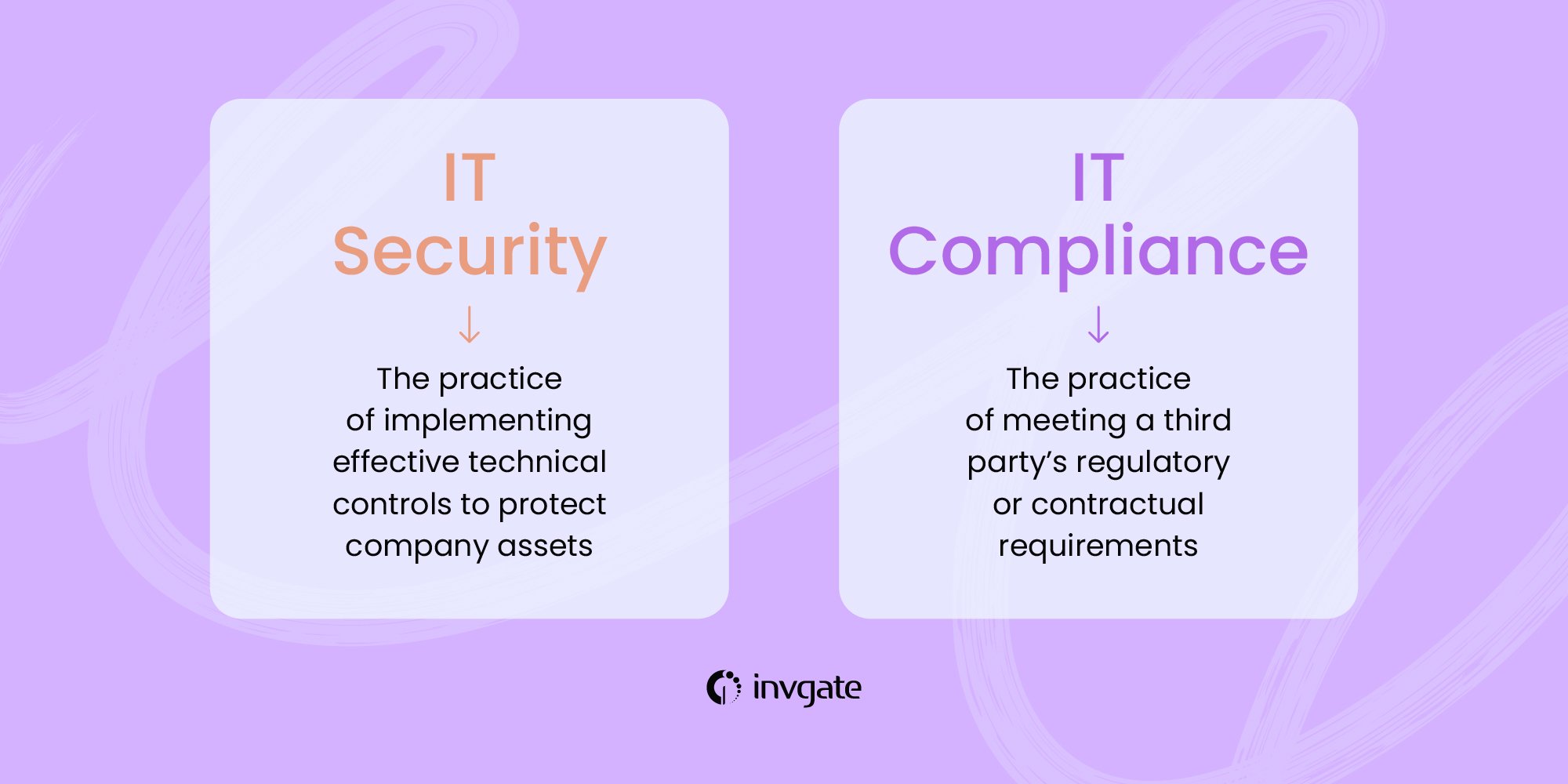
What’s the real difference between IT security and compliance? Can you just focus on one and call it a day? The fact is that IT security and compliance are both critical, yet they play different roles in keeping your organization safe from cyber threats.
The fact is, everyone needs to understand basic cybersecurity concepts. Cyberattacks have been on the rise, especially with recent changes like the shift to remote work. In 2025, the global average cost of cybercrimes will hit 10.5 trillion USD, making it clear that these threats come with serious consequences.
At the same time, governments and regulatory bodies are stepping in with stricter rules to protect data and hold organizations accountable. That’s why IT security and compliance are now top priorities for businesses worldwide.
In this article, we’ll break down what IT security and compliance mean, how they differ, and why they’re both important for protecting organizations and their customers.
What is IT security?
