As cyber attacks continue to evolve, it's essential to stay informed about potential vulnerabilities and take proactive steps to secure your systems. On December 13, 2022, Citrix released an official statement about a critical vulnerability affecting Citrix ADC and Gateway, known as CVE-2022-27518.
The vulnerability can allow attackers to execute arbitrary code on targeted systems, bypass authentication controls, and gain unauthorized access to sensitive data. In this article, we'll provide a comprehensive overview of CVE-2022-27518, including how to identify vulnerable devices with InvGate Asset Management and patch them.
If you're concerned about the security of your Citrix ADC and Gateway systems, keep reading to learn more about CVE-2022-27518 and how to protect your devices!
About CVE-2022-27518
CVE-2022-27518 is a critical vulnerability that was discovered in the Citrix ADC (Application Delivery Controller) and Citrix Gateway, formerly known as NetScaler ADC and NetScaler Gateway.
The vulnerability allows attackers to execute arbitrary code on the targeted system, bypassing authentication controls and gaining access to sensitive data. Thus, it is rated as critical, with a CVSS score of 9.8.
The exploit affects all supported versions of Citrix ADC and Gateway and was caused by a software's certificate handling mechanism flaw. Specifically, it occurs due to improper certificate validation within Citrix ADC and Gateway's Certificate Trust List (CTL) feature.
Attackers can send specially crafted requests to the targeted system, allowing them to execute arbitrary code with administrative privileges. If not patched, the vulnerability allows attackers to control the targeted system completely, including access to sensitive data and applications. Attackers could also use it to launch attacks on other systems connected to the same network. Therefore, patching it as soon as possible is essential to avoid any potential damage or data loss.
