Cybersecurity threats are becoming more sophisticated and frequent, making it imperative for businesses and individuals to stay vigilant and keep their systems up-to-date. On January 10, 2023, Microsoft informed users about a critical vulnerability in Windows ALPC (Advanced Local Procedure Call) service, known as CVE-2023-21674.
This vulnerability can allow attackers to elevate privileges and gain unauthorized access to sensitive data, making it a significant threat to users' cybersecurity.
In this article, we’ll provide an in-depth overview of CVE-2023-21674, including what it is, its associated risks, how to identify devices exposed to this vulnerability, and how to patch them to ensure your systems are secure.
If you're concerned about your device's security and want to learn more about CVE-2023-21674, keep reading!
About CVE-2023-21674
CVE-2023-21674 is a vulnerability in the Advanced Local Procedure Call (ALPC) interface of Microsoft Windows operating systems. The ALPC interface is a component that enables inter-process communication on Windows systems.
The CVE-2023-21674 exploit is classified as an elevation of privilege vulnerability. It allows attackers with limited privileges to escalate them to gain higher-level access. In the case of CVE-2023-21674, an attacker could use the vulnerability to gain system-level access, allowing them to install software, modify data, and perform other malicious activities.
To exploit the CVE-2023-21674 vulnerability, an attacker would need access to a vulnerable system through a network connection or by gaining physical access to the device. Once access is gained, the attacker could execute a specially crafted application or script to exploit the vulnerability and gain elevated privileges.
Microsoft has released a security update to address the CVE-2023-21674 vulnerability in affected Windows operating systems. The patch should immediately be applied to all affected systems to prevent potential attacks. The latest version of Windows with the patch is Windows 10 version 21H1 (May 2021 Update), Windows 10 version 20H2 (October 2020 Update), and Windows Server version 20H2 (October 2020 Update).
