With cyber threats increasing in frequency and sophistication, staying up-to-date on the latest security vulnerabilities is essential for individuals and businesses. On February 14, 2023, Microsoft released a statement warning users about a critical vulnerability affecting the Windows Graphics Component, known as CVE-2023-21823.
This vulnerability could allow attackers to execute remote code on affected systems, leading to severe consequences such as data theft, system compromise, and more. Microsoft has released a security patch to mitigate the risk of an attack, and users and organizations must apply it as soon as possible.
In this article, we’ll look at CVE-2023-21823 vulnerability, including its associated risks, and how to identify devices exposed to it. If you are concerned about the security of your devices and want to learn more about CVE-2023-21823 and how to protect yourself, keep reading!
About CVE-2023-21823
CVE-2023-21823 is a critical security vulnerability that affects the graphics component of Microsoft Windows. It allows an attacker to execute arbitrary code in an elevated context.
It affects various versions of Microsoft Windows, including Windows 10 and 11. Microsoft has released a security patch to address this vulnerability, and users are strongly advised to apply the patch as soon as possible to protect their systems from potential attacks.
How to find devices exposed to CVE-2023-21823
To find devices that are exposed to the CVE-2023-21823 exploit, you can count on InvGate Asset Management. You just need to follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
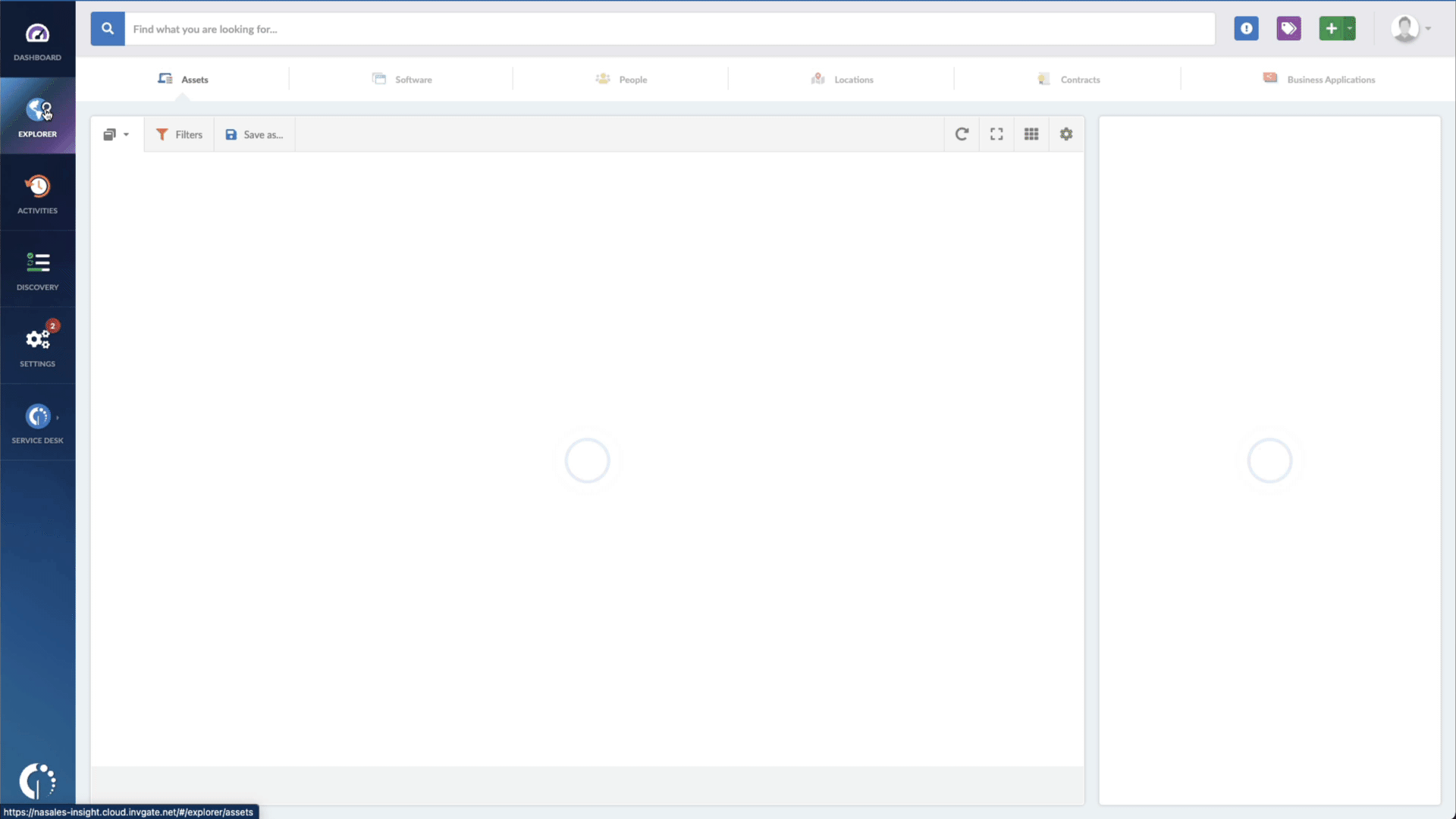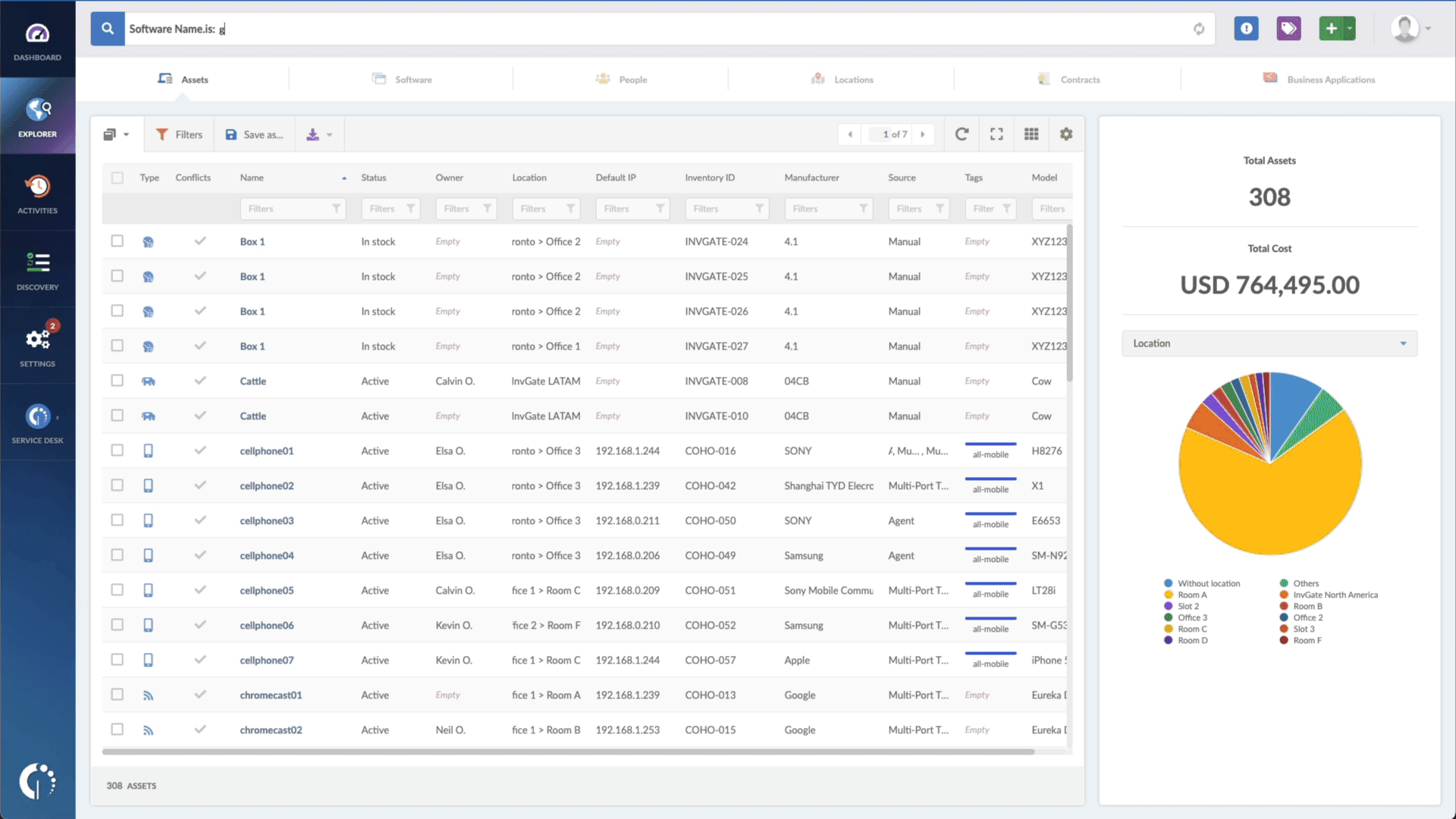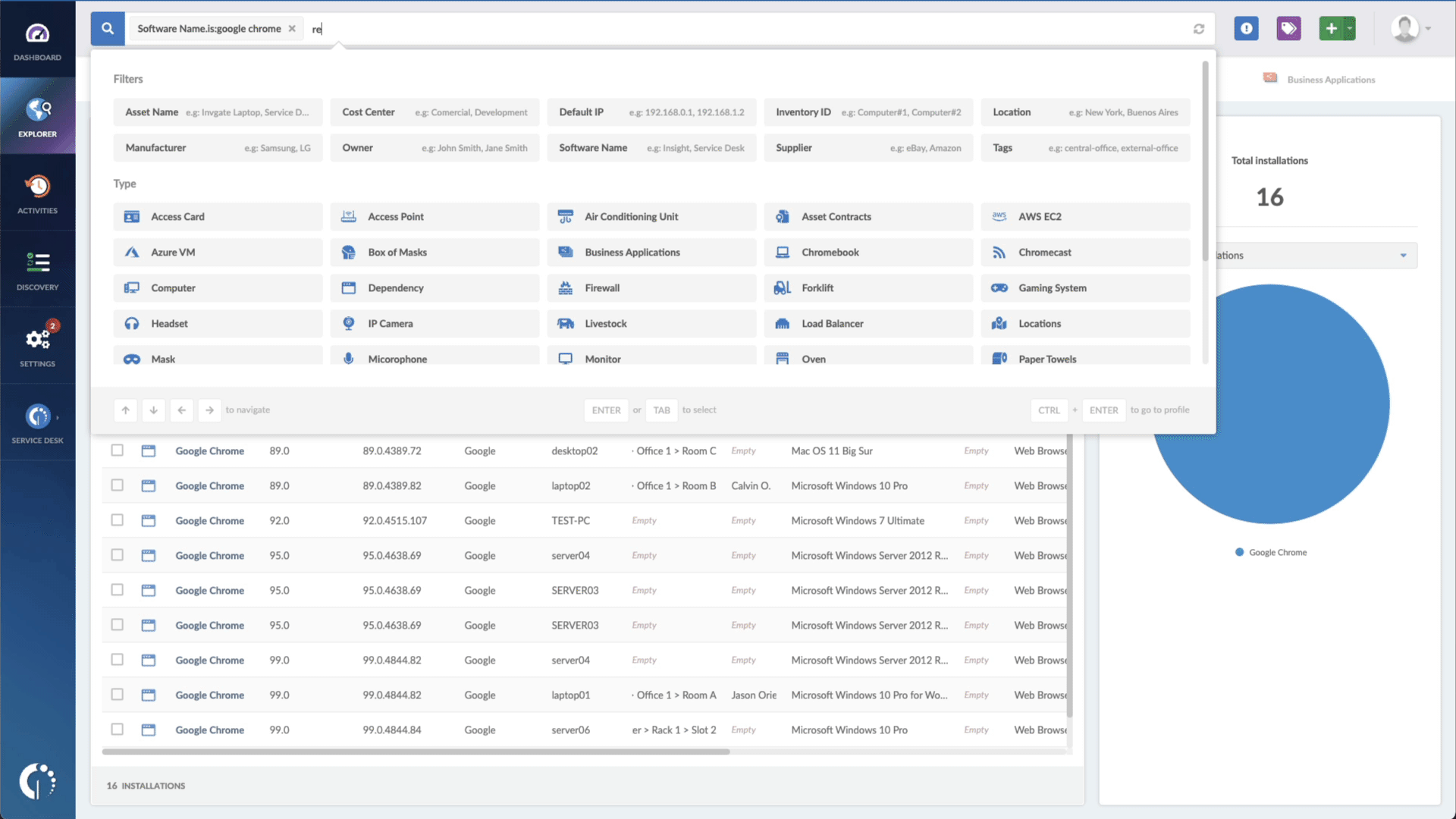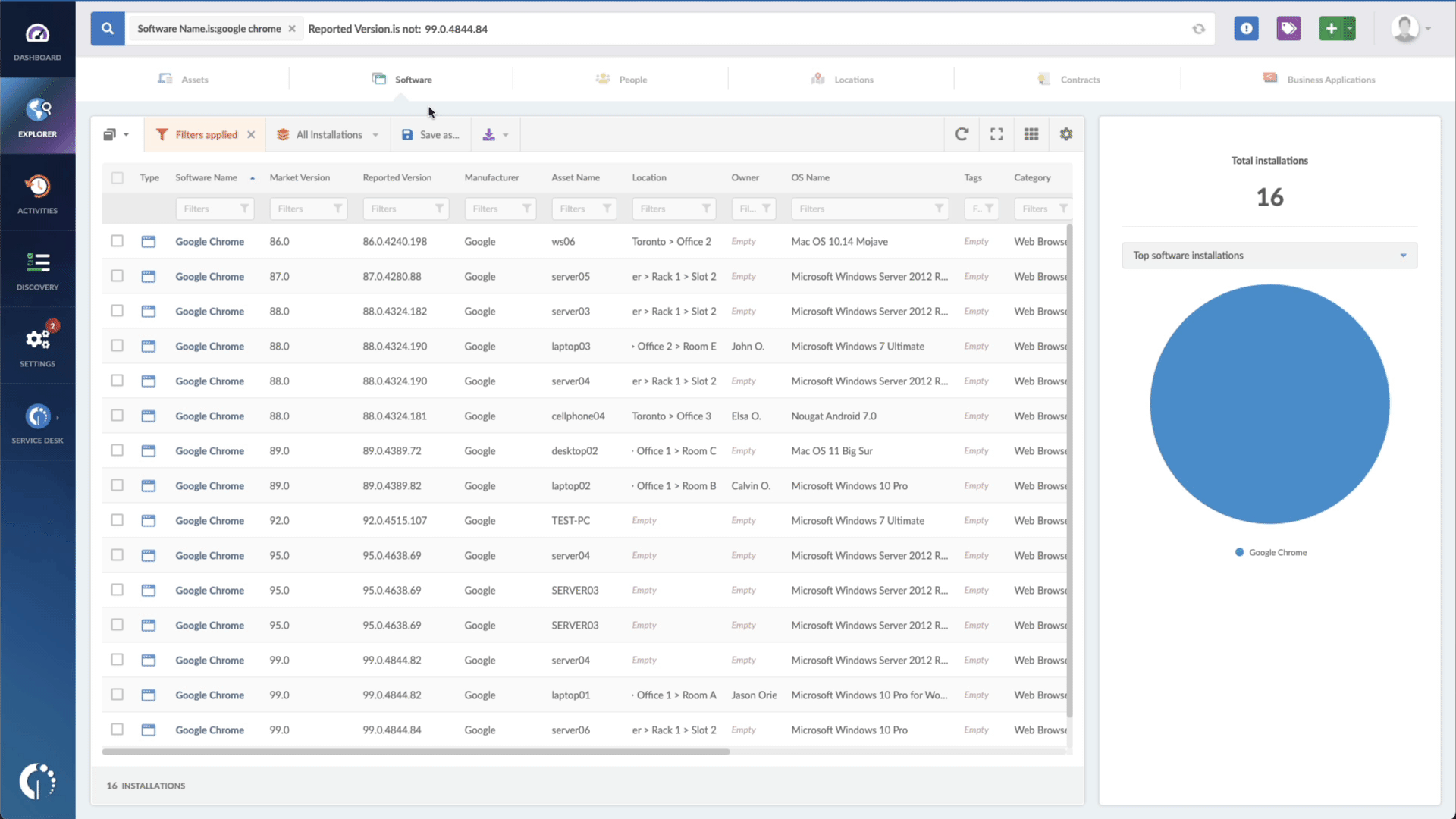
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your operating system, you’ll find the security update number on Microsoft’s webpage).
