In February 2023, security researchers discovered a critical vulnerability in Microsoft Word that could allow attackers to execute code on a victim's computer remotely. This vulnerability, identified as CVE-2023-21716, poses a significant risk to individuals and organizations who use Microsoft Word, potentially leading to serious consequences.
As soon as the vulnerability was reported, Microsoft issued a security update to address the issue. In a statement released on their official website, Microsoft urged all users of Word to install the latest security updates to protect their systems.
In this blog post, we’ll provide an in-depth overview of the CVE-2023-21716 vulnerability, including what it is, how it works, its risks, and how to use InvGate Asset Management to simplify Patch Management.
If you are concerned about the security of your organization's network, read on to learn more about how you can safeguard your systems from this critical security threat.
About CVE-2023-21716
CVE-2023-21716 is a remote code execution vulnerability discovered in Microsoft Office. It is rated as a critical severity and has been assigned a CVSS score of 9.8.
The vulnerability exists in how wwlib library handles certain types of RTF commands. When an RTF document is opened, wwlib parses the document and executes the commands that it contains. If an attacker can craft a malicious RTF document that contains a specially crafted command, they can exploit the vulnerability to execute arbitrary code on the victim's computer.
How does CVE-2023-21716 work?
An attacker can exploit the CVE-2023-21716 vulnerability to execute arbitrary code on a victim's computer by tricking them into opening a malicious RTF document. The attacker could deliver this file as an email attachment or by other means.
When the victim opens the malicious RTF document, wwlib will parse the document and execute the commands that it contains. If the document contains a specially crafted command that triggers the vulnerability, the attacker can execute arbitrary code on the victim's computer.
How to protect yourself from CVE-2023-21716
Microsoft has released a patch for this vulnerability, and users are advised to install the patch as soon as possible.
