Staying on top of cybersecurity threats is more crucial than ever in today's rapidly evolving digital landscape. On February 27, 2023, a critical vulnerability in WebKit was identified, labeled as CVE-2023-23529.
This vulnerability allows attackers to execute arbitrary code on a target system and gain unauthorized access to sensitive information. In this article, we'll overview CVE-2023-23529 vulnerability, including its associated risks, how to identify devices exposed to it, and most importantly, how to patch it to ensure your systems remain secure.
Don't leave your systems vulnerable to cyber threats. Keep reading to learn more about patching WebKit Vulnerability (CVE-2023-23529).
About CVE-2023-23529
CVE-2023-23529 is a type of confusion issue in the WebKit browser engine, which can be triggered by maliciously crafted web content and ultimately allow code execution.
WebKit is an open-source web browser engine used by popular browsers such as Safari. It is widely used across multiple platforms, including iOS, macOS, iPadOS, and Linux. The vulnerability was found in the JavaScript engine of WebKit, which is responsible for executing JavaScript code on websites.
The CVE-2023-23529 exploit allows attackers to execute arbitrary code on a user's device when they visit a specially crafted website. An attacker can take advantage of this by using a malicious website to send a crafted message to the JavaScript engine, causing it to execute the attacker's code instead of the intended code. Once the attacker's code is executed, they can gain full control of the user's device.
The severity of this vulnerability is classified as critical, as it poses a significant risk to the security and privacy of users who visit affected websites. Since WebKit is used in many popular web browsers, this vulnerability potentially impacts many users.
