The cybersecurity landscape is constantly evolving, with new vulnerabilities and exploits surfacing every day. One such critical vulnerability, known as CVE-2022-47966, has recently come to light and poses a significant risk to organizations utilizing ManageEngine software.
This remote code execution vulnerability demands immediate attention from IT professionals and system administrators.
In this article, we’ll provide an in-depth analysis of the CVE-2022-47966 vulnerability, covering what it is, its risks, what products are affected, and how InvGate Asset Management can simplify Patch Management.
Keep reading to learn more about CVE-2022-47966 and how to safeguard your systems.
About CVE-2022-47966
CVE-2022-47966 is a critical remote code execution vulnerability in multiple Zoho ManageEngine on-premise products. The vulnerability is caused by the use of an outdated third-party dependency, Apache Santuario, in these products.
The impact of CVE-2022-47966 is critical. The vulnerability allows an attacker to execute arbitrary code on a vulnerable system by sending a specially crafted request to the affected product. The attacker can then use this code to gain full control of the system. As a consequence, the attacker can steal data, install malware, or disrupt operations.
The vulnerability has been exploited in the wild. In January 2023, researchers at Bitdefender found that attackers were using the vulnerability to install tools and malware on vulnerable ManageEngine ServiceDesk Plus servers.
CVE-2022-47966 affects the following Zoho ManageEngine on-premise products:
- Access Manager Plus
- Active Directory 360
- ADAudit Plus
- ADManager Plus
- ADSelfService Plus
- Analytics Plus
- Application Control Plus
- AssetExplorer
- Browser Security Plus
- Device Control Plus
- Endpoint Central
- Endpoint Central MSP
- Endpoint DLP
- Key Manager Plus
- OS Deployer
- PAM 360
- Password Manager Pro
- Patch Manager Plus
- Remote Access Plus
- Remote Monitoring and Management (RMM)
- ServiceDesk Plus
- ServiceDesk Plus MSP
- SupportCenter Plus
- Vulnerability Manager Plus
This advisory is applicable only when SAML SSO is/was enabled in the ManageEngine setup.
How to find devices exposed to CVE-2022-47966
With InvGate Asset Management, you can swiftly identify devices affected by the CVE-2022-47966 vulnerability. Here are the steps to follow:
- Open InvGate Asset Management and go to the Explorer tab.
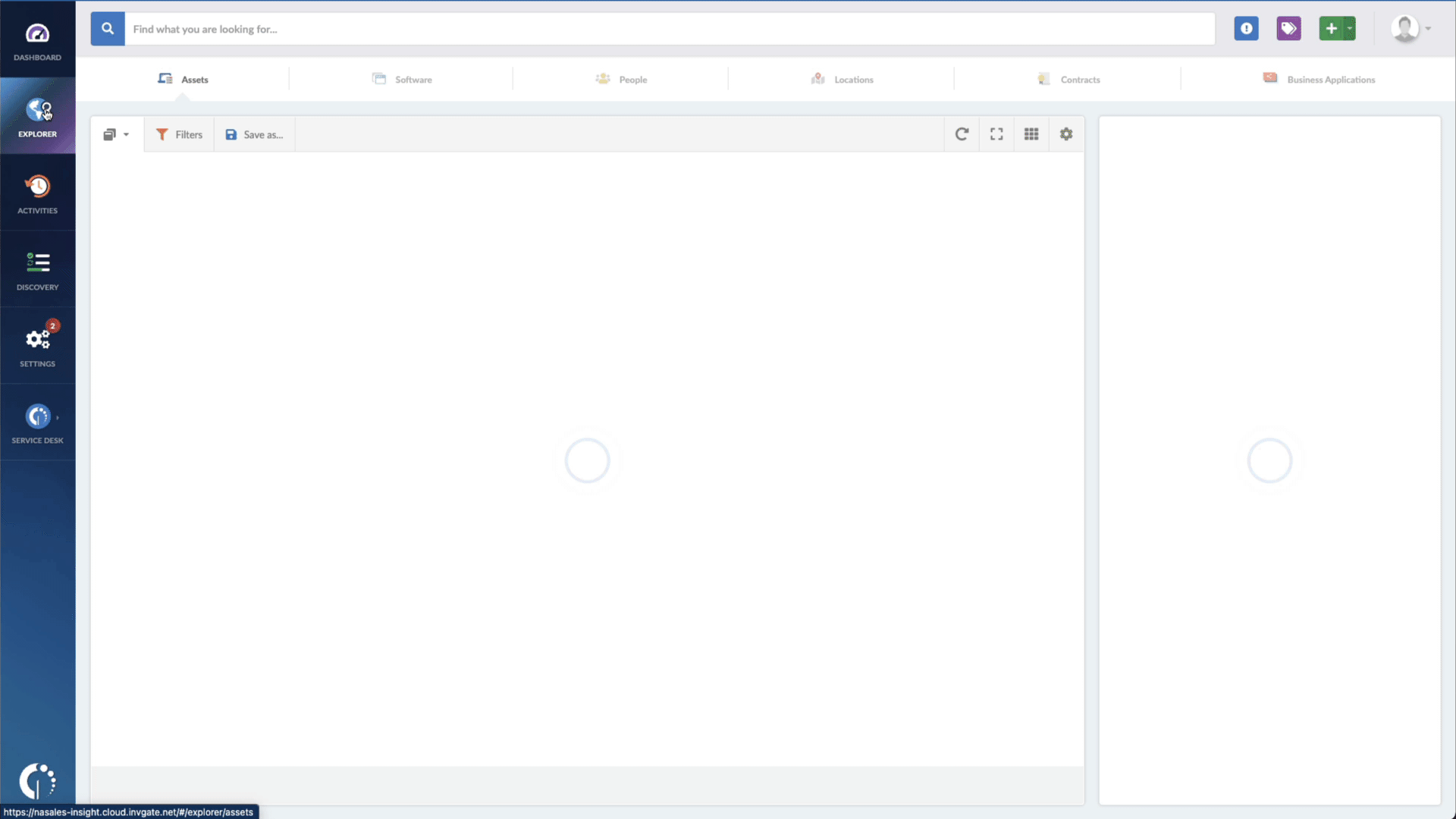