Red team scenarios are frameworks companies use to evaluate their level of security from an adversarial approach.
Red teams look for vulnerabilities or security holes in the system by simulating a cyber attack. This helps identify what needs to be improved so that the organization is well-prepared to defend itself against a real-life cyber threat.
But in order to understand how exactly they can do that, we'll take a closer look at red team scenarios and red teaming methodologies, give a couple of examples, and see the benefits this method can bring to your company.
What are red team scenarios?
Red teaming is a methodology used to assess an organization's security by simulating an attack; and it's an indicative of a strong cybersecurity culture. In a red team scenario, the experts will use different tools and techniques to imitate an actual attack to determine how vulnerable your company is to this type of situation.
They will evaluate your organization's detection, mitigation, and response capabilities. With the information security gathered from these exercises, red teams can perform threat intelligence, that is, data about possible threats and vulnerabilities.
Once you get the red team assessment, you will be able to address what needs to be improved so that the organization is better prepared to respond to any threat actor.
Examples of red team scenarios
Red team attack scenarios imitate different threat actors and, in so doing, resort to other intrusion vectors. This will then allow them to move on to the objective, which could be the deployment of ransomware or leakage of sensitive information.
Red teams can be inside or outside the company. In other words, attack simulations can be performed by the company's employees within the IT department or third parties offering these exercises as part of their advisory services.
Examples of attack simulations:
- A hacktivist exploits a vulnerability to sabotage the industry's infrastructure and delay production.
- A malicious employee with privileges deploys malware in the system to ruin several machines.
- A hacker uses social engineering to fool an employee, get credentials to access a robust database, and expose that information.
- A cybercriminal exploits unpatched network services to access sensitive information about clients.
There are other cybersecurity teams with different goals, which are part of what is known as the InfoSec security wheel. This model attributes different colors to the various teams based on the type of activities they perform.
Just as there is a red team, there is also a blue team responsible for proactively taking and/or suggesting protective measures to defend the company from possible attacks. While the red team takes an offensive strategy, the blue team takes a defensive one.
There could also be a purple team made up of red and blue teamers. They work together, from their perspectives, to improve the company's security.
Benefits of red teaming
Red teaming provides several benefits in terms of security. This methodology can help:
- Improve your company's capability to detect and defend itself from an attack.
- Learn about security holes and vulnerabilities to design better security practices.
- Evaluate how ready the IT security department is to respond to an attack.
- Make end-users aware of the risks they are exposed to.
How the red team scenario methodology works
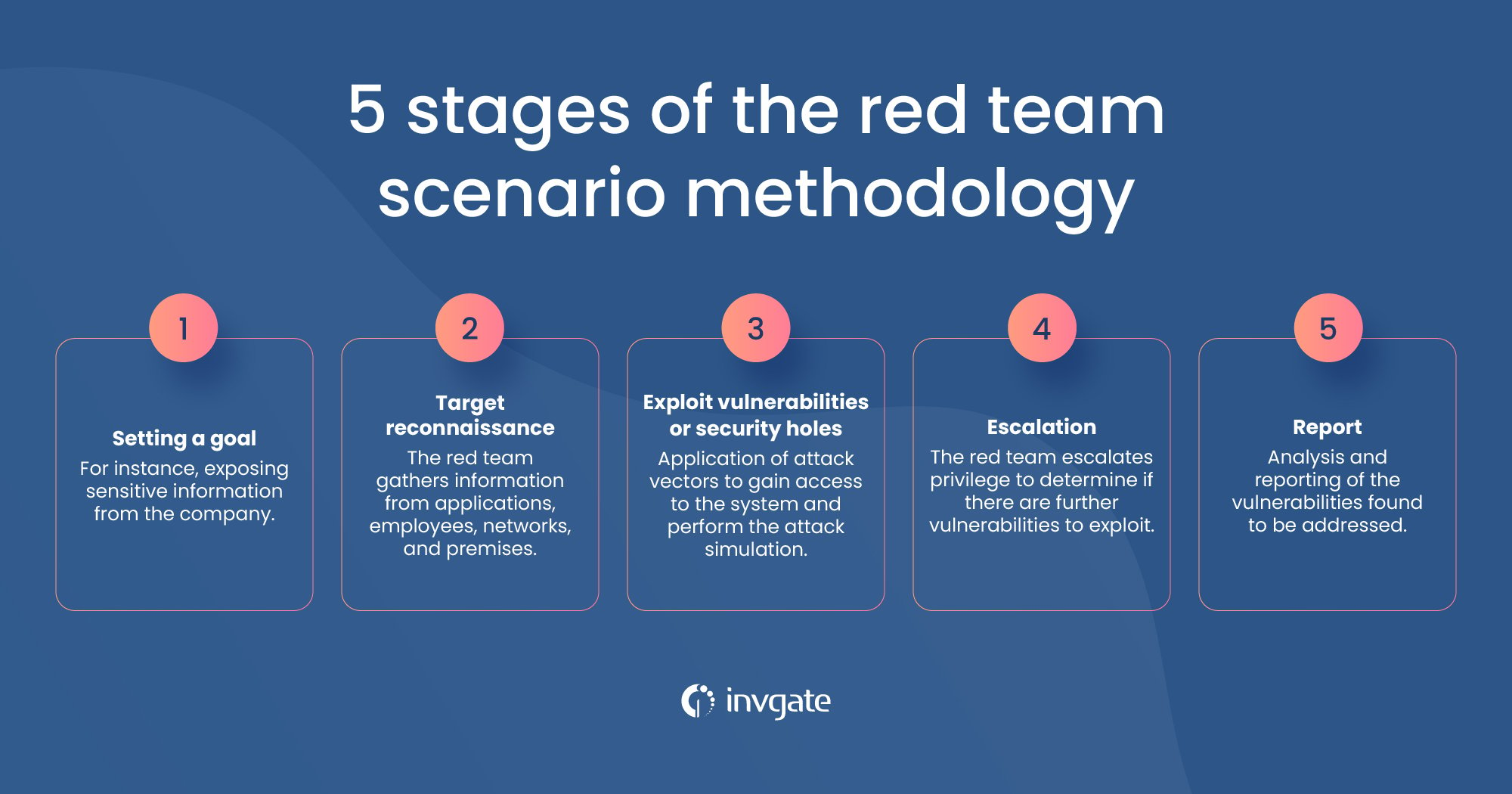
Red team simulation has various stages that can be summarized as follows:
- Setting a goal - This could be exposing sensitive information from the company.
