In cybersecurity, organizations need to use a combination of prevention, detection, and response to reduce attacks and keep the data safe. One approach that has gained traction in recent years is the Purple Team. It is an innovative method that fosters collaboration between IT operations and security departments to stop or mitigate data breaches in their early stages. According to Forbes, the cost of cyber attacks is expected to reach $10.5 trillion USD annually by 2025. This statistic reminds organizations to step up their security defenses and ensure they implement security controls that are robust and effective. In this context, companies must build cybersecurity on collaboration across teams.
The Purple Team's job is to ensure everyone is working towards the same goal. In this blog post, we'll look at its best practices, challenges, and limitations.
What is a Purple Team?
In IT security, a Purple Team is a collaborative approach to security testing that combines the strengths of the Red Team (offensive) and the Blue Team (defensive). The primary objective of the Purple Team exercise is to identify vulnerabilities and improve the overall security posture of an organization.
What are Red and Blue Teams in cybersecurity?
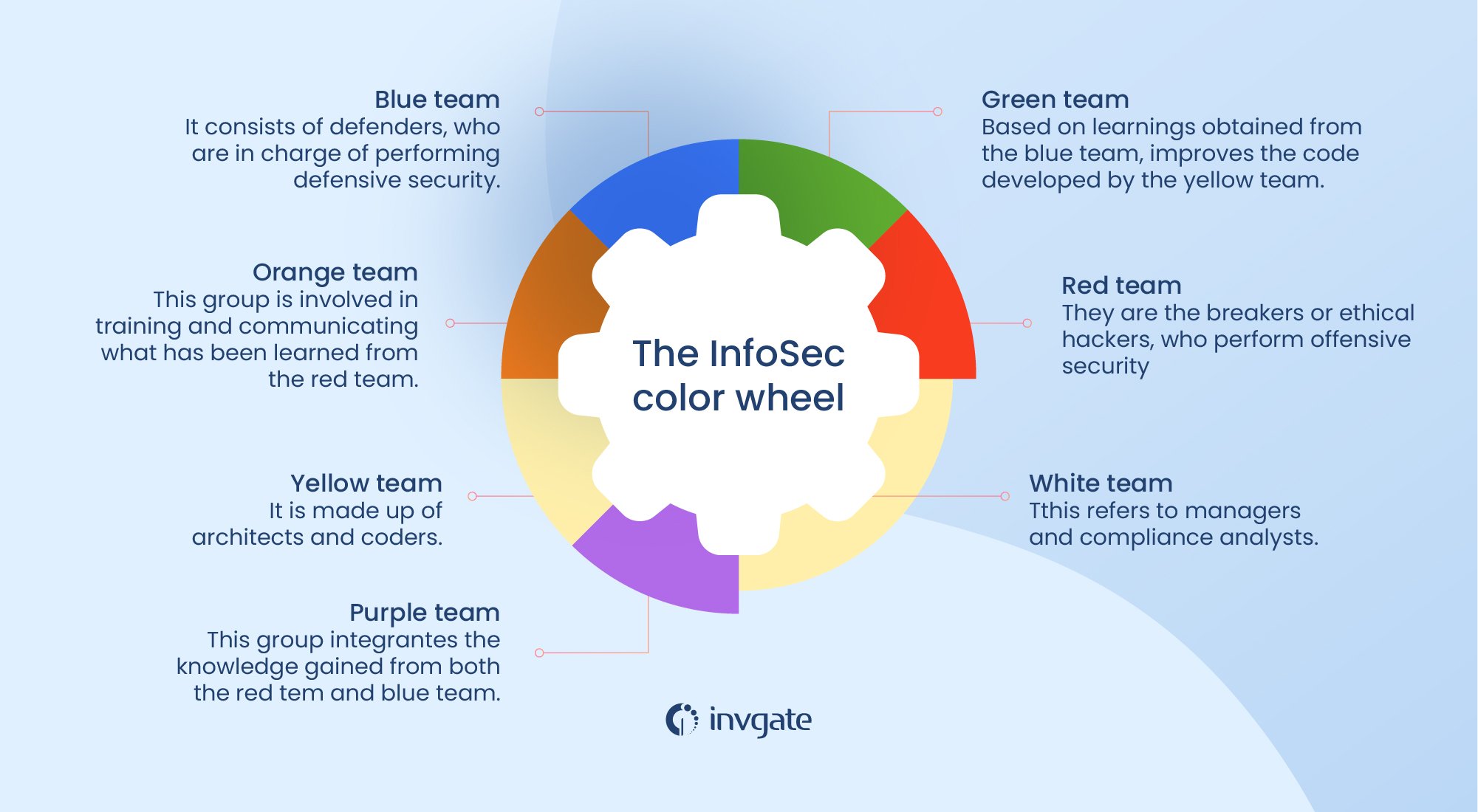
Red, Blue, and Purple Teams are all part of the InfoSec color wheel, which aims to unite the efforts of information security and software deployment experts.