How to find devices exposed to CVE-2023-21674
With InvGate Asset Management, you can quickly identify devices exposed to the CVE-2023-21674 vulnerability. Users can create a list of devices that need to be updated with a few clicks, allowing system administrators and security professionals to take appropriate action to remediate the issue.
To use InvGate Asset Management to find devices that are exposed to the CVE-2023-21674 vulnerability, follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is: Windows” to filter all Windows devices.
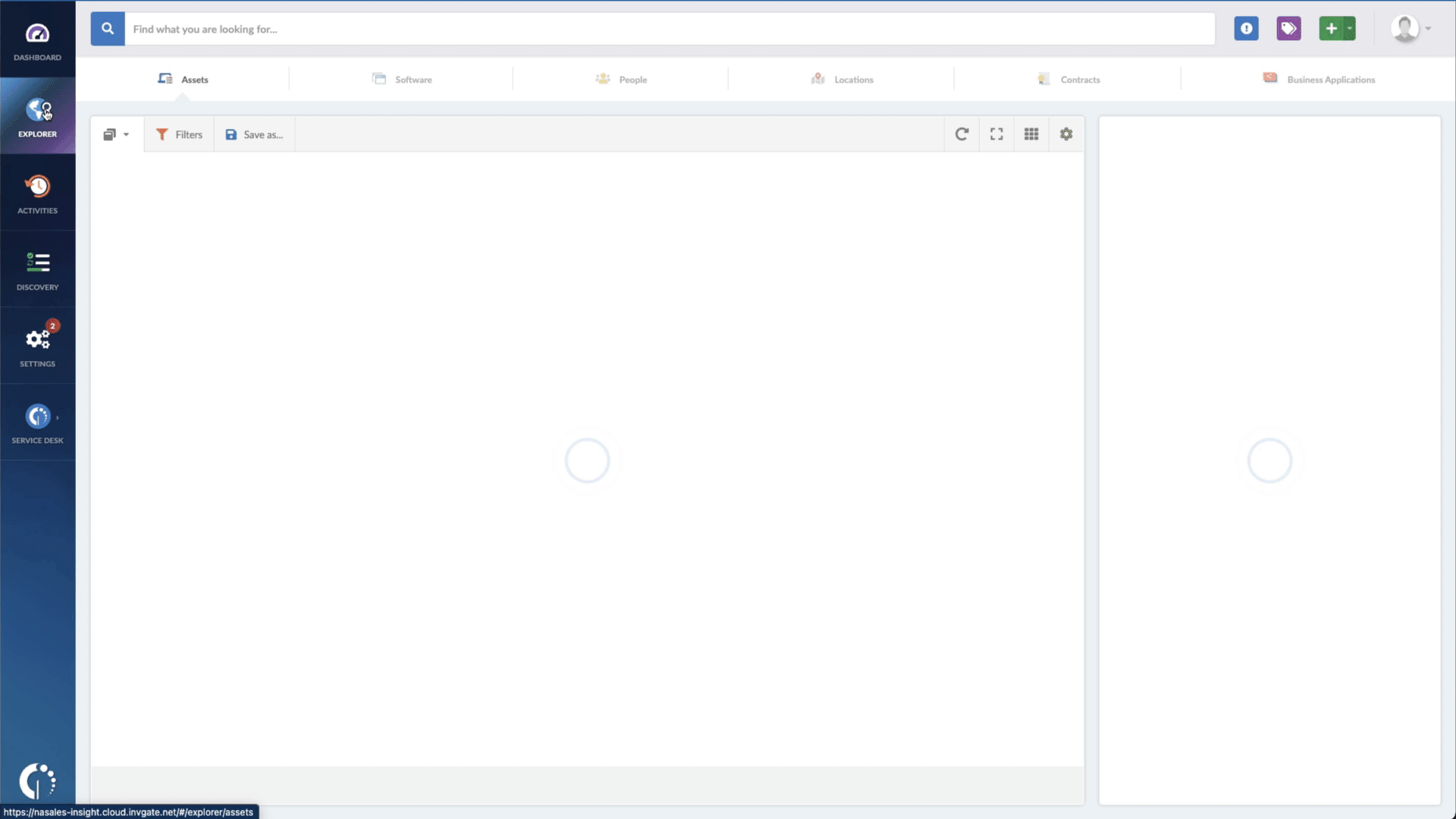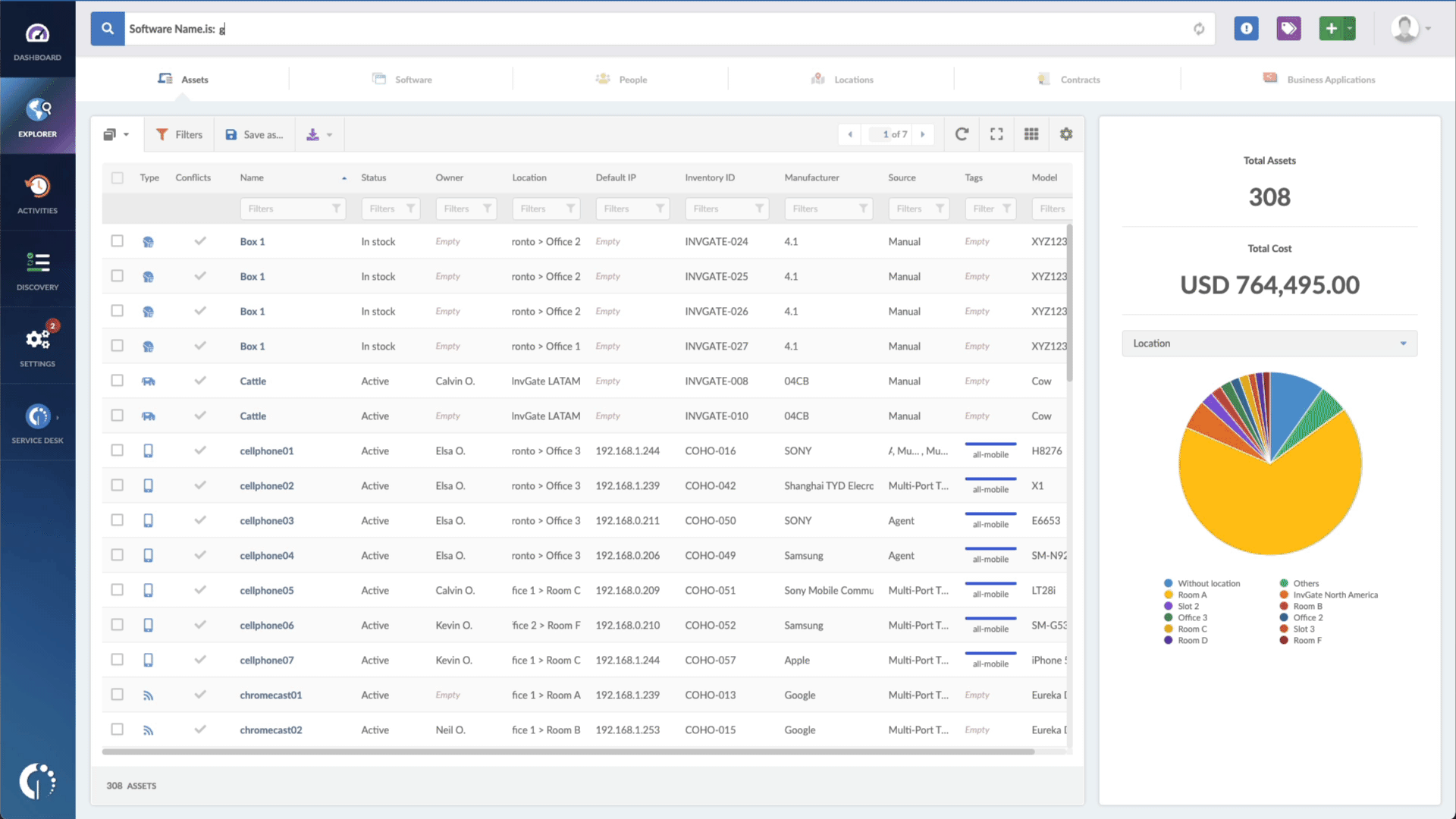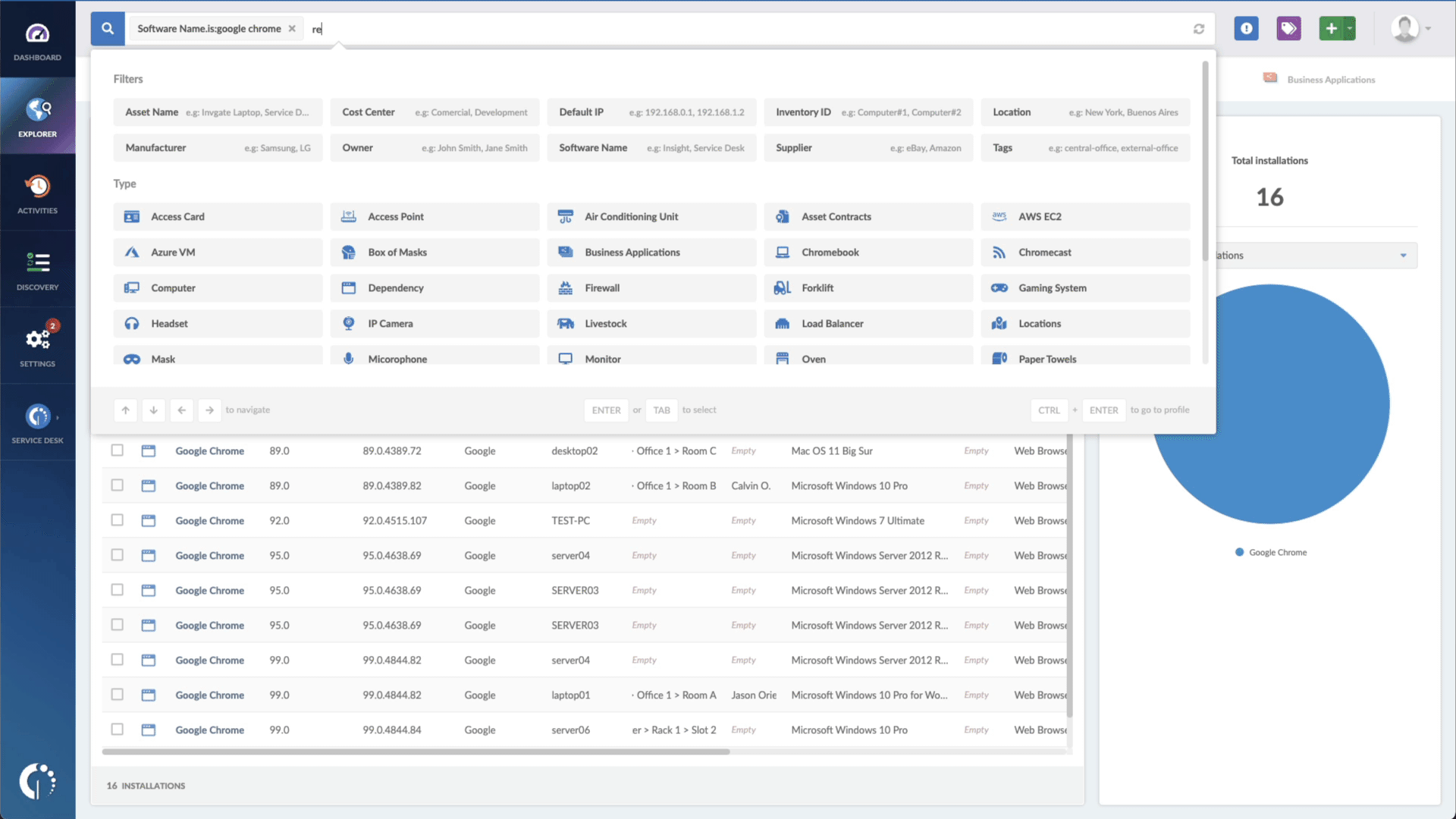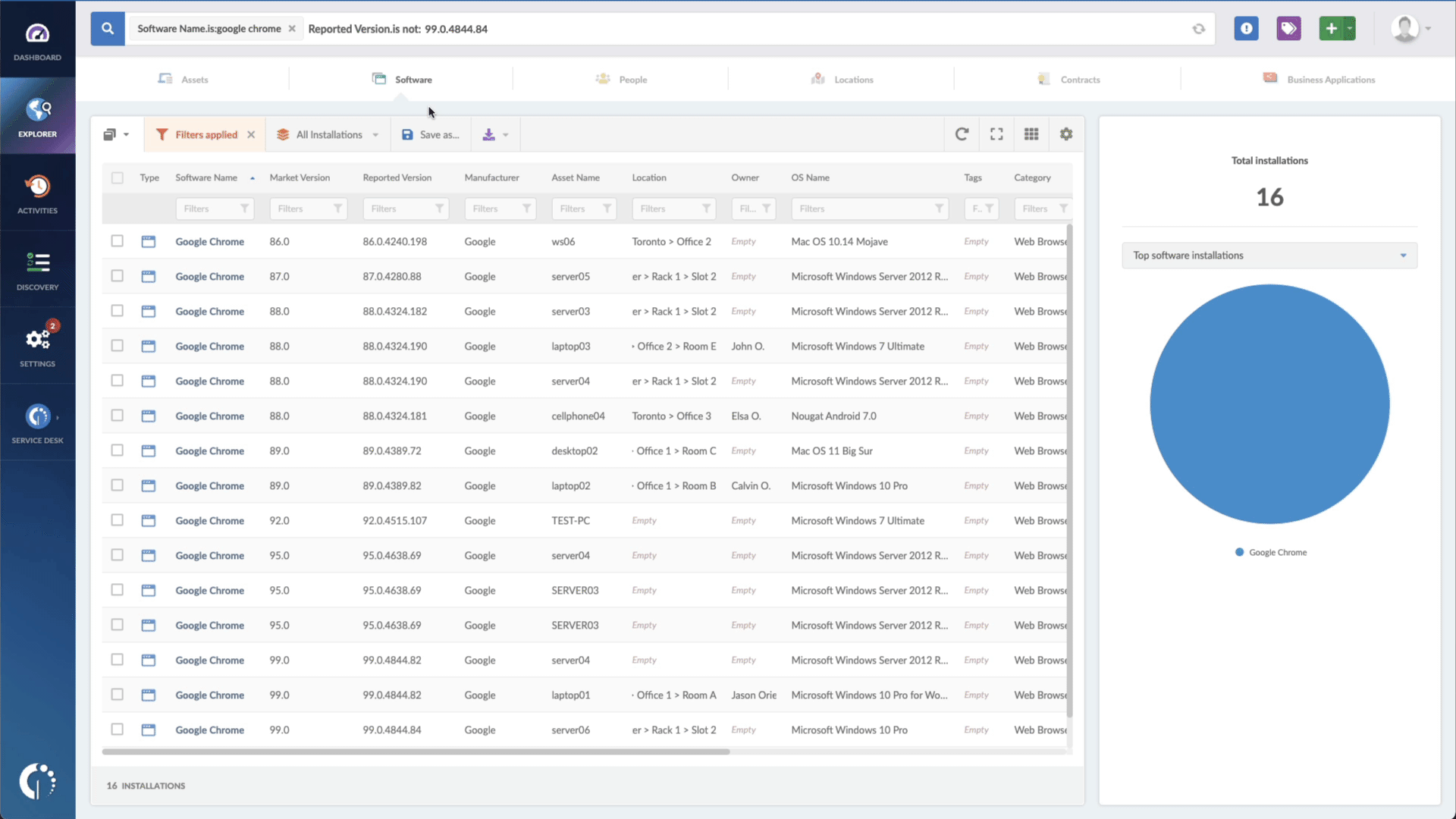
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 10 for 32-bit Systems, it's KB5022297).
That’s all! Now you have a list of all the Windows devices vulnerable to CVE-2023-21674. You can then export this list in CSV format and give it to one of your agents to patch or create a ticket so they can be manually updated.
The bottom line
CVE-2023-21674 vulnerability poses a severe risk to Windows users and their data, as it allows attackers to elevate privileges and potentially gain control over affected systems. To mitigate this risk, Microsoft has released a patch that addresses the vulnerability by correcting how the Windows ALPC service handles objects in memory.
To ensure that all your devices are protected against this vulnerability, it's essential to identify which ones need updating and patch them immediately. InvGate Asset Management can simplify this process by providing an easy-to-use Patch Management solution that allows you to quickly identify all devices that require updates and ensure that they are patched promptly.
Don't wait for CVE-2023-21674 vulnerability to catch you off guard! Try InvGate Asset Management now and take advantage of its powerful capabilities to simplify Patch Management and keep your devices secure. Sign up for our 30-day free trial and see how easy it can be to stay on top of your network's security needs.