In the ever-evolving landscape of cyber attacks, it's crucial to stay informed about the latest vulnerabilities that may put your devices at risk. One such vulnerability that demands immediate attention is CVE-2023-28206. With potential consequences ranging from unauthorized access to full system control, understanding and addressing this zero-day vulnerability is of paramount importance.
In this blog post, we’ll delve into the details of CVE-2023-28206, its implications, and the steps you can take to protect your devices with InvGate Asset Management for efficient Patch Management.
Let's dive in and arm yourself with the knowledge and insights necessary to safeguard your digital world.
About CVE-2023-28206
CVE-2023-28206 is a security vulnerability that affects Apple devices, specifically macOS, iOS, and iPadOS. This vulnerability was discovered by researchers Clément Lecigne of Google’s Threat Analysis Group (TAG) and Donncha Ó Cearbhaill, the head of Amnesty International’s Security Lab.
CVE-2023-28206, along with CVE-2023-28205, were exploited together to achieve full device compromise.
The vulnerability resides in IOSurfaceAccelerator, which is a framework used by Apple devices to accelerate image and video processing. Exploiting CVE-2023-28206 allows a malicious app to execute arbitrary code with kernel privileges. This means that an attacker who successfully exploits this vulnerability can gain control over the affected device at a deep level, potentially leading to unauthorized access and control of sensitive information.
Potential exploitation scenarios
The exploitation of CVE-2023-28206 can have severe consequences for the security and privacy of Apple device users. By leveraging this vulnerability, attackers can escape the sandbox restrictions imposed by Safari, the default web browser on Apple devices. This privilege escalation enables them to achieve full system access and execute malicious activities without detection.
While the details regarding specific attacks exploiting CVE-2023-28206 are limited, the involvement of Amnesty International's Security Lab suggests that these vulnerabilities were likely used in targeted attacks against human rights advocates. The ultimate goal of such attacks might be to install spyware on targeted devices, compromising the privacy and security of individuals who work in sensitive and high-risk environments.
CVE-2023-28206 patches
Recognizing the severity of these vulnerabilities, Apple promptly responded by releasing security updates to address the issues. Users of macOS, iOS, and iPadOS are strongly advised to update their operating systems to the latest versions. For macOS users, the updates are available for newer versions (13.3.1) and older versions (12.6.5 and 11.7.6). Similarly, iOS and iPadOS users should update to versions 16.4.1 and 15.7.5, respectively. In addition, macOS Monterey and Big Sur users must not only update their operating systems but also ensure they install the Safari update.
How to find devices exposed to CVE-2023-28206 with InvGate Asset Management
You can leverage InvGate Asset Management and its capabilities to identify your devices that demand immediate attention. You can follow the steps outlined below:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:[name of the software]”.