IT security is a set of measures and practices implemented within the organization to protect its assets, its employees, and customers safe from cyber threats. The IT department is responsible for protecting the organization’s network and assets, as well the data stored by the organization.
As you can imagine, there are different aspects to IT security and is as complicated as the variety of threats the organization may face. IT security has to defend the organization from malicious software, attacks that interrupt the company’s services, malicious actors that may damage or destroy the company’s and its clients’ assets, social engineering attacks targeting the employees or the customers, and attackers trying to steal data from the company servers, to name a few.
And just like the evolving nature of cyber threats, IT security is also a constantly changing field.
The security of the data that may concern the organization, its employees, and its customers is considered to be a subset of IT security referred to as information security. With the rise in the internet of things, artificial intelligence, and advanced analytics solution which all store and use large amounts of data, information security has become a key part of IT security.
Among other things, this is why it's important to build a culture of cybersecurity. IT security strategy of an organization is essentially a risk mitigation strategy; minimize the possibility of a successful attack and also the consequence of an attack.
For example, an organization may implement two-factor authentication throughout its digital workplace, biometric access to the company premises, and ask its employees to use the best password managers. And at the same time, the company may isolate its core systems, add multiple redundancies to its servers, and device and practice a disaster recovery and business continuity plan.
It’s important to understand that IT security is not just about the technical aspects; it’s not just implementing the latest security updates and patches or constantly monitoring the network for suspicious activity. It's also about building a robust cybersecurity culture within the organization; it’s about educating and informing the employees to identify and mitigate cybersecurity threats and encouraging them to follow strong security practices.
Key components of IT security
IT security includes various domains, each focusing on specific aspects of protection:
- Network security: Safeguards the infrastructure by monitoring and managing access to networks, ensuring threats are identified and mitigated.
- Application security: Focuses on protecting software applications from vulnerabilities during their development and deployment phases.
- Data security: Involves methods such as encryption and access controls to keep sensitive information safe from unauthorized access.

What is IT compliance?
IT compliance is exactly as the name suggests: ensuring that your IT processes and practices comply with the standards and regulations set by your customers, the governments, and the certifying bodies.
While IT security is a set of practices the IT department defines to keep the organization secure, IT compliance is about implementing practices defined by a third party to showcase a minimum level of IT security and meet regulatory requirements.
The compliance requirements for IT vary with industries. For example, financial and healthcare organizations usually have to comply with more strict regulations compared to a chain of mattress stores or a fast-food business. Organizations that deal with the personal data of their customers are also usually tightly regulated.

IT compliance places a huge emphasis on the documentation of processes. For example, with compliance standards related to data security, organizations have to maintain clear records on who has had access to data sets. This documentation will also be subject to periodic audits by third parties to ensure compliance (which is why it's important to have a software license compliance audit checklist).
In simple terms, the goal of IT compliance is quality control and assurance; assuring a third party that your organization is following a prescribed standard.
What is the difference between IT security and IT compliance?
There may be significant overlaps between the organization’s IT security and compliance practices. But while the goal of IT security is to protect the organization and its clients and customers, the focus of IT compliance is more towards protecting the clients, their assets, and their data. And while the IT security strategy of organizations may vary even within an industry, the compliance standards remain consistent at least within an industry.
IT compliance requirements also tend to be very specific; for example, 256-bit encryption for all payment transactions or two-factor authentication for logins can be implemented. And IT security is more about the goals, and the methods and practices may vary.
Lapses in IT compliance may incur severe penalties from the respective authorities. At best the company can lose certifications and at worst you may face revenue loss, significant fines, along with other measures from regulatory authorities. Lapses in IT security can take down the business processes of the entire company, damage the assets of the company and its customers, can result in loss of company and consumer data, and on top of that, they may incur fines or other penalties from government agencies.
Why is IT compliance necessary?
In very simple terms, IT compliance is necessary for an organization to remain in business.
Here’s why.
IT compliance is necessary to work with clients and customers
Following certain standards and having certification assures potential customers that your organization is trustworthy enough to work with; that your services will have a certain level of quality and security.
For example, the ISO 20000-1 standard dictates how an organization will handle the planning, designing, and delivery of services and how the organization and clients will define the requirements. This ensures that both the client and the organization clearly understand what’s expected of each other. In the case of ISO/IEC 27001, it requires that the organization is constantly evaluating its information security risk management strategies and assures clients about how your organization will safely handle their data
Another factor is that your client may be working with multiple service providers. And if all of these providers are following different practices or standards, this will complicate things for the client. But with IT compliance, the client simply has to choose providers that follow a consistent standard which will greatly simplify processes on their end.
Lapses in IT compliance can lead you to lose your clients. It can also affect your reputation and may cause you to lose potential business and clients.