Traditionally, cybersecurity teams have been divided into two main groups, Red and Blue teams. Let's see their differences:
-
Red Teams: These are the offensive security experts. They simulate real-world attacks to test an organization's defenses, much like ethical hackers. They use a variety of tactics, techniques, and procedures (TTPs) to try to breach an organization's defenses, including social engineering, phishing, and brute-force cyber attacks.
-
Blue Teams: These are the defensive security professionals. They're responsible for maintaining security systems, detecting threats, and responding to incidents. They monitor the systems for signs of attacks, such as unusual network traffic or attempted breaches, and respond to incidents as they occur.
The middle point: Purple Teams
Purple teaming is a collaborative approach to cybersecurity that combines the strengths of both red and blue teams to enhance an organization's overall security posture.
Purple teaming brings these two sides together, creating a synergy that's greater than the sum of its parts. The term "purple" comes from mixing the colors typically associated with these teams - red and blue.
In practice, purple teaming involves close collaboration between offensive and defensive teams. Here's what it typically looks like:
The red team members carry out simulated attacks on the organization's systems, networks, or applications. As they do this, they work closely with the blue team, providing real-time feedback on their techniques and findings.
The blue team, in turn, actively defends against these simulated attacks. They analyze the red team's methods, adjust their defenses, and provide immediate feedback on what they're seeing and how they're responding.
This back-and-forth creates a continuous feedback loop. The red team's attacks become more sophisticated based on the blue team's responses, while the blue team's defenses improve as they learn from the blue teams work and the red team's tactics.
The goal of purple teaming isn't for one side to "win" over the other. Instead, it's about fostering a collaborative environment where both teams learn from each other, ultimately strengthening the organization's overall network security together.
Purple teaming can take various forms. It might involve formal exercises where teams work together on specific scenarios, or it could be an ongoing process integrated into daily operations. Some organizations have dedicated purple team teams, while others practice purple teaming as a methodology within their existing security structure.
The benefits of this approach are significant. It helps identify security gaps that might be missed by either team working in isolation. It improves the skills of both offensive and defensive team members to address security vulnerabilities. And perhaps most importantly, it cultivates a holistic understanding of security within the organization, moving beyond the traditional siloed approach.
Unlike the Red and the Blue Teams, the Purple Team seeks to bring both sides together to simulate attacks and assess the effectiveness of the organization's security controls. This collaboration helps improve the organization's security posture by identifying defenses' vulnerabilities and weaknesses before an attacker can exploit them.
How can Purple Teams help organizations?
The primary role of the Purple Team is to improve an organization's security posture by identifying vulnerabilities, improving incident response, and ensuring that the organization's security controls are adequate. The Purple Team achieves this by bringing together both the Red and Blue Teams, combining their knowledge and expertise to simulate attacks and assess the organization's existing security controls and defenses.
The Purple Team also helps bridge the Red and Blue teams' communication gap. Encouraging collaboration ensures that everyone is working towards the same goal and that the organization's defensive measures are solid and effective.
Do you need separate red and blue teams to implement purple teaming?