Citrix has released a patch, which users can download from the company's website. The latest software version that includes it is Citrix ADC and Gateway version 13.0-58.32.
How to find devices exposed to CVE-2022-27518
You can quickly detect devices that are impacted by the CVE-2022-27518 vulnerability using InvGate Asset Management. The following are the procedures to adhere to:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Citrix ADC” or “Software name, is:Citrix Gateway” to filter all devices that have those products installed.
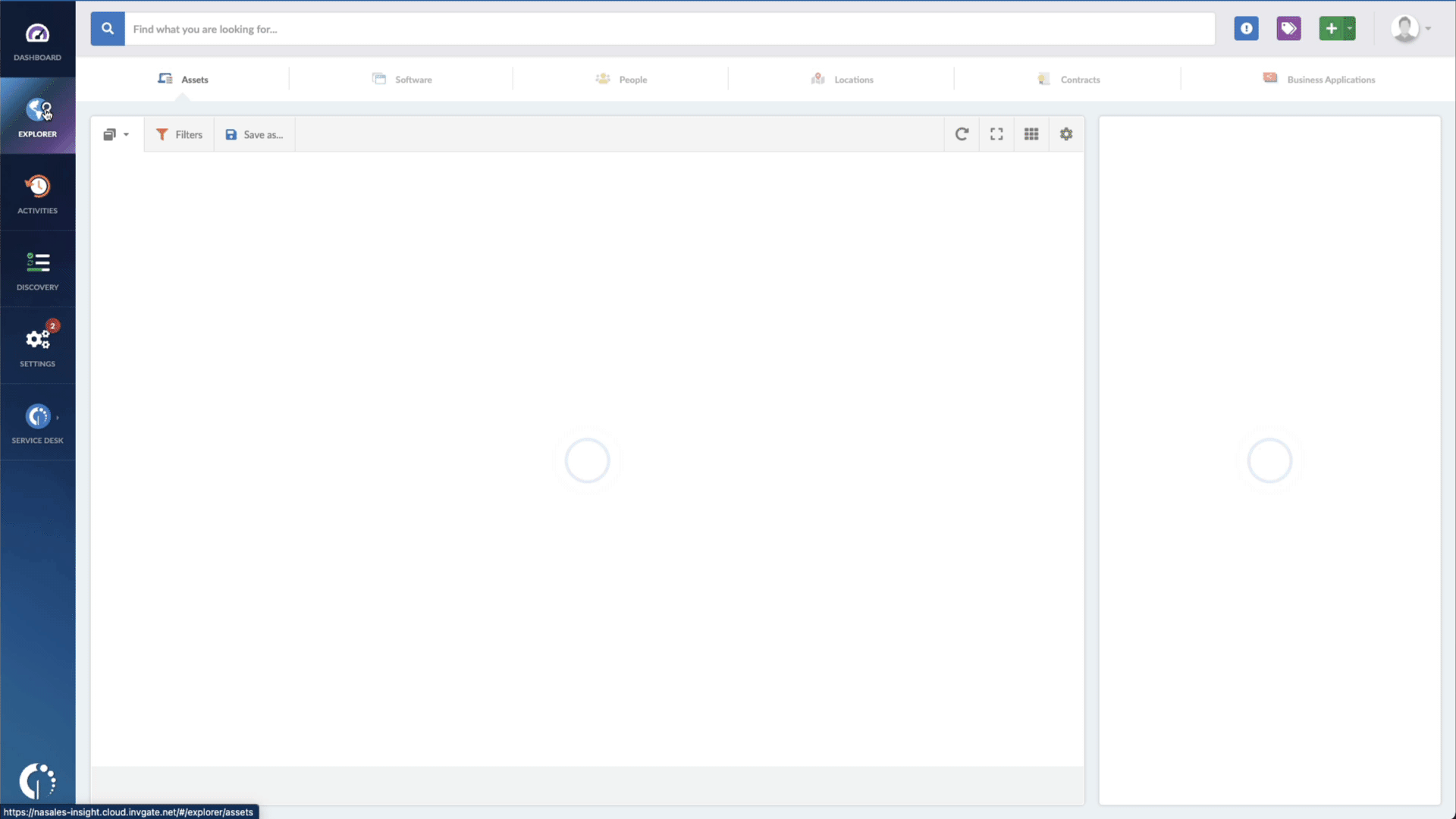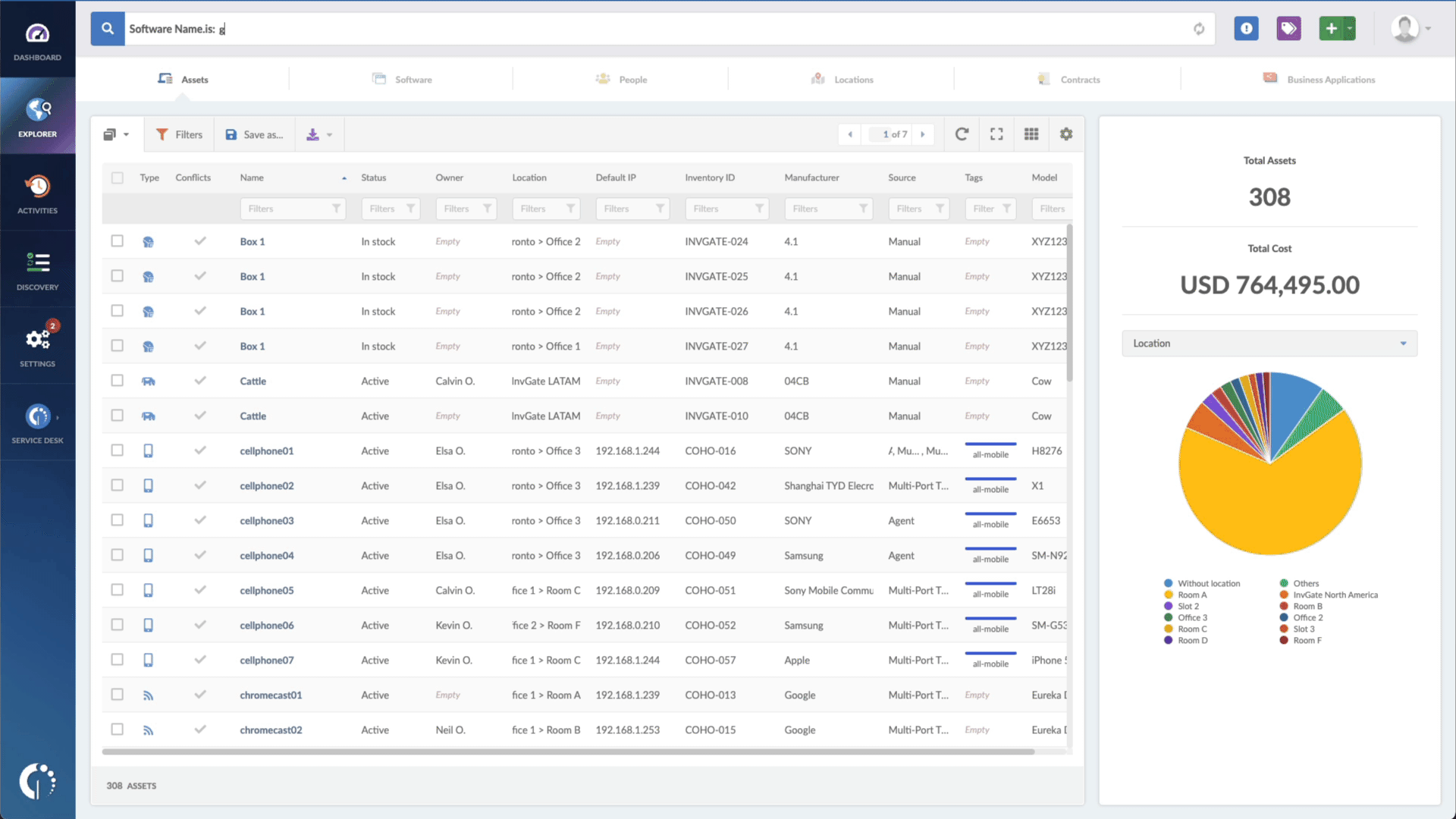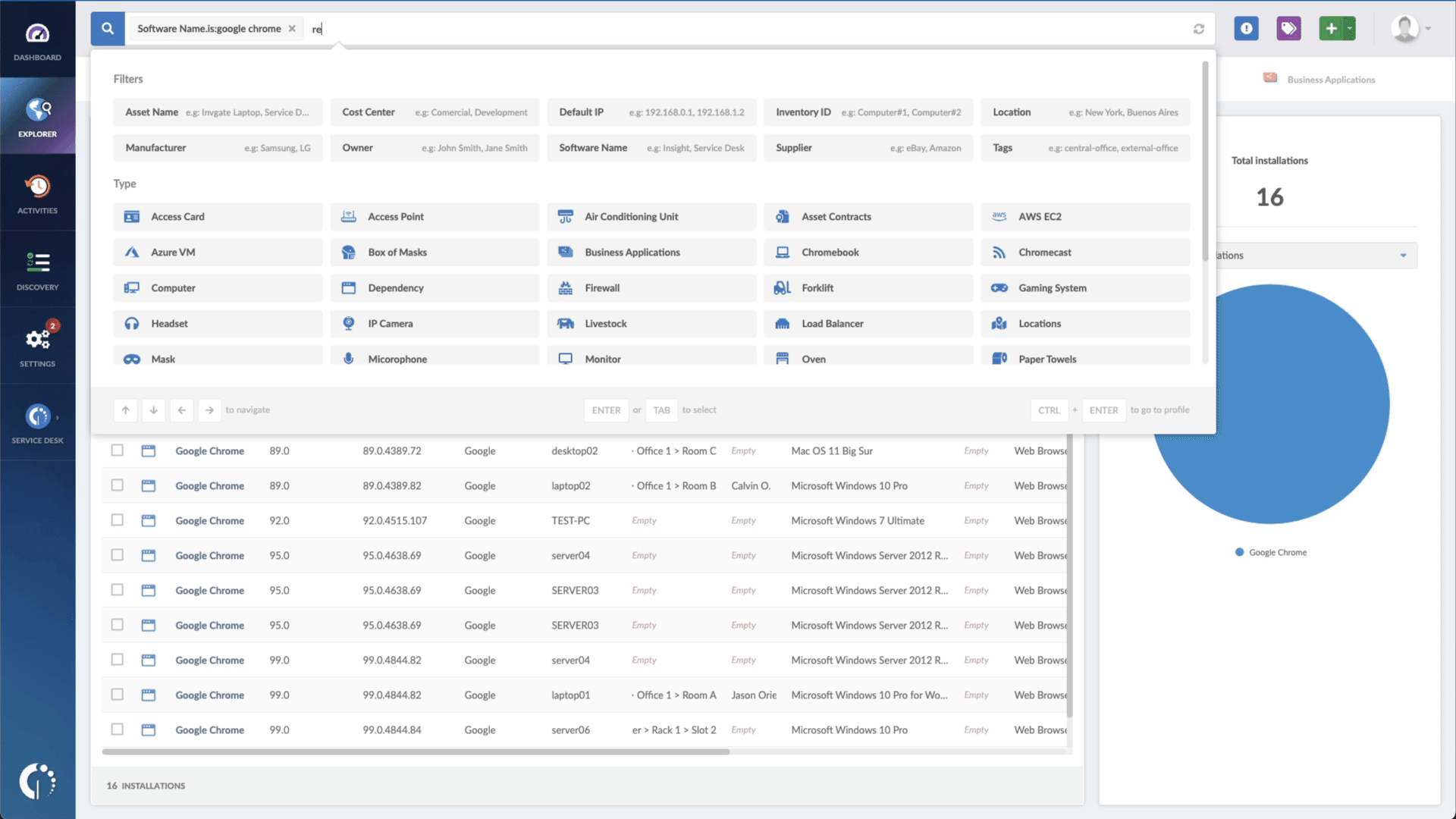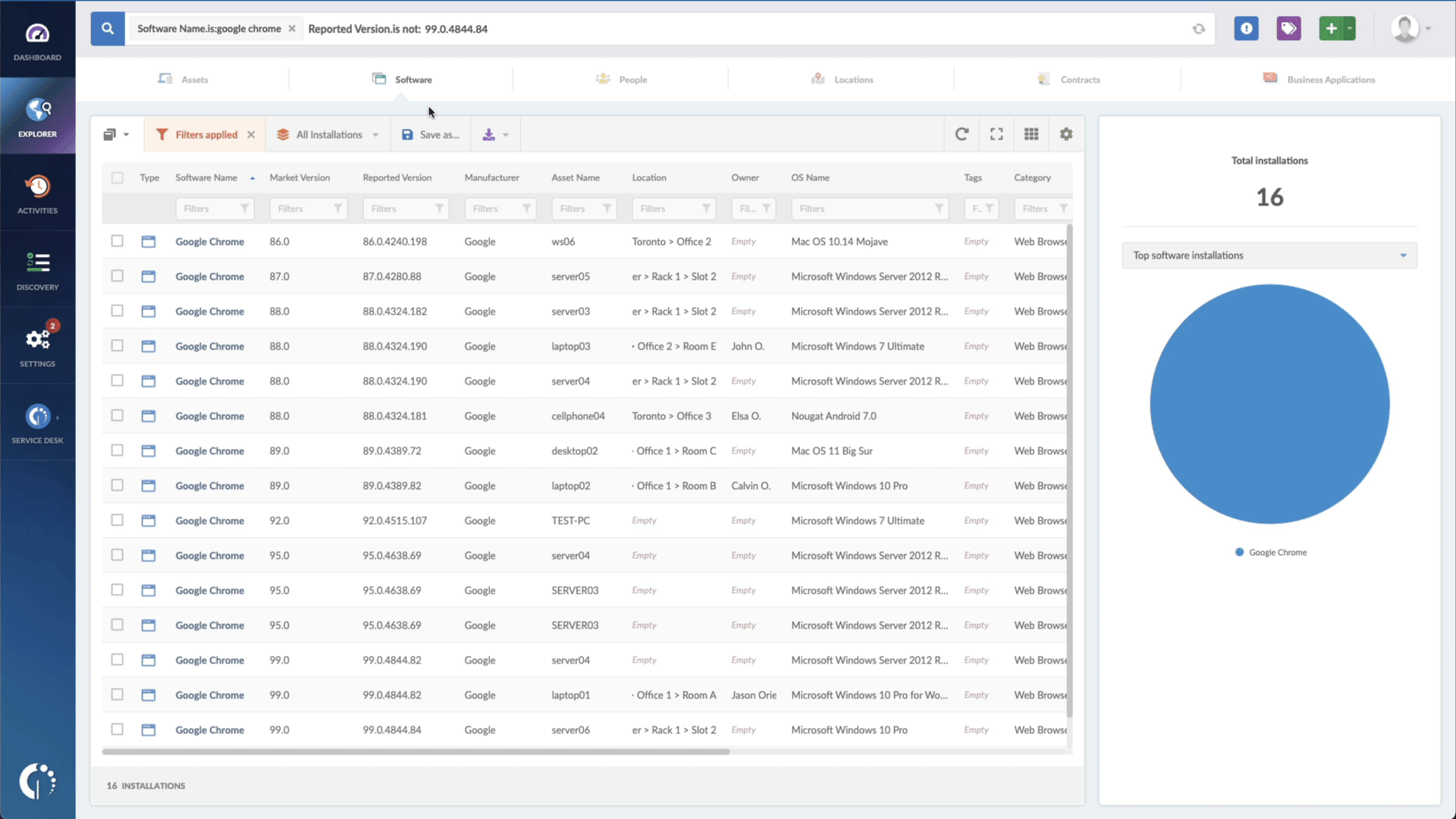
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Citrix’s patched version.
The updated versions of Citrix ADC or Citrix Gateway are the following:
- For ADC and Gateway 13.1 > 13.1-33.52
- For ADC and Gateway 13.0 > 13.0-88.14
- For ADC and Gateway 12.1 > 12.1.65.21
- For ADC 12.1 FIPS > 12.1.55.289
- For ADC 12.1-NDcPP > 12.1.55.289
The bottom line
CVE-2022-27518 is a critical vulnerability that affects Citrix ADC and Gateway, allowing attackers to execute arbitrary code on targeted systems and gain access to sensitive data. The risk associated with this vulnerability is severe, and failure to patch affected systems with the latest software version could result in significant damage and data loss.
Citrix has released a patch to avoid it along with the software version Citrix ADC and Gateway 13.0-58.32. It is highly recommended that all users install the patch immediately to protect their systems from potential attacks.
InvGate Asset Management simplifies patch management by allowing users to identify devices impacted by CVE-2022-27518 swiftly. Request a 30-day free trial today and take control of your Patch Management!