IT compliance is necessary to avoid fines and other penalties from regulatory agencies
With GDPR, the EU empowers authorities to impose fines up to $24.1 million or 4% of global annual turnover for a company, whichever is higher. For willful HIPAA violations, criminal penalties start at a minimum of $50,000 and may even include a jail term. Violations of other IT regulations can also incur similar penalties.
Even in B2C companies, IT compliance lapses can be costly. Nowadays, all companies manage lots of sensitive data, and security incidents garner a lot of media attention and can damage your reputation. Customers can easily lose their trust and may turn to other brands.
According to the Cost of a Data Breach Report 2024, the average cost of a data breach has soared by 10% in 2024, hitting a jaw-dropping $4.88 million—the steepest increase since the pandemic. Meanwhile, GDPR penalties (which enforces strict data privacy and protection laws) have exceeded a whopping €5.3 billion in cumulative fines according to CMS Law, with a significant chunk added just this year.
On top of this, these lapses can result in lengthy expensive investigations which can erode customer trust.

Understanding security standards, frameworks, and regulatory compliance
The IT compliance standards include GDPR, HIPAA, PCI DSS, ISO 27001, as well as standards that may be dictated by the clients.
There are different kinds of compliance standards depending on the goal. For example, GDPR, or General Data Protection Regulation, is concerned with keeping data secure, while HIPAA is concerned with protecting health information. ISO 20000 is related to the quality of service delivered by an IT company.
As you can see, some standards, for example, GDPR and HIPAA are defined and mandated by governmental agencies, while ISO 27001 is defined by certifying bodies. And some of these standards are legally mandated while others are implemented to assure potential clients and customers of the level of security.
Let's review this in more detail:
Regulatory compliance: legal requirements
Regulatory compliance represents mandatory requirements set by government bodies and regulatory authorities. These aren't optional - organizations must comply or face legal consequences.
Some key regulations by sector:
Financial Services:
- SOX (Sarbanes-Oxley Act) - Financial reporting and controls
- Dodd-Frank Act - Financial institution regulation
- BSA (Bank Secrecy Act) - Anti-money laundering requirements
Healthcare:
- HIPAA - Patient data privacy and security
- HITECH Act - Electronic health records requirements
- FDA regulations - Medical device security
Personal Data Protection:
- GDPR (EU) - Personal data protection and privacy
- CCPA/CPRA (California) - Consumer privacy rights
- PIPEDA (Canada) - Personal information protection
Industry standards and best practices
These represent agreed-upon practices within specific industries. While not legally mandated, they often become de facto requirements for business operations:
- PCI DSS - Payment card industry security standard
- SWIFT security controls - Financial messaging security
- NERC CIP - Electric utility cybersecurity
Security frameworks
Security compliance frameworks provide structured approaches to security implementation. Organizations can choose which frameworks to follow based on their needs:
NIST Frameworks:
- NIST Cybersecurity Framework (CSF)
- NIST SP 800-Series (Federal systems and information protection)
International standards:
- ISO/IEC 27000 - Information security management
- ISO 27701 - Privacy information management
- ISO 31000 - Risk management
Other notable frameworks:
- COBIT - IT governance and management
- CIS Controls - Prioritized security actions
- MITRE ATT&CK - Threat modeling and defense
The key distinction lies in enforceability and choice. Regulatory compliance requirements must be met - organizations face fines, penalties, or operating restrictions for non-compliance. Standards and frameworks, while valuable, remain voluntary tools for building security programs.

IT security and compliance: Where do they align?
The overlap between IT security and compliance roles creates both opportunities and challenges. While security teams focus on implementing technical controls and managing day-to-day security operations, compliance teams interpret regulatory requirements and prepare for audits. Yet, these roles frequently intersect. During a data breach, for example, security teams lead the technical investigation and containment while compliance teams handle regulatory reporting - but both must work together on root cause analysis and corrective measures.
Creating an effective roadmap requires understanding how different regulations overlap. Consider how GDPR and HIPAA both address data breach notifications but with different timeframes and processes. By mapping these requirements against security controls, organizations can develop efficient processes that satisfy multiple regulatory needs simultaneously.
We've seen organizations struggle when treating security and compliance as entirely separate domains. This approach often leads to duplicate efforts and missed opportunities for efficiency. Instead, success comes from viewing them as interconnected components of a broader risk management process.
Tips for security / compliance management
While these challenges are significant, organizations can take deliberate steps to align their efforts.
1- Treat frameworks and guidelines as complementary
Use security frameworks to structure your overall approach and compliance guidelines to fill in the regulatory details. For instance, you can implement ISO 27001 controls to strengthen your security posture and cross-reference them with PCI DSS requirements to ensure compliance in handling payment data.
