As technology advances, so do cyber-attack tactics, making it crucial to stay ahead in the battle against potential security breaches. CVE-2010-3904 is one such vulnerability that deserves immediate attention. Identified as a significant risk in the Linux kernel's Reliable Datagram Sockets (RDS) protocol implementation, this flaw allows local attackers to gain elevated privileges on susceptible systems.
In this blog post, we’ll delve into the details of CVE-2010-3904, its implications, and the steps you can take to shield your systems from exploitation with InvGate Asset Management.
Learn how to fortify your Vulnerability Management strategy and ensure a robust defense against this security threat!
About CVE-2010-3904
CVE-2010-3904 is a critical local privilege escalation vulnerability in the Linux kernel's Reliable Datagram Sockets (RDS) protocol implementation. The vulnerability is specifically located in the rds_page_copy_user function, where inadequate validation of addresses obtained from user space allows a potential attacker to craft and send a malicious packet to the target system, thereby gaining elevated privileges.
The exploitation process for CVE-2010-3904 is relatively straightforward. An attacker simply needs to transmit the specially-crafted packet to the vulnerable system. Upon receipt, the vulnerability will be exploited, providing the attacker with elevated privileges on the system.
The consequences of not addressing CVE-2010-3904 are severe and could lead to various malicious activities, including installing malware, stealing sensitive data, and disrupting operations.
To protect your system from this vulnerability, you should update the Linux kernel to version 2.6.36 or later.
