Apple released a series of patches today to address zero-day vulnerabilities CVE-2023-32434 and CVE-2023-32435. As Patch Management’s best practices indicate, the company advised updating the following products: iOS, iPadOS, macOS, watchOS, and Safari browser.
Keep reading to understand the extent of the exploits and discover how to easily spot outdated devices on your network using InvGate Asset Management.
About CVE-2023-32434
The CVE-2023-32434 exploit corresponds to a vulnerability that enabled attackers to execute arbitrary code with kernel privileges. This affected Apple iOS, iPadOS, macOS, and watchOS.
The vulnerability was patched starting with the following software versions:
- watchOS 8.8.1
- iOS 16.5.1 and iPadOS 16.5.1
- iOS 15.7.7 and iPadOS 15.7.7
- macOS Big Sur 11.7.8
- macOS Monterey 12.6.7
- macOS Ventura 13.4.1
- watchOS 9.5.2
About CVE-2023-32435
Meanwhile, CVE-2023-32435 corresponds to a memory corruption issue that could also potentially lead to arbitrary code execution.
This particular exploit was patched in the following software versions:
- Safari 16.4
- iOS 16.4 and iPadOS 16.4
- macOS Ventura 13.3
- iOS 15.7.7 and iPadOS 15.7.7
How to find devices exposed to CVE-2023-32434 and CVE-2023-32435 with InvGate Asset Management
If you want to detect which devices in your organization need immediate attendance, you should leverage InvGate Asset Management's features.