In just a few clicks, you have a list of all the Windows devices vulnerable to CVE-2023-21823. You can then export this list in CSV format and give it to one of your agents to patch or create a ticket so they can be manually updated.
Notable vulnerabilities to watch for
Another critical vulnerability that has recently been identified is CVE-2023-21716, a remote code execution (RCE) vulnerability in Microsoft Word. This vulnerability exists due to how Microsoft Word handles certain objects in memory, and it could allow an attacker to execute arbitrary code on a targeted system.
Like CVE-2023-21823, CVE-2023-21716 has the potential to cause significant damage, including the theft of sensitive data or the compromise of an entire system. Microsoft has released a security patch to address this vulnerability, and users and organizations should apply it as soon as possible.
The bottom line
CVE-2023-21823 is a critical exploit that affects the graphics component of Microsoft Windows, allowing attackers to execute arbitrary code on affected systems. Microsoft has released a security patch to address it, and users and organizations need to apply the patch immediately to mitigate the risk of an attack.
The consequences of a successful attack exploiting CVE-2023-21823 can be severe, ranging from data theft to full system compromise. Therefore, taking proactive measures to secure your network and devices is crucial.
InvGate Asset Management can help simplify Patch Management by quickly identifying devices needing updates, allowing system administrators and security professionals to take appropriate action to remediate the issue.
Don't wait for an attack to happen. Request InvGate Asset Management's 30-day free trial and scan your network for devices exposed to CVE-2023-21823. Take action now to protect your organization from potential threats.