Cybersecurity Asset Management is becoming harder to ignore as the number of connected devices inside organizations continues to grow.
A report by JupiterOne found a 133% year-over-year increase in cyber assets. Meanwhile, attackers are shifting their attention toward the assets on the edge of networks. CrowdStrike's 2025 Global Threat Report highlights that adversaries are now exploiting endpoints like laptops, smartphones, and tablets — especially in environments shaped by remote work and bring-your-own-device (BYOD) policies.
It's a risky combination. Every device that connects to your network opens up a potential entry point. Compromised assets often go unnoticed until it's too late. Attackers don't need to hit the core to do damage — they just need one vulnerable device on the edge.
So, are you sure you’ve accounted for every asset in your environment? Keep reading to understand why Cybersecurity Asset Management is key to closing those gaps.
What is Cybersecurity Asset Management (CSAM)?
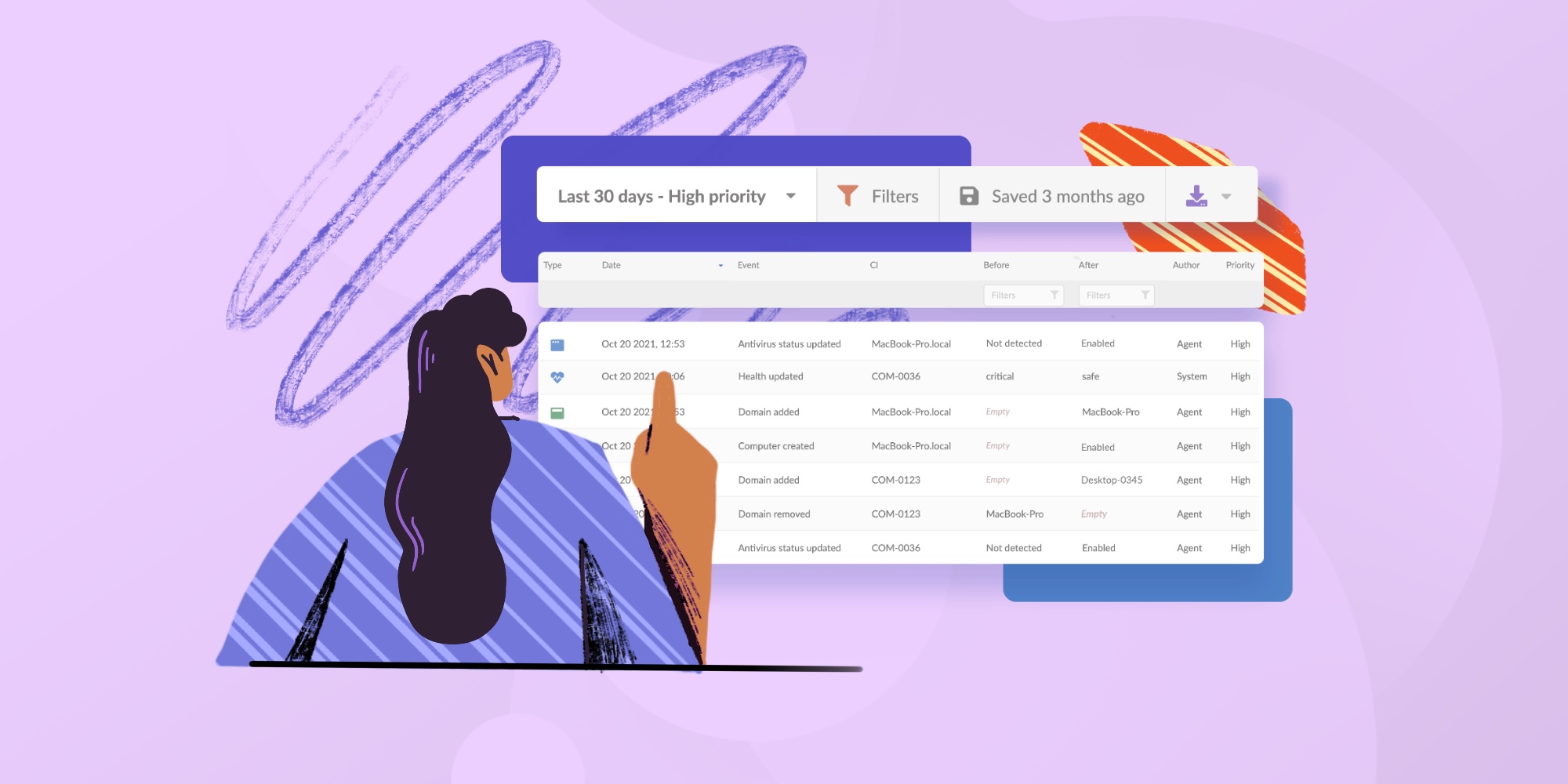
Cybersecurity Asset Management (CSAM) is the process of discovering, classifying, and monitoring every device, application, and service in your organization from a security perspective. It goes beyond just listing what's on your network — it must help security teams understand the exposure, configuration, and behavior of each asset.
The goal is to maintain a live, accurate inventory that reflects not just what exists, but also how it’s secured and whether it poses a risk. That includes tracking unmanaged devices, identifying outdated software, and flagging assets that fall outside of policy.
Done right, CSAM gives organizations the visibility they need to detect vulnerabilities early, reduce blind spots, and respond to threats before they escalate.