Not necessarily. While having dedicated red and blue teams can be beneficial, smaller organizations can practice purple teaming by having team members alternate between offensive and defensive roles or by partnering with external security firms.
Benefits of the Purple Team
A Purple Team offers several benefits for organizations that want to improve their security posture:
-
Collaboration: By bringing together the Red and Blue Teams, the Purple Team encourages collaboration between groups that may have operated in silos previously. This collaboration can lead to a better understanding of the organization's security posture and improve the overall effectiveness of security measures.
-
Real-world simulations: The Purple Team allows organizations to simulate real-world attacks, which can provide a more realistic assessment of their security posture. By using actual attack methods and TTPs, it can identify weaknesses that may have gone unnoticed in traditional testing scenarios.
-
Improved communication: By working together, the Red and Blue team can improve communication and coordination during security incidents. The results can be faster incident response times and better overall security outcomes.
-
Better Return On Investment (ROI): A Purple Team can provide a better ROI compared to traditional Red Team/Blue Team exercises. By collaborating and focusing on specific areas of weakness, the Purple Team can identify vulnerabilities and suggest remediation measures more efficiently and effectively.
-
Continuous improvement: Purple Teaming is all about ongoing collaboration and continuous improvement. Thus, the organization's security posture can be continuously assessed and improved over time rather than relying on periodic testing exercises.
Purple Team best practices
Building and running an effective Purple Team requires specialized skills and knowledge. Here are some best practices to consider:
-
Hire skilled professionals: Purple Team members should have a mix of offensive and defensive skills and should be able to work collaboratively with others.
-
Use the right tools: There are many tools and technologies available to support the Purple Team, such as penetration testing tools, vulnerability scanners, and incident response platforms.
-
Foster collaboration: The success of the Purple Team relies on effective collaboration between the Red and Blue Teams to ensure everyone is working towards the same goal.
-
Focus on continuous improvement: Regularly assess the Purple Team approach's effectiveness and look for improvement areas.

The Purple Teaming process
At the heart of effective purple teaming lies a dynamic, iterative process. This cycle forms the backbone of a proactive security strategy, enabling organizations to stay ahead of potential threats and continuously strengthen their defenses.
Let's dive deeper into this cycle and explore how it works:
-
Assessment: The cycle begins with a thorough assessment of the organization's current security posture. It involves a deep dive into systems, networks, and processes, often utilizing advanced tools and techniques to uncover hidden vulnerabilities. The red team typically leads this phase with realistic attack scenarios.
-
Collaboration: Once the assessment is complete, the red and blue teams come together to analyze the findings. This collaborative phase is where the magic of purple teaming really happens. The red team shares insights into the vulnerabilities they discovered and the methods they used to exploit them. The blue team members, in turn, provide context on the organization's cybersecurity defenses that are already in place and the challenges they face.
-
Remediation: Armed with a comprehensive understanding of the vulnerabilities and weaknesses identified, they move into the remediation phase. This is where plans are made, and actions are taken to address the discovered issues. It might involve patching systems, updating policies, implementing new security controls, or even redesigning certain processes. The key here is prioritization - first focusing on the most critical vulnerabilities while developing a roadmap for addressing all identified issues.
-
Validation: After remediation efforts have been implemented, it's crucial to validate their effectiveness. This often involves another round of testing, where the red team attempts to exploit the same vulnerabilities or find new ones. This validation ensures that the remediation efforts have been successful and haven't inadvertently created new security gaps.
But the cycle doesn't end here. It's a continuous process, constantly repeating to adapt to new and emerging threats and evolving technologies. Each iteration builds upon the last, creating a spiral of continuous improvement in the organization's offensive and defensive strategies.
This cyclical approach offers several key benefits:
-
It provides a structured framework for identifying and addressing security weaknesses.
-
It encourages ongoing collaboration between offensive and defensive security teams.
-
It helps prioritize security efforts, ensuring resources are focused where they're needed most.
-
It creates a documented trail of security improvements over time.
