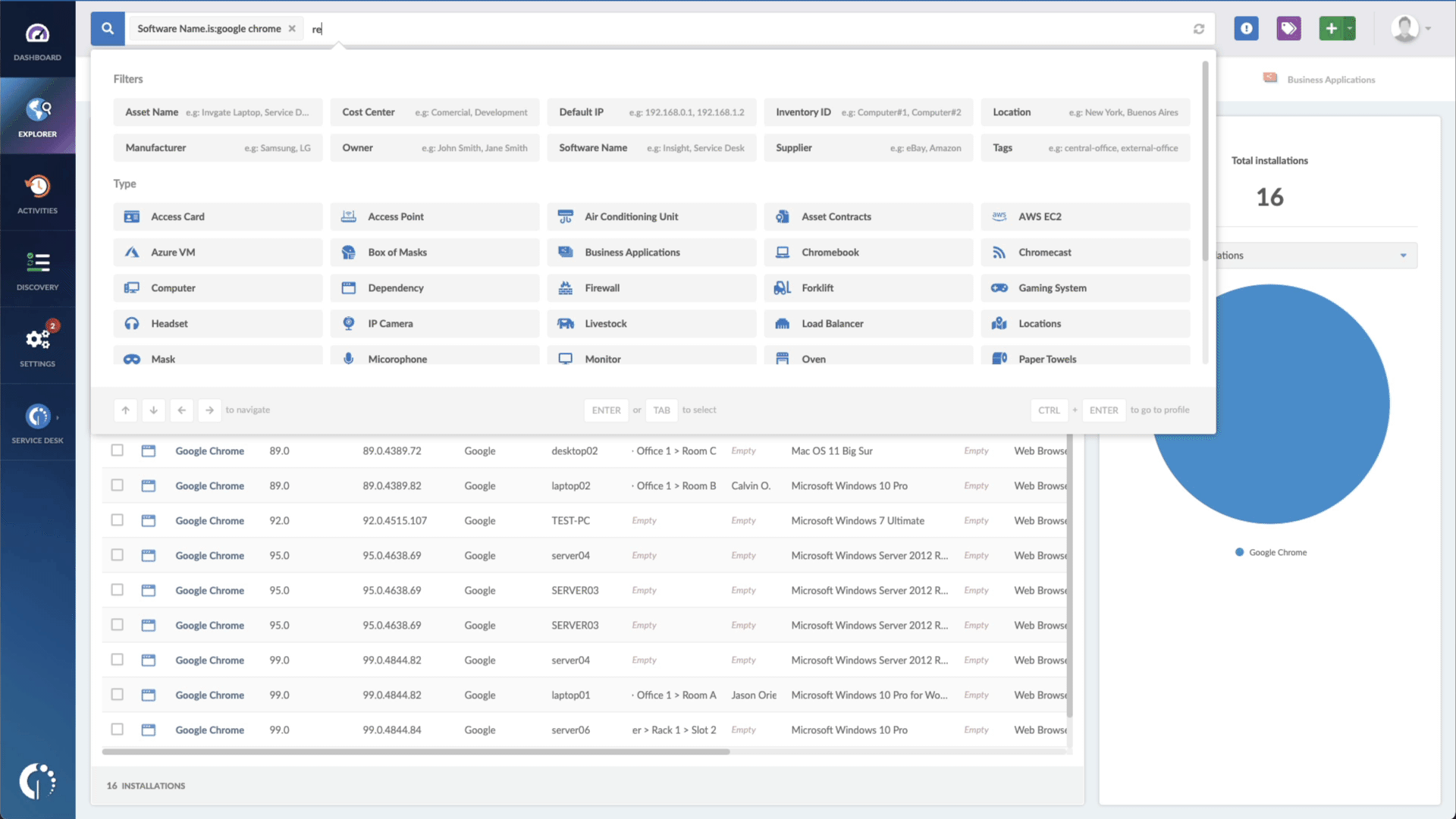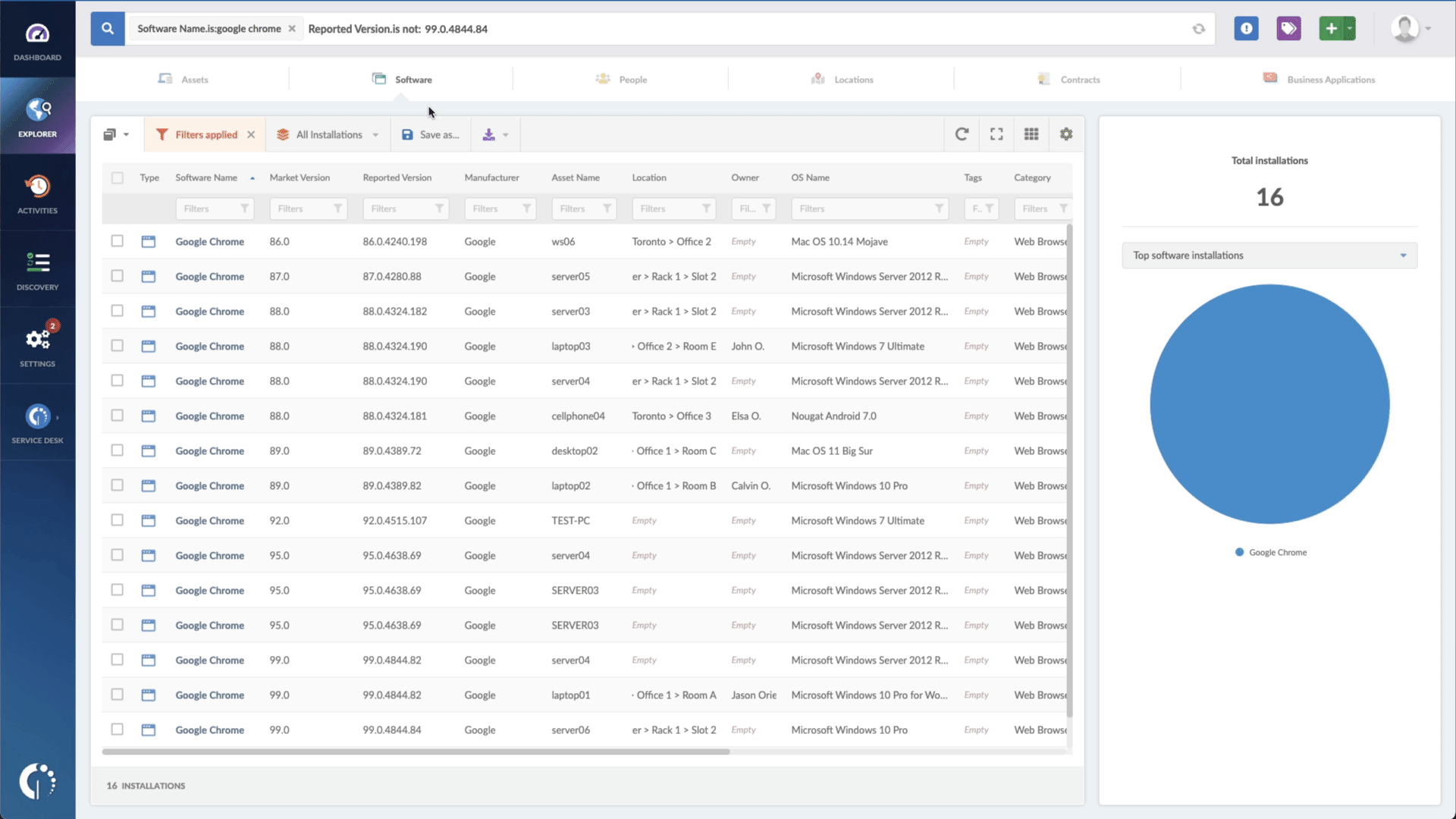
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version.
And there you have it! In just a few seconds, you'll receive a complete inventory of at-risk devices that demand prompt attention. You can effortlessly download this information as a CSV file and share it with your team, ensuring they are well-informed about the necessary updates that need to be applied.
For additional details, watch our instructional video on identifying vulnerable devices for patching.
The bottom line
In conclusion, the identified vulnerability CVE-2023-28252 in the Windows Common Log File System (CLFS) poses a significant risk to organizations, as attackers can exploit it to gain SYSTEM privileges on targeted machines. To mitigate this risk, it is crucial to promptly update affected systems with the latest software version provided by Microsoft.
InvGate Asset Management, as part of a Vulnerability Management strategy, offers a comprehensive set of features to help you effortlessly identify vulnerable devices within their network that require immediate attention.
To experience the benefits of InvGate Asset Management firsthand, request our 30-day free trial. Safeguard your organization's infrastructure and protect against potential cyber threats!