All you need to do is type the following commands in the search bar:
- "Software name, is:[name of the software]"
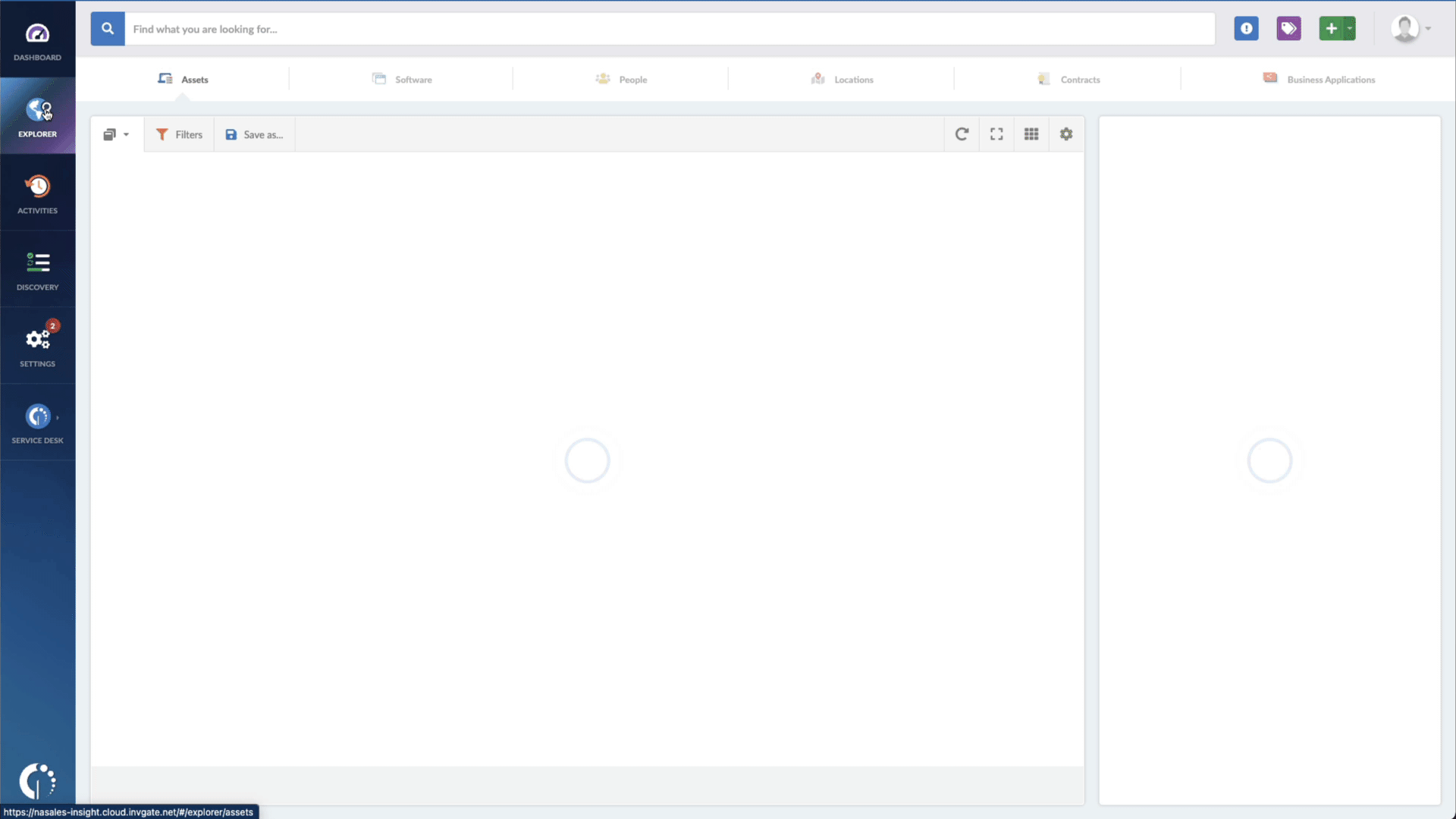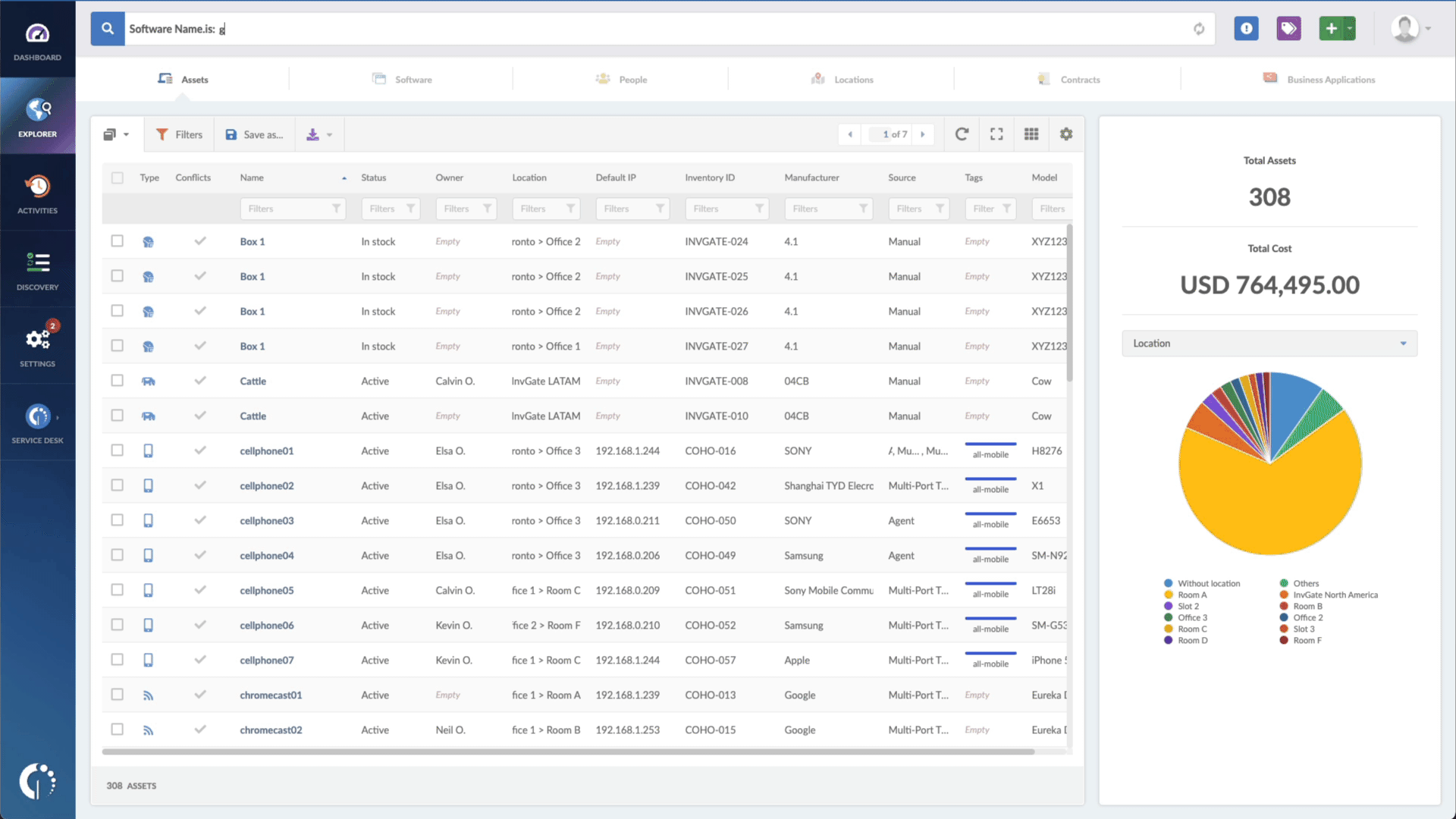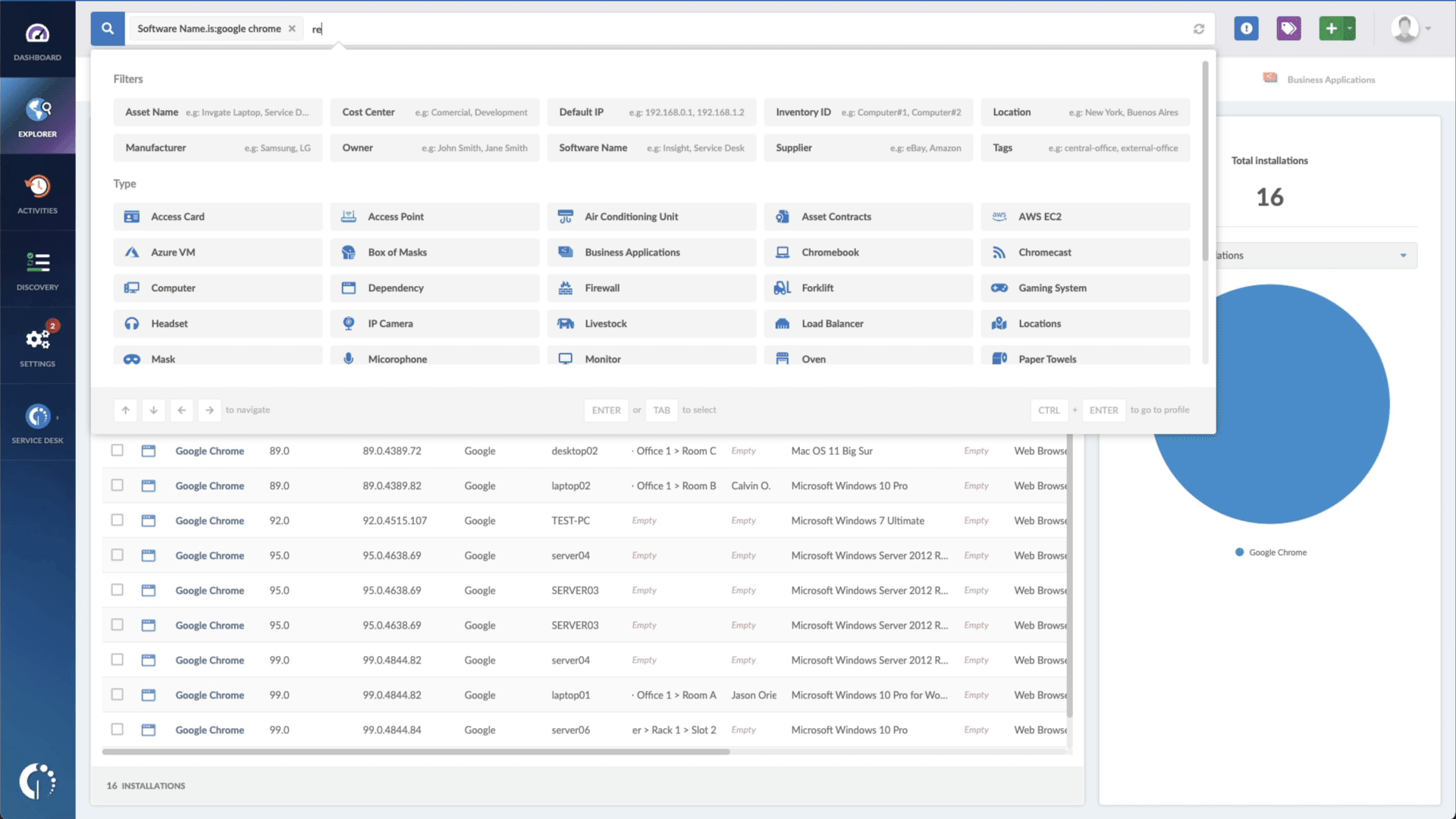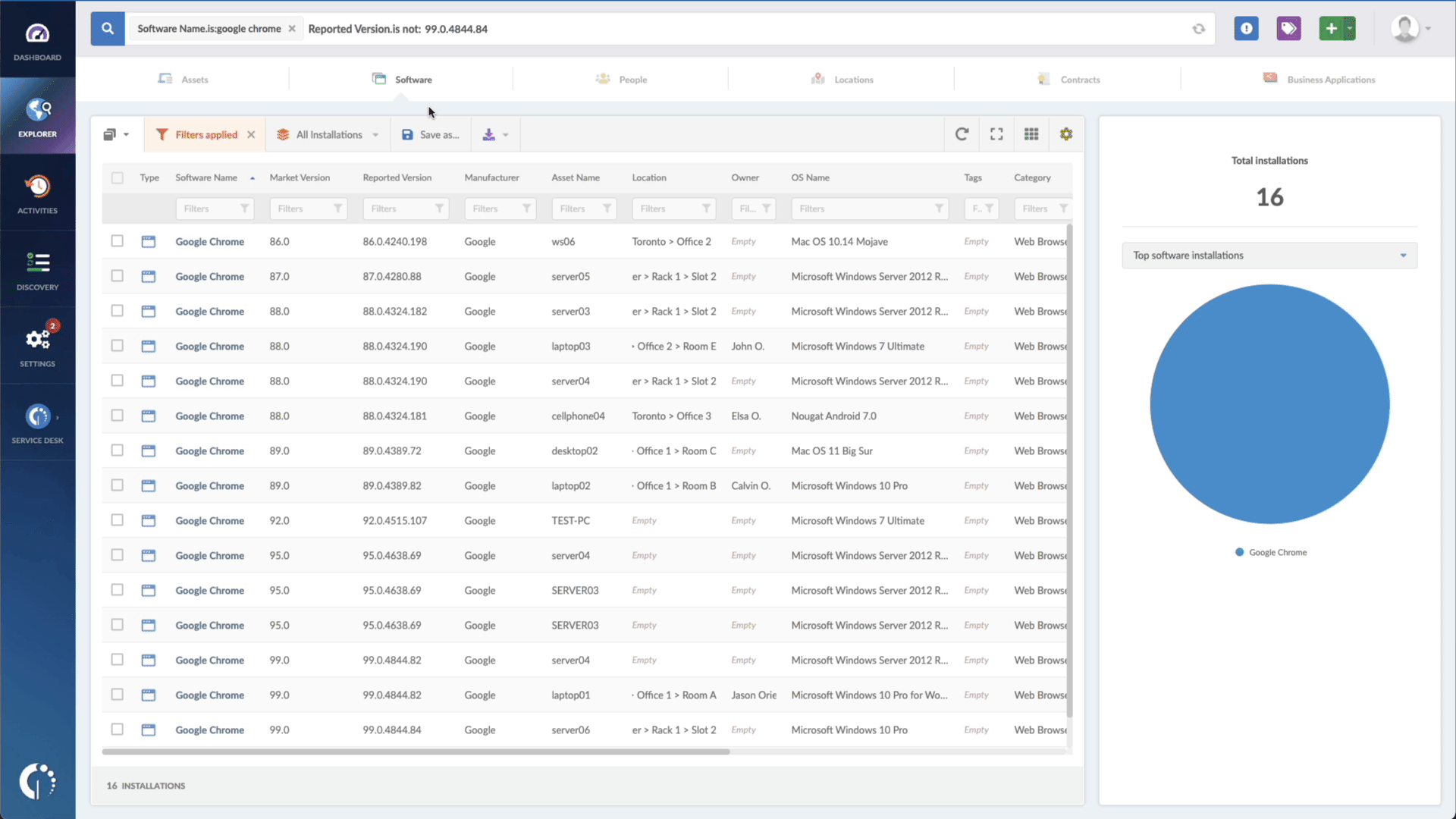
- And right next to that, "Reported version, is not:" and paste the patched version.
And voilá! In a few seconds, you'll have a complete list of vulnerable devices to act upon. Remember that you can download the information in CSV and pass it along to your agents so they can see the updates through.
If you need more information, check out our video on how to find vulnerable devices for patching.
In short
With CVE-2023-32434 and CVE-2023-32435, Apple added two more exploits to the list of known vulnerabilities exploited in 2023. Both zero-days allowed attackers to execute arbitrary code and affected several Apple products.
The company informed that the issues might have been "actively exploited against versions of iOS released before iOS 15.7" and thus recommended the rapid installation of the released patched versions.
If you need a hand identifying the devices that require the update, add InvGate Asset Management to your Vulnerability Management strategy. Request our 30-day free trial and see how you can easily filter your assets right away!
















