In response to the ever-present cybersecurity landscape, Apple has taken a proactive approach by releasing comprehensive security updates across its operating systems. Among the critical vulnerabilities addressed is the noteworthy CVE-2023-32409, which has captured the attention of users and experts alike.
In this blog post, we’ll take an in-depth look at CVE-2023-32409, its implications, and the actions Apple users should take to protect their devices with InvGate Asset Management.
Let's unlock the knowledge you need to fortify your digital assets and maintain a secure online presence in the face of evolving cyber-attacks.
About CVE-2023-32409
CVE-2023-32409 is a zero-day vulnerability that can allow a remote attacker to "break out of Web Content sandbox." This type of sandbox escape vulnerability can be particularly dangerous as it enables unauthorized access to the underlying operating system, potentially leading to the execution of arbitrary code and unauthorized access to sensitive data.
Given the severity of CVE-2023-32409, as well as CVE-2023-28204 and CVE-2023-32373, Apple users are strongly advised to update their devices immediately to ensure protection against potential attacks. The following updates should be applied:
- watchOS 9.5
- tvOS 16.5
- macOS Ventura 13.4
- iOS/iPadOS 15.7.8
- Safari 16.5
- iOS/iPadOS 16.5
How to find devices exposed to CVE-2023-32409 with InvGate Asset Management
InvGate Asset Management offers a wide array of robust functionalities to help you easily detect devices in your organization that may be at risk from CVE-2023-32373, requiring urgent attention. To make the most of these capabilities, just follow the provided instructions:
