As cyber threats continue to evolve, staying informed about potential vulnerabilities is critical to protecting your systems from malicious attacks. On January 10th, 2023, Microsoft announced a critical security vulnerability in the Windows Ancillary Function Driver for WinSock, known as CVE-2023-21768.
This vulnerability could allow attackers to elevate their privileges and gain unauthorized access to sensitive data, putting users' cybersecurity at risk. In this article, we'll provide a comprehensive overview of the CVE-2023-21768 vulnerability, including its associated risks, and how to identify and patch devices that may be exposed to this threat.
Don't wait until it's too late. Read on to learn more about CVE-2023-21768 and how to safeguard your devices from this critical vulnerability.
About CVE-2023-21768
CVE-2023-21768 is a critical vulnerability found in the Ancillary Function Driver (AFD) of the Windows Operating System. AFD is responsible for supporting WinSock, a programming interface that allows applications to communicate over the internet using TCP/IP protocols.
The CVE-2023-21768 vulnerability has a CVSS score of 7.8, which means it is rated as high severity. It affects all supported versions of Windows, including Windows 10 and Windows Server 2019.
The exploit occurs due to a flaw in how the AFD driver handles input/output control (IOCTL) requests, allowing attackers to elevate their privileges on a targeted system. An attacker can exploit this vulnerability by sending a specially crafted IOCTL request to the AFD driver, allowing them to execute arbitrary code with elevated privileges.
If left unpatched, this vulnerability can allow attackers to take complete control of a system, steal sensitive data, and install malicious software. An attacker who