It is essential to work in teams to strengthen organizations' security. Regarding cybersecurity, in particular, this job is best done from a red team vs. blue team perspective.
Red teaming implies mimicking the role of an attacker by trying to find vulnerabilities and avoiding cybersecurity defenses within the network. On the other hand, a blue team has a defensive approach: they take precautions and respond to incidents once they have occurred. Both jobs seek to improve the overall security of the company.
But there's more to it than red and blue. Get ready to explore the InfoSec color wheel, the types of exercises and tasks the red and blue teams perform, and the benefits of combining both perspectives.
If you want to learn all about this “colorful” approach and how this will help you improve your company's overall security, keep on reading.
The InfoSec color wheel
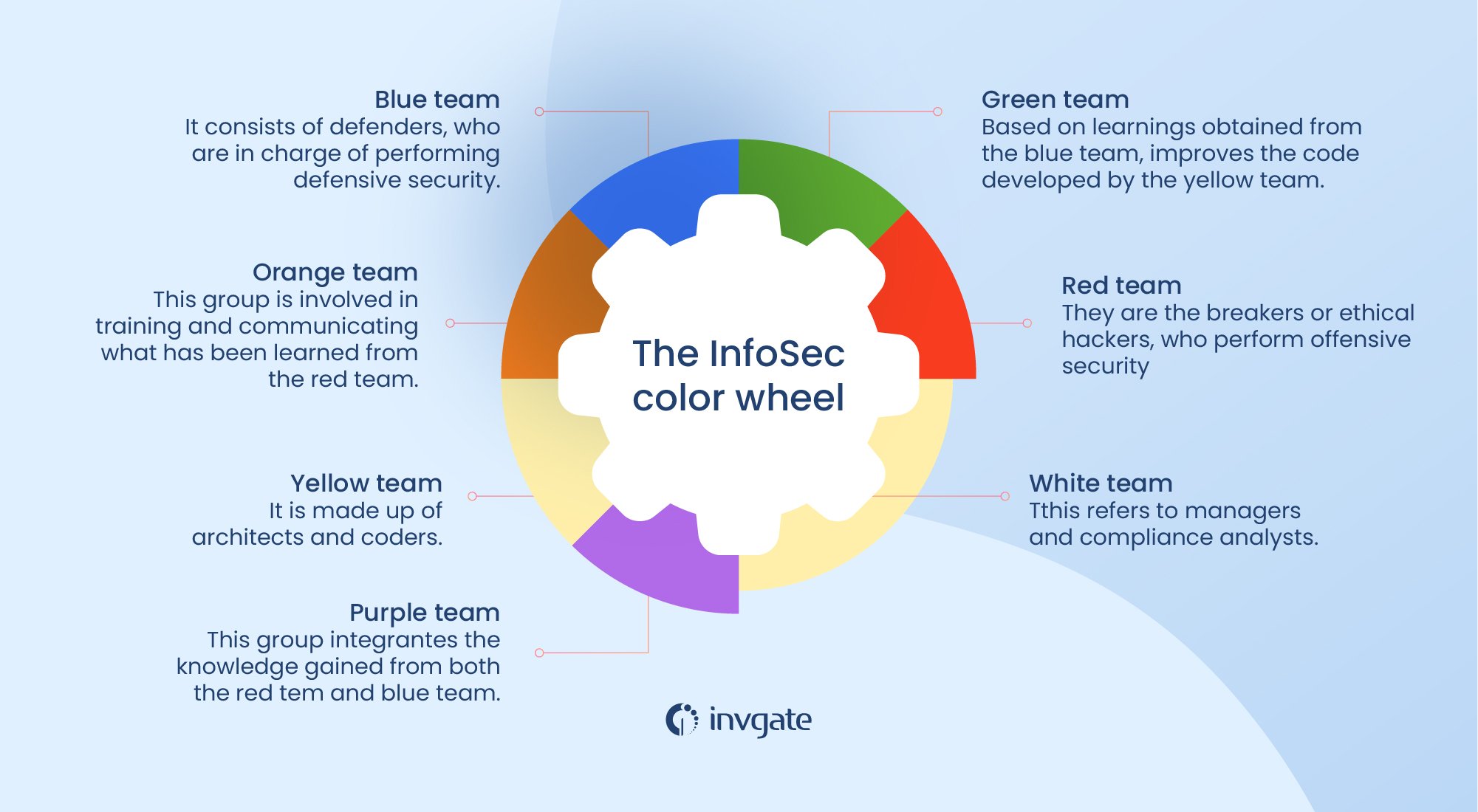
Cyber Specialist April C. Wright developed the InfoSec color wheel as an expansion of the concept defined to classify the red team and blue teams. This perspective includes other colors to advocate collaboration between information security and software development.
