Apple released a set of security updates for its various operating systems, including iOS, iPadOS, macOS, tvOS, and watchOS, to address zero-day vulnerability CVE-2023-28204.
In this blog post, we’ll delve into the details of CVE-2023-28204 and explore the steps users can take to protect their devices from its potential risks with InvGate Asset Management.
About CVE-2023-28204
CVE-2023-28204 is a WebKit zero-day vulnerability addressed in Apple's Rapid Security Response update. WebKit is the browser engine powering Safari and all web browsers on iOS and iPadOS. This makes the vulnerability highly significant as it could potentially affect a large user base.
The exploit occurs when WebKit processes specially crafted web content. In the case of CVE-2023-28204, it poses a threat to sensitive information disclosure. When this vulnerability is triggered, attackers might be able to access sensitive data, which could have serious implications for user privacy and data security.
As with CVE-2023-32373, given the severity of CVE-2023-28204 and the potential risks it poses, Apple strongly advises users to update their devices as soon as possible. This issue is fixed in the following versions:
- watchOS 9.5
- tvOS 16.5
- macOS Ventura 13.4
- iOS 15.7.6
- iOS 16.5
- iPadOS 15.7.6
- iPadOS 16.5
- Safari 16.5
How to find devices exposed to CVE-2023-28204 with InvGate Asset Management
InvGate Asset Management offers a range of robust functionalities aimed at helping you easily detect the devices