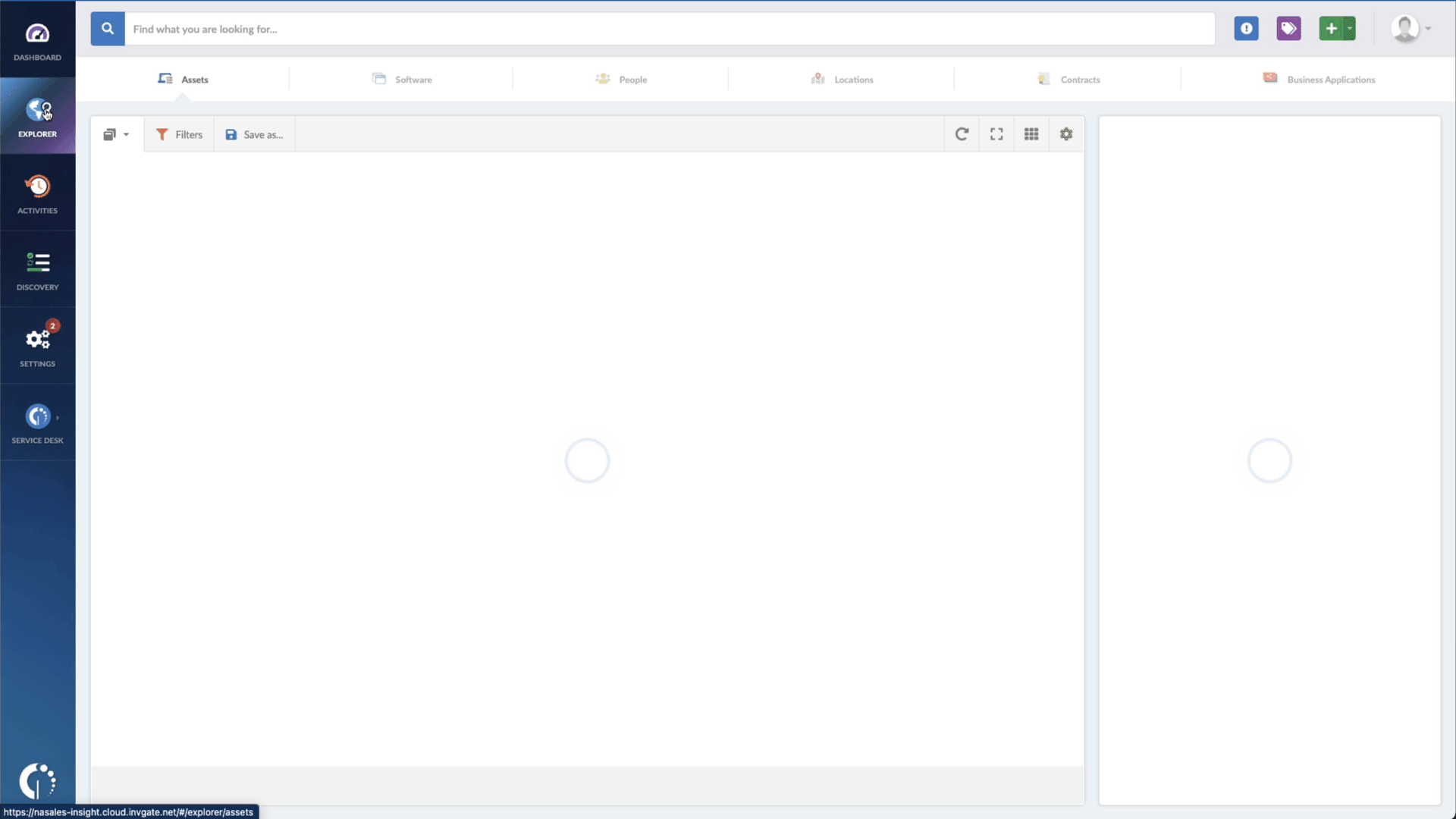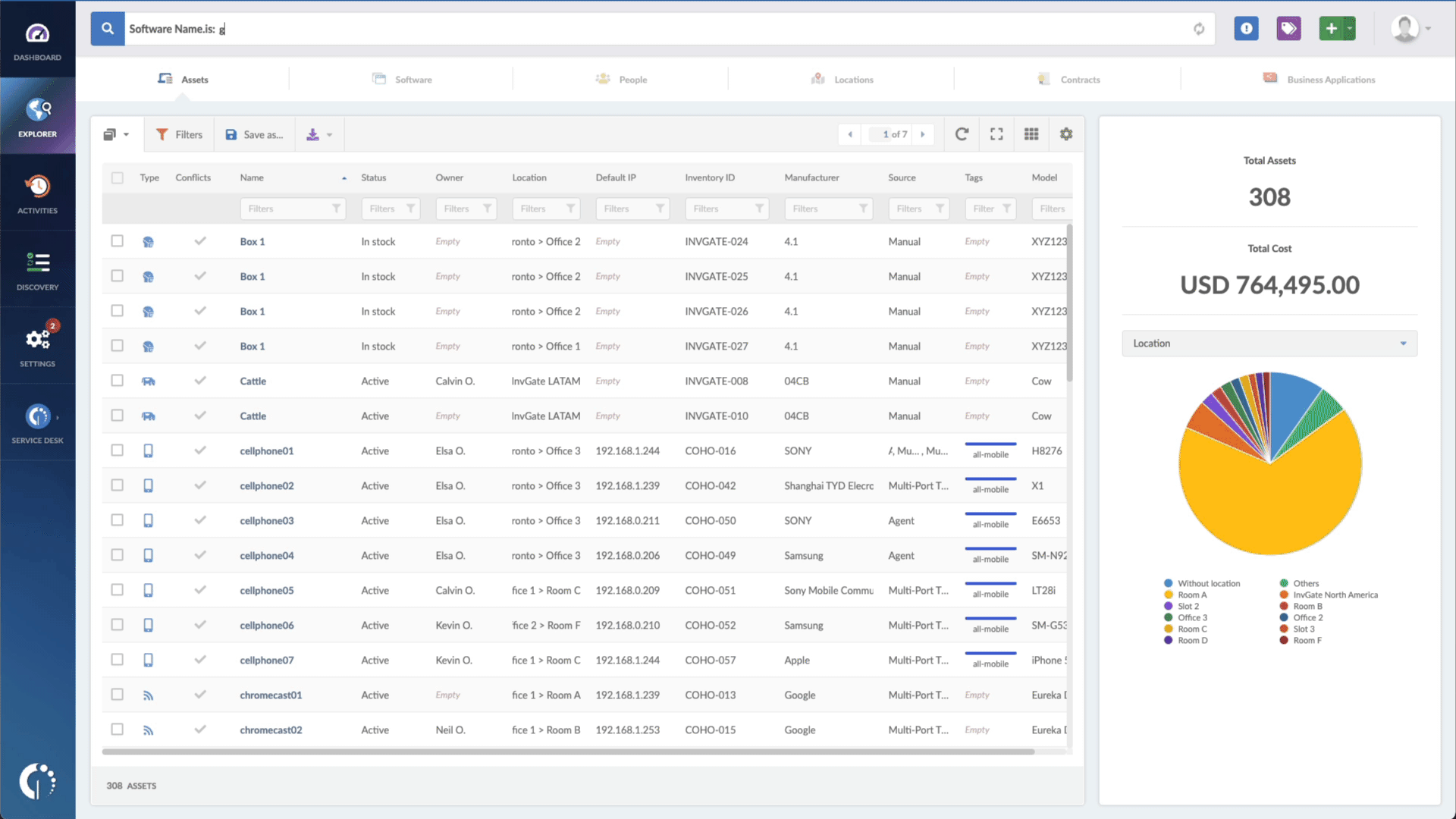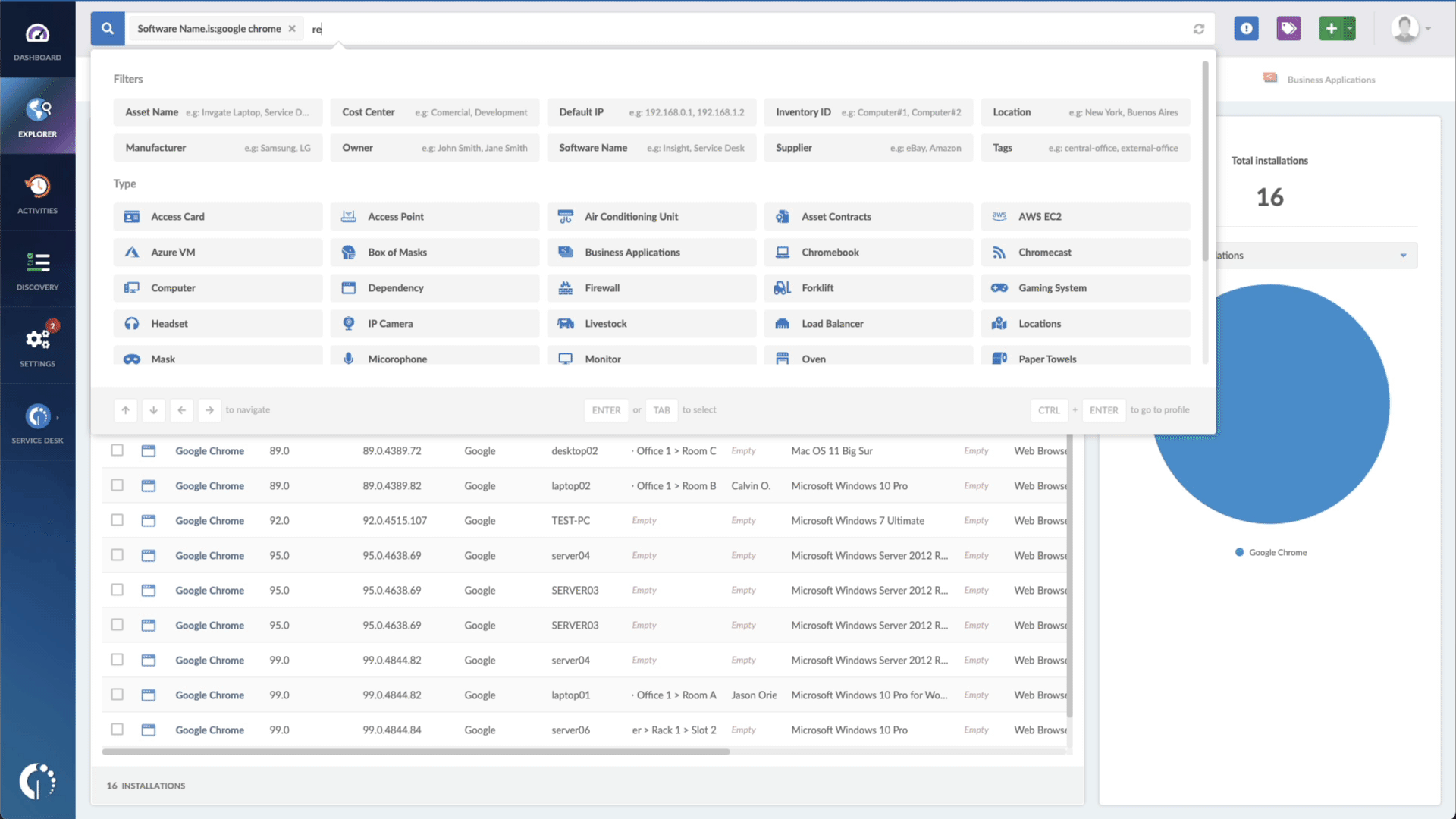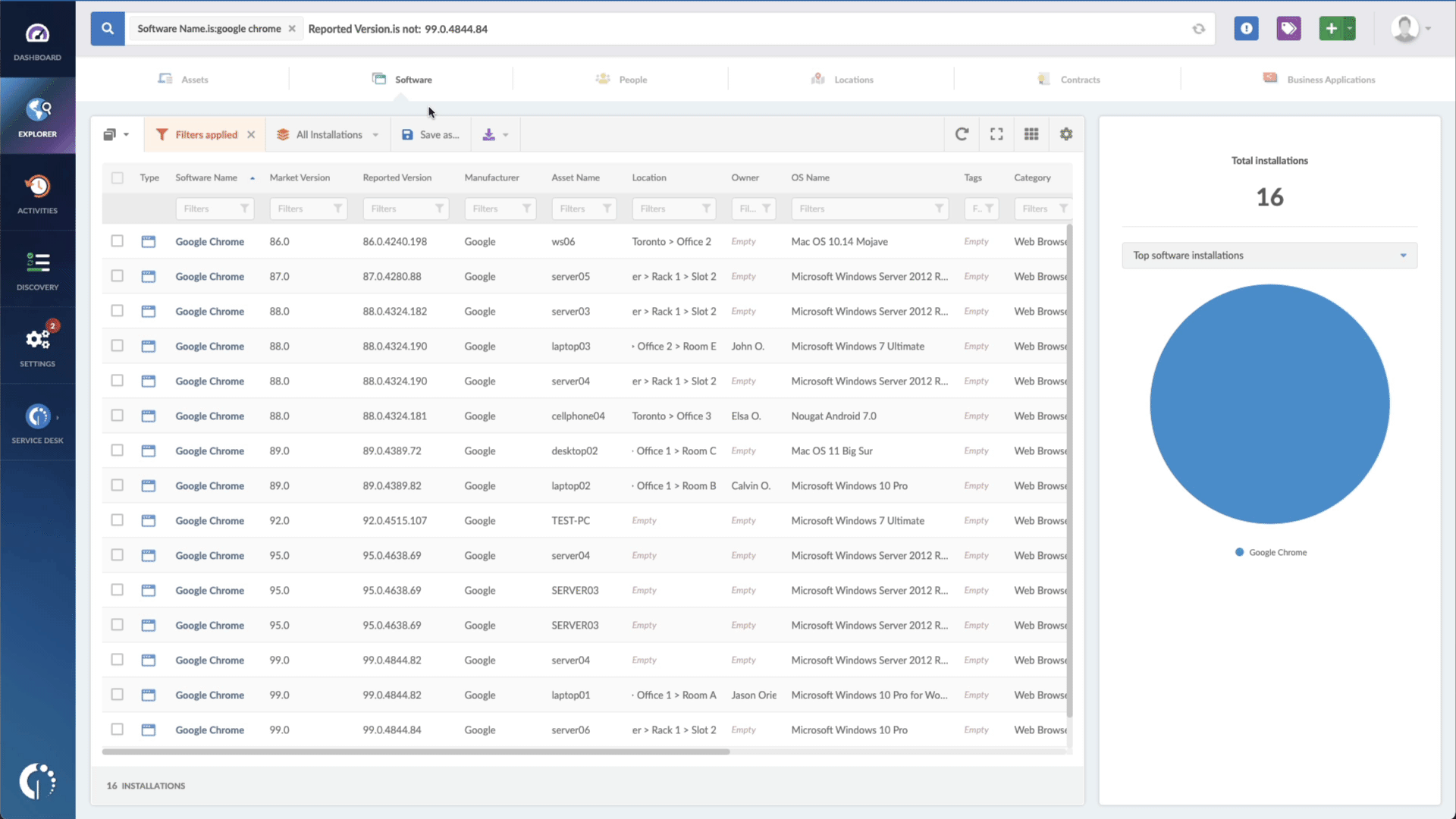
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version.
In a matter of seconds, you will receive a comprehensive list of devices that are at risk and require immediate action. This valuable information can be easily downloaded as a CSV file, allowing you to share it with your team effortlessly. By doing so, you ensure that everyone is well-informed about the critical updates that must be implemented.
For more in-depth instructions, check out our instructional video on how to identify vulnerable devices for patching.
The bottom line
CVE-2023-28206 is another addition to the list of known vulnerabilities exploited in 2023. This zero-day poses a significant threat to Apple devices, potentially enabling attackers to execute arbitrary code with kernel privileges and gain complete control over compromised systems. To mitigate this risk, it is crucial for users of macOS, iOS, and iPadOS to update their operating systems to the latest versions promptly.
For organizations seeking to optimize their Vulnerability Management strategy, InvGate Asset Management offers an efficient solution. With its comprehensive scanning capabilities, you can effortlessly generate a detailed inventory of at-risk devices within seconds.
To experience the benefits of InvGate Asset Management, request our 30-day free trial and leverage its advanced features to search for vulnerable devices in your network.