In addition to installing the patch, users can also protect themselves from this vulnerability by following these best practices:
- Do not open attachments from unknown senders.
- Scan all attachments with antivirus software before opening them.
- Keep your software up to date with the latest security patches.
- Use a firewall to protect your computer from unauthorized access.
- Be careful about what websites you visit and what links you click on.
- By following these best practices, you can help to protect yourself from this and other vulnerabilities.
How to find devices exposed to CVE-2023-21716
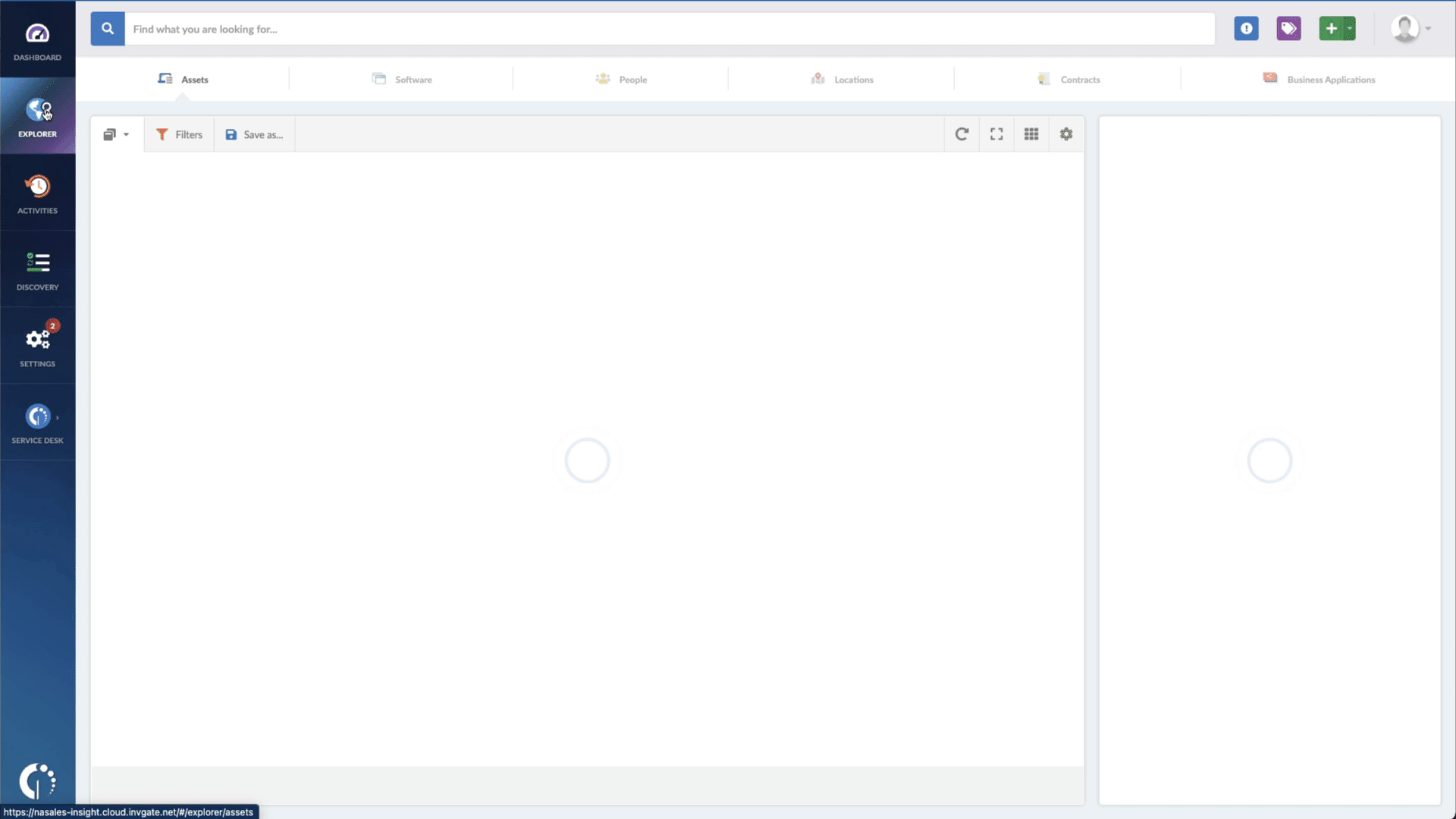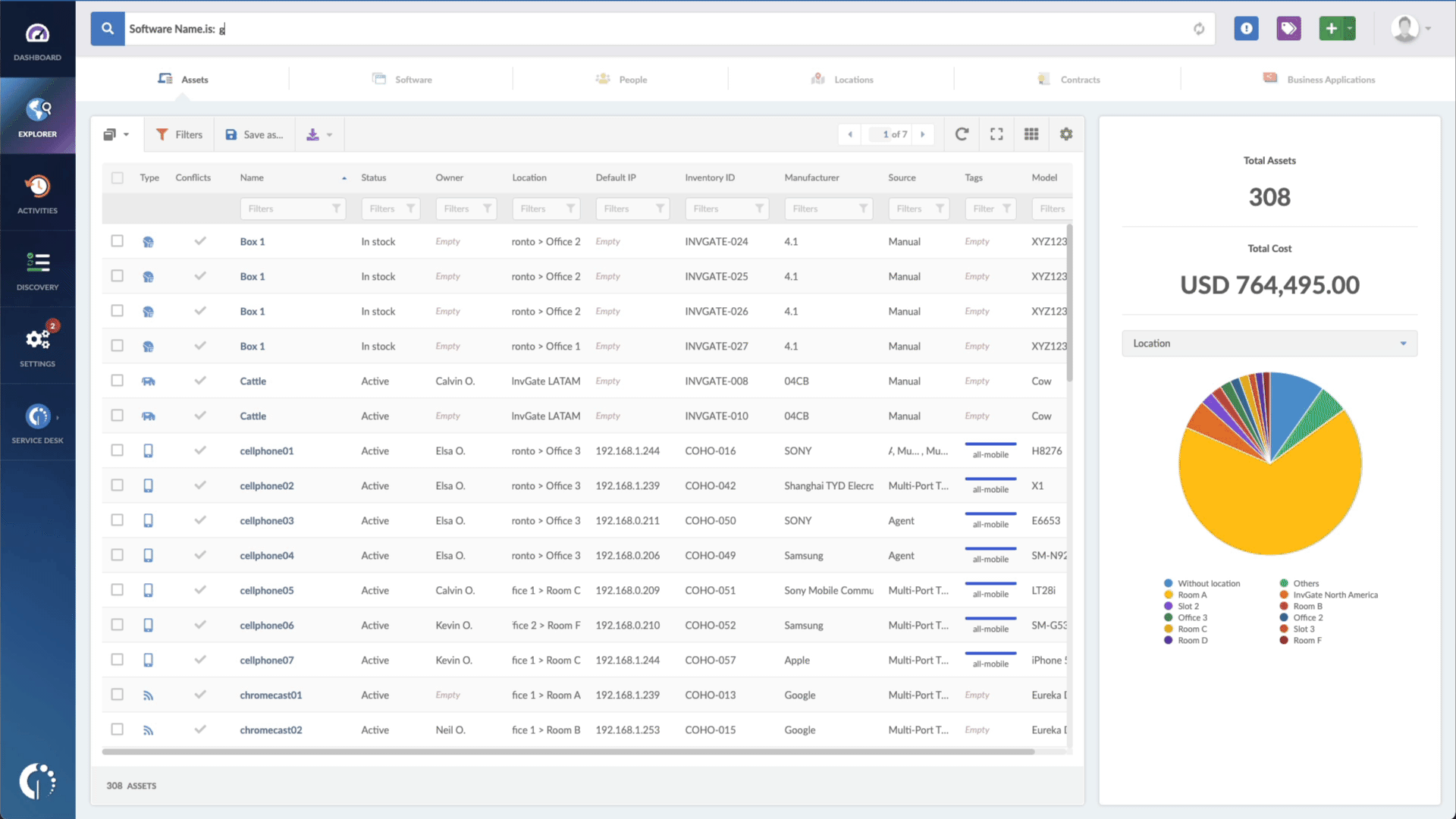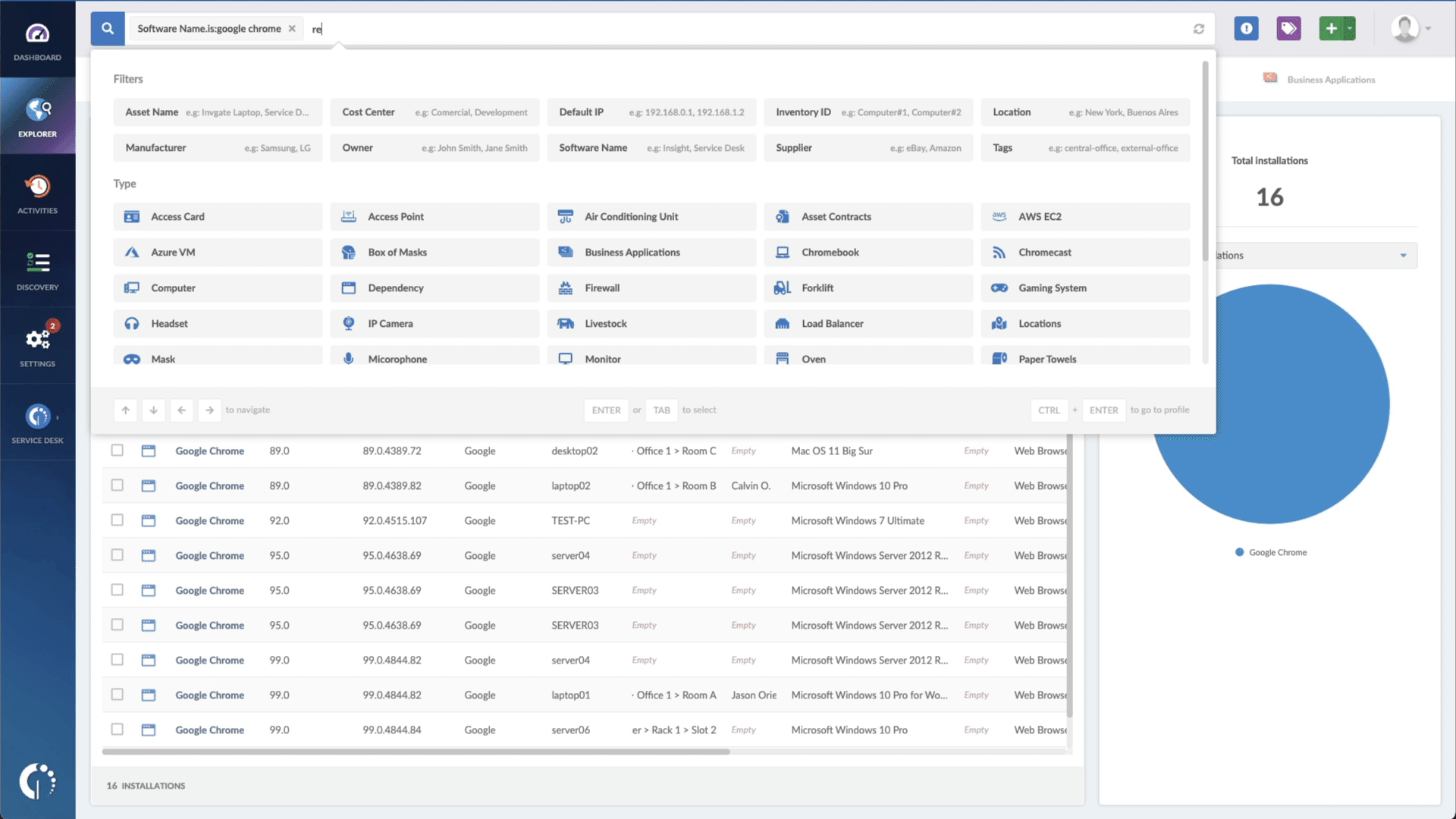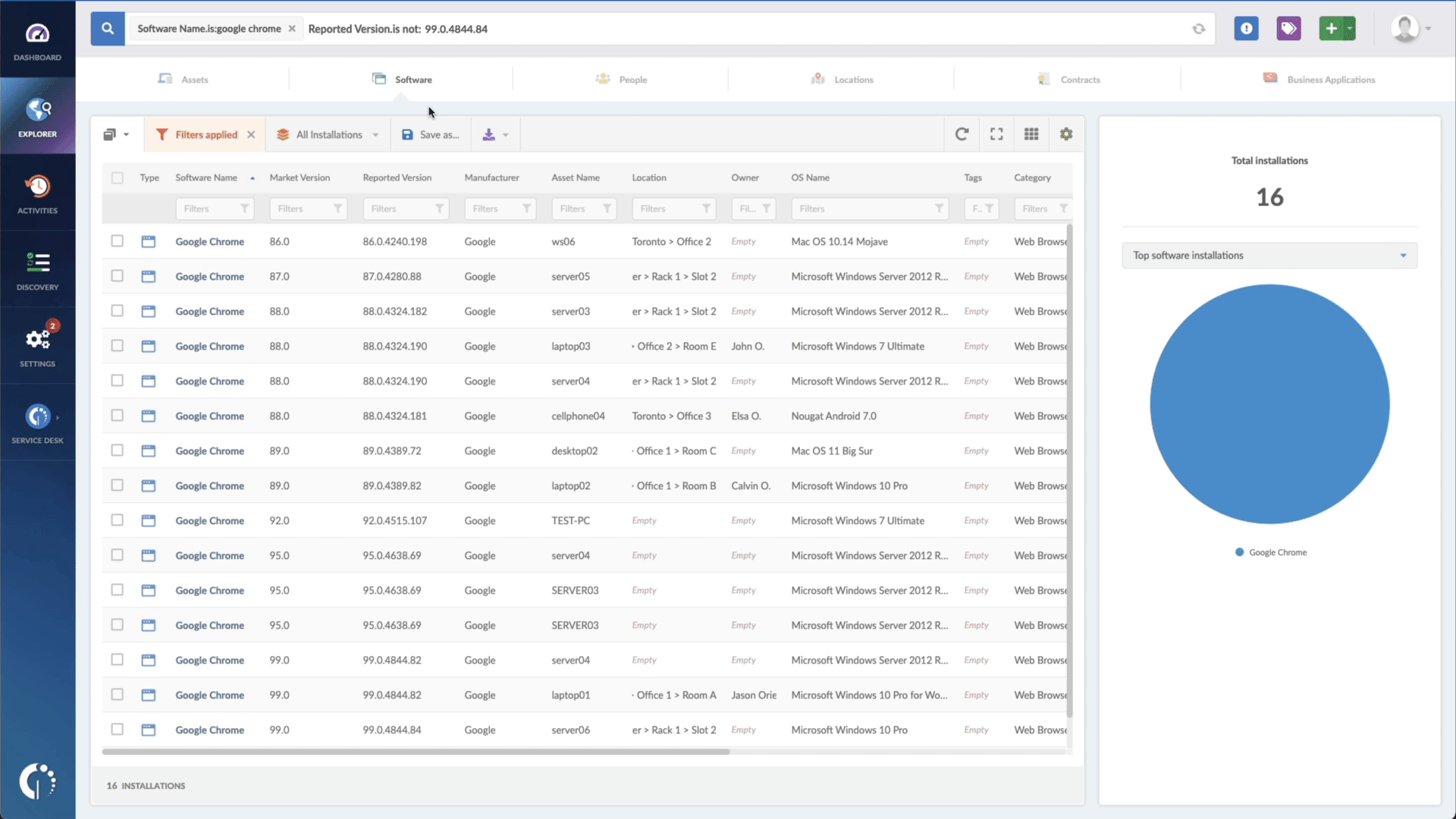
You can quickly detect devices that are impacted by the CVE-2023-21716 vulnerability by using InvGate Asset Management. Here are the steps to follow:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Microsoft Word” to filter all the devices with this software.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your version, you’ll find the security update number on Microsoft’s webpage).
The bottom line
The CVE-2023-21716 vulnerability in Microsoft Word is a critical security issue that poses a significant risk to individuals and organizations. If left unpatched, this vulnerability can allow attackers to take control of affected devices and potentially compromise sensitive data.
To protect against this vulnerability, users must update their Microsoft Word software to the latest version, which includes the necessary security patch.
InvGate Asset Management is a comprehensive Asset Management tool that simplifies Patch Management by providing a centralized platform to monitor and update software across an organization's entire network. With InvGate Asset Management, users can quickly identify devices that CVE-2023-21716 impacts and take immediate action to patch these devices.
If you are concerned about the security of your network, take advantage of InvGate Asset Management's capabilities and request a 30-day free trial to experience the benefits firsthand. Don't wait until it’s too late- take action today to protect your organization from this critical security threat.