It wasn’t too long ago that a security system would be nothing more than a few walls, some cameras, and an inattentive security guard.
That’s no longer the case In today’s digital landscape.
Now organizations must invest in securing their assets from a growing number of cyberthreats. To start, they must first draw up the boundaries of their IT security perimeter.
What is an IT/network perimeter?
Acting as one of the most important branches of cybersecurity today, it is often the IT team of an organization that helps carve out the digital territory of a business by establishing a network perimeter. And while IT perimeter security (we’ll get to this below) has had to evolve with the development of cloud computing and software as a service, the idea of a electronic security perimeter is not too dissimilar than that of the more easily defined physical security perimeter.
In short, a network perimeter (or IT perimeter) defines the line between a company’s local and private intranet from that of the public and outside world more commonly known as "the internet." This boundary is important if you want to keep the most private information and resources out of the hands of malicious actors, or out of any hands at all.
On its face, it’s not too difficult to understand. However, actually protecting what used to be a closed-off space physically connected to servers, computers, and printers becomes tricky when the very concept of a perimeter evolves with the advent of new technology around it.
What is IT perimeter security?
Simply put, IT perimeter security is the process of securing a network perimeter by implementing a combination of software, devices, and techniques. Some strategies or guidelines used within IT perimeter security may include passive or active surveillance, threat detection, and pattern analysis. Of course, there are a number of tools used to enforce network security which we’ll elaborate on later.
For now, it’s important to understand that IT perimeter security is a constantly evolving process. The development of new, user-defined technology is in perpetual conflict with timeworn cybersecurity strategies. With everybody and their grandparents in possession of a phone (i.e. a mobile device that connects to various networks), you can begin to see the difficulty in pinpointing where a network perimeter is, much less in how to secure it.
The modern network perimeter is literally expanding. It is dynamic, but not necessarily due to the physical growth of an organization. As such, IT managers and specialists are required to be vigilant in their exploration and assessment of the perimeter.
Why is IT perimeter security important?
The obvious answer is: you don’t want other people stealing your stuff. In this case browsing (or more seriously, investigating) without your consent would be a form of theft as it’s stealing a look, so to speak, at your private information without permission.
However, since we know any electronic security perimeter is vulnerable to and defined by the onslaught of new technology, we know in order to protect an organization’s data the IT perimeter security must adopt the latest practices and tools to keep pace. Hackers, malware, and data breaches are just a few of the more common threats that have been around for decades, and alone justify the need for thorough perimeter defense. But the onset of new applications and modes of working further necessitate up-to-date and flexible security measures.
Consider the remote workforce, for example. The transition from a more traditional office and the ability for employees to work from their own devices presents a new set of challenges for IT departments trying to keep the peace throughout a corporate network. No longer defined by physical limits, the modern organization needs perimeter security dedicated to protecting the constantly shifting entry and exit points of its private network.
Network perimeter guidelines & best practices
Given the relatively indistinct nature of a network perimeter in today’s digital environment, it helps to remind ourselves of its abstract nature and how no one-size-fits-all security solution exists. Instead, your IT team should use a varied application of hardware and best practices to enforce network security around a data center.
Network Design
The first step in perimeter protection is configuring a secure network design which incorporates all the systems, software, and hardware that’ll be used to protect all your valuable data. Mapping out external connectivity points, adjusting firewall settings, and setting up authentication user access control are several ways to get started. At this stage it’s auditing your current set up to find weak points and define, to the best of your ability, the boundaries of your perimeter.
Passive Monitoring
To find the chinks in your armor, you’ll need to keep a close eye on it with a collection of monitoring tools. With the help of security devices, routers, desktops, remote servers, and firewalls, you can scan for vulnerabilities and identify devices connected to your network which essentially act as the nodes and limits of your perimeter. Passive monitoring tools are passive because they need to be activated or scheduled at set times to look for suspicious network activity.
Active Monitoring
More aggressive monitoring is also recommended when sniffing out weaknesses in your network security. With alerts to notify your team in real time of irregular network traffic patterns, failed log in attempts, or any other red flags, active monitoring tools ensure more thorough surveillance of your network with 24/7 coverage. Use these tools when you need a fine-tooth comb to cover all possible breaches in your network as well as create a picture of the communication patterns between linked devices.