- Target reconnaissance - Once the goal has been set, the team will get information from applications, employees, networks, and premises. This last aspect is vital because overseeing physical security could lead to cyber hacks. For example, an attacker could break into the building and access computers or servers where they could steal confidential data or damage the system by installing malware.
- Exploit vulnerabilities or security holes - The team will resort to different attack vectors, such as password dumps, weak credentials, or phishing, to gain access to the system and perform their attack simulation.
- Escalation - The red team will try to escalate privilege and might determine if there are further vulnerabilities to exploit. They will attempt to probe information security, cloud security, etc.
- Report - Once the attack is complete, the red team will analyze and report the vulnerabilities found so that they are addressed.
To perform their exercises, red teams can follow different frameworks, such as the Mitr Attck framework, which classifies cyberattacks based on adversaries' techniques.
Under the Mitr Attck, the tactics are categorized as follows:
- Reconnaissance - Getting data about the organization through social engineering or other tools.
- Resource development - Establishing infrastructure to support the activities to be carried out.
- Initial access - Phishing could be an example of access into the network.
- Execution - Deploying the malware.
- Persistence - Keeping access through changed credentials and other methods.
- Privilege escalation - Gaining higher-level permissions.
- Defense evasion - Using techniques to hide malicious code and prevent being detected.
- Credential access - Getting users and passwords to access the system.
- Discovery - Obtaining information about the system and the network, such as accounts, applications, etc.
- Lateral movement - Using techniques to control remote systems on a network.
- Collection - Gathering data to perform the objective.
- Command and control - Mimicking expected traffic to avoid detection to communicate and control the hacked systems.
- Exfiltration - Stealing data.
- Impact - Disrupting or compromising integrity by manipulating different processes.
Another well-known framework to analyze and simulate a cyber-attack that could be used in red teaming is Cyber Kill Chain, developed by Lockheed Martin. The Kill Chain model includes the following stages:
- Reconnaissance - Getting information about the target network to identify vulnerabilities and security holes. Cybercriminals could use social engineering at this stage.
- Weaponization - Creating or adapting malware to the vulnerabilities reached in the organization to be attacked.
- Delivery - Sending the malware (weapon) to the target via USB, mail, or other means.
- Exploitation - Exploiting a vulnerability that executes code in the system.
- Installation installing malware.
- Command and control - Getting continued access to the target to control it and manipulate it remotely.
- Actions on objectives - Taking steps to achieve the goals such as data destruction, encryption, or exfiltration.
Red team vs. pentest: the main differences
Pentesting is only a small portion of red team testing. Penetration testing exploits specific system vulnerabilities to assess how resilient that technology is. It is more like a minor targeted attack.
On the other hand, red teamers emulate an actual world situation to perform a thorough risk analysis. They try to get as far as possible into the system and simulate an advanced persistent threat.
