With the increasing frequency and sophistication of cyber attacks, staying on top of potential vulnerabilities in your software and systems is critical. On March 14, 2023, Microsoft alerted users about a critical vulnerability, CVE-2023-23397, in Microsoft Outlook.
The vulnerability allows attackers to gain elevated privileges and compromise sensitive information, affecting users of Microsoft Outlook worldwide. In this article, we'll provide a detailed overview of the CVE-2023-23397 vulnerability, including its associated risks, how to identify devices exposed to this vulnerability, and how to patch your systems to ensure your security.
If you want to learn more about CVE-2023-23397, read on and learn how to stay secure!
About CVE-2023-23397
CVE-2023-23397 is a security vulnerability that affects Microsoft Outlook, the popular email client application used by individuals and businesses around the world.
This vulnerability allows an attacker to gain elevated privileges on a targeted system, potentially leading to the compromise of sensitive information or the installation of malware.
An attacker who can exploit it can execute arbitrary code with elevated privileges, which could allow them to take control of the affected system, access sensitive information, or launch other attacks.
The risk of not patching this vulnerability is significant. If left unaddressed, attackers can use this vulnerability to compromise systems and gain access to sensitive information. The potential impact of an attack could be severe, leading to data breaches, financial losses, and reputational damage.
Microsoft has released a patch to address it. All supported versions of Microsoft Outlook for Windows are affected, so users are urged to update it to the latest version as soon as possible.
How to find devices exposed to CVE-2023-23397
If you suspect your system may be vulnerable to the CVE-2023-23397 vulnerability, taking immediate action to mitigate the risk is crucial. With InvGate Asset Management, you can easily track your devices that are exposed to it. Follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
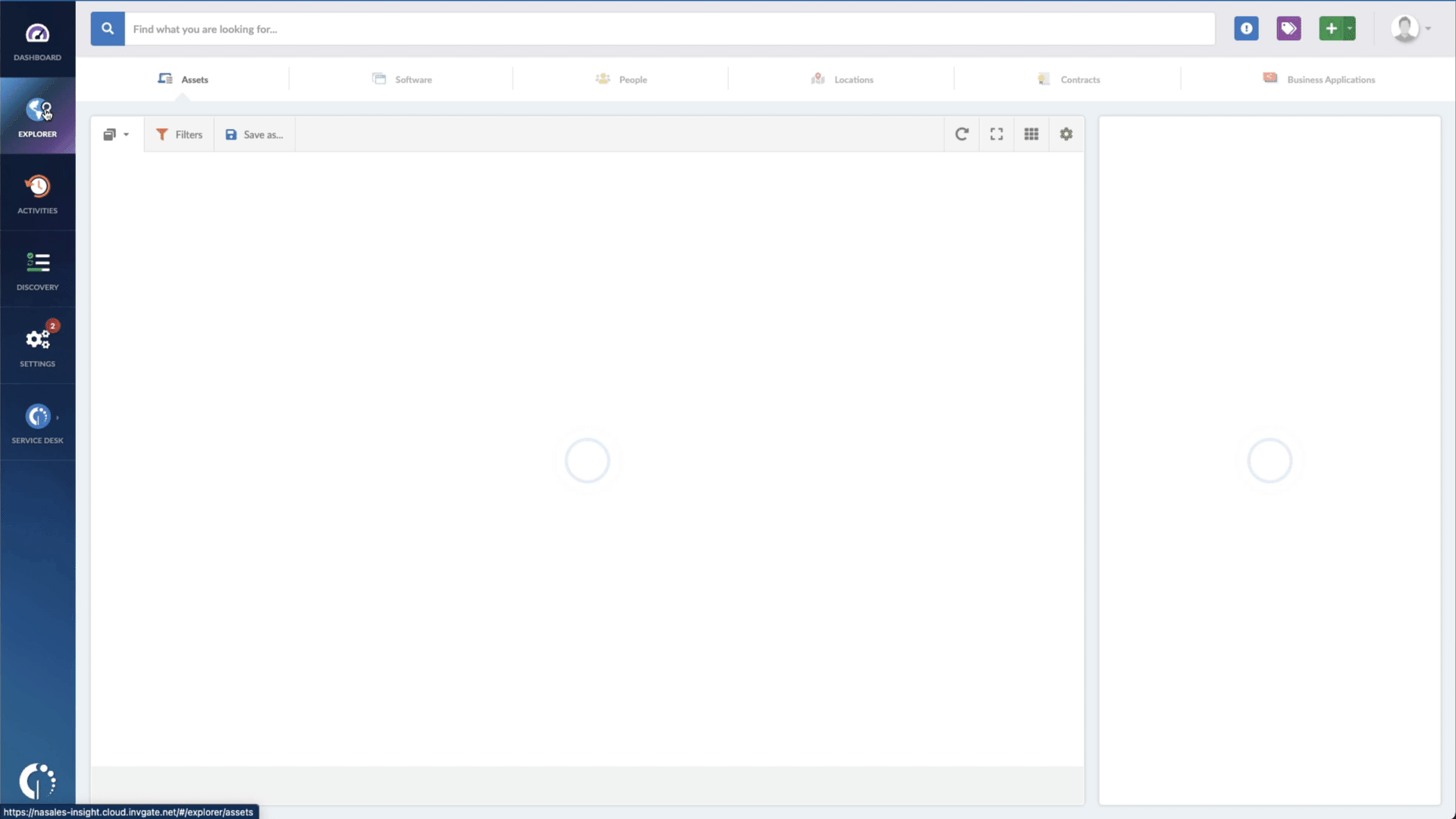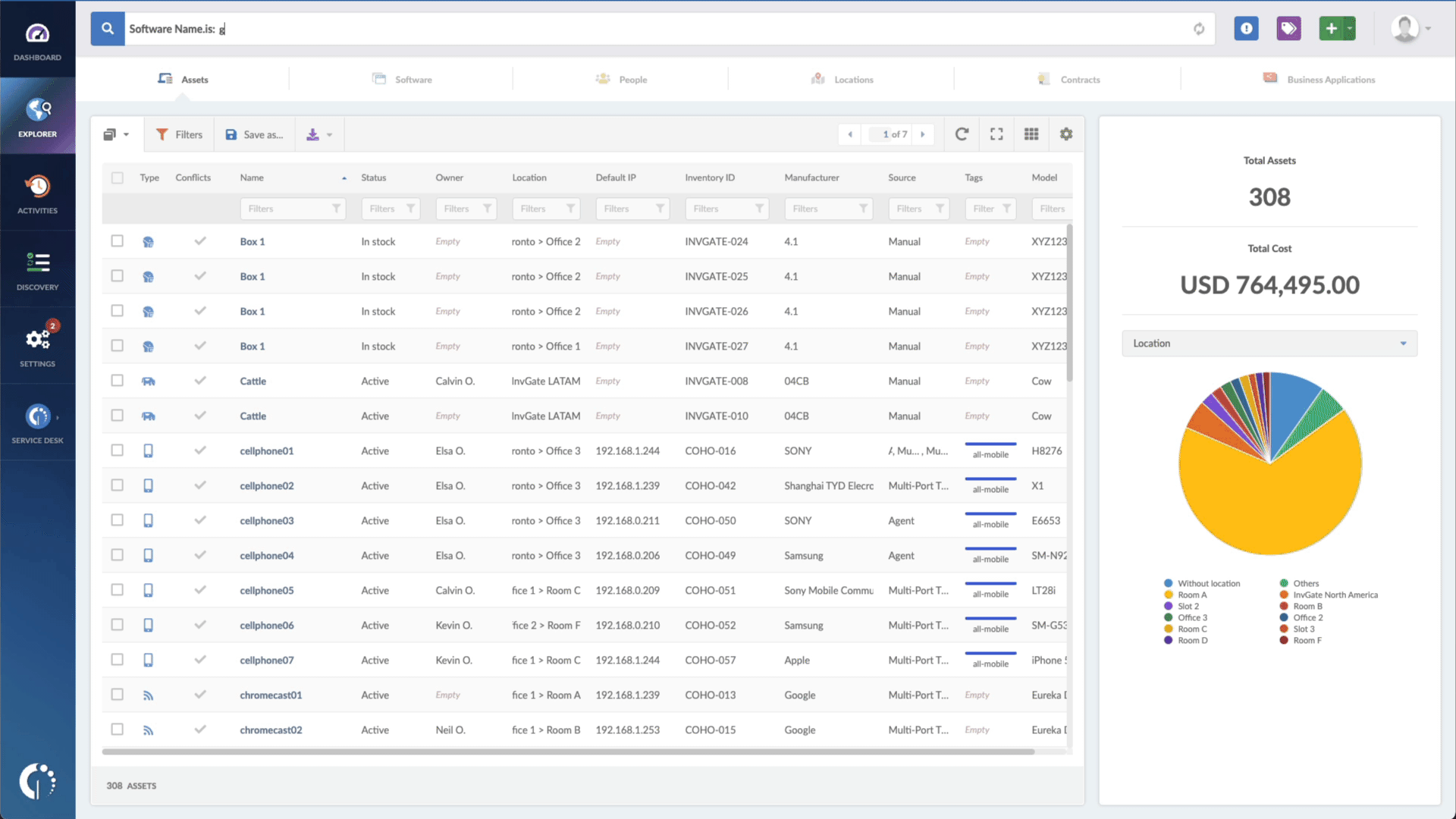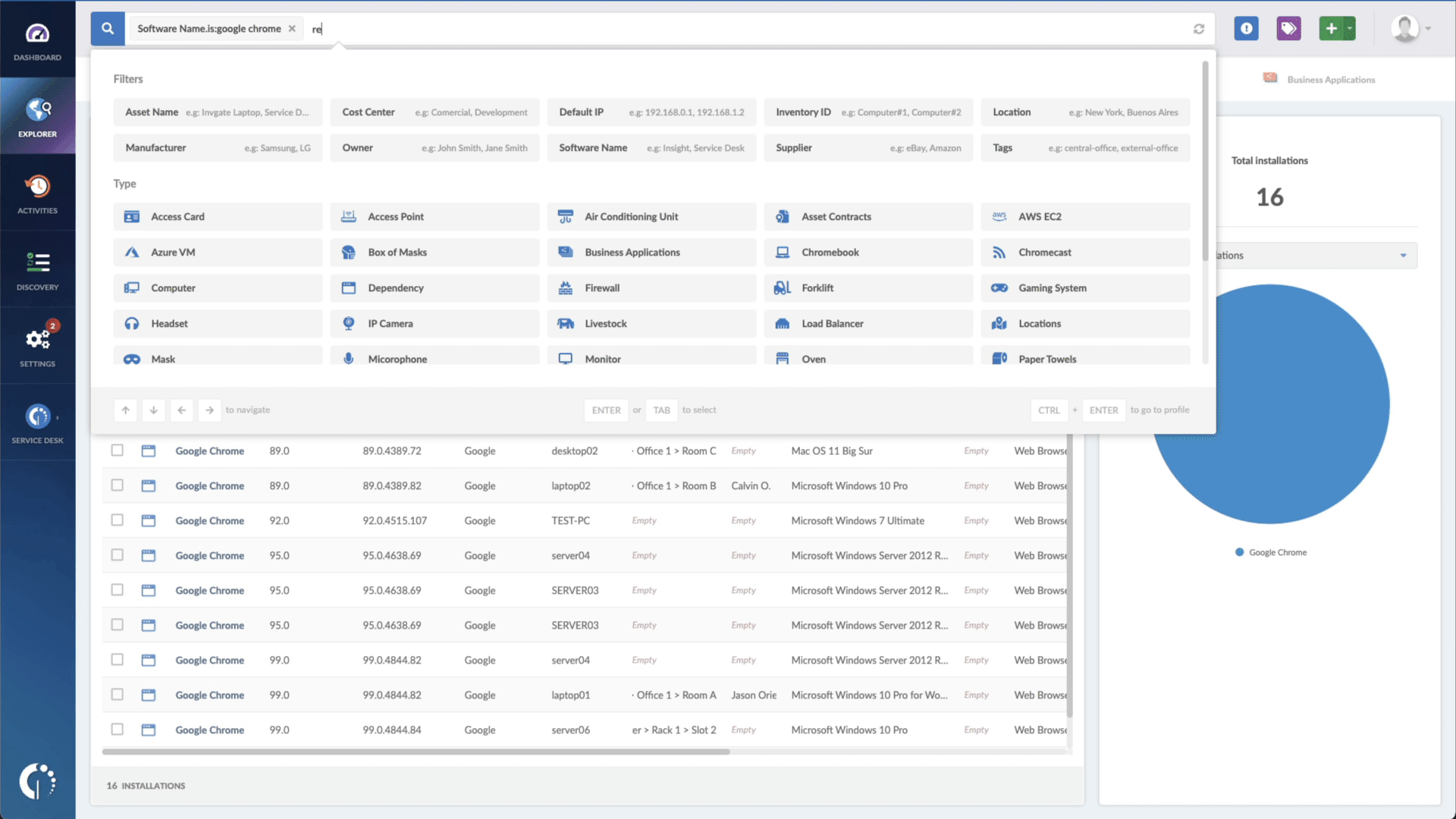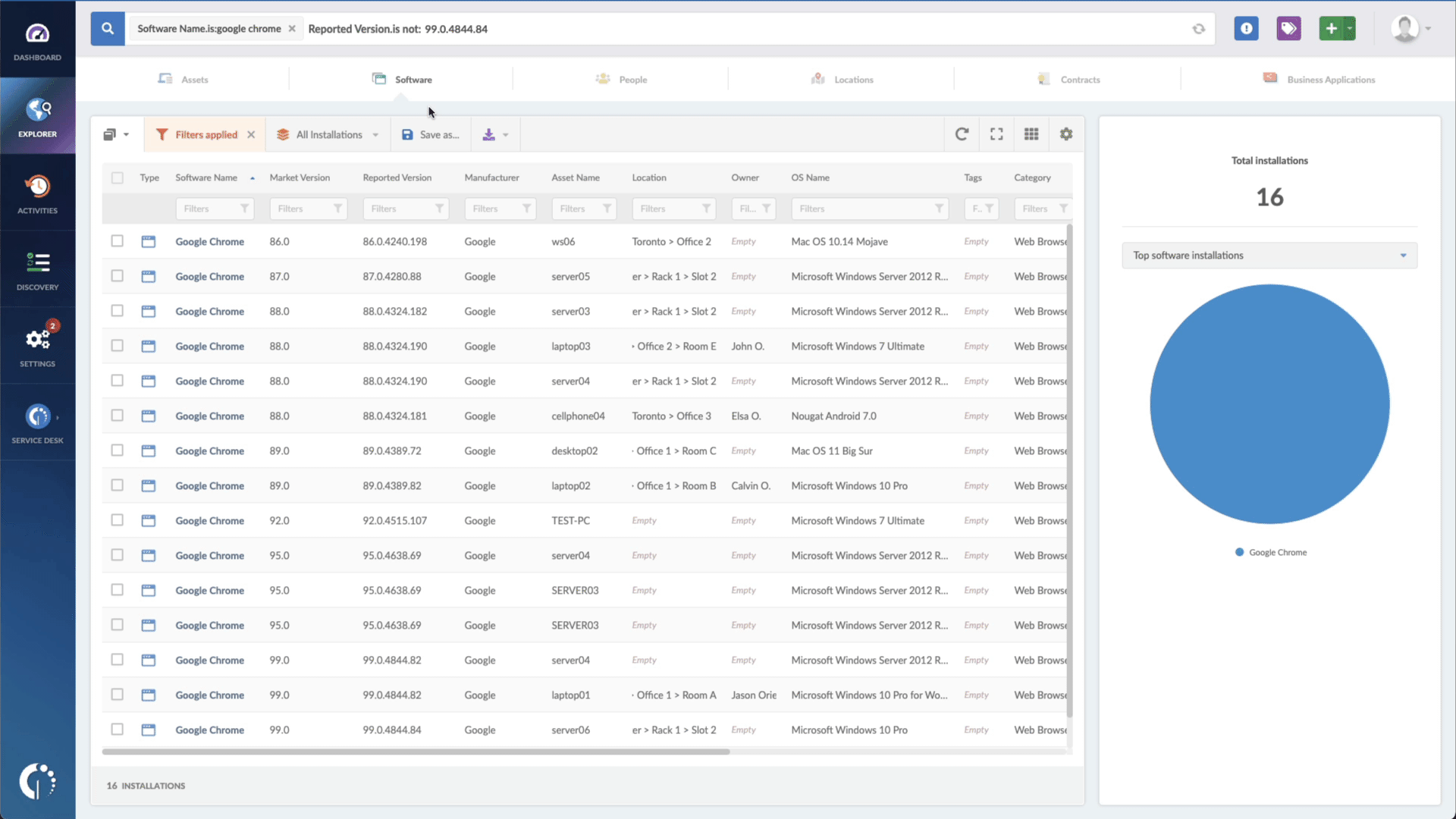
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your version, you’ll find the security update number on Microsoft’s webpage).
In just a few clicks, you have a list of all the Windows devices vulnerable to CVE-2023-23397. You can then export this list in CSV format and give it to one of your agents to patch or create a ticket so they can be manually updated.
The bottom line
CVE-2023-23397 is a critical vulnerability affecting Microsoft Outlook that can lead to elevated privileges and potential system compromise. Failure to patch this vulnerability can result in significant risks, including data breaches and financial losses.
With InvGate Asset Management, identifying and patching vulnerabilities in your organization's systems is simple. Don't take the risk of leaving your systems vulnerable to attacks like CVE-2023-23397. Request a 30-day free trial of InvGate Asset Management and see how easy it can be to stay on top of your network's security needs.