In today's interconnected world, where cyber attacks continue to evolve, it is crucial to stay vigilant and proactive in protecting our systems and data. One such vulnerability that has recently come to light is CVE-2023-24880, which targets the Windows SmartScreen feature.
Implemented by Microsoft, SmartScreen acts as a safeguard, preventing users from downloading and executing potentially malicious files from the internet. However, this critical zero-day vulnerability allows threat actors to bypass SmartScreen's defenses, posing a significant risk to users and organizations.
With CVE-2023-24880, Microsoft has added another flaw to the list of known vulnerabilities exploited in 2023. Let's dive into its details and discover how InvGate Asset Management can help you detect exposed devices on your network.
About CVE-2023-24880
CVE-2023-24880 is a critical vulnerability that targets the Windows SmartScreen feature. SmartScreen is a security measure implemented by Microsoft to protect users from downloading and running potentially malicious files from the internet.
When a file is downloaded, Windows adds a zone identifier or Mark of the Web (MOTW) as an NTFS stream to the file. SmartScreen then checks for the presence of the zone identifier Alternate Data Stream (ADS) to determine if the file was downloaded from the internet. If the ADS indicates ZoneId=3, which signifies that the file was downloaded from the internet, SmartScreen performs a reputation check before allowing the file to run.
However, CVE-2023-24880 allows attackers to craft malicious files that evade the MOTW defenses. This means that protective measures like Windows SmartScreen and Microsoft Office Protected View won't be triggered, enabling attackers to execute potentially malicious code on the victim's system.
Exploitation and discovery
The exploitation of CVE-2023-24880 was initially reported to Microsoft by researchers Benoît Sevens and Vlad Stolyarov of Google's Threat Analysis Group (TAG). They discovered that threat actors were using the vulnerability to deliver the Magniber ransomware.
The TAG team observed over 100,000 downloads of these malicious MSI files since January 2023, with a significant concentration in Europe. This targeting strategy represents a notable deviation from Magniber's typical focus on South Korea and Taiwan. The attackers' ability to exploit this vulnerability successfully highlights the significance of the flaw and the need for immediate remediation.
This is not the first time SmartScreen bypass vulnerabilities have been observed. In September and November 2022, similar vulnerabilities (e.g., CVE-2022-44698) were exploited to deliver the Magniber ransomware and the Qakbot info stealer. However, the patches provided at that time were limited in scope and did not address the underlying root cause. As a result, attackers were able to iterate and discover new variants of the original bug.
How to find devices exposed to CVE-2023-24880 with InvGate Asset Management
To mitigate the risks associated with CVE-2023-24880, organizations and users must apply the latest security patches released by Microsoft. InvGate Asset Management provides a set of powerful features designed to assist you in effortlessly identifying the devices in your organization that demand immediate attention. To leverage these capabilities, follow the steps outlined below:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows”.