Apple, the primary maintainer of WebKit, quickly released a patch for the vulnerability shortly after its discovery.
How to find devices exposed to CVE-2023-23529
With InvGate Asset Management, you can swiftly identify devices affected by the CVE-2023-23529 vulnerability. Here are the steps to follow:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:iOS” (or your device) to filter all Apple devices.
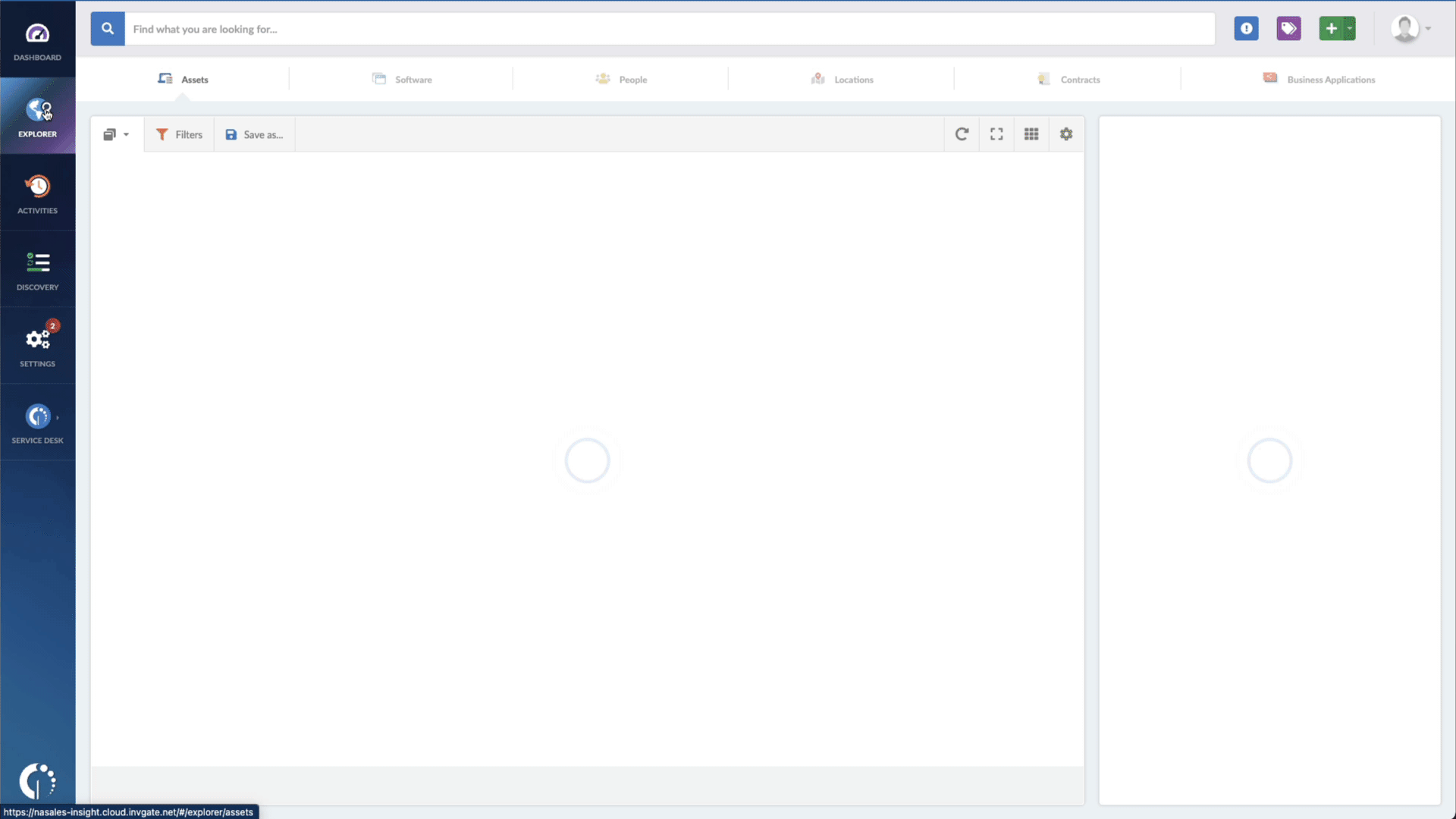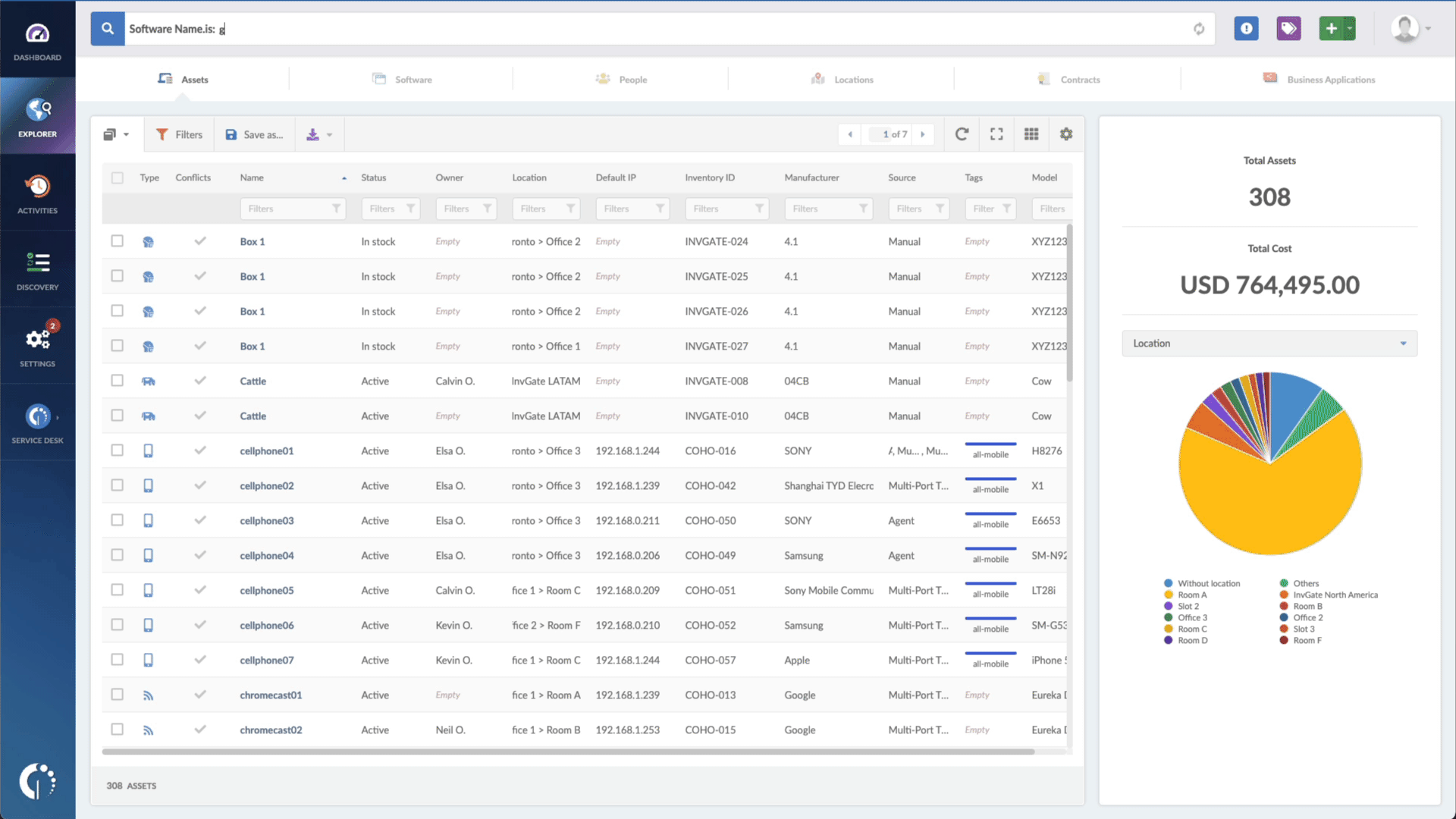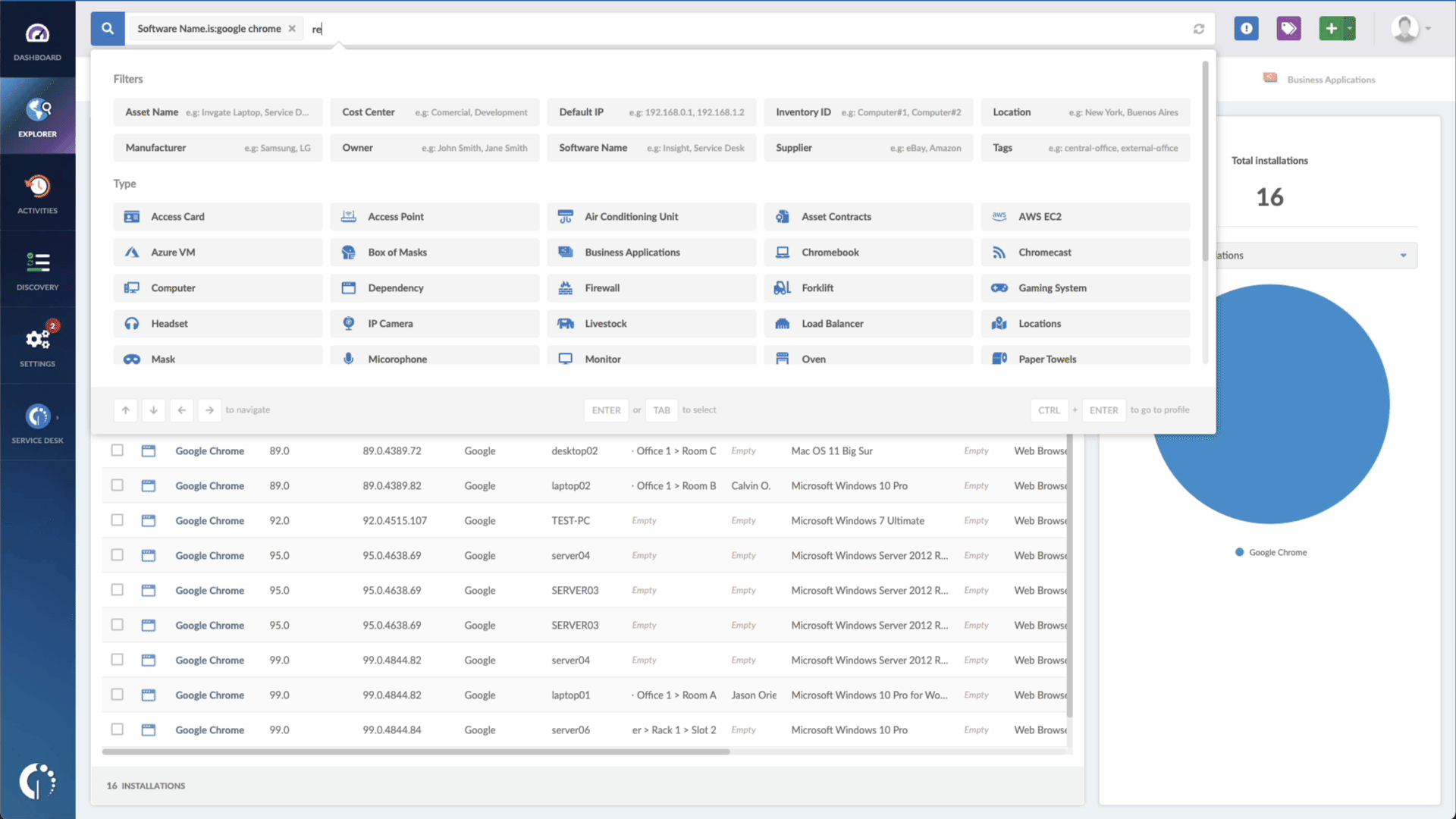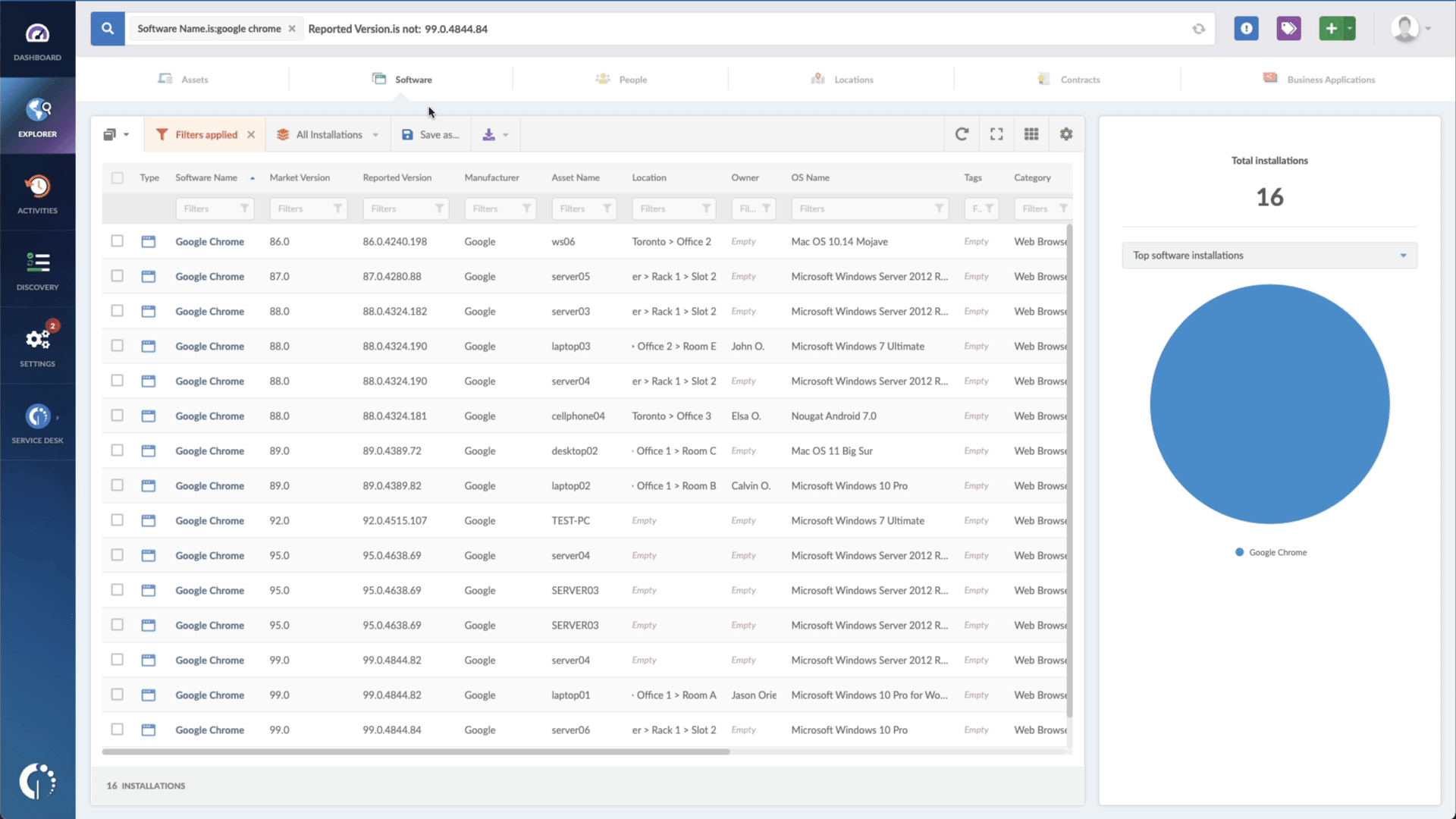
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version (macOS Ventura 13.2.1, iOS 16.3.1 and iPadOS 16.3.1, Safari 16.3).
That’s it! Now you have a list of all the Apple devices vulnerable to CVE-2023-23529. You can then export this list in CSV format and give it to one of your agents to patch or create a ticket so they can be manually updated.
The bottom line
The CVE-2023-23529 vulnerability in WebKit highlights the importance of prompt Patch Management to mitigate potential risks to organizations. Attackers can exploit it to execute arbitrary code on affected devices, leading to data breaches, system crashes, and other security incidents.
It is crucial to update the latest version of the affected software containing the patch for this exploit. To help you with that, InvGate Asset Management can simplify Patch Management by allowing system administrators and security professionals to identify and track vulnerable devices in their networks quickly.
If you're interested in trying out InvGate Asset Management's Patch Management capabilities, we invite you to sign up for our 30-day free trial. With InvGate Asset Management, you can quickly identify and remediate vulnerabilities in your network, protecting your organization's security posture. Don't wait any longer; start your free trial today and safeguard your network from potential threats.