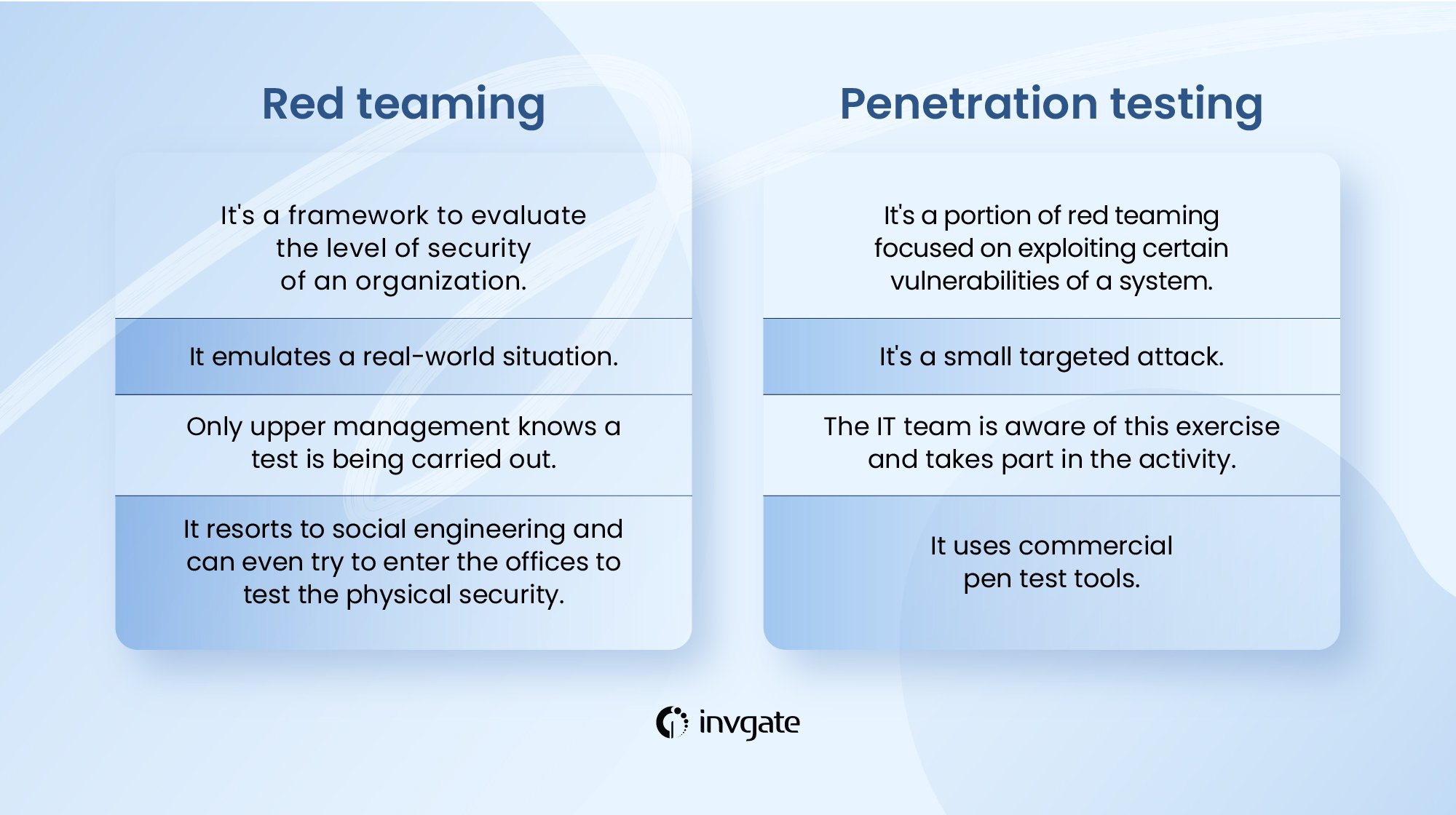
Penetration testing is only one part of the tasks performed within red teaming, which includes persistence, evasion, escalation, and data exfiltration.
When it comes to red teaming, just upper management knows a test is being carried out, whereas the IT team is not aware of this situation.
Penetration testing is part of an exercise performed to evaluate one aspect of the system. The IT team is aware and is part of this activity.
Another aspect is the diversity of tools employed. Red team assessment resorts to social engineering and even implies trying to enter the offices to test the physical security. None of those techniques are employed in a penetration test.
Key takeaways
Red teams evaluate a company's security policies and strategies by emulating a real-life cyber attack. They resort to different techniques that can be performed and analyzed from various frameworks, such as Mitre Attck or Cyber Kill Chain but could be summed up as follows:
- Setting a goal
- Target reconnaissance
- Exploit vulnerabilities or security holes
- Escalation
- Report
It is essential to bear in mind that pen testing is only part of what a red team does. While pen testing is about finding and exploiting particular vulnerabilities in the system, red teaming emulates a cyber attacker. That is why they resort to all sorts of techniques such as social engineering or even physically breaking into the organization´s premises. Besides, once they gain access to the network, they seek to perform a persistent adversarial attack (APT).
Frequently Asked Questions
What is red teaming?
Red teaming implies testing a company's security by emulating a threat actor that performs a cyber attack. A red team comprises security experts who act as adversaries to overcome cyber security controls.
This approach thoroughly analyzes an organization's systems and security policies to identify weaknesses and design solutions to address those issues.
How to become a red team member?
It is required to have a deep knowledge of cybersecurity and primary programming languages. In general, having some experience working as part of a blue team is necessary. Training and certifications are also essential to prove proficiency in the field.















