As cybersecurity threats continue to evolve, keeping your systems secure and up-to-date is essential. On September 30, 2022, Microsoft released a statement regarding a critical vulnerability in Microsoft Exchange Server, known as CVE-2022-41040.
This vulnerability can allow attackers to perform an elevation of privilege attack, potentially compromising the entire network. In this article, we’ll explore the CVE-2022-41040 vulnerability in detail, including its risks, how InvGate Asset Management can help you identify devices that may be affected, and how to patch your systems.
Don't miss out on this crucial information. Keep reading to protect your organization from the CVE-2022-41040 vulnerability!
About CVE-2022-41040
CVE-2022-41040 is a Server-Side Request Forgery (SSRF) vulnerability that allows attackers to make server-side application requests from an unintended location – for example, allowing them to access internal services without being within the perimeter of the network.
This vulnerability affects Microsoft Exchange Server 2013, 2016, and 2019. Microsoft released patches for these issues on November 8, 2022, and users are advised to apply the latest updates as soon as possible. The latest versions that include the patch are:
- Exchange Server 2013 CU23
- Exchange Server 2016 CU22 and CU23
- Exchange Server 2019 CU11 and CU12
How to find devices exposed to CVE-2022-41040
The use of InvGate Asset Management enables you to pinpoint the devices that the CVE-2022-41040 vulnerability has impacted quickly. The following instructions outline the steps to be taken:
- Open InvGate Asset Management and go to the Explorer tab.
