Apple faced a significant security challenge with the discovery of the zero-day vulnerability CVE-2023-32373. This WebKit flaw can lead to arbitrary code execution, putting users of iOS, iPadOS, macOS, tvOS, and watchOS at risk.
In this blog post, we’ll delve into the details of CVE-2023-32373 and how users can safeguard their devices against its potential threats using InvGate Asset Management.
About CVE-2023-32373
CVE-2023-32373 is a WebKit vulnerability that Apple has addressed in its recent security updates. The WebKit engine powers Safari and all web browsers on iOS and iPadOS, making it a crucial component of Apple's operating systems.
This particular vulnerability can be exploited when WebKit processes specially crafted web content. Once triggered, it enables attackers to execute arbitrary code on the affected system. This could potentially lead to unauthorized access, data breaches, and other malicious activities that jeopardize user privacy and security.
Like CVE-2023-28204, which can result in the disclosure of sensitive information, CVE-2023-32373 poses a severe threat to Apple's users. Considering its critical nature and the potential threats it presents, Apple urges users to update their devices to address this issue promptly. The vulnerability has been resolved in the following software versions:
- watchOS 9.5
- tvOS 16.5
- macOS Ventura 13.4
- iOS 15.7.6
- iOS 16.5
- iPadOS 15.7.6
- iPadOS 16.5
- Safari 16.5
How to find devices exposed to CVE-2023-32373 with InvGate Asset Management