within your organization that may be at risk from CVE-2023-28204 and require urgent attention. To make the most of these capabilities, follow the provided steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:[name of the software]”.
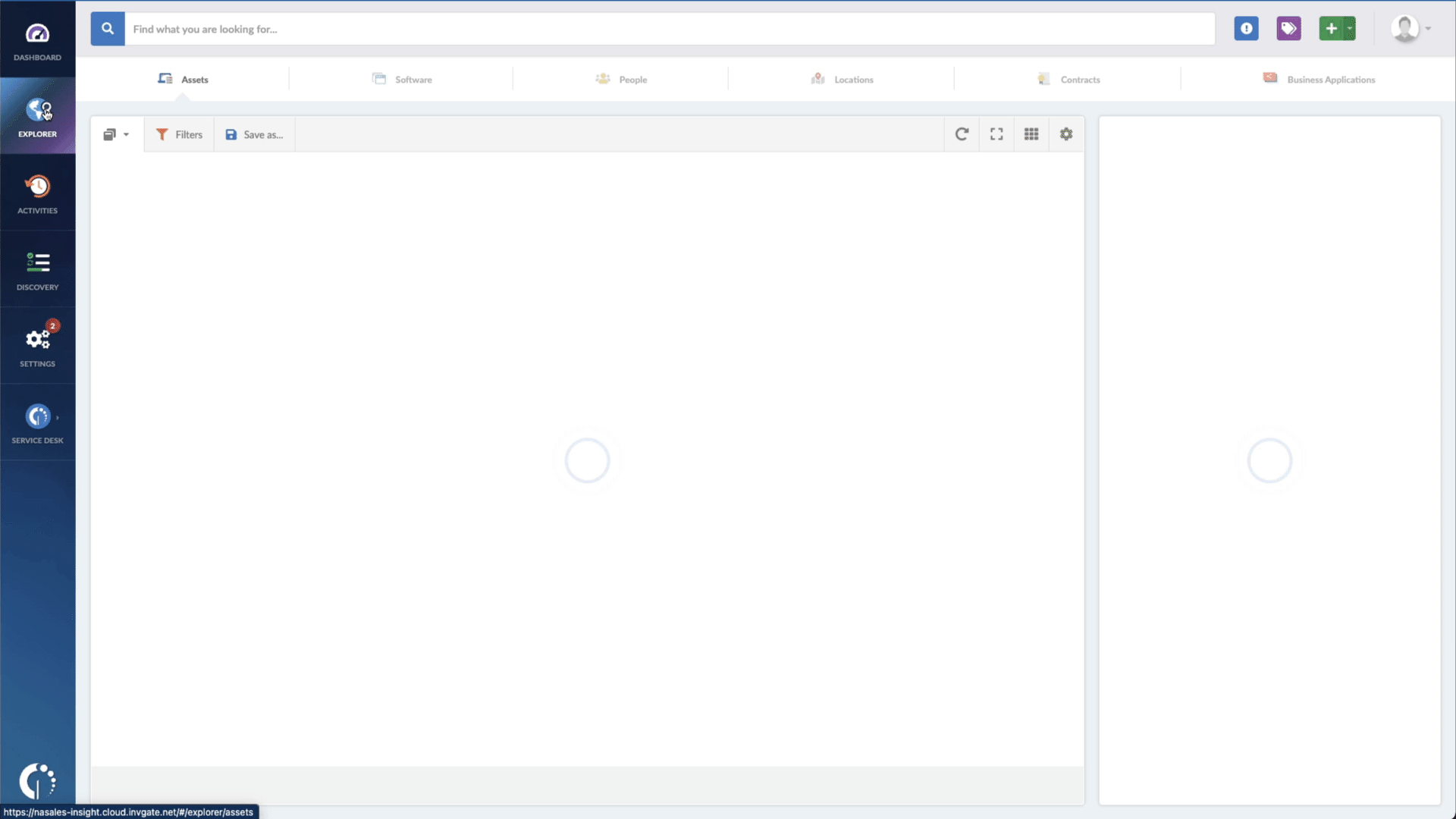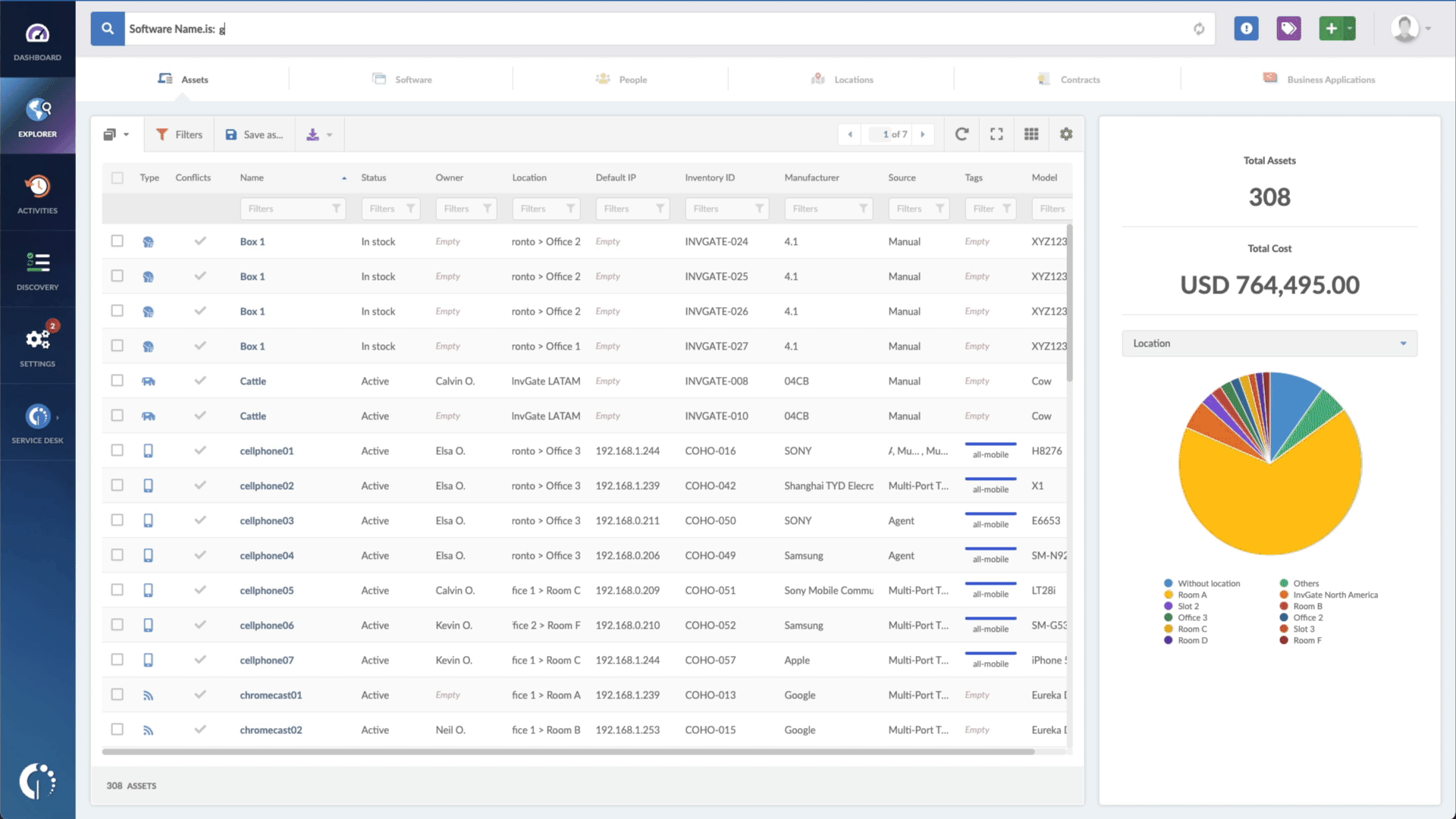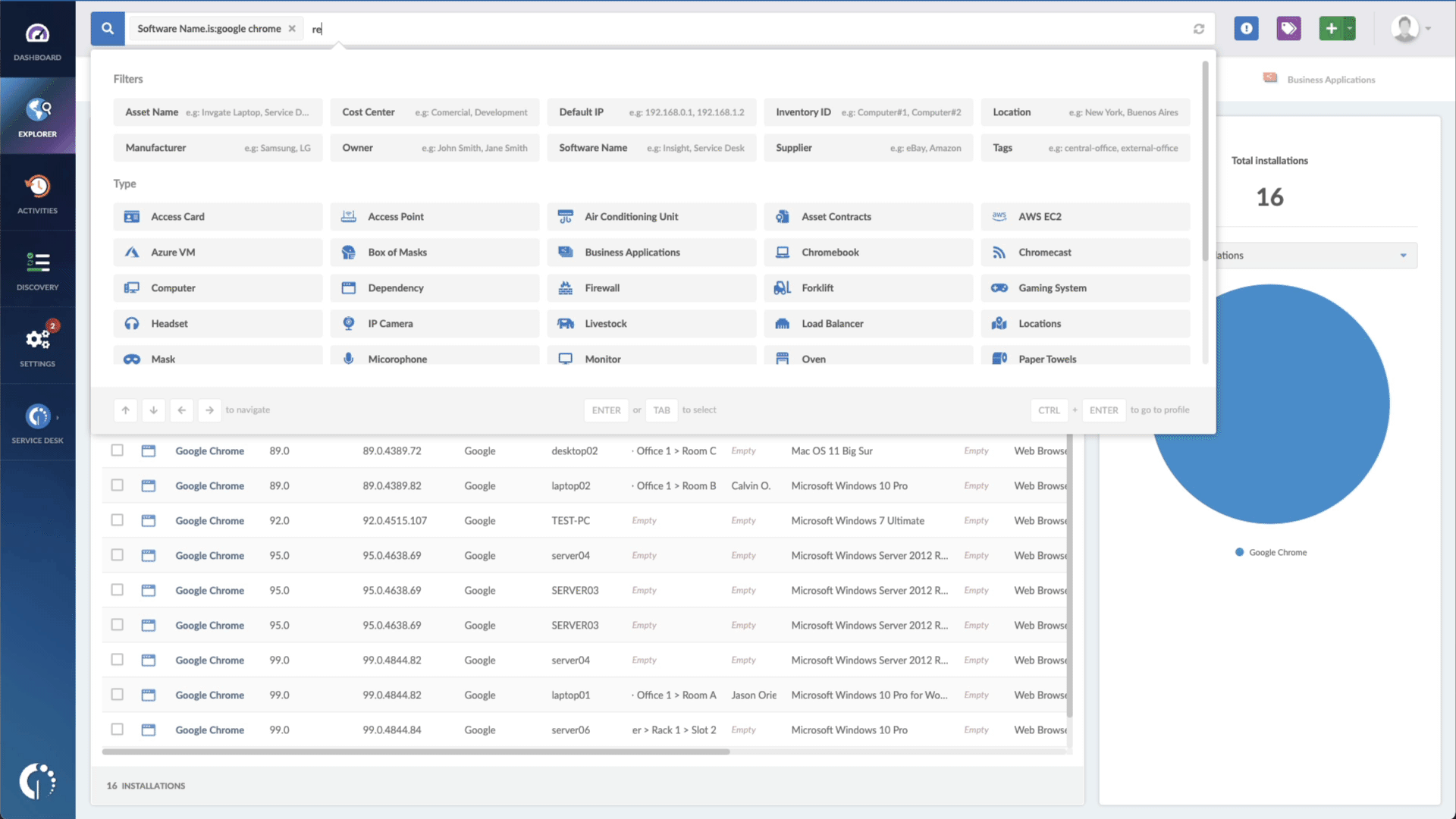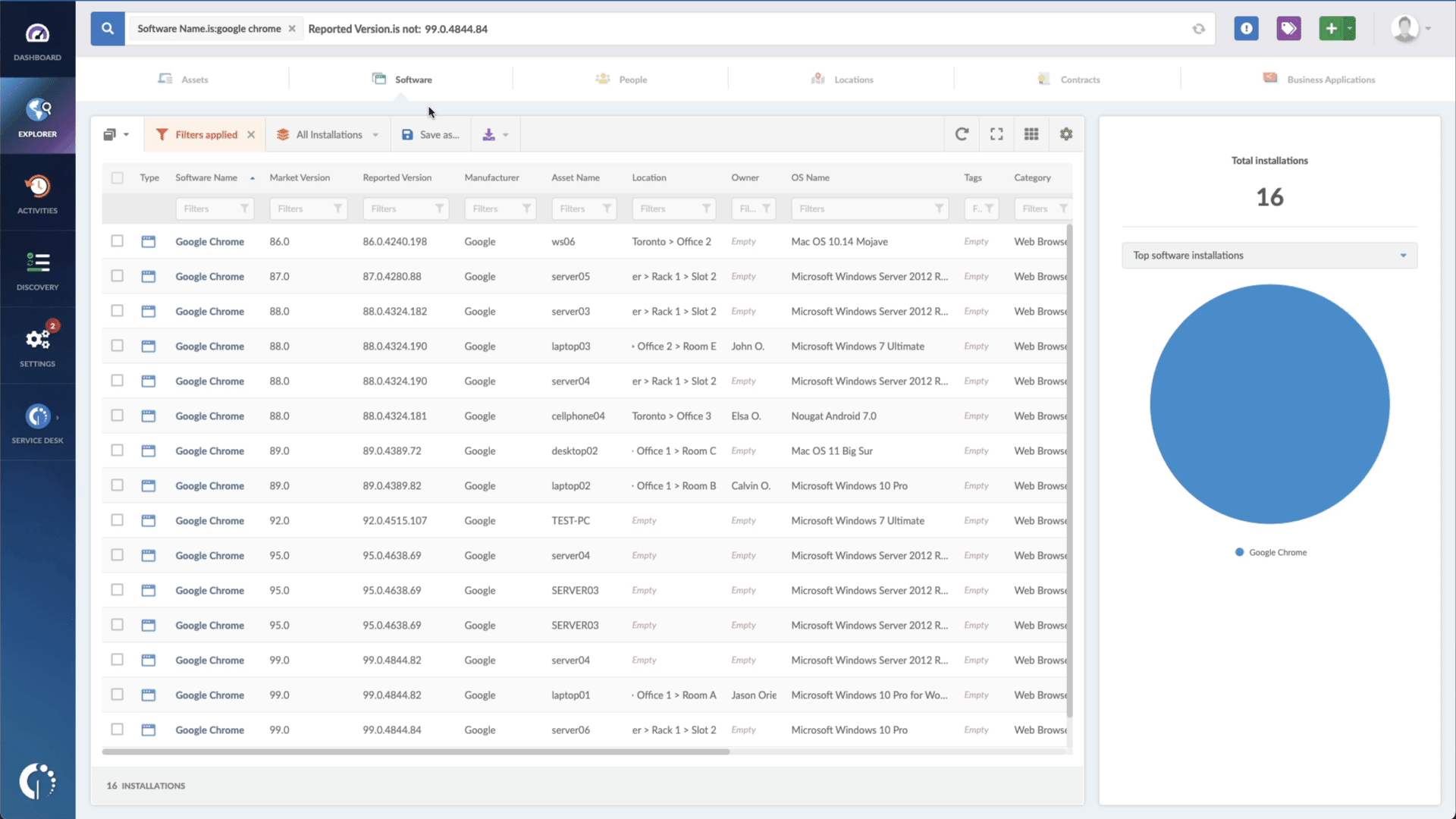
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version.
And there you have it! Within seconds, you'll receive a comprehensive list of vulnerable devices that require attention. You can easily download this information in CSV format and share it with your agents, allowing them to monitor and implement the necessary updates.
For further details, explore our video on locating vulnerable devices for patching.
The bottom line
Security is of paramount importance in today's digital landscape, and timely updates play a critical role in safeguarding our devices and data. CVE-2023-28204, alongside the list of known vulnerabilities exploited in 2023, serves as a reminder of the ongoing efforts required to identify and address potential security threats continually.
Integrate InvGate Asset Management into your Patch Management strategy and gain a comprehensive view of your devices' update status, enabling you to prioritize and apply necessary security fixes for a robust, efficient, and safeguarded digital infrastructure. Request our 30-day free trial and leverage its capabilities!
