How to find devices exposed to CVE-2010-3904 with InvGate Asset Management
InvGate Asset Management offers a wide array of robust functionalities that assist in identifying vulnerable devices present in your organization, which may be at risk of CVE-2019-1388 and demand urgent attention. To make the most of these capabilities, follow the provided guidelines:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Linux”.
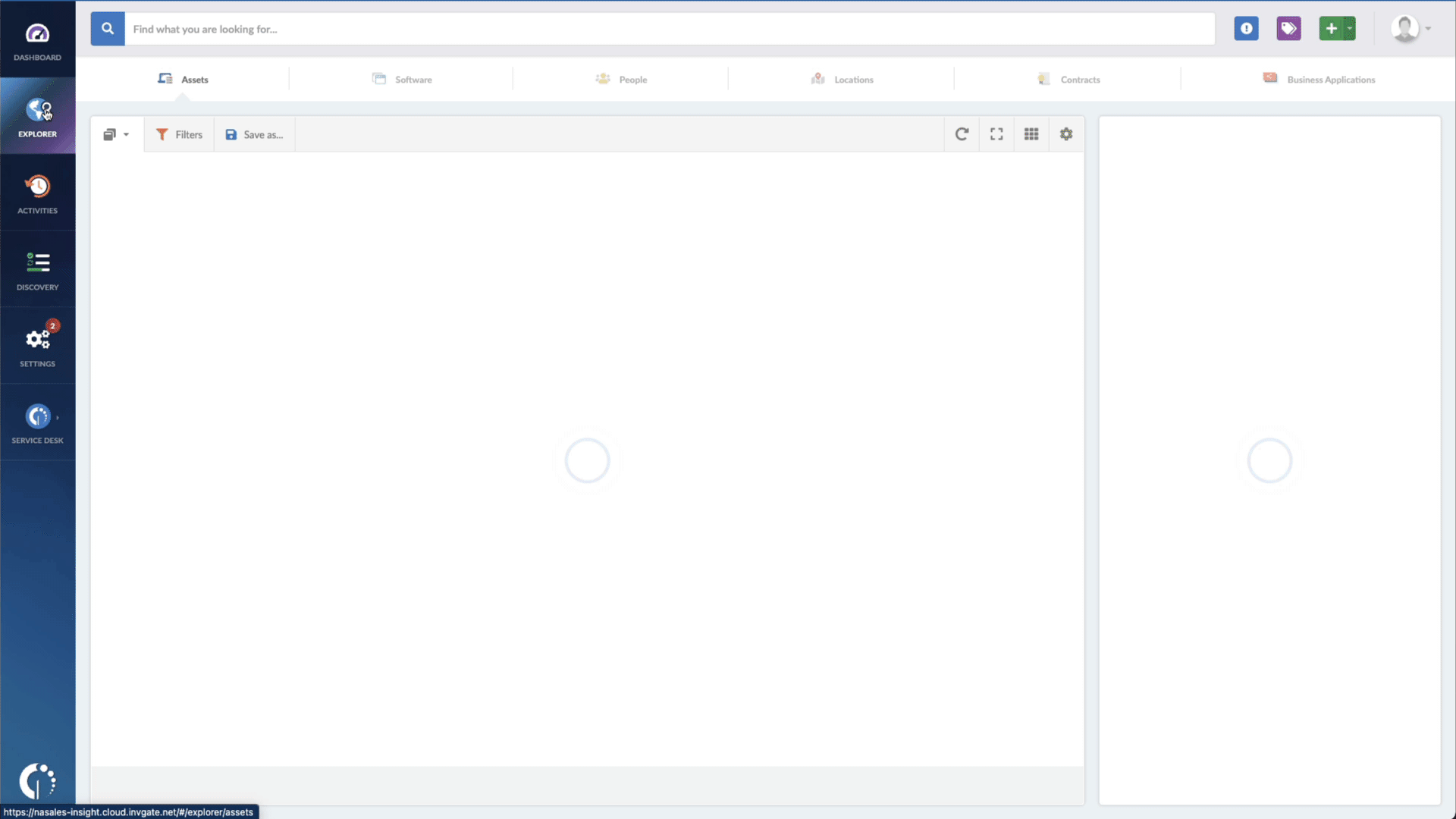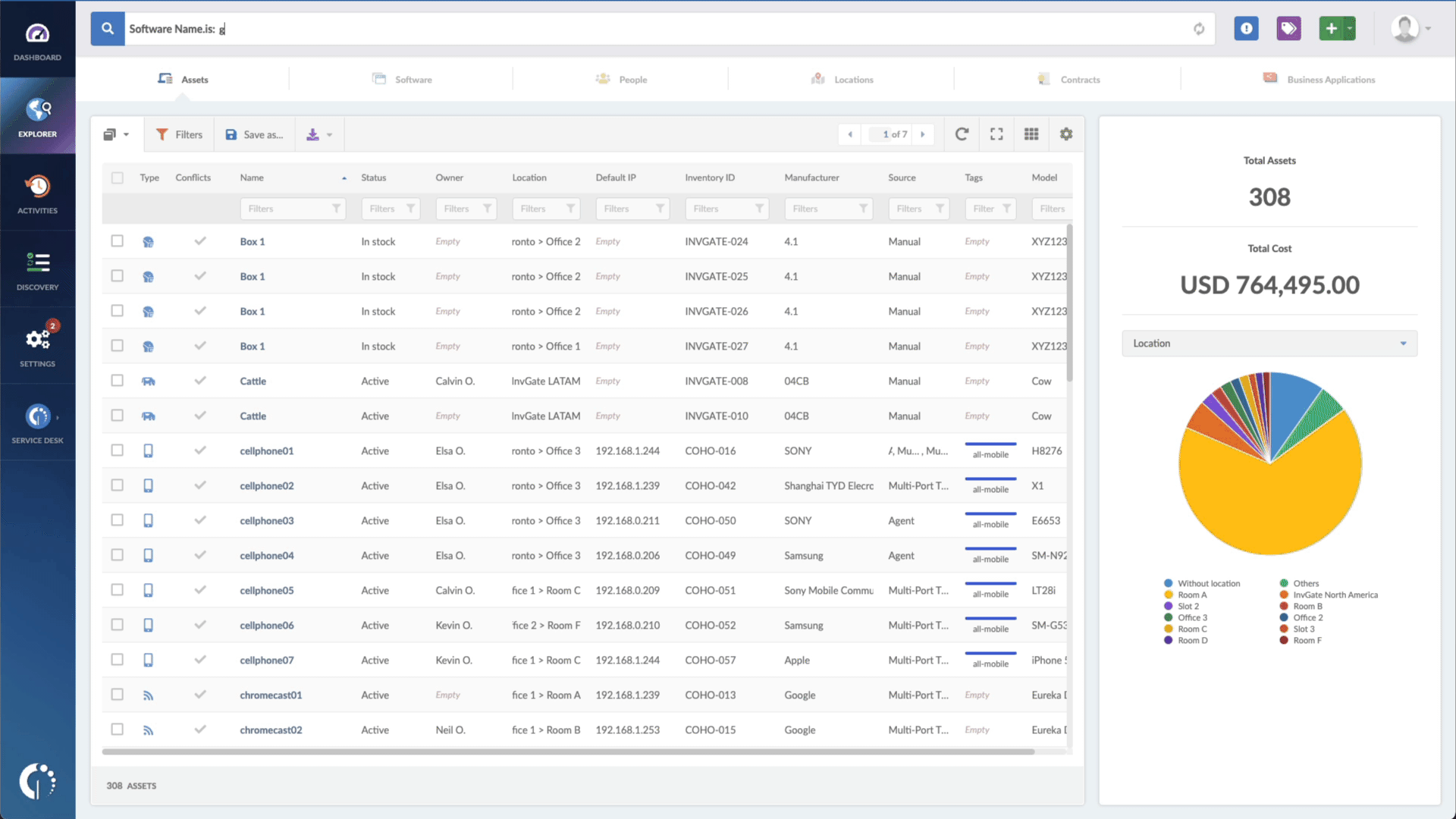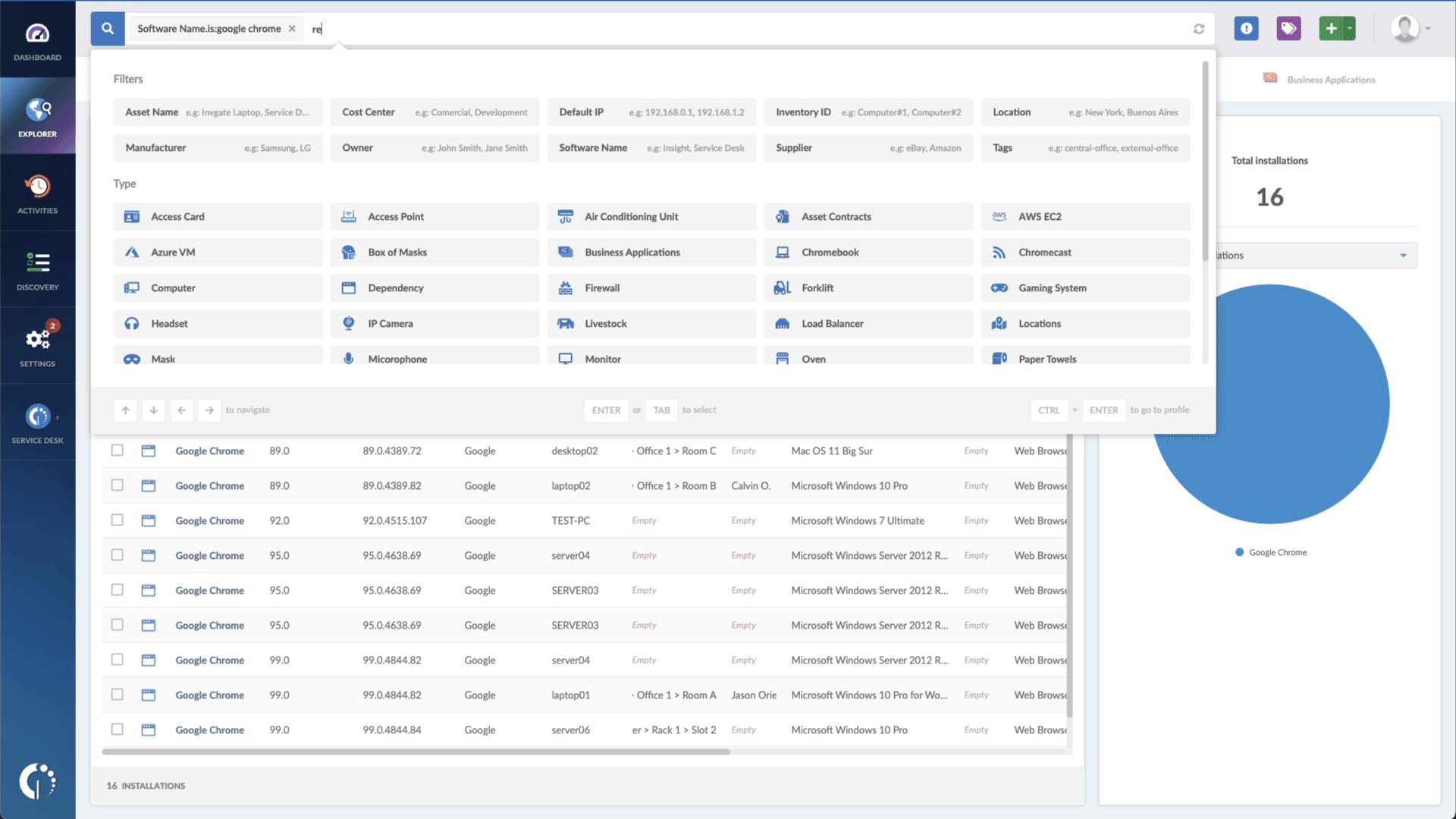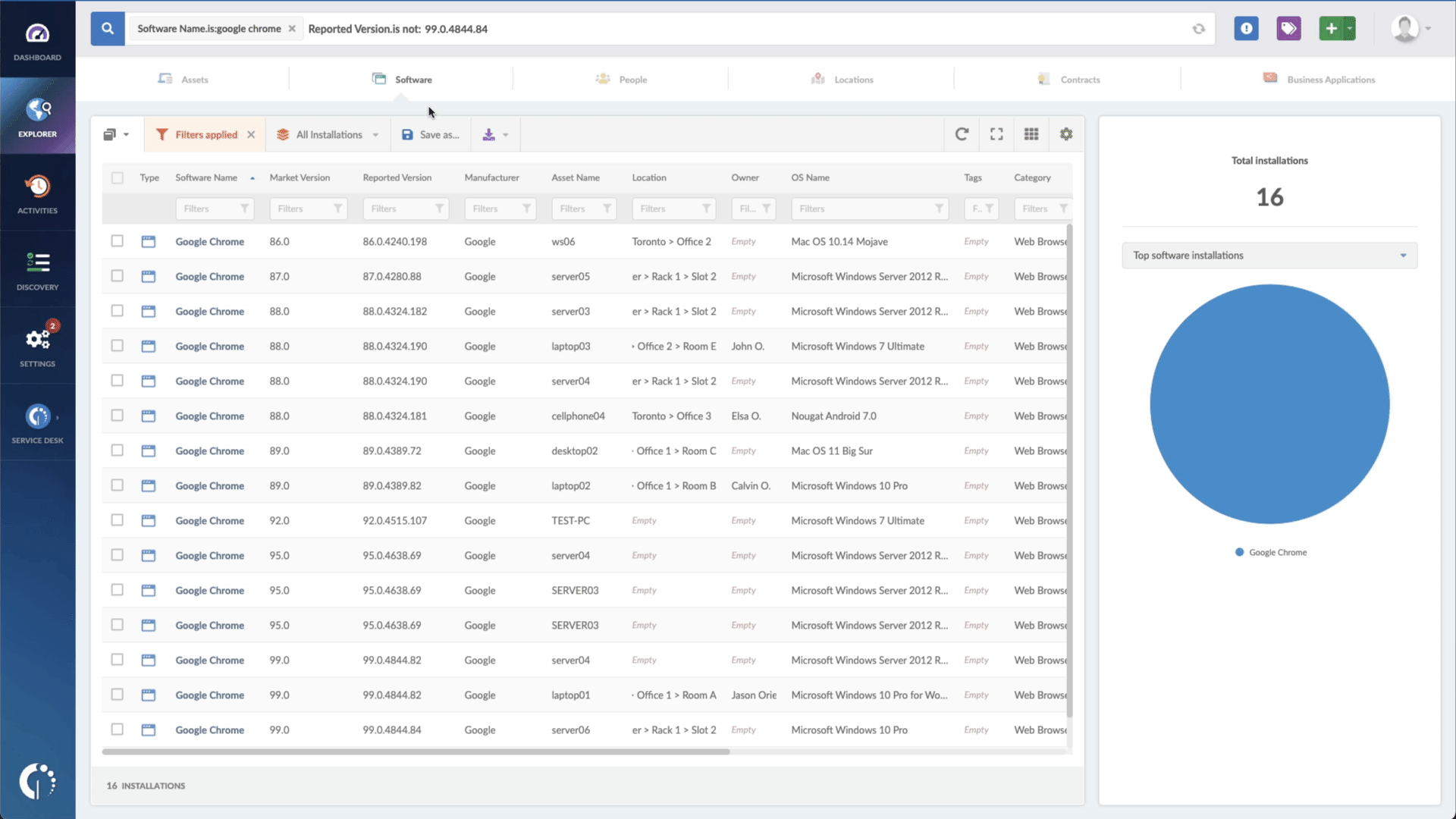
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste the patched version.
That’s it! In a matter of mere seconds, you’ll receive a comprehensive inventory of devices that are vulnerable and require urgent action. This valuable information can be effortlessly downloaded in CSV format, enabling seamless sharing with your team for prompt monitoring and necessary updates.
If you need more insights, watch our informative video that illustrates the step-by-step process of identifying vulnerable devices for patching.
The bottom line
The CVE-2010-3904 vulnerability in the Linux kernel's Reliable Datagram Sockets (RDS) protocol implementation poses a significant risk. Local attackers can exploit the flaw, gaining elevated privileges on vulnerable systems.
InvGate Asset Management offers a powerful solution to address this vulnerability and simplify Patch Management. To experience its full capabilities and protect your network from potential exploits, request our 30-day free trial now and confidently secure your systems.