Network Zoning
Network zoning is when your team identifies, segments, and creates security zones within your network infrastructure. This process takes into account the different security policies of individual zones as each may require differing levels of restriction or authentication. Each is then divided into controlled, uncontrolled, restricted, or secure zones. The isolation of these particular zones helps keep a security breach in one from affecting another. In this way, it’s a bit like controlling a fire.
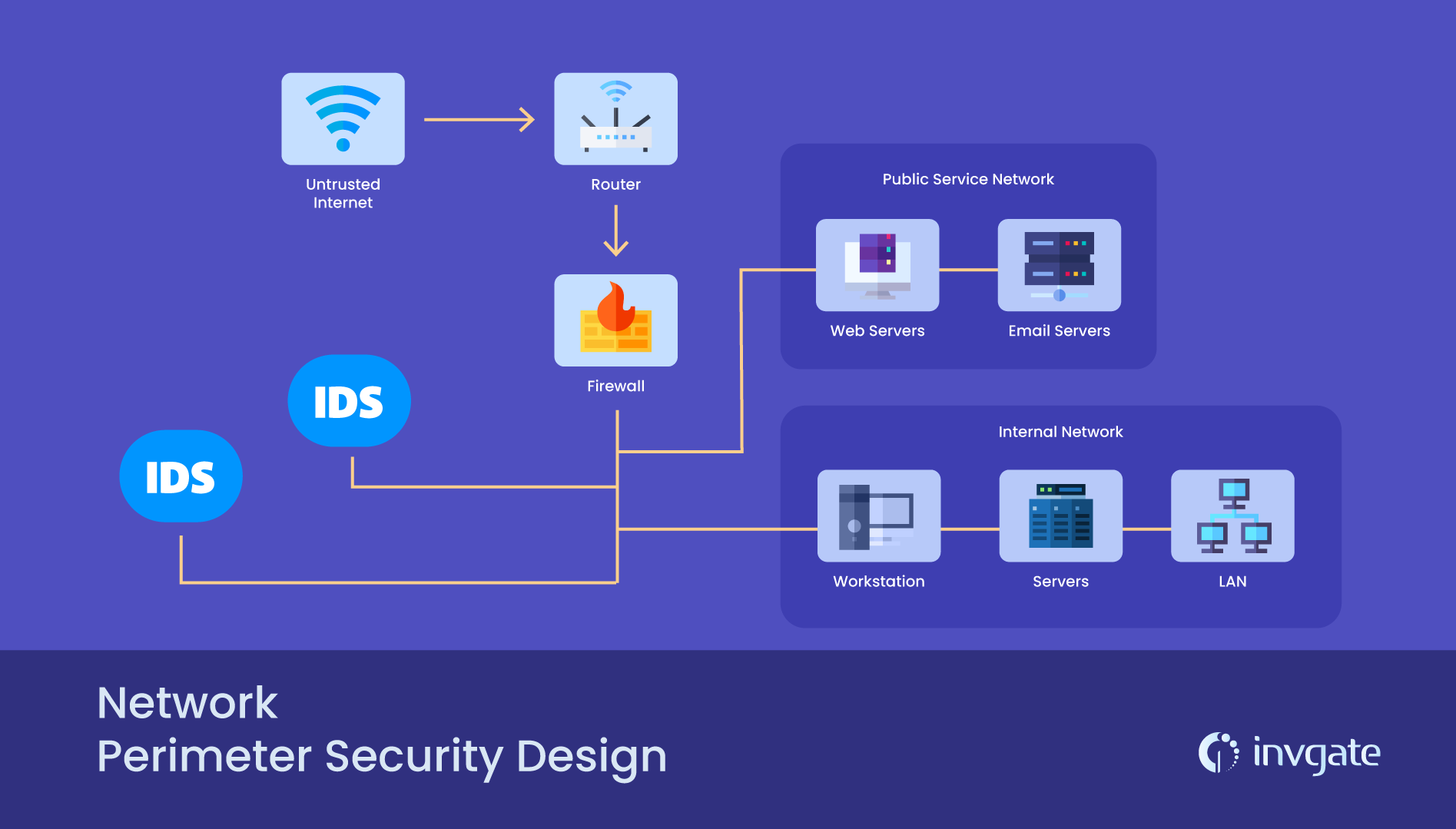
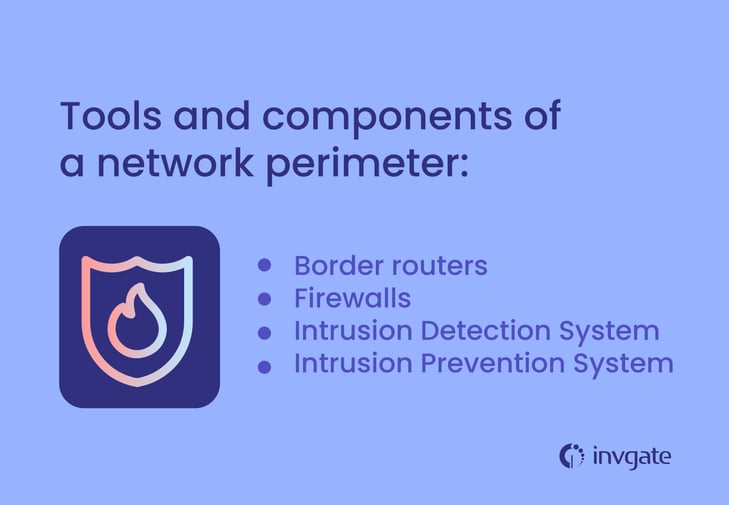
The tools and components of a network perimeter
Now that you have a general idea of what a perimeter can look like, with some basic tips on how to secure it, let’s dive into some of the specific tools used to bolster your defense.
Border Routers
Like the gates on the furthest limits of a castle’s walls, border routers dot the limits of your network perimeter and serve as a guide for incoming or outgoing traffic. They establish the border, as much as it can be established, sharing parts with both your private network and the wilds of the internet beyond.
Firewalls
To keep the metaphor going, firewalls are the inner series of walls which act as a additional filter for oncoming traffic. They decide who (or what) shall and or shall not pass based on a set of predefined rules. Similar to the other tools listed here, they aren’t meant to be an organization’s only line of defense, rather should be used in conjuction with other software and devices.
Intrusion Detection System (IDS)
The intrusion detection system is your alarm system. It can either be a single device or series of them that monitors your network for malicious activity or policy violations. An IDS differs from a firewall as it watches for intrustions within an internal network (within the keep, we’ll say) and notifies you of an attack from within a network.
Intrusion Prevention System (IPS)