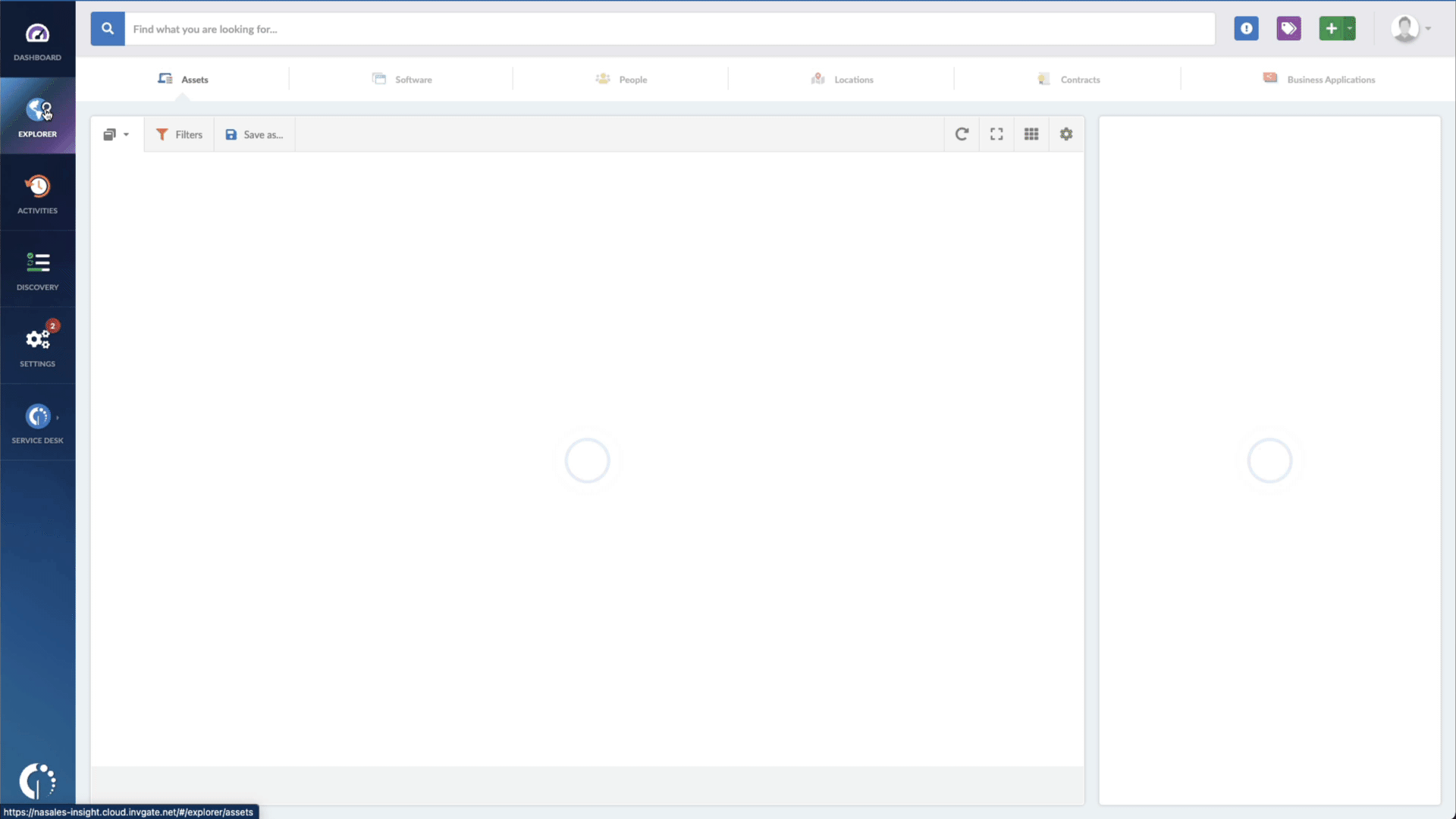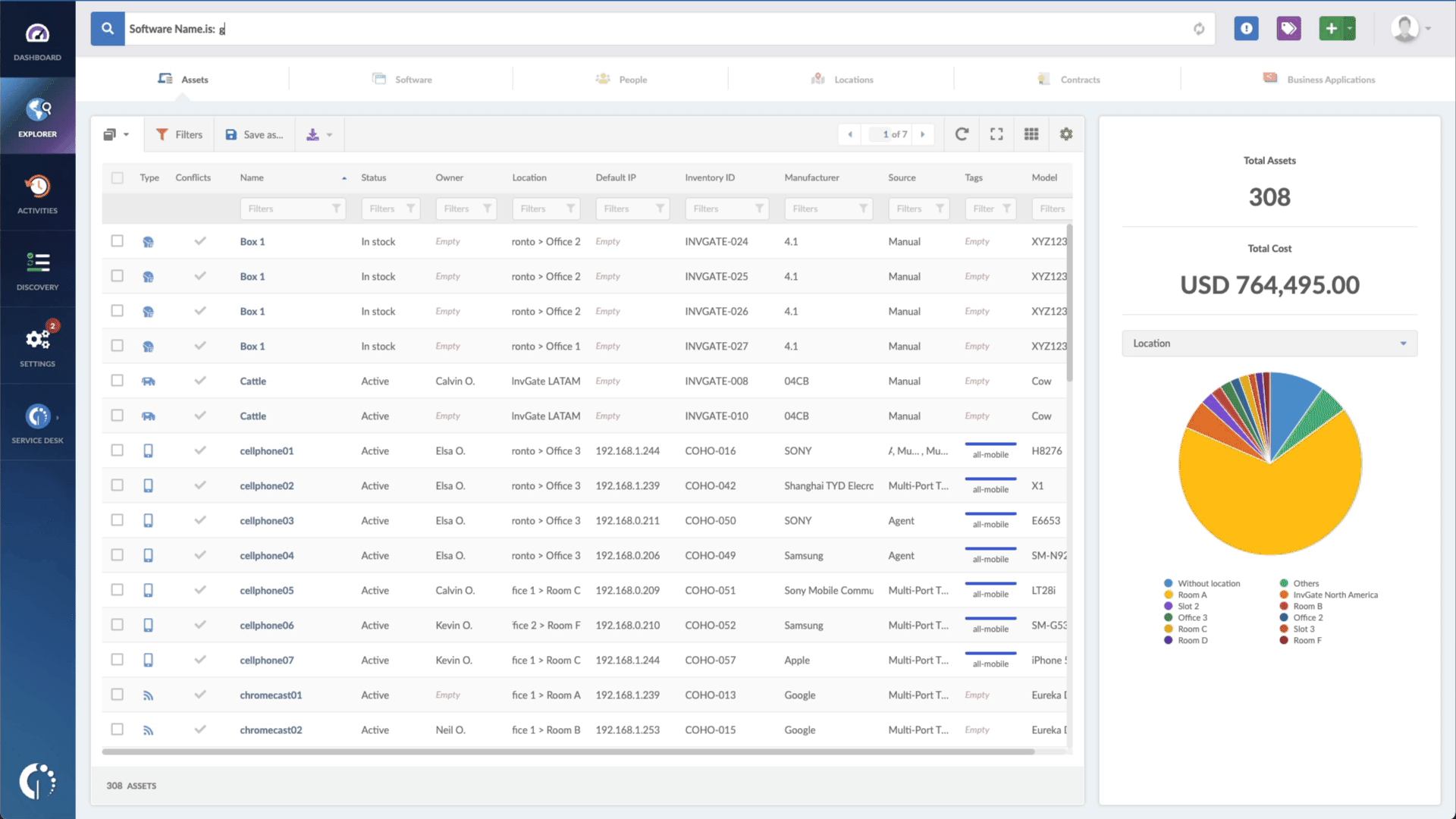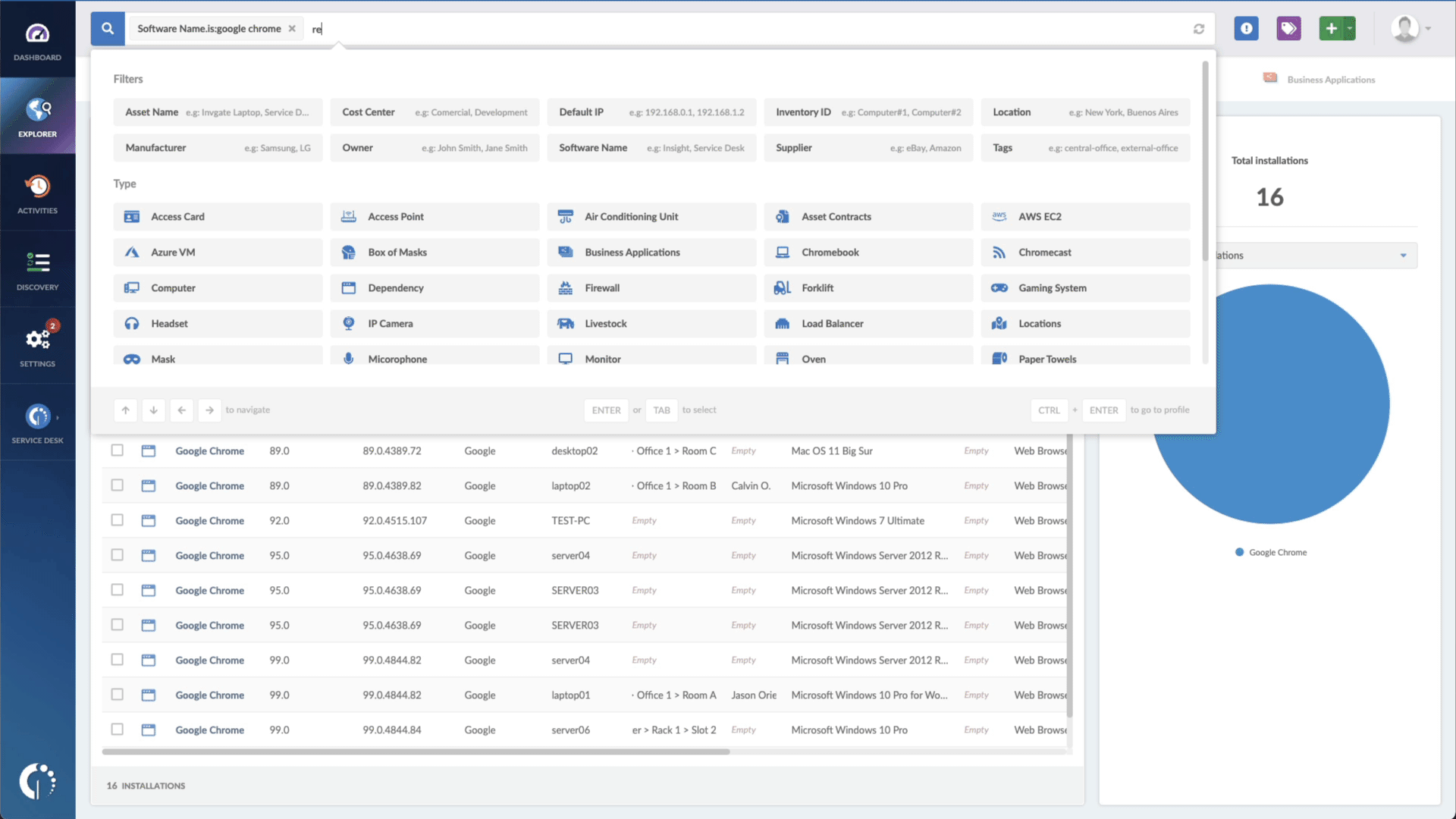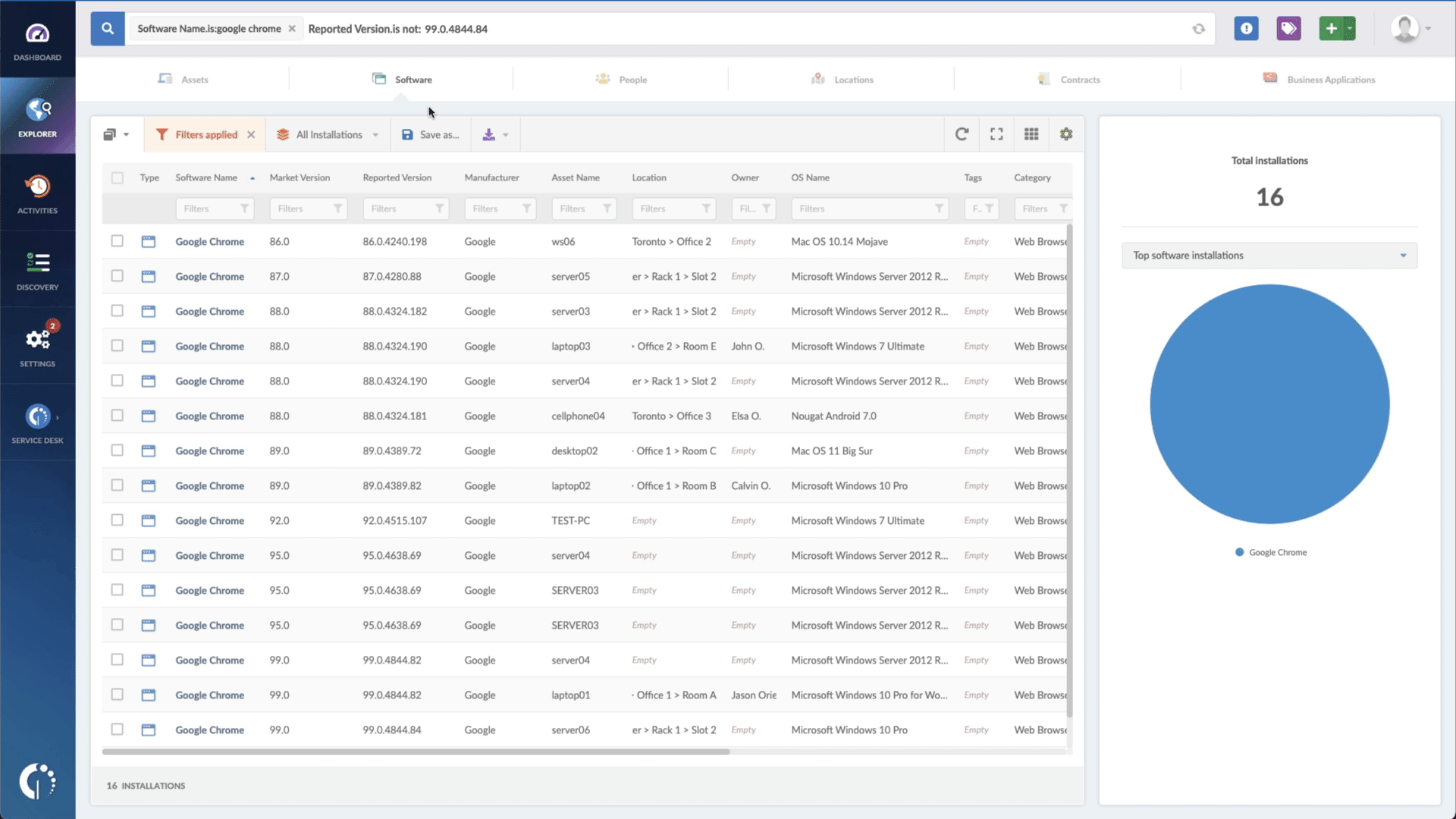
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version.
And there you have it! Within a matter of seconds, you will receive a comprehensive list of devices that are vulnerable and require immediate action. It's important to note that you can easily download this information in CSV format and share it with your agents, enabling them to stay informed about the updates that need to be implemented.
If you need more information, check out our video on how to find vulnerable devices for patching.
The bottom line
CVE-2023-24880 poses a significant risk to Windows users, as it allows threat actors to bypass the protective measures of the Windows SmartScreen feature. By updating to the patched version, users can effectively mitigate the risks associated with CVE-2023-24880 and prevent potential exploitation.
To simplify the crucial task of Patch Management and identify devices exposed to this vulnerability, InvGate Asset Management offers powerful capabilities. With just a few simple steps, users can take immediate action to secure their systems.
Request our 30-day free trial today and safeguard your network from potential exploits.















