Two new zero-day exploits that affect the Chromium browser core were reported on April 14th. And since both Chrome and Microsoft Edge are based on it, Google advised to update the browsers. The vulnerabilities CVE-2023-2033 and CVE-2023-2136 can lead to remote code execution and have already been fixed.
But that doesn't mean that's the end of the problem. If the automatic updates on your organization's browsers aren't enabled, you need to find outdated versions and patch them as soon as possible to avoid potential threats.
Keep reading to learn more about the exploits and how to spot software that needs updates on your company network with InvGate Asset Management!
About CVE-2023-2033
CVE-2023-2033 corresponds to a type confusion in Chromium's open-source JavaScript engine V8 in Google Chrome browsers that haven't been updated to versions 112.0.5615.121 or later. If exploited, an attacker could "potentially exploit heap corruption via a crafted HTML page."
According to the NIST's National Vulnerability Database (NVD), the Chromium security severity is high.
Since this is a remote code execution, the vulnerability can be exploited from outside your company network. If we take into account that Google confirmed this exploit has been actively exploited in the wild, patching outdated Chrome browsers is urgent.
About CVE-2023-2136
On the other hand, CVE-2023-2136 corresponds to an integer overflow in Skia in Google Chrome browsers that haven't been updated to versions 112.0.5615.137 or higher. According to the official statement, it allows a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page.
As with the other vulnerability, this one has been labeled as high severity and exploited in the wild.
And since Microsoft Edge browsers are also Chromium-based, you should see that they are updated to versions 112.0.1722.58 or later.