The idea is that the security aspect should be involved throughout the development process so that the products have built-in measures or mechanisms to prevent possible intrusions. Here are the colors and their role in terms of security:
- Red team: they are the breakers or ethical hackers who perform offensive security.
- Blue team: consists of defenders, who are in charge of performing defensive shields.
- Purple team: this group integrates the knowledge gained from the red team and blue teams.
- Green team: based on learnings obtained from the blue team, it improves the code developed by the yellow team.
- Yellow team: it is made up of architects and coders.
- Orange team: this group is involved in training and communicating what has been learned from the red team. The orange squad encourages the yellow section to be more aware of possible attacks.
- White team: this refers to managers and compliance analysts.
What is a red team?
A red team comprises security specialists who emulate hackers to overcome cyber security measures. Red teamers are ethical hackers who resort to various techniques to find flaws or weaknesses in the technology and procedures for employees to obtain unauthorized access to the network. The purpose of red teaming is to evaluate security to strengthen the company's security status.
Red team responsibilities
The responsibilities of the red team specialist are the following:
- Determine a target, and do reconnaissance.
- Extract information by breaking into the premises, invading the system, or resorting to social engineering.
- Exploit weaknesses.
- Avoid detection by the blue team.
- Perform penetration testing to evaluate various aspects.
- Develop a report based on the findings and make recommendations to improve security.
To compromise the organization's cyber security, red team members should act like a hacker, which is why they will have to perform the following activities:
- Social engineering through phishing, for example, to trick employees into giving away their credentials.
- Card cloning to enter premises.
- Intercepting communication between employees.
- Penetration testing to identify vulnerabilities in applications.
Red teamer required skills
- Experience: in general, it is required to have gained experience working as a cyber security specialist.
- Creativity: it is necessary to have a creative outlook, bypass defenses, and perform effective social engineering techniques.
- Coding: it is vital to know to code because this will help red teamers be better prepared to identify any possible flaw or vulnerability.
- Social engineering: red teamers should be able to perform social engineering techniques such as phishing or vishing to assess how vulnerable the people within the organization could be to these scams.
- Penetration testing: it is required to know how to identify and exploit different vulnerabilities in the network.
- Threat intelligence: this implies gathering information about potential attacks from various sources.
Red teamer professional profile
A red team expert belongs to the group of security professionals. It could be referred to as an ethical hacker or vulnerability specialist. A read team specialist could be required to have a certification that validates his knowledge in the field.
- Certified Ethical Hacker (CEH)
- Certified Red Team Operations Professional (CRTOP)
- Licensed Penetration Tester (LPT) Master
- Offensive Security Certified Professional (OSCP)
- GIAC Penetration Tester (GPEN)
- GIAC Exploit Researcher and Advanced Penetration Tester (GXPN)
What is a blue team?
As opposed to the red team, which has an offensive outlook, the blue team has a defensive strategy to protect the company's information and other assets.
Blue team responsibilities
A blue team is part of a security operations center responsible for defending and preventing red team attacks and actual life attacks performed by threat actors. If the attack in the red team scenario is successful, then the blue team is in charge of the incident response, meaning the process by which the organization handles an attack.
The security team should analyze the strategies used in the intrusion and implement mechanisms to prevent that from happening again in the future.
These are some of the activities by a blue team member:
- Use Intrusion Detection Systems (IDS) to identify any possible attack and defense of the organization's infrastructure.
- Perform DNS assessments to make sure there are no activities that could compromise the security of the network.
- Manage firewall controls and end-point software to protect workstations.
- Conduct a footprint analysis to identify any possible breach.
Blue teamer required skills
From a defensive perspective, a blue team member must have the following skills:
- Attention to details: it is essential to be oriented to more information as this is crucial to identify any possible security flaw or vulnerability.
- Perform risk assessment: blue teamers need to know how to handle assessment tools to identify risk and establish resources and means to protect assets at stake.
- Handle detection systems: it is required to know specific tools such as intrusion prevention systems (IPS), intrusion detection systems (IDS), and security and information event management software (SIEM).