- Open InvGate Asset Management and go to the Explorer tab.
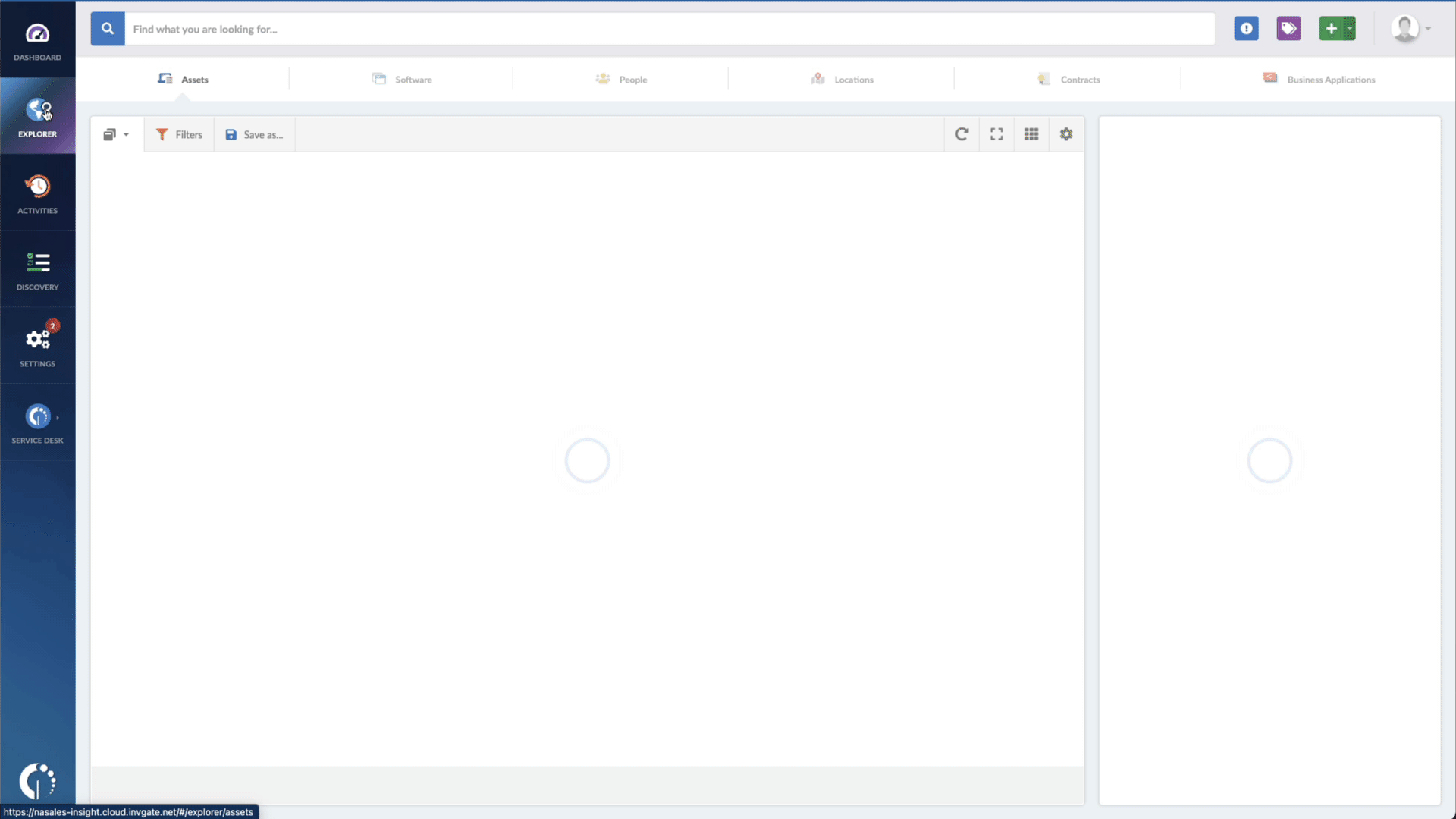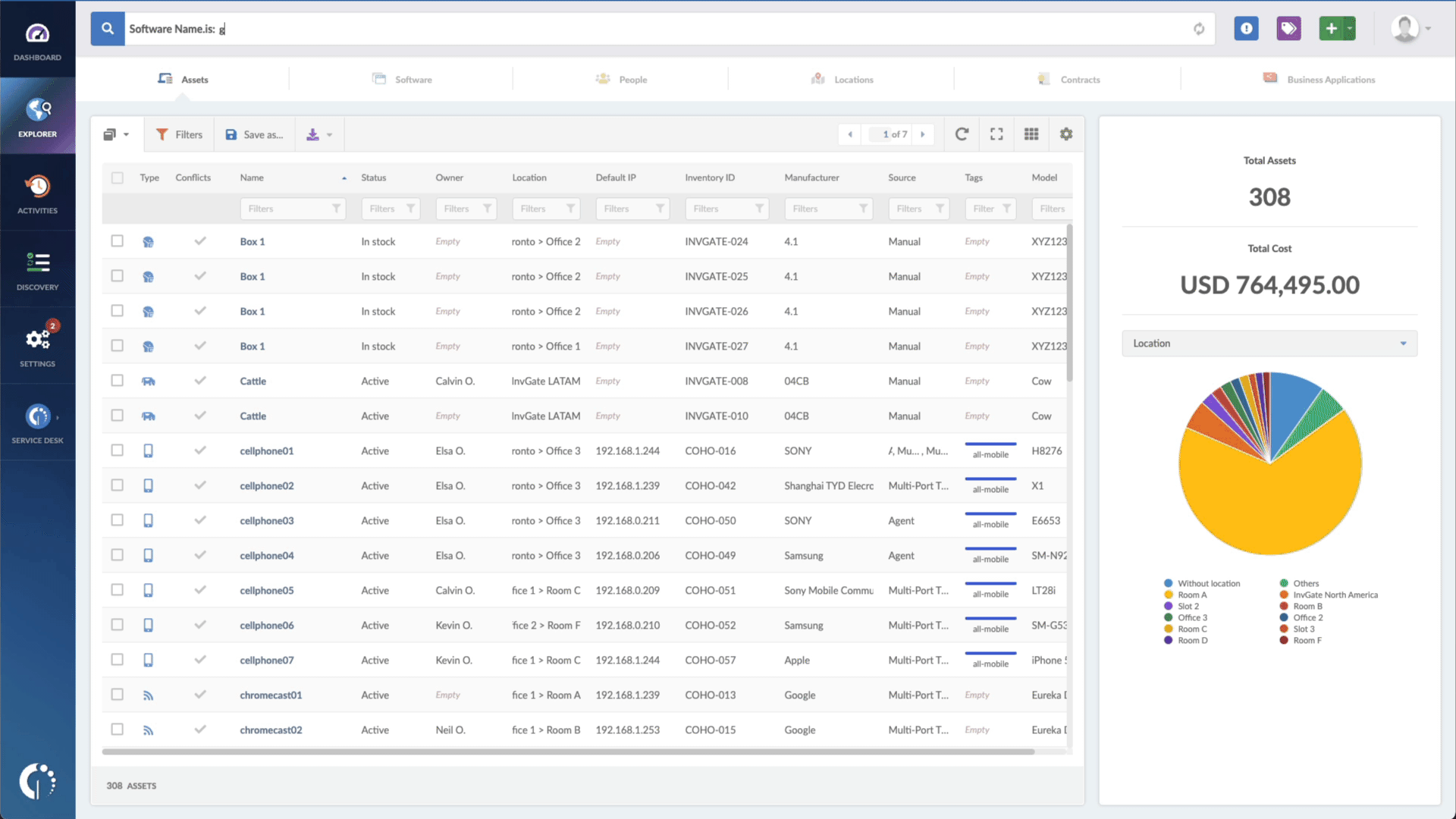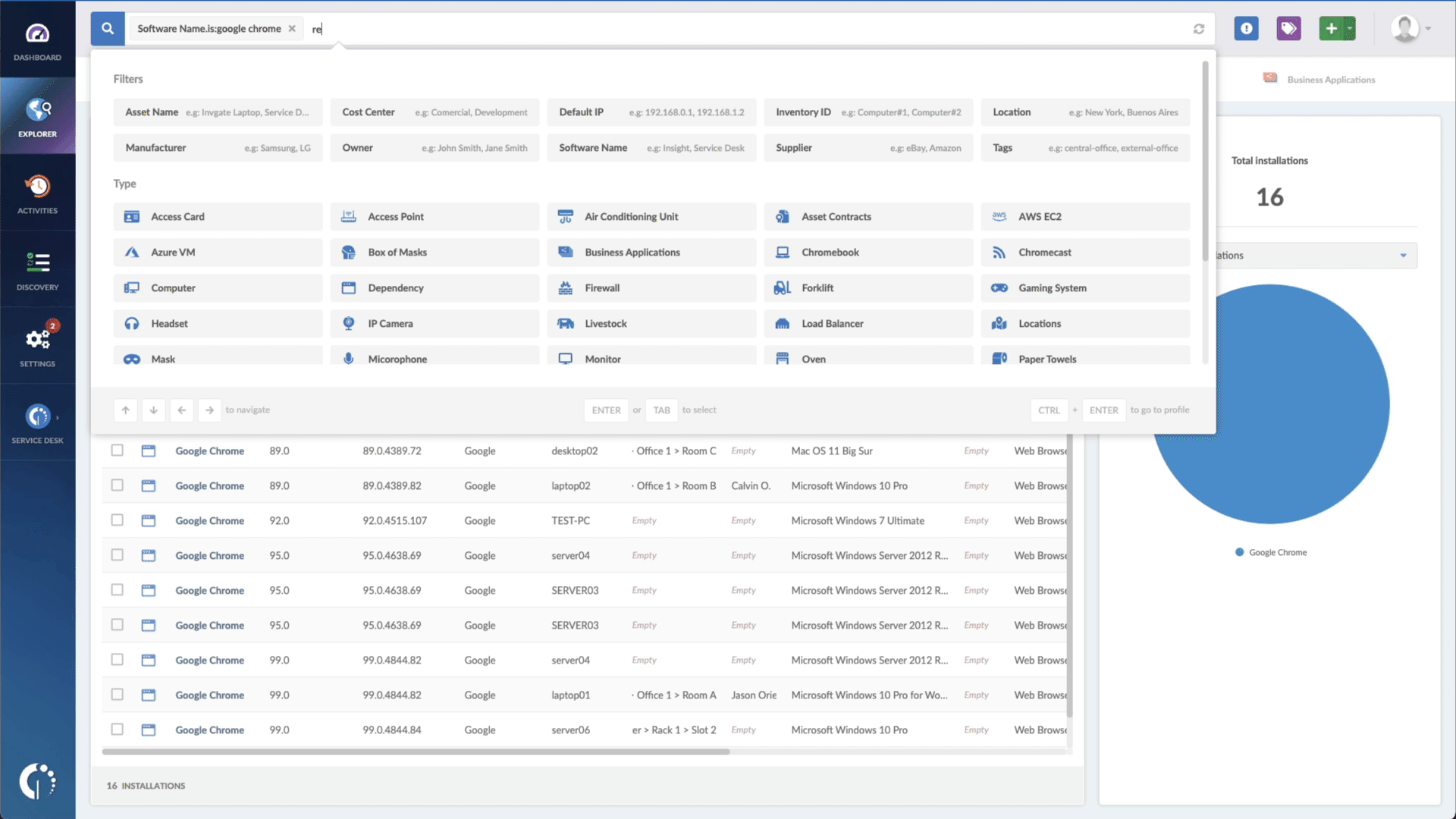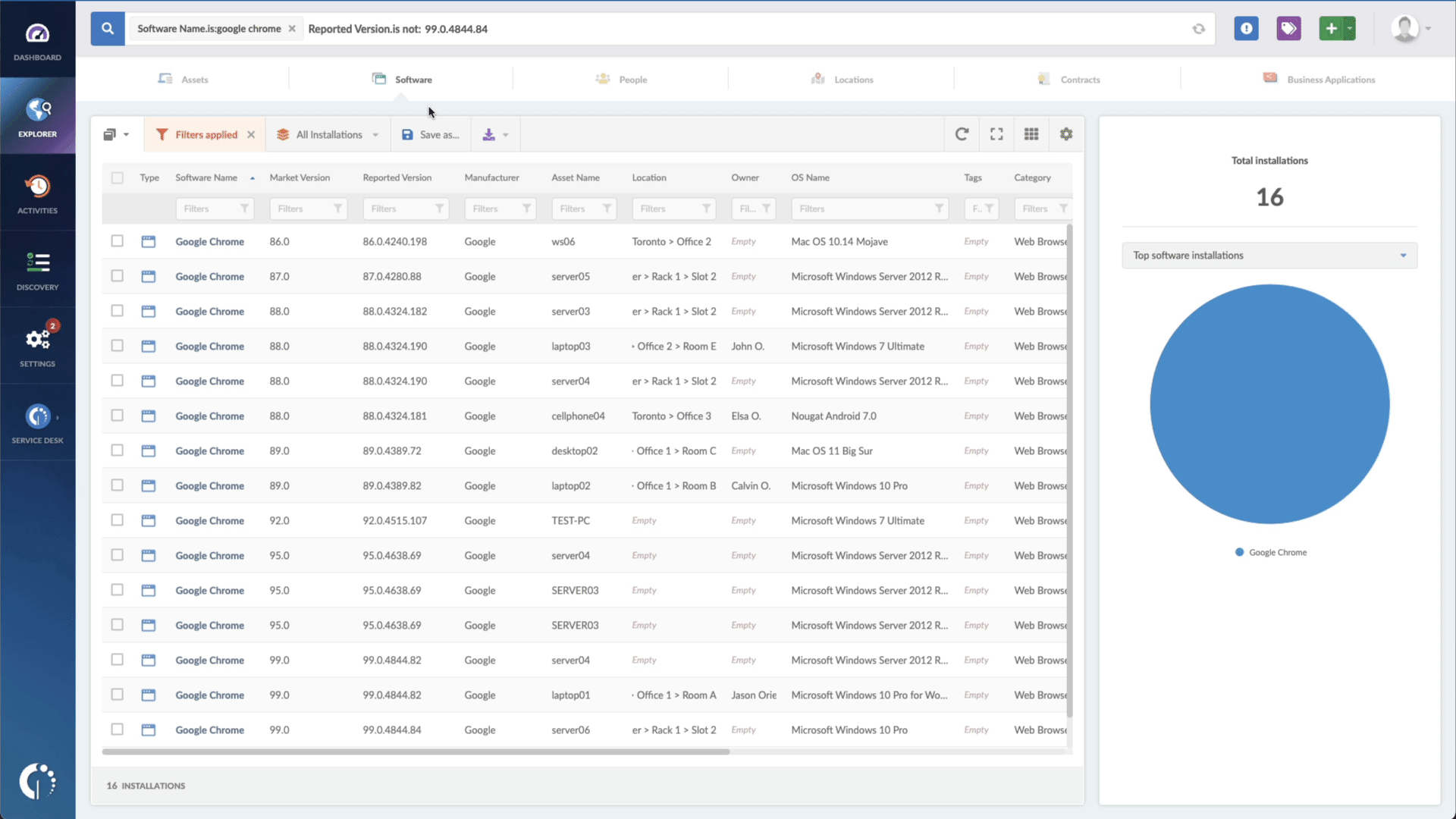
- Type in the Search bar “Software name, is:[name of the software]” to filter all Apple devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version.
That's all! Within seconds, you'll have access to a comprehensive list of vulnerable devices requiring your attention. You can easily download this information in CSV format and share it with your team to ensure they can oversee and implement the necessary updates.
For more details, watch our video showcasing identifying vulnerable devices for patching.
The bottom line
The discovery and patching of vulnerabilities like CVE-2023-32409, alongside the list of known vulnerabilities exploited in 2023, are a reminder of the ever-present threats in the digital landscape. Users must remain vigilant and promptly update their devices to the latest versions to mitigate the risk of falling victim to cyberattacks.
Integrate InvGate Asset Management into your Patch Management strategy to comprehensively understand your devices' update status. This solution empowers you to prioritize and apply critical security updates, guaranteeing a robust, efficient, and secure digital infrastructure. Request our 30-day free trial to experience its capabilities to the maximum extent!
