How to find devices exposed to CVE-2023-2033 and CVE-2023-2136 with InvGate Asset Management
InvGate Asset Management has a quick and efficient way to detect devices that the CVE-2023-2033 and CVE-2023-2136 vulnerability may impact. You can follow these steps to identify potentially vulnerable devices:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar "Software name, is:Google Chrome" or "Software name, is:Microsoft Edge" to filter all Chrome or Edge browsers.
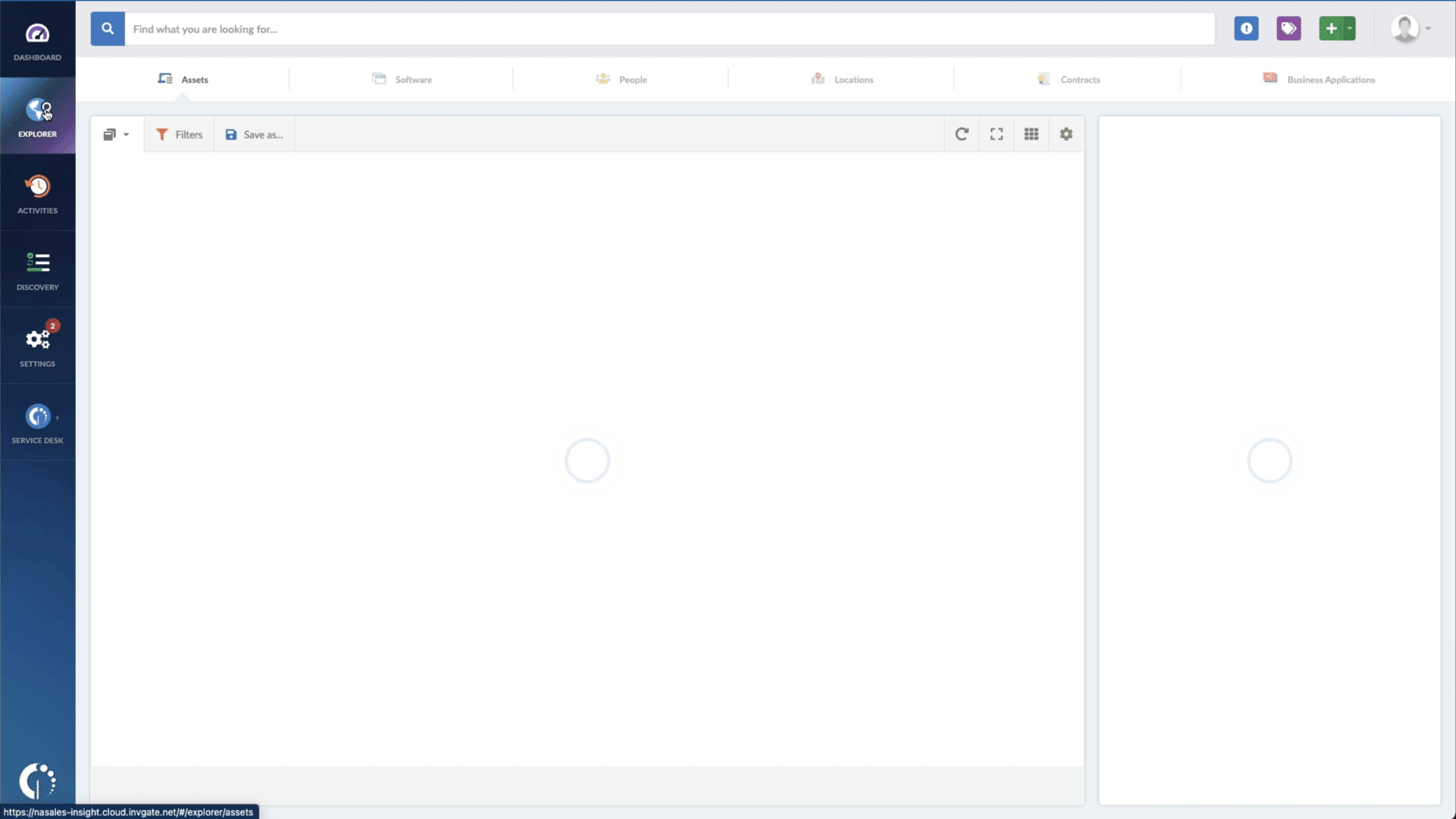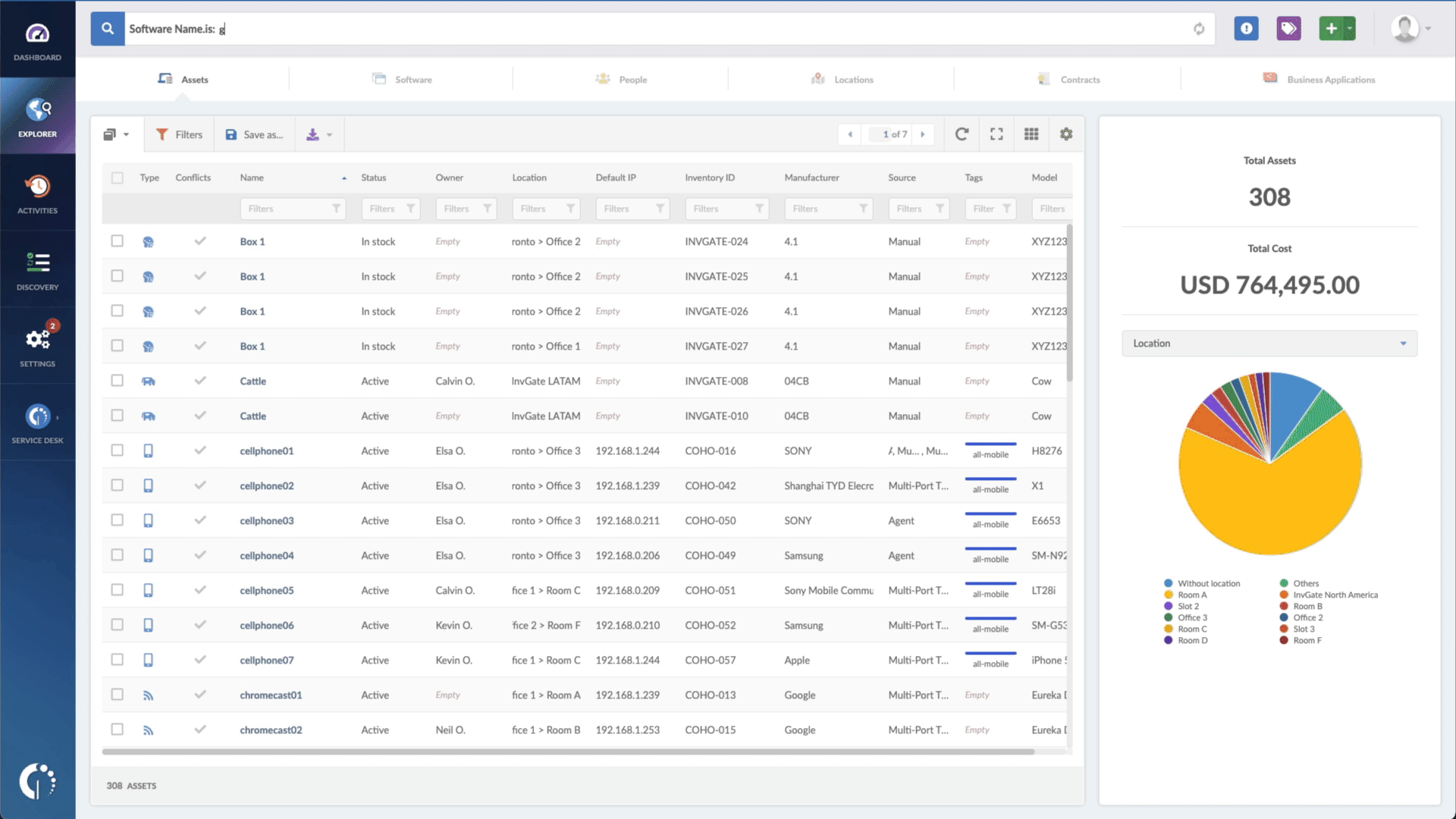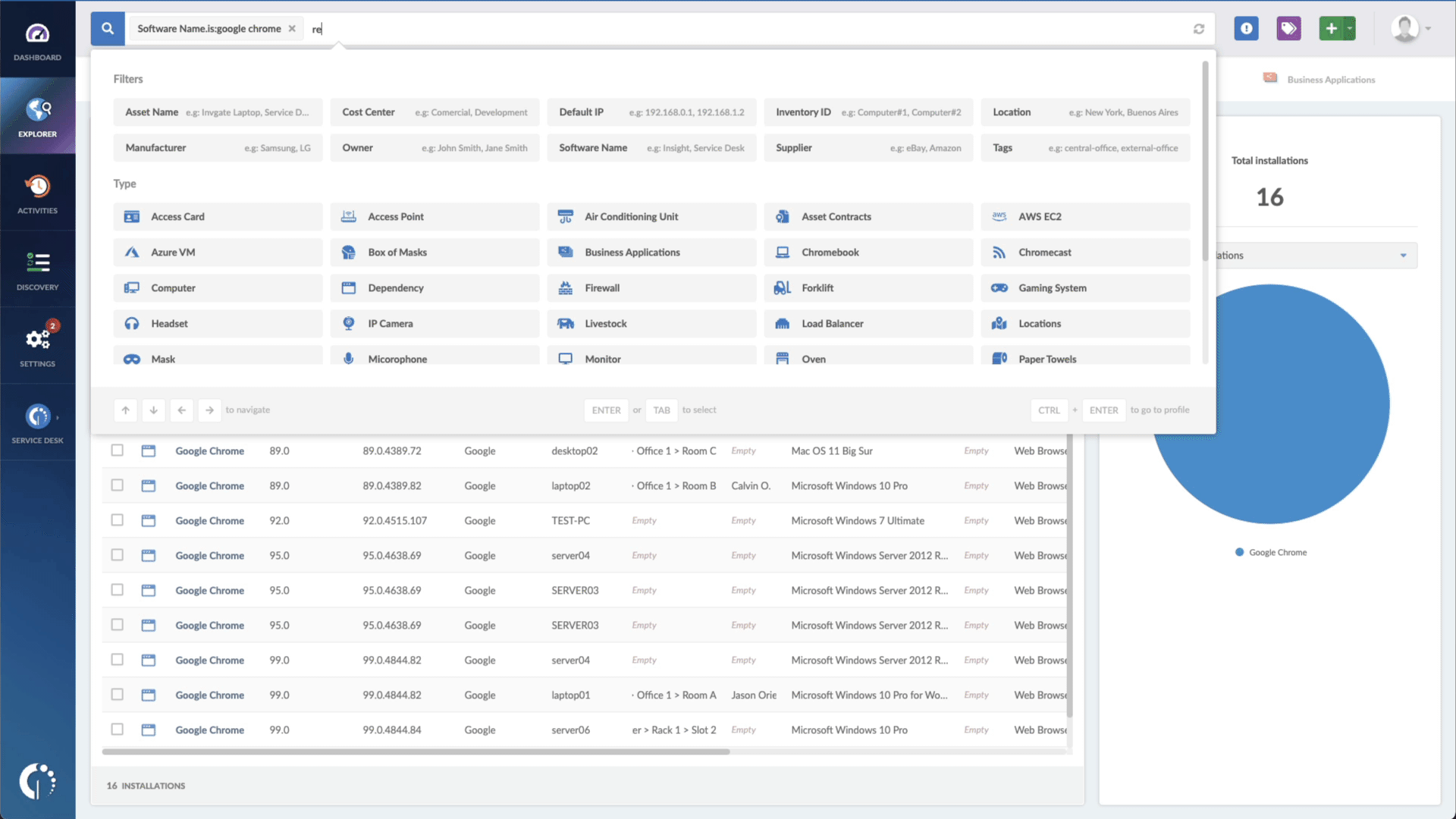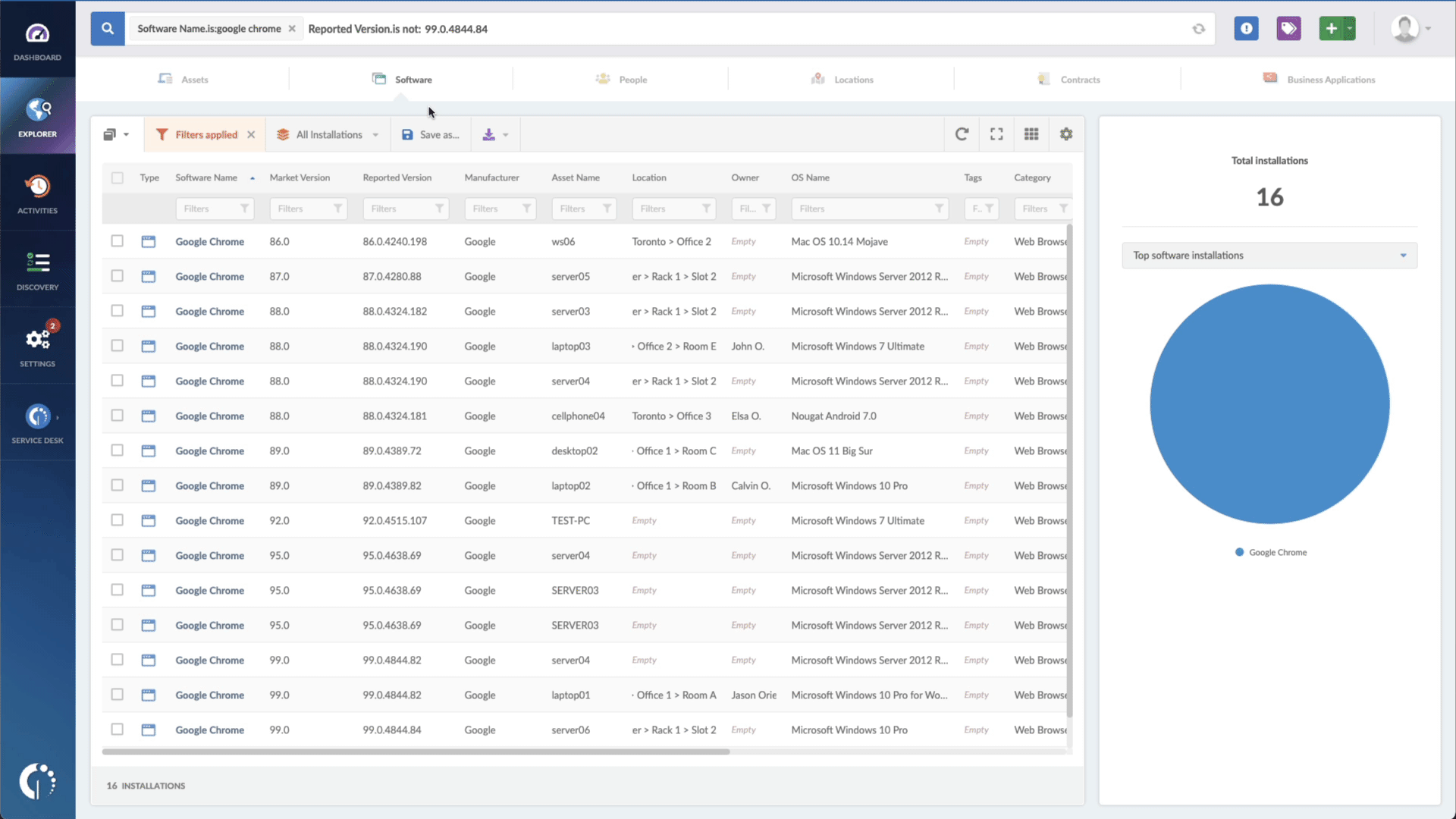
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: "Reported version, is not:" and paste Chrome or Edge's patched version.
That's it! You'll have a list of devices to patch with just a few clicks. You can export it in CSV and give it to one of your agents to fix or create a ticket so they can be manually updated.
Also, check our video on how to find vulnerable devices for patching.
The bottom line
CVE-2023-2033 and CVE-2023-2136 vulnerabilities affect both Google Chrome and Microsoft Edge browsers. And since they are being exploited in the wild, you must update your devices as soon as possible. Otherwise, they can be subjected to a remote code execution.
Having a Vulnerability Management strategy in place can help you avoid these and future exploits and keep your company devices as safe as possible. And InvGate Asset Management can be of great help in developing it.
If you want to search for vulnerable devices on your network, you can do it right now with our 30-day free trial! Just make sure that, after that, you explore all the other capabilities it has – we promise you won't regret it!