- Carry out threat intelligence: this implies gathering data about the different risks and threats to the organization that might be exposed. This is important to design a reliable defense plan.
Handle hardening techniques: it is necessary to know how to fix security holes and vulnerabilities identified. - Use detection systems: it is required to use packet sniffers, security and information event management (SIEM) software, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Blue teamer professional profile
A blue team is part of the defensive strategy within a security team. Professionals in this field could also be referred to as cybersecurity analysts or threat intelligence analysts. There are some other roles related to blue teaming such as security architect or information security expert.
This type of job is ideal for someone who has an analytic mindset and likes planning and following set out regulations and standards. Blue team members might be required to have certain certifications to validate their knowledge such as the following:
- Certified Information Systems Auditor (CISA)
- GIAC Security Essentials Certification (GSEC)
- Certified Information Systems Security Professional (CISSP)
- GIAC Certified Incident Handler (GCIH)
- CompTIA Advanced Security Practitioner (CASP+)
- Systems Security Certified Practitioner (SSCP)
5 benefits of the red team vs blue team approach
The red team vs blue team approach has several benefits in terms of cybersecurity:
- Healthy competition. The competition between both groups can result in improved performance.
- Strong security. While the red team identifies vulnerabilities in the system, the blue team knows how to address those issues.
- Cooperation. This can be achieved by designing a strategy that improves communication between both teams. The red team shares the threats identified and their knowledge of hacking techniques, while the blue team discloses their defensive mechanisms.
- Response procedure. Combining both types of information and outlooks makes it possible to design better response plans.
- Raise awareness. Both teams work together and help raise security awareness among other organization members.
How to set up a red team/blue team exercise?
The idea behind the red team-blue team exercise is that the first one attacks the network while the other group tries to defend it. The objective of this exercise is not only to pinpoint security issues but also to get information that will help improve those issues. It is also an opportunity to raise awareness and train employees on the importance of taking precautions and the need to include cybersecurity when developing products and services.
Steps to perform this exercise
Step 1: Brainstorming
Getting both teams together and devoting at least a day to discussing possible scenarios is recommended. This will help red and blue teamers improve their techniques before the exercise starts.
Step 2: Formulation of general goals
It is essential to establish the goals to accomplish. The ultimate objective is to improve security, but it could be helpful to narrow down the scope and decide to focus on two or three aspects in particular.
Step 3: Setting limits
Before starting the game, it might be helpful to set limits. Is anything going to be off-limits? Can the red team go to any extent? How far can they go when doing simulation? The fewer limits, the better because it will be more realistic. Maybe there are specific issues that the company prefers to preserve.
Step 4: Data collection
Determine how the data from the exercise will be collected and shared. It is imperative to carry out the activity and make sure the organization profits from the whole experience. Organizing how the information will be gathered and how the reports will be delivered is crucial.
Key takeaways
The red team imitates the mind of a hacker who wants to get into your organization, while the blue team is in charge of defending the network from any possible attack. The interaction between these two groups will give your company valuable insights on improving your security measures.
Within the InfoSec color wheel, other teams receive different colors (yellow, purple, green, orange, and white) depending on the tasks performed. The central concept here is that all the organization members should include cybersecurity in their routines and jobs. This aspect should be built into the products developed and part of their daily lives so that they do not fall into any trap and end up opening the organization's doors to a cyber attacker.
Frequently Asked Questions
Why is it called a red team?
The red team is made up of cybersecurity experts who play the role of an attacker intending to identify security holes in a network.
Which is more challenging, the red team or the blue team?
Both jobs require to be updated. Red teamers must be creative and persistent to break into a well-defended network. Blue teamers must put a lot of energy into defending the organization against possible attacks. This is hard and stressful.
What is the purple team?
This team is responsible for compiling and sharing the cybersecurity learnings obtained from the red team vs blue team interaction.
What is the goal of a red versus blue team?
The ultimate goal is to improve cybersecurity measures and increase employees' awareness and compliance.
What is a gray team in cybersecurity?
It is made up of cybersecurity experts who sometimes violate ethical standards to discover vulnerabilities but do not have the malicious intent of a black hat hacker. As opposed to ethical hackers who break into the network at the request of the organization to perform an assessment, gray teamers might do this without permission. But once they find the vulnerability, they will disclose it to the company so that it can solve it.