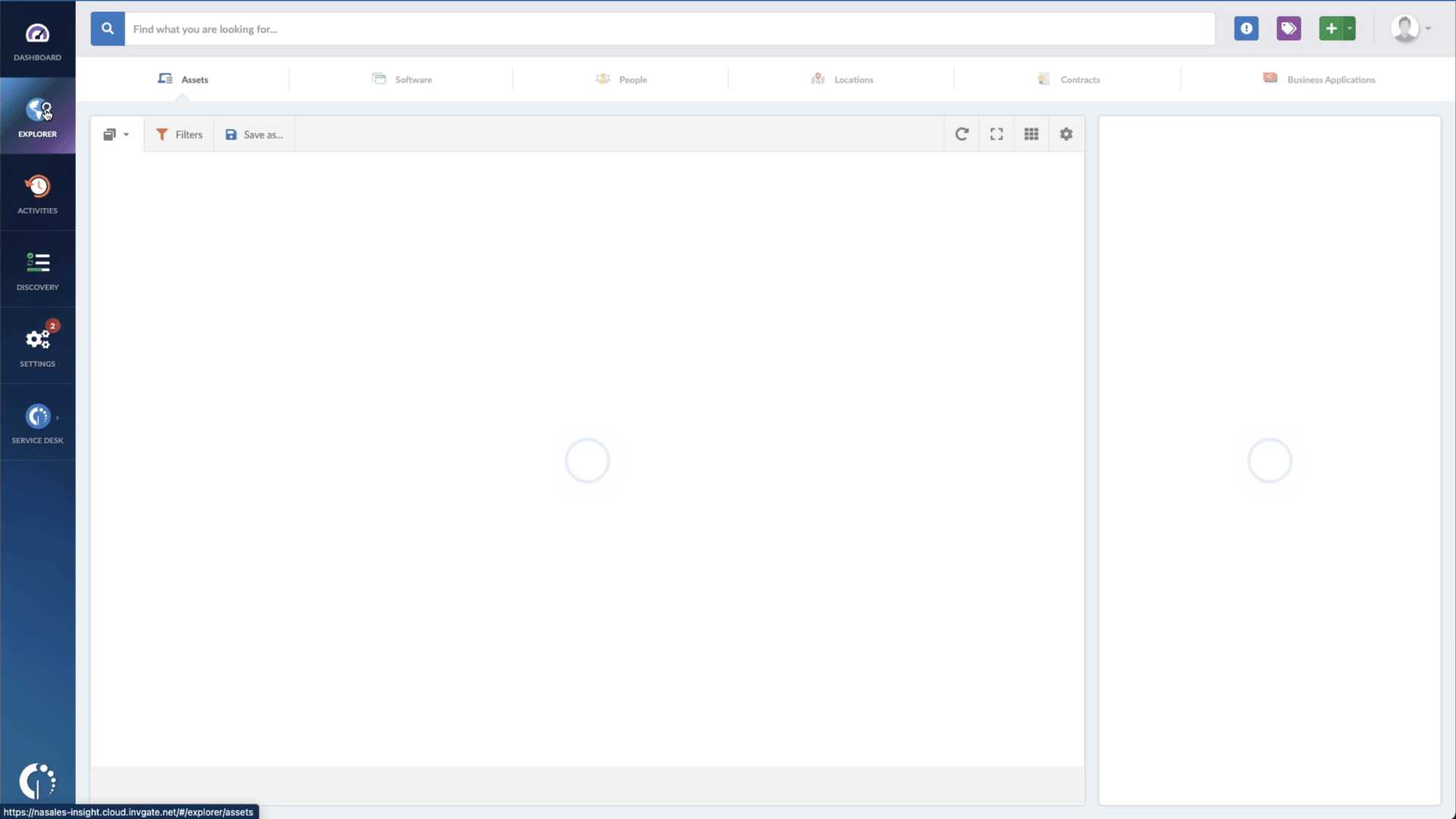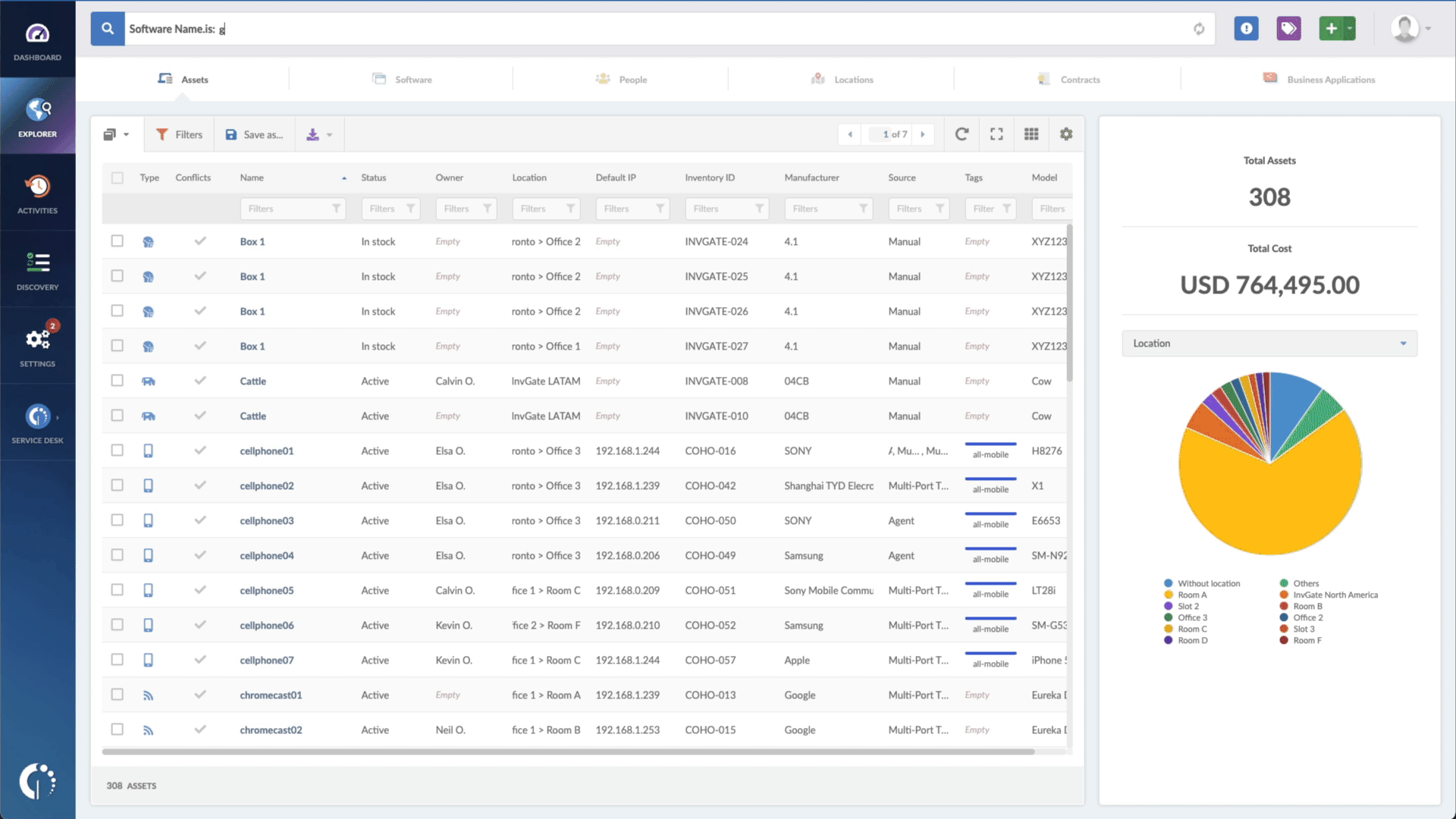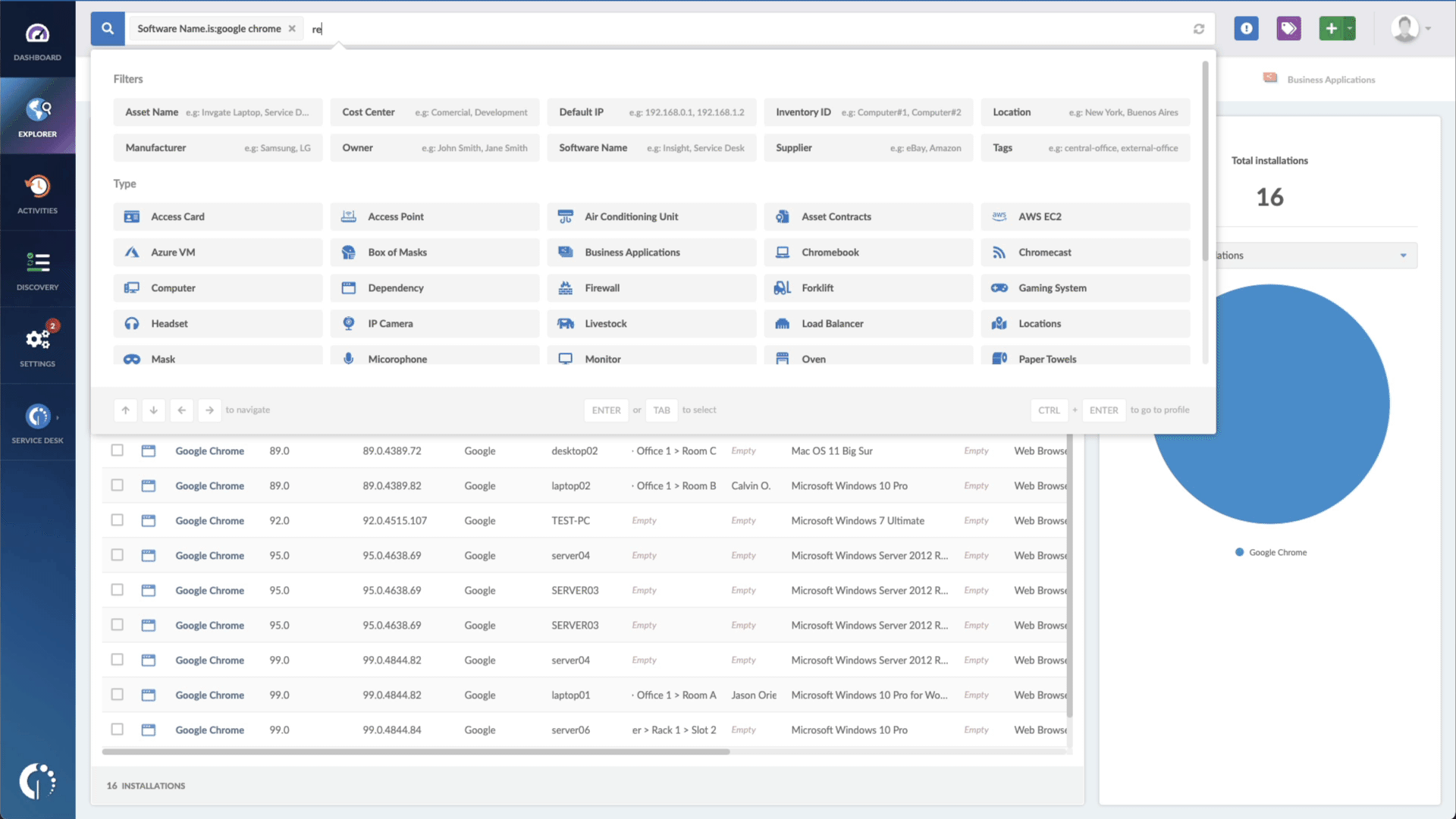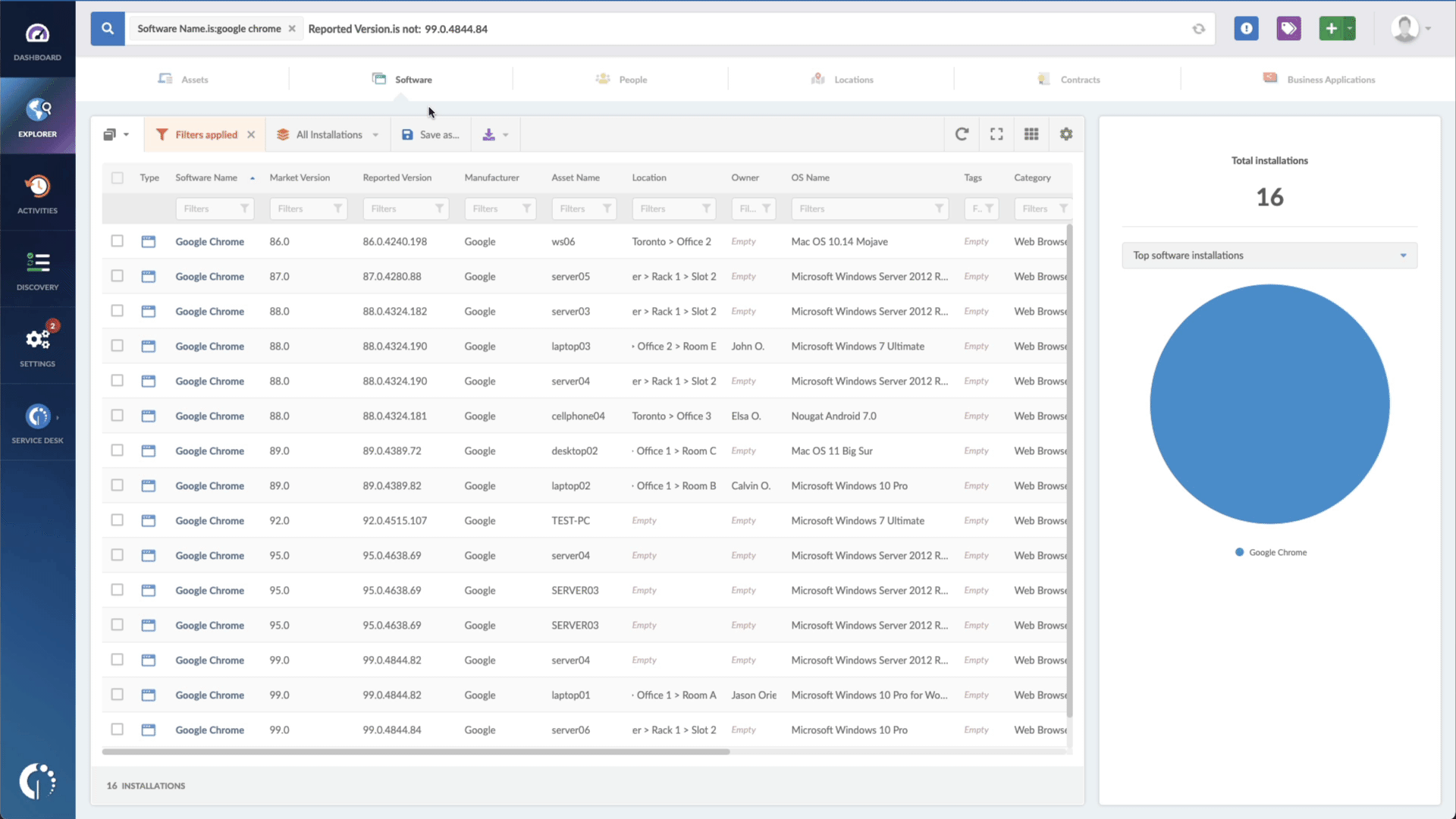
- Type in the Search bar “Software name, is:Microsoft Exchange Server” to filter all Windows devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (KB5019758).
Another related vulnerability
Another vulnerability that requires urgent attention is CVE-2022-41082. It is a remote code execution vulnerability found in the Exchange PowerShell backend, which has a CVSS score of 8.8 (High).
To exploit this vulnerability, attackers must first bypass authentication by abusing CVE-2022-41040. This means that if CVE-2022-41040 has not been patched, then attackers can gain complete control of the vulnerable Exchange Server by exploiting CVE-2022-41082.
CVE-2022-41040 can enable an authenticated attacker to trigger CVE-2022-410822 remotely. However, authenticated access to the vulnerable Exchange Server is necessary to exploit either vulnerability successfully, and they can be used separately.
The bottom line
CVE-2022-41040 is a SSRF vulnerability found in Microsoft Exchange Server 2013, 2016, and 2019. Exploiting this vulnerability can lead attackers to make server-side application requests from an unintended location. However, this vulnerability can be mitigated by applying the latest updates from Microsoft, which include the necessary patch.
With InvGate Asset Management, IT teams can quickly and easily identify the devices in their network that are affected by the CVE-2022-41040 vulnerability.
Try a 30-day free trial to experience the benefits of InvGate Asset Management for yourself. Don't hesitate to take the necessary steps to secure your organization's IT infrastructure.