What are cyber assets?
Cyber assets are any digital components that support your organization’s IT or security operations. That includes hardware like laptops, servers, IoT sensors, routers, and smartphones, as well as software, cloud services, user accounts, and even APIs. If it stores data, communicates over your network, or interacts with other systems, it counts.
The definition has expanded in recent years. It's not just company-issued laptops or on-prem servers anymore. Personal devices under BYOD policies, virtual machines in the cloud, third-party tools with API access — they’re all part of your attack surface. Each one adds complexity, especially when it’s not centrally managed or tracked.
CSAM vs. ITAM
While IT Asset Management (ITAM) focuses on lifecycle and operational management — like procurement, maintenance, and depreciation — CSAM zeroes in on risk and security. The goal is to understand what assets exist, where they are, how they're configured, and whether they pose a threat to the organization.
The distinction matters. ITAM might tell you that you own 300 laptops. CSAM tells you which ones are unpatched, running outdated software, or actively communicating with known malicious IPs.
Why is CSAM cybersecurity important?
Security starts with knowing what you’re protecting. Without a complete and up-to-date inventory of your assets, it’s easy to miss risks hiding in plain sight. Cybersecurity Asset Management (CSAM) helps eliminate that blind spot by giving security teams a clear view of every device, service, and system connected to their environment—regardless of who owns it or where it's running.
It's important because assets are constantly changing. New devices join the network, configurations drift, and old software doesn’t always get patched. That makes it hard to know what’s secure and what’s not. And attackers know it. They often target overlooked assets —like laptops, cloud instances, or IoT devices—because those tend to have fewer protections in place.
With CSAM, you’re not just keeping a list of devices. You’re creating a real-time map of your attack surface. That means being able to:
- Spot unmanaged or unauthorized devices before they become a problem.
- Identify outdated or vulnerable software running across environments.
- Understand how assets are connected so that incidents can be contained faster.
- Prioritize response based on real-world risk, not assumptions.
Real-world data backs up the need for better visibility. Cisco’s 2024 Cybersecurity Readiness Index found that while many organizations are investing in cloud and network protections, endpoint security often lags behind. Only 7% of surveyed companies reached a “Mature” level of readiness for endpoint protection. At the same time, adoption of key controls like firewalls and behavior monitoring is widespread—but full deployment remains inconsistent.
That gap between deployment and actual coverage highlights why CSAM matters. It helps organizations understand where protections are truly in place—and where they’re only assumed to be.

Challenges in Cybersecurity Asset Management
CSAM isn't as straightforward as installing a tool and calling it done. Organizations face several challenges:
- Inventory accuracy: Many companies don't have an up-to-date record of what's in their environment. Assets spin up and down dynamically, especially in cloud and virtualized setups.
- Shadow IT and BYOD: Employees introduce personal devices or cloud services that fly under the radar.
- Data silos: Security, IT, and operations teams often maintain separate systems with incomplete data.
- Lack of context: Knowing an asset exists is not enough. You need to know how it's used, who owns it, and whether it's vulnerable.

How to implement Cybersecurity Asset Management
A strong CSAM program starts with three foundational steps:
- Build a unified inventory: Use automated tools to detect and catalog all devices and services across on-prem, cloud, and edge environments. Passive discovery, active scans, and API integrations can help gather a full picture.
- Classify and contextualize assets: Assign ownership, tag by business function, and correlate with vulnerability and threat intelligence data. This gives security teams meaningful insight into where risk lives.
- Continuously monitor and respond: CSAM isn’t a set-it-and-forget-it task. Establish continuous monitoring for device behavior, configuration drift, and exposure to known threats. Integrate alerts into your broader incident response workflows.
Some organizations implement CSAM through specialized platforms. Others extend their ITAM, configuration management database (CMDB), or EDR tools. Whatever the approach, success depends on cross-functional cooperation between IT, security, and business units.
In conclusion
Cybersecurity Asset Management isn't just another box to check — it's a core part of a resilient security strategy. As attackers target the edge and digital ecosystems grow more complex, having a clear and accurate view of your assets becomes non-negotiable.
Organizations that treat CSAM as a living, active process are better positioned to prevent breaches, detect threats early, and minimize risk across their environments.
You can use InvGate Asset Management to support your CSAM strategy. It will allow you to identify every asset connected to your network—on-prem, remote, or cloud-based. It will also give you detailed visibility into device configurations, software versions, and ownership, helping you spot unmanaged or risky assets faster. Try it for free for 30 days!