Where an IDS sounds the alarm on potential threats, an intrusion prevention system stops them automatically from a preset list of rules. An IPS is the night guard who steps in to intercept oncoming traffic, block it, drop malicious packets of data, or reset the connection altogether. It provides that extra bit of examination and internal security, but without the direct intervention of an administrator. An IPS is also considered a next generation firewall, which is basically an advanced version of a more traditional firewall but with the added ability to block malware and use in-line deep packet inspection (DPI).
Frequently asked questions
What is security architecture?
Security architecture is the guiding framework of principles used to protect an organization from cybersecurity threats. It’s an encapsulating or overarching term that includes some of the same methods, models, and tools of an network security perimeter without necessarily being limited to certain components, devices, or a software defined perimeter. It is a unified, replicable design of your security system.
What are some threats to perimeter security?
Some threats to your team’s perimeter security may include (but are not limited to) the following:
- Malware - viruses, spyware, ransomware, worms, etc.
- Phishing
- Mobile applications and devices
- Password attacks
- Outdated security software
- Employees - can be either malicious actors who attempt to steal or sabotage company data, or those who simply don’t follow IT security compliance
How can IT security be measured?
Measuring the effectiveness of something as intangible as IT security or the perimeter (as we’ve seen) is no easy task. Reports and logs of past cyberthreats can be benchmarked against industry standards. Carry out frequent evaluations and analysis of measurable occurances like attempted log ins from unidentified networks, a spike in unrecognized devices, or an unusual amount of security alerts. Collected data from old records should be compared with any changes in the components of your network security to determine where any vulnerabilities or gaps in the system lie.
To tighten up your team’s IT security and asset monitoring, try InvGate Asset Management. With it you can bolster your organization’s security and identify vulnerablities by detecting devices running outdated or otherwise unauthorized software.
