-
It fosters a culture of continuous learning and adaptation within the security team.
Perhaps most importantly, with this approach, you'll be shifting your organization's security stance from reactive to proactive. Rather than waiting for actual breaches to occur, it allows teams to stay one step ahead, constantly testing, improving, and validating their defensive tactics, threat detection, incident response procedures, and mitigation strategies. This approach recognizes that cybersecurity isn't a destination but a journey.
Purple Team challenges and limitations
While a Purple Team can be effective, there are some challenges and limitations to consider:
-
The need for specialized skills and knowledge: Purple Team members should have a mix of offensive and defensive skills, which can be difficult to find in one person.
-
The potential for conflicts between the Red and Blue Teams: These teams may have different priorities, and conflicts may arise during the collaboration process.
-
The Purple Team may not be suitable for all organizations: Smaller organizations may need more resources to implement Purple Teaming, while larger organizations may find it challenging to implement due to organizational structure and politics.
Certifications and continuous learning: Building your Purple Team
As we stated, staying ahead of the curve is a great advantage when it comes to cybersecurity. For purple team members who need to master both offensive and defensive skills, continuous learning is the key to success.
The true strength of a purple team lies in its ability to adapt and grow continuously. Embracing continuous learning is essential, and to nurture this mindset, you can start by working with each team member to develop a personalized learning roadmap.
It might begin with foundational certifications and progress to more specialized areas of expertise. Encourage your team to dive into diverse learning opportunities. Send them to conferences where they can hear from industry leaders and network with peers. Support their participation in webinars and online courses that pique their interest. And don't underestimate the value of hands-on experience – platforms like Hack The Box or TryHackMe offer excellent opportunities to put skills to the test in a safe environment.
Knowledge sharing within the team is another powerful tool for collective knowledge transfer and growth. Set up regular internal training sessions where team members can present their areas of expertise or recent learnings. This not only spreads knowledge but also hones communication skills – a crucial asset for any purple team member.
Let's explore some of the most valuable certifications for purple team experts and discuss how to foster a culture of ongoing education within your team.
Certifications for your Purple Team
Certifications serve as milestones in a cybersecurity professional's career, validating their skills and knowledge. For purple team members, a mix of offensive and defensive certifications is ideal. Here are some of the most relevant certifications to consider:
-
Certified Ethical Hacker (CEH): This certification is a great starting point for understanding the offensive side of security. It covers the tools and techniques used by hackers, giving purple team members insight into potential attack vectors. With this knowledge, they can better anticipate and counter threats.
-
Certified Information Systems Security Professional (CISSP): Often considered the gold standard in security certifications, the CISSP provides a comprehensive overview of information security. It's particularly valuable for purple team members who need to understand the big picture of organizational security.
-
Certified Information Systems Auditor (CISA): While it might seem more aligned with blue team activities, the CISA certification is crucial for purple team members. It helps them understand how to assess and improve information systems controls, which is essential when evaluating the effectiveness of security measures.
-
GIAC Security Essentials Certification (GSEC): This certification offers a solid foundation in security principles. It's an excellent choice for those new to the field or for experienced professionals looking to fill knowledge gaps.
Key takeaways
In conclusion, the Purple Team approach is highly valuable to an organization's security program. As a combination of the Red and Blue Teams, it helps to:
-
Identify vulnerabilities.
-
Improve incident response.
-
Ensure that an organization's security defenses are strong and effective.
While there are challenges and limitations to implementing it, the benefits make it worth considering for organizations of all sizes.
Organizations should hire skilled professionals, use the right tools to build an effective Purple Team, foster collaboration, and continuously assess the approach's effectiveness. By doing so, they can ensure that their security program is solid and practical and that they are well-prepared to defend against today's ever-evolving threats.
As IT security threats continue to grow in complexity and frequency, organizations must remain vigilant to protect their data, systems, and networks from advanced threats. Purple Teaming is one tool in the security professional's toolbox. By implementing it, they can take an essential step towards improving their security posture and protecting against cyber threats.