successfully exploits this vulnerability can take over the targeted system and use it as a platform to launch further attacks against other systems on the network.
Microsoft has released a security update to fix this vulnerability, and users are strongly advised to update their systems as soon as possible.
How to find devices exposed to CVE-2023-21768
If you are concerned about the CVE-2023-21768 vulnerability and want to ensure that your system is not vulnerable to this threat, you can count on InvGate Asset Management.
To use InvGate Asset Management to find devices that are exposed to the CVE-2023-21768 vulnerability, follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
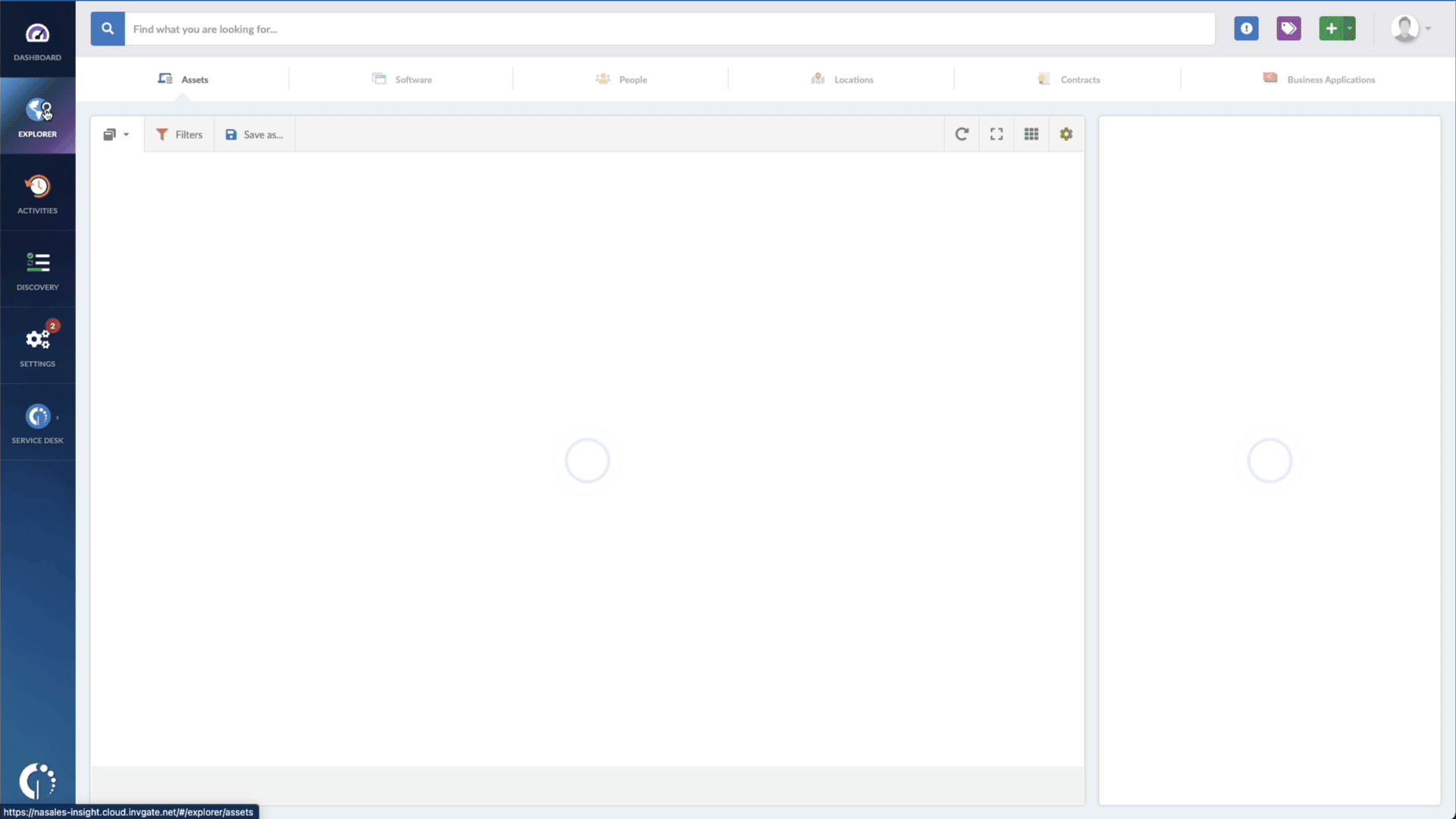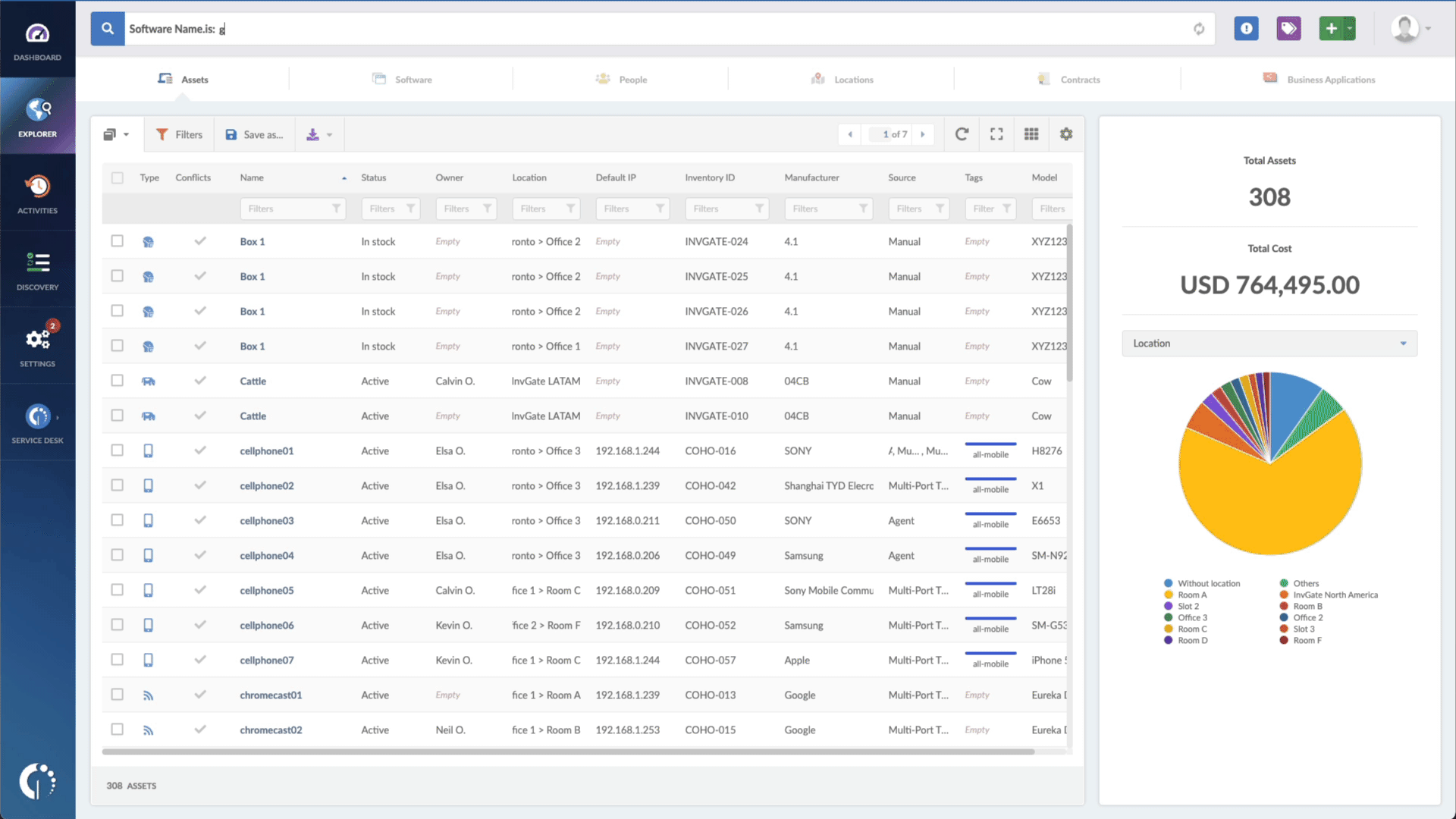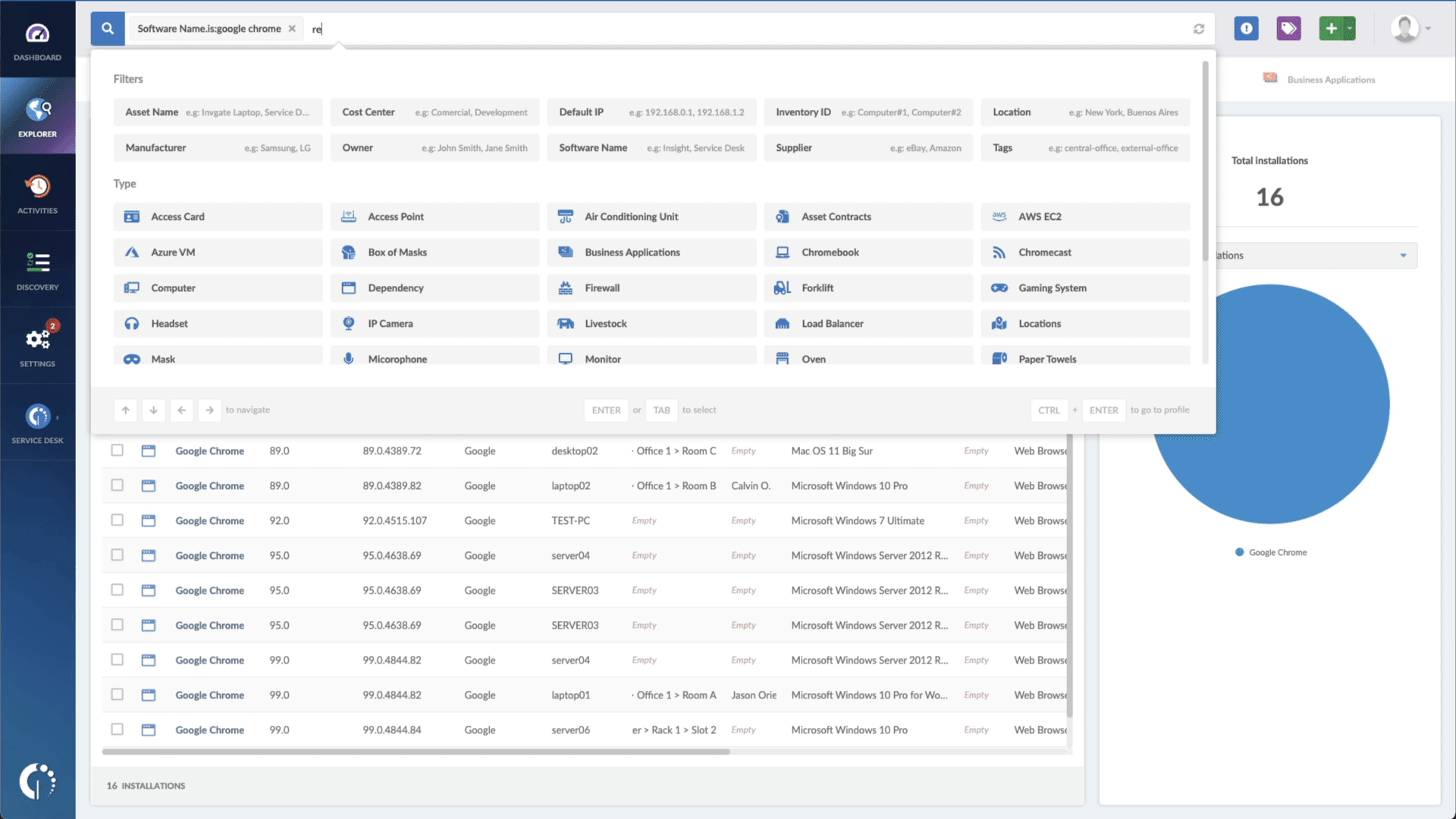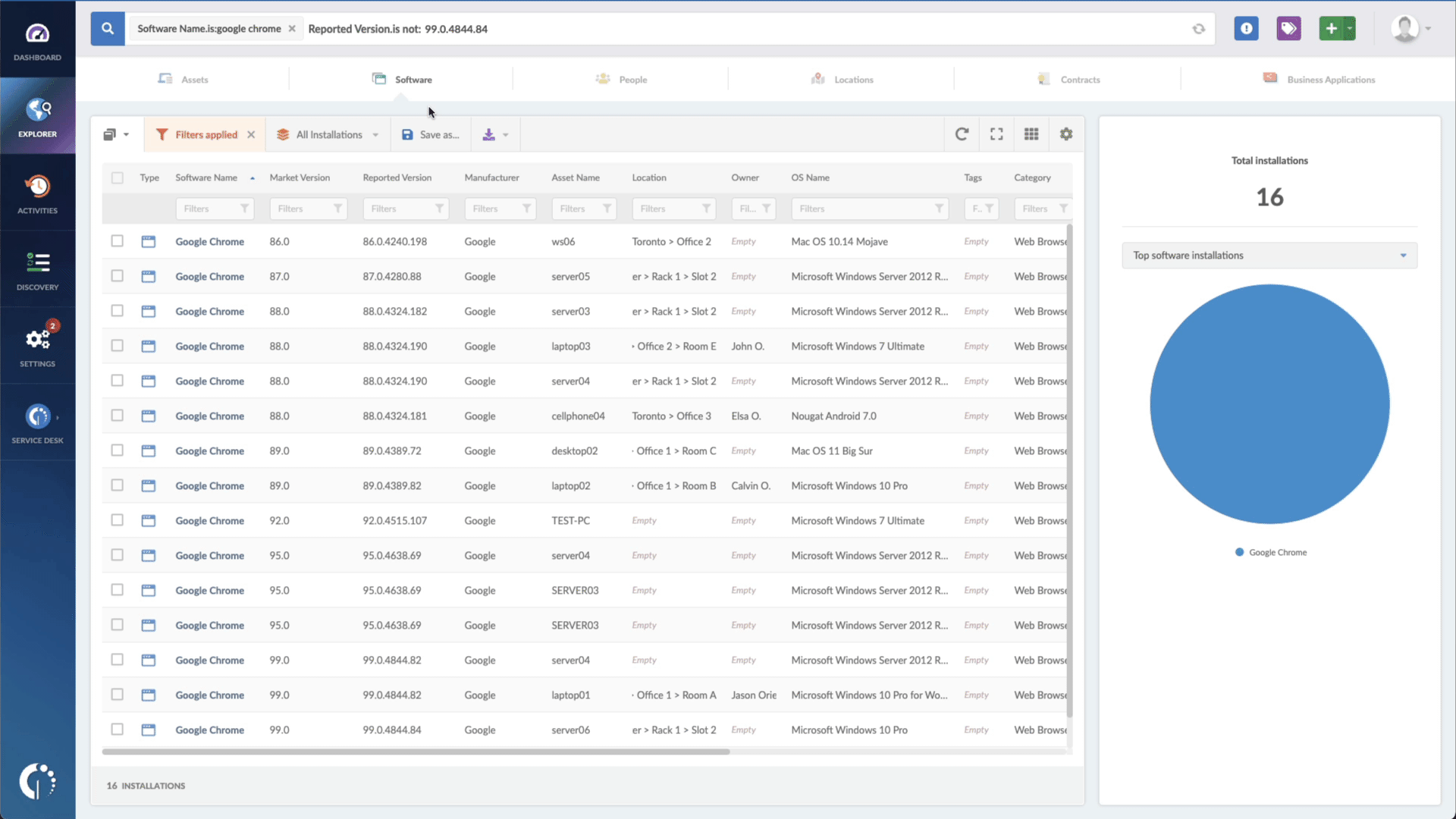
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows Server 2022, it's KB5022291).
The bottom line
The CVE-2023-21768 vulnerability in the Windows Ancillary Function Driver for WinSock is a critical security issue allowing attackers to elevate their privileges and take control of vulnerable systems. Microsoft has released a security update to fix it, and Windows users must update their systems as soon as possible.
InvGate Asset Management can simplify Patch Management by providing an easy way to identify vulnerable devices in your network and track the status of the latest security updates.
To ensure that your systems are up-to-date with the latest security patches, sign up for InvGate Asset Management's 30-day free trial today. You can gain visibility into your network and easily search for devices vulnerable to this and other similar vulnerabilities. Take proactive steps to protect your systems and safeguard your business today!