2- Focus on risk-based prioritization
Not all compliance requirements carry equal weight in terms of security impact. Perform a risk assessment to determine which controls provide the most benefit to your organization. For example, addressing data encryption might satisfy multiple regulations while directly enhancing security.
3- Regularly review both standards and threats
Schedule periodic reviews of your compliance obligations and security controls to keep up with new regulations and evolving risks. This practice can highlight gaps and areas for improvement before they become problems.
4- Document interpretations and decisions
When applying security frameworks to meet compliance requirements, document your reasoning. For example, explain how a specific NIST control satisfies a HIPAA mandate. This approach not only aids in audits but also helps internal teams stay aligned.
5- Invest in expertise and automation
Consider using tools that map security frameworks to compliance requirements automatically. Some solutions can generate reports showing how your current security measures align with regulations, saving time and reducing errors.

Security and compliance teams: Roles and responsibilities
The relationship between security and compliance teams shapes an organization's risk management effectiveness. While these teams maintain distinct focuses, their work intersects at crucial points that demand careful coordination and mutual understanding.
Their division can create tension - security might prefer strict technical controls that compliance sees as too restrictive for business operations, or compliance might request documentation that security teams find burdensome during incident response.
When these teams work well together, they strengthen each other's efforts. Security measures often satisfy multiple compliance requirements, while compliance processes help identify security gaps.
Some of the roles include:
- Chief Information Security Officer (CISO)
- Chief Compliance Officer
- Risk Manager
- Security Operations Manager
- GRC Director
- Security Engineers
- Compliance Analysts
- Security Architects
- Audit Coordinators
- Policy Specialists
At the executive level, the Chief Information Security Officer (CISO) and Chief Compliance Officer work together to set organizational strategy. The CISO focuses on security vision and implementation, while the Compliance Officer ensures regulatory alignment. These roles often report to different executives - the CISO typically to the CIO or CTO, and the Compliance Officer to the General Counsel or CEO - creating a healthy system of checks and balances.
Below this level, we see three main operational areas where security and compliance intersect:
Risk Management serves as a bridge between security and compliance. The Risk Management team, led by the Risk Manager, works closely with both departments to assess threats, vulnerabilities, and regulatory exposure. They help translate security risks into compliance implications and vice versa.
Security Operations represents the technical heart of security implementation. The Security Operations Manager oversees the daily execution of security measures, coordinating with the compliance team to ensure controls meet regulatory requirements while remaining operationally feasible. This often includes managing privileged-access tools such as a password manager for IT teams, which helps standardize credential governance across systems.
Governance, Risk, and Compliance (GRC) acts as an integration point. The GRC team oversees security and activities to achieve compliance, ensuring alignment between technical controls and regulatory demands.
These roles interact through formal and informal channels. For instance, when implementing new security controls, Security Engineers consult with Compliance Analysts early in the design phase. During audits, Audit Coordinators work closely with Security Operations to gather technical evidence.
The effectiveness of this structure depends on clear communication paths and well-defined processes. Shared reporting structures ensure consistent tracking of both security and compliance metrics. Joint planning sessions allow teams to coordinate responses to new threats or regulatory changes.
Building an integrated security and compliance program
We recommend starting with these key elements:
-
Map your requirements: Create a unified control framework that aligns security measures with compliance requirements. This reveals where different regulations overlap and helps prevent duplicate efforts.
-
Establish clear communication: Set up regular meetings between security and compliance teams. This keeps everyone aligned on objectives and helps identify potential issues early.
-
Document everything: Maintain detailed records of decisions, changes, and control implementations. This documentation serves both security and compliance needs.
-
Plan for growth: Build flexibility into your roadmap. Make continuous risk assessments to identify security needs and keep tabs on how regulatory requirements evolve. Your program should adapt accordingly.
From our work with various organizations, we've learned that success comes from viewing security and compliance as interconnected components of risk management. When implementing new security controls, involving compliance teams early helps ensure regulatory alignment. This prevents situations where technical solutions meet security needs but fall short of compliance requirements.
Final thoughts
Security and compliance may often feel like two opposing forces, but they’re far from irreconcilable. Throughout this article, we’ve examined the distinctions and the challenges in balancing these priorities, along with practical tips to navigate the process. It’s clear there’s no one-size-fits-all answer. Each organization will need to find the balance that fits its unique risk profile, regulatory requirements, and business objectives.
Writing about this topic has highlighted just how nuanced and layered it can be. If it left you with more questions than answers, that’s actually a good sign—it means you’re engaging critically with the topic. The process of aligning security and compliance requires both thoughtfulness and adaptability, and with the right strategies, it’s entirely manageable.