InvGate Asset Management provides a comprehensive set of powerful features designed to assist you in effortlessly identifying vulnerable devices within your organization that might be exposed to CVE-2023-32373 and demand immediate action. To fully utilize these capabilities, simply follow the outlined steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:[name of the software]” to filter all Apple devices.
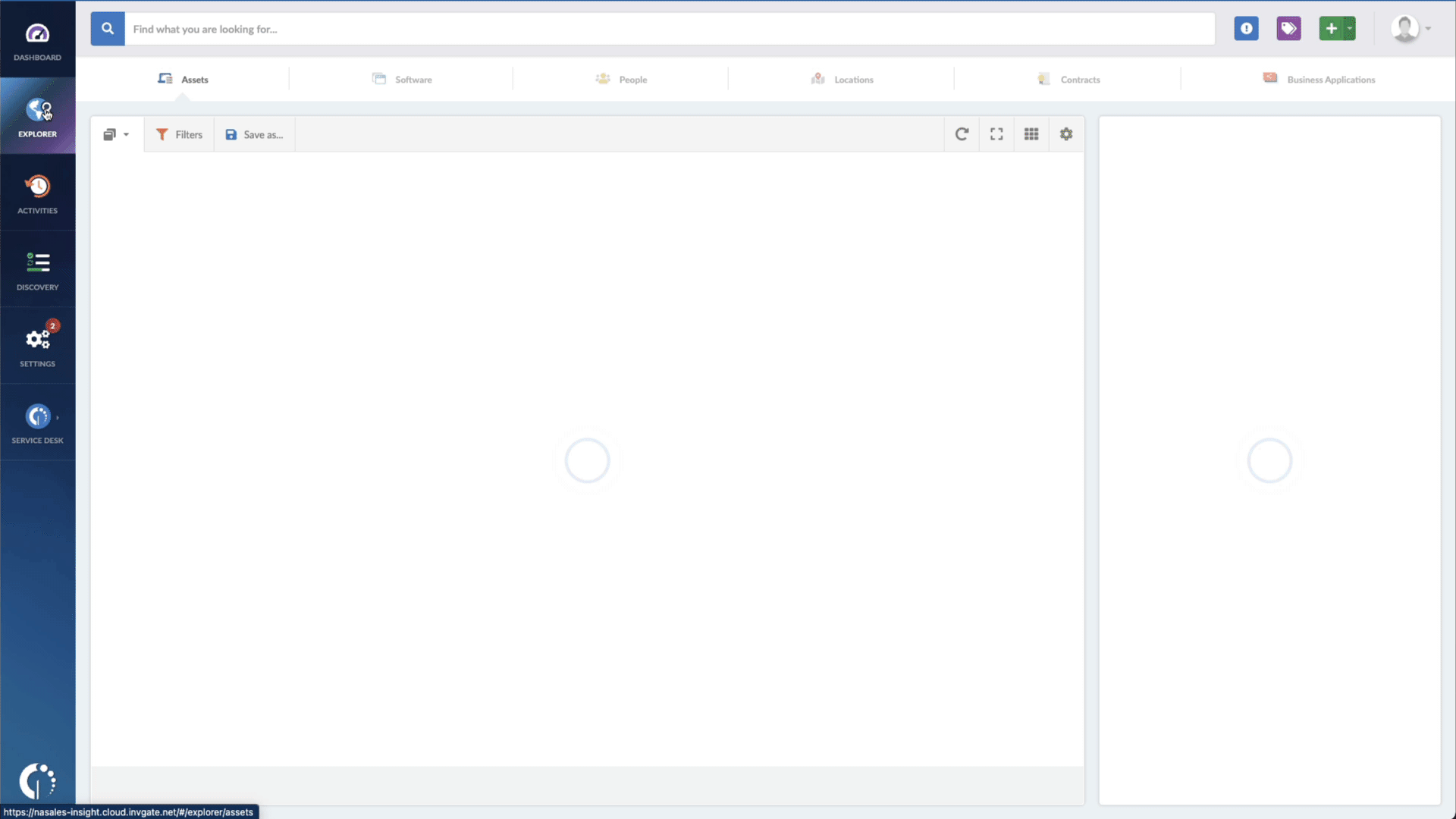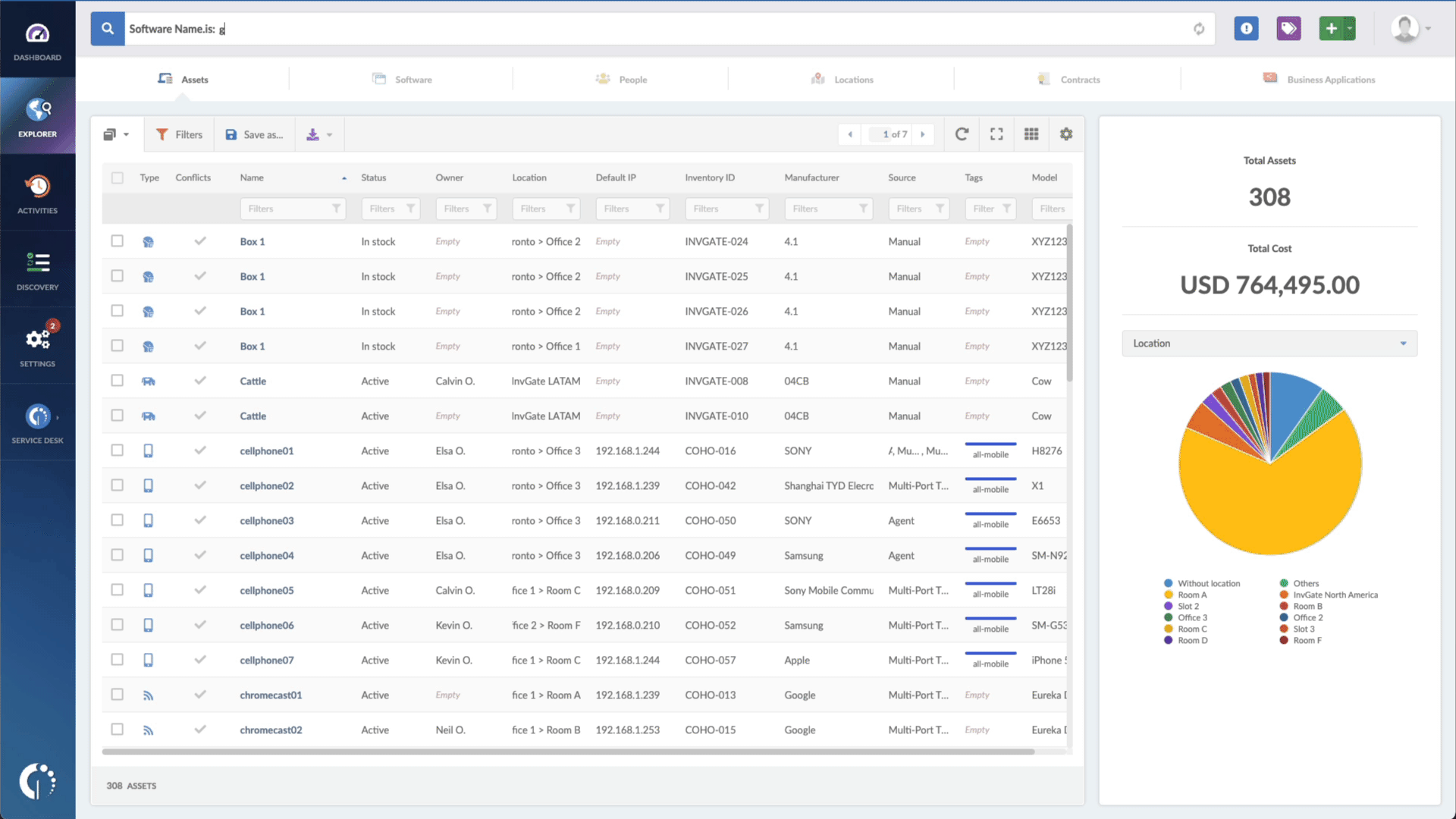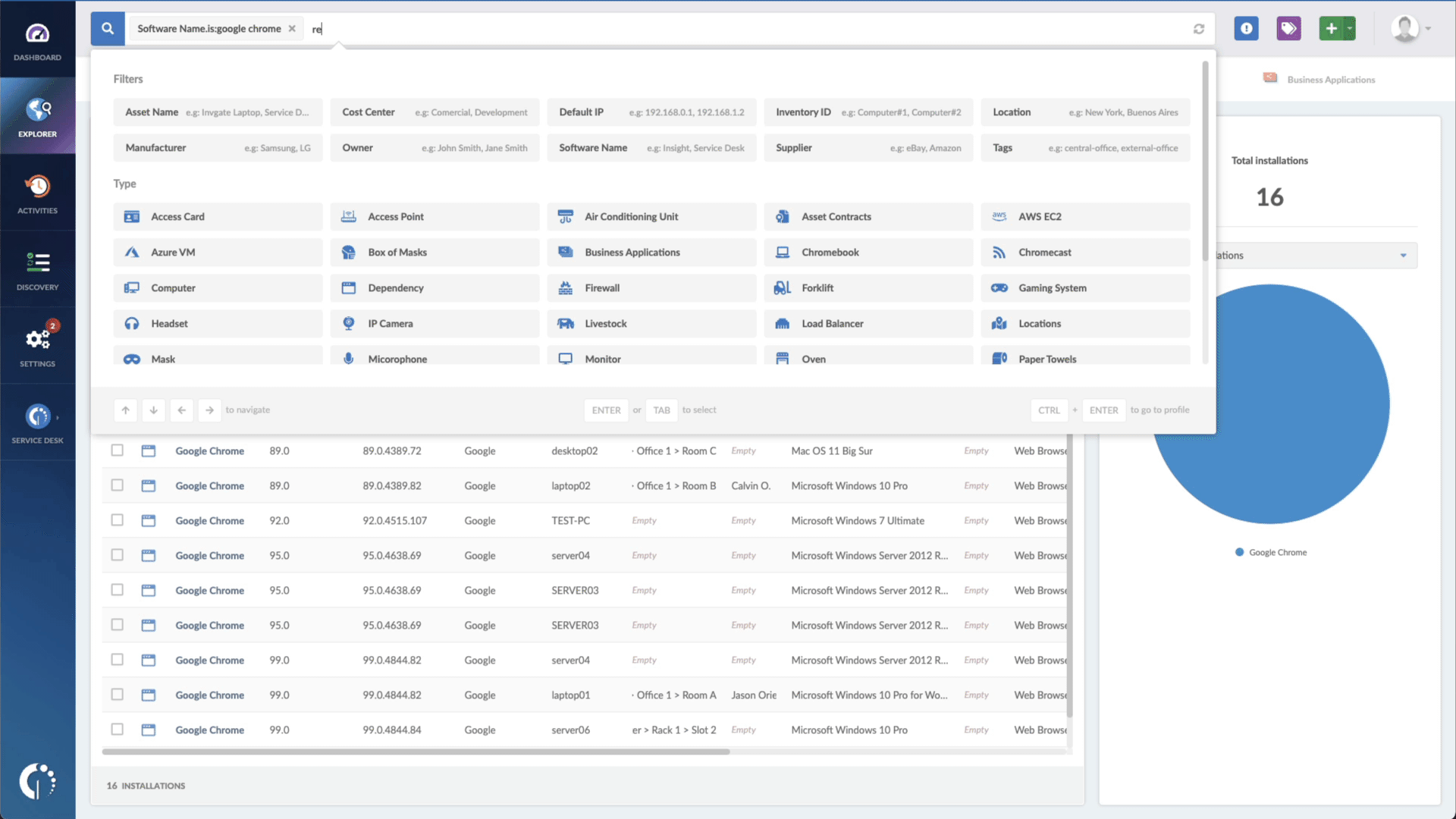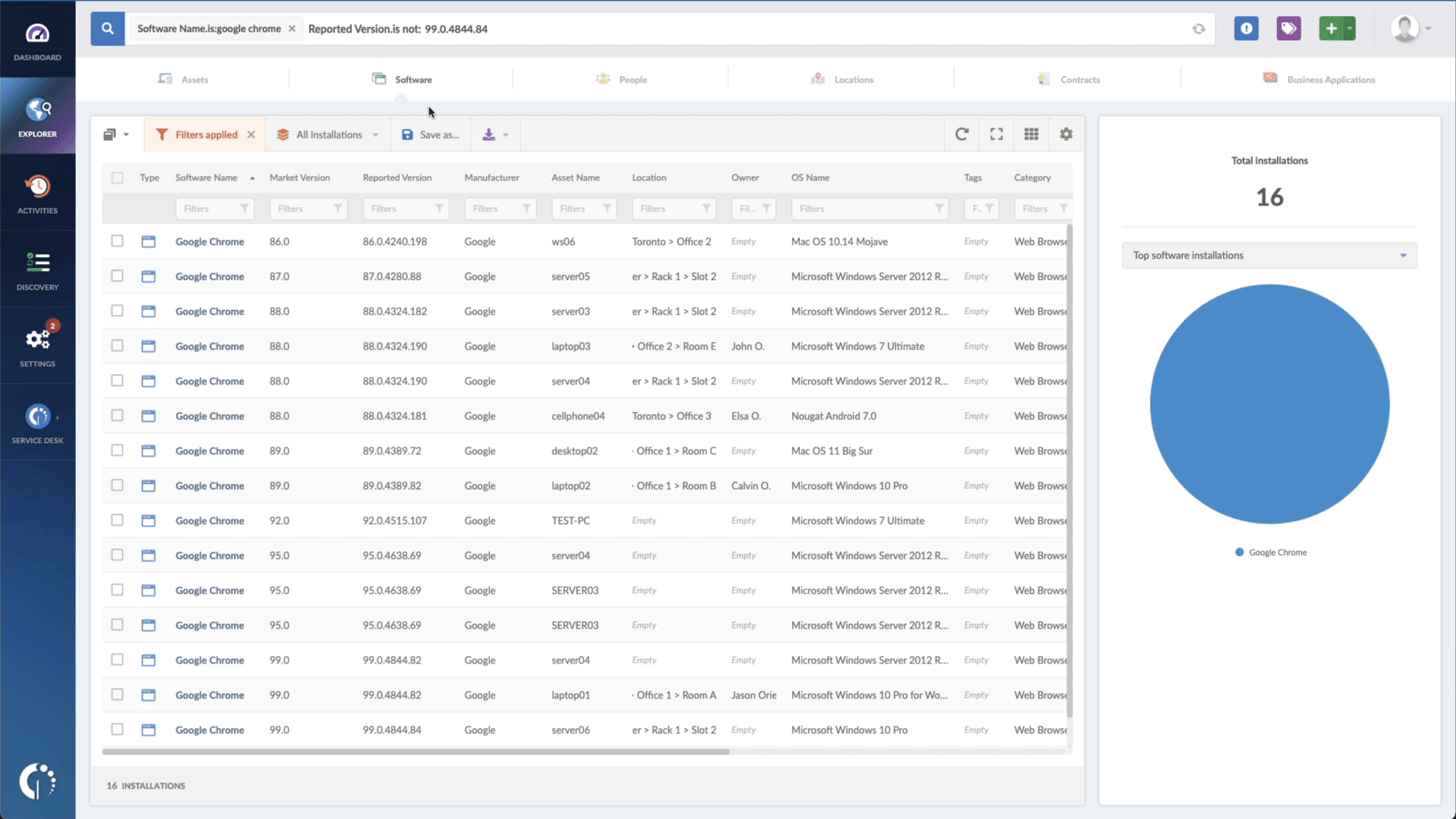
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version.
And that's it! In a matter of seconds, you'll be presented with a detailed inventory of at-risk devices that need your focus. You can effortlessly download this data in CSV format and distribute it to your team, enabling them to oversee and apply the essential updates.
For additional information, check out our video demonstrating how to identify vulnerable devices for patching.
The bottom line
The discovery and prompt resolution of CVE-2023-32373, which joins the list of known vulnerabilities exploited in 2023, demonstrate the importance of regular security updates.
Incorporate InvGate Asset Management into your Patch Management approach to obtain a complete overview of your devices' update status. This platform enables you to prioritize and implement essential security fixes, ensuring a strong, streamlined and protected digital infrastructure. Request our 30-day free trial and harness its functionalities to the fullest!
















