Cybersecurity researchers have recently informed that a vulnerability in the latest version of Microsoft Teams allows attackers to inject malware into any organization's network. Though the company has yet to release a patch, there's a change in the configuration you can do to prevent this in the meantime.
The exploit was communicated by Max Corbridge and Tom Ellson from the JUMPSEC's Red Team on June 21. They promptly notified Microsoft about this security breach but didn't receive a satisfactory reply. The company acknowledged the vulnerability but considered it "did not meet the bar for immediate servicing."
Keep reading to fully understand the risk this poses, as well as how you can mitigate it as part of your Vulnerability Management strategy.
Microsoft Teams vulnerability
Even though this is not the only known Microsoft vulnerability in 2023, it seems to be a big one since it allows cybercriminals to introduce malware into any company.
According to the report, the exploit is possible because the current version of Microsoft Teams allows any user with a Microsoft account to access external tenancies.
Now, a tenancy is understood as an organization that uses Microsoft Teams. External tenancies let users from one organization (tenancy) send messages to another. By default, this is enabled and only allows a mere exchange of messages but blocks the possibility of sending files.
And that's precisely what the cybersecurity experts managed to bypass. After a short attempt at changing this security control, they could send files to a target organization by using a "traditional IDOR technique of switching the internal and external recipient ID on the POST request." And this is how an attacker can potentially inject malware.
How to prevent the latest Microsoft Teams bug
While you wait for Microsoft to release a patch and solve the issue, this is what you can do to prevent attackers from injecting malware into your company.
Since the exploit requires external tenancies to be enabled, you can turn it off for now. This has no further complexities for companies that don't use this functionality. If yours requires it, you can only allow communication with the domains that need it.
This can be configured from Microsoft Teams Admin Center >> External Access.
Patching outdated software with InvGate Asset Management
Most cybersecurity breaches are addressed by releasing updates. So, as part of your Patch Management practice, you should periodically review if your organization's software is updated to the latest version.
And you can use InvGate Asset Management to speed up this process. All you need to do is go to the Explorer tab and type "Software name, is:[Name of the software or device]" and "Reported version, is not:[Number of patched version]". And that's it!
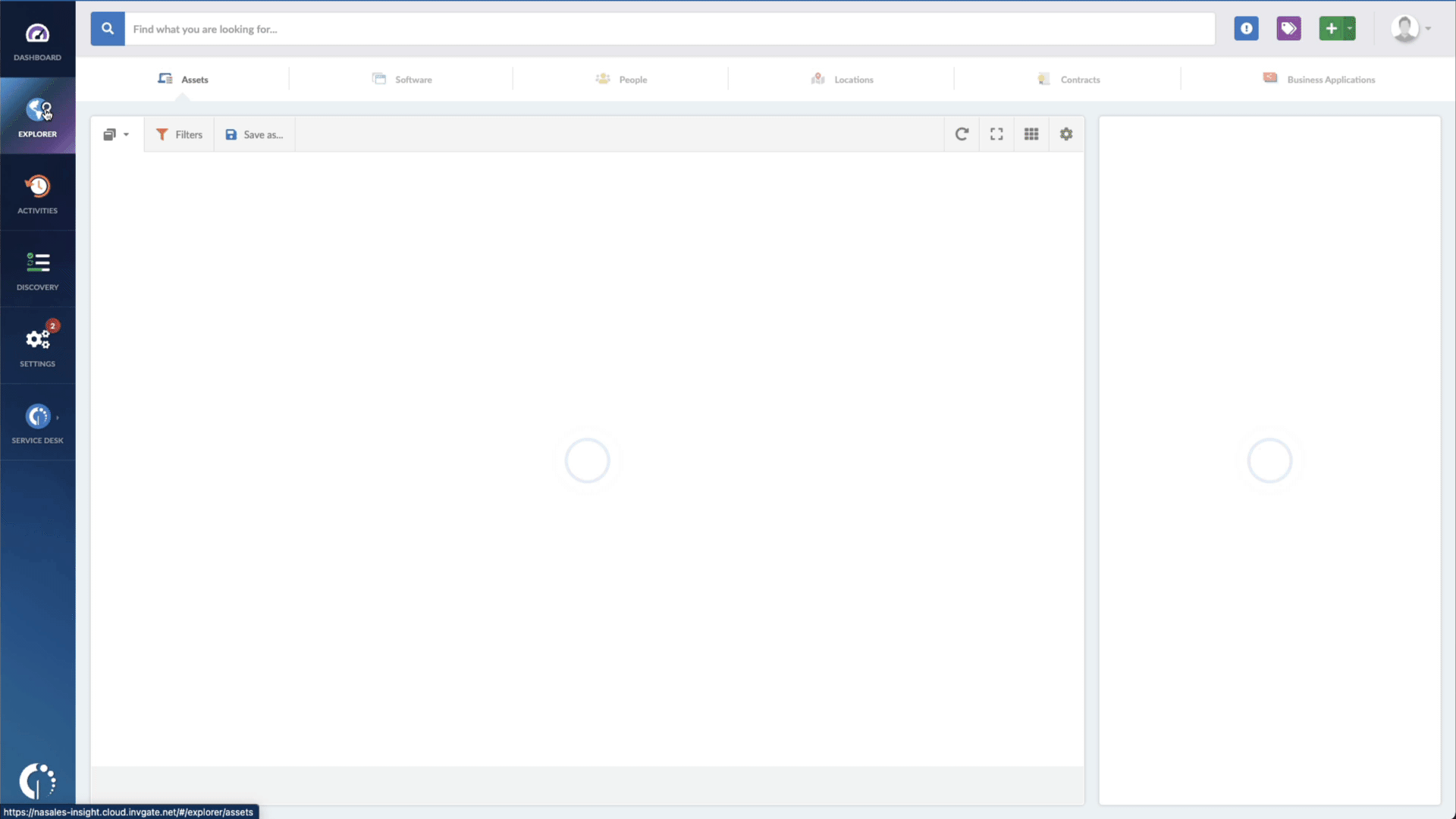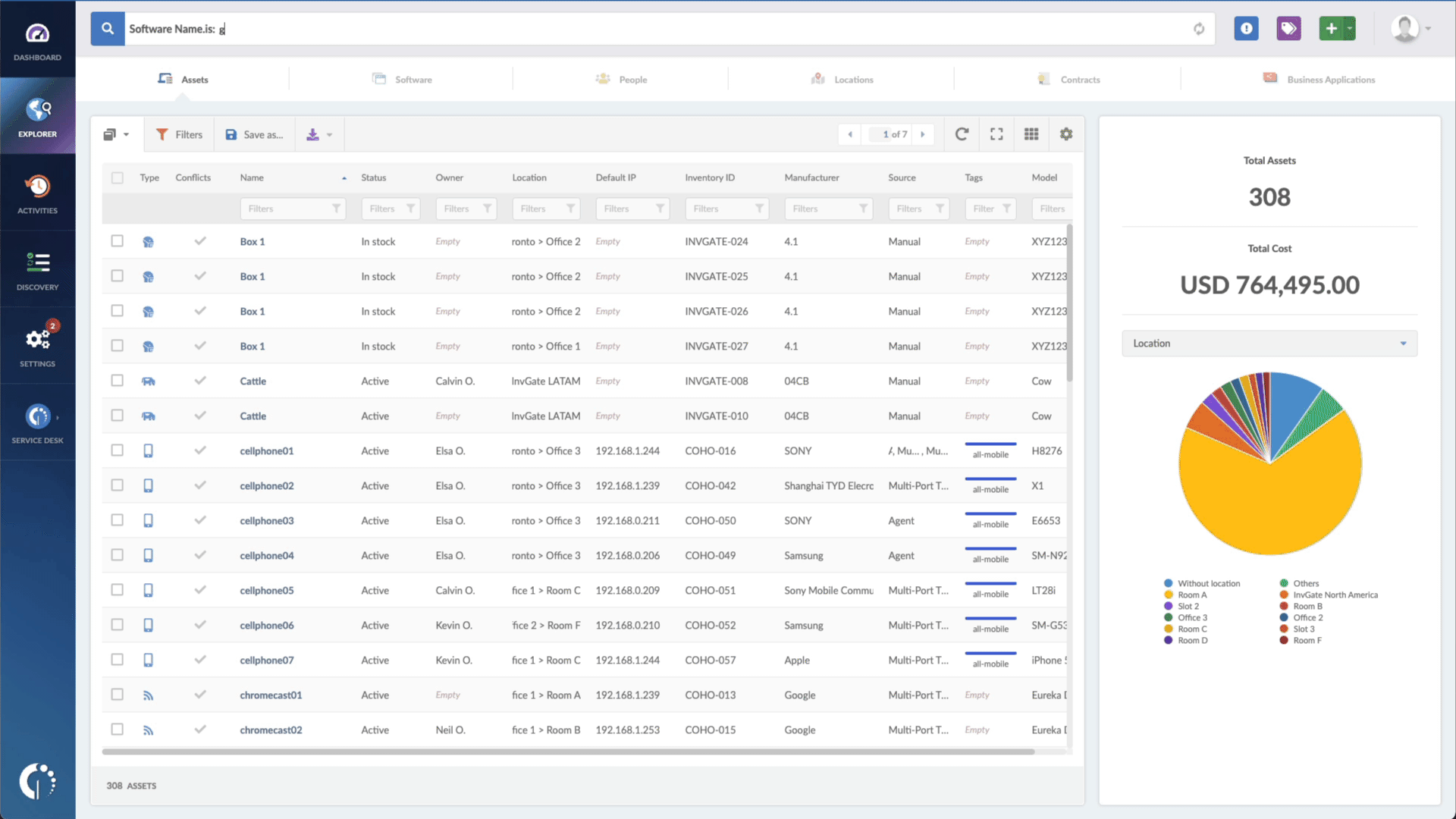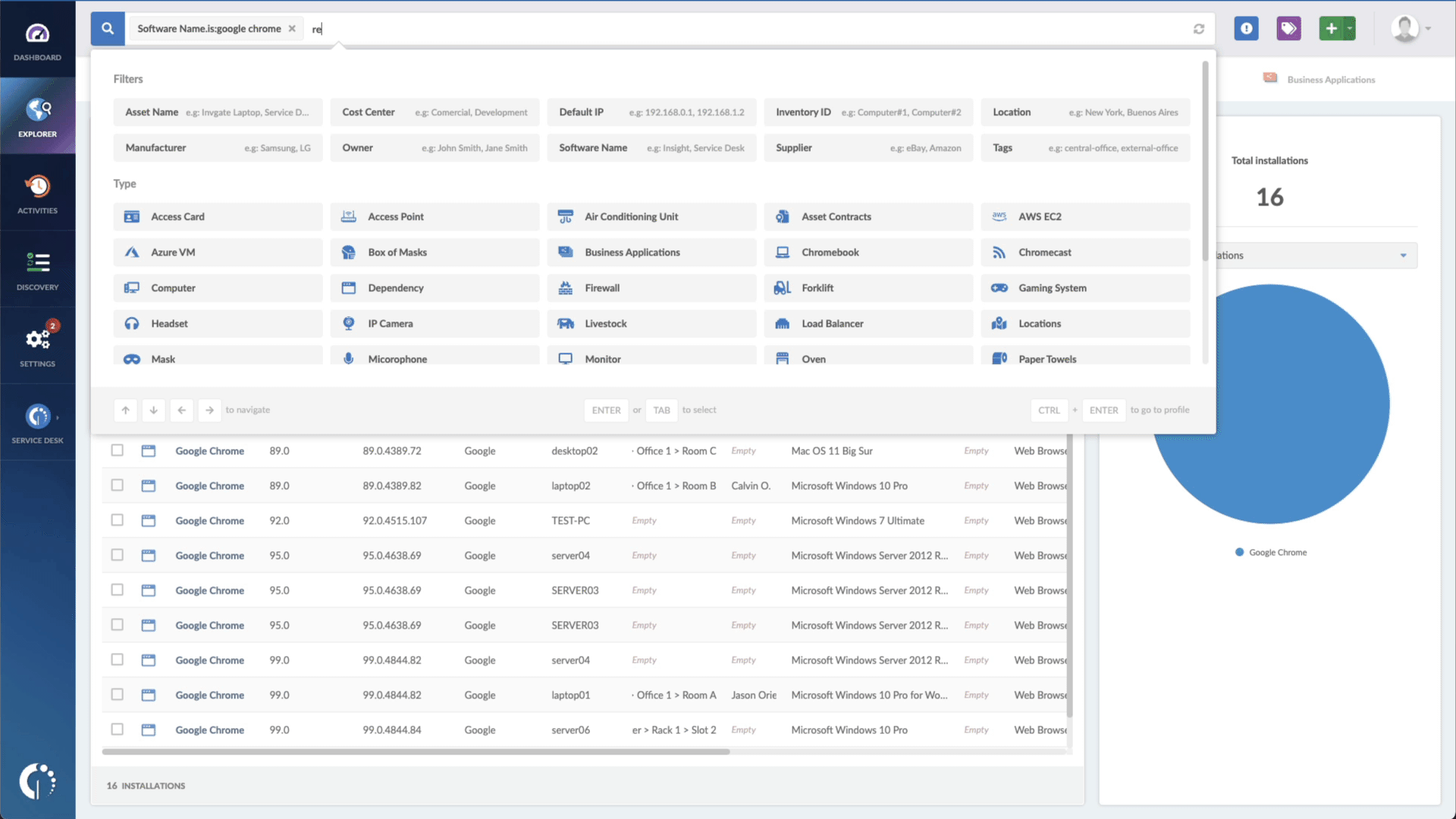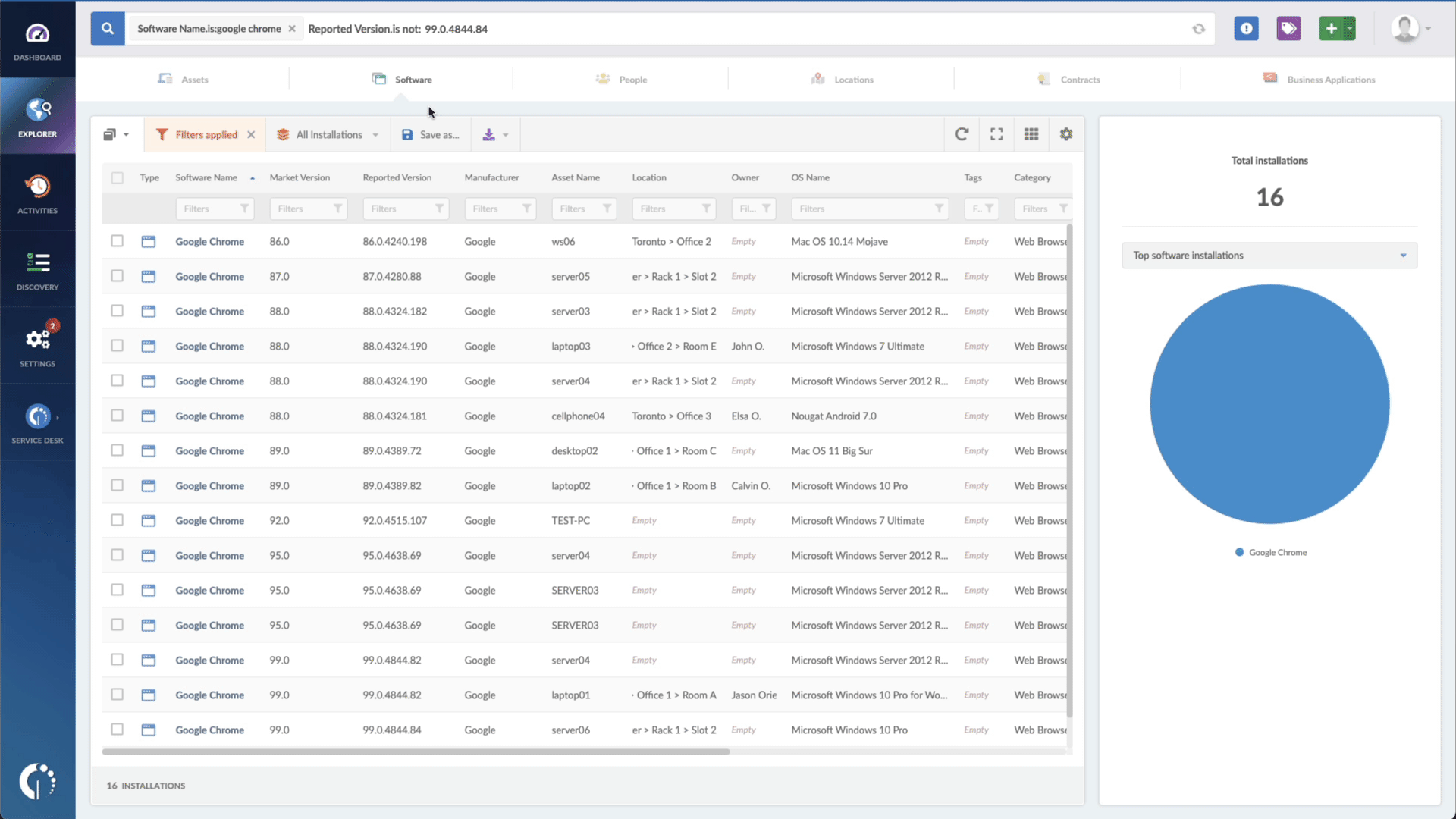
You'll have a list of software that needs attention in seconds. Want to try it out? Request InvGate Asset Management's 30-day free trial or explore the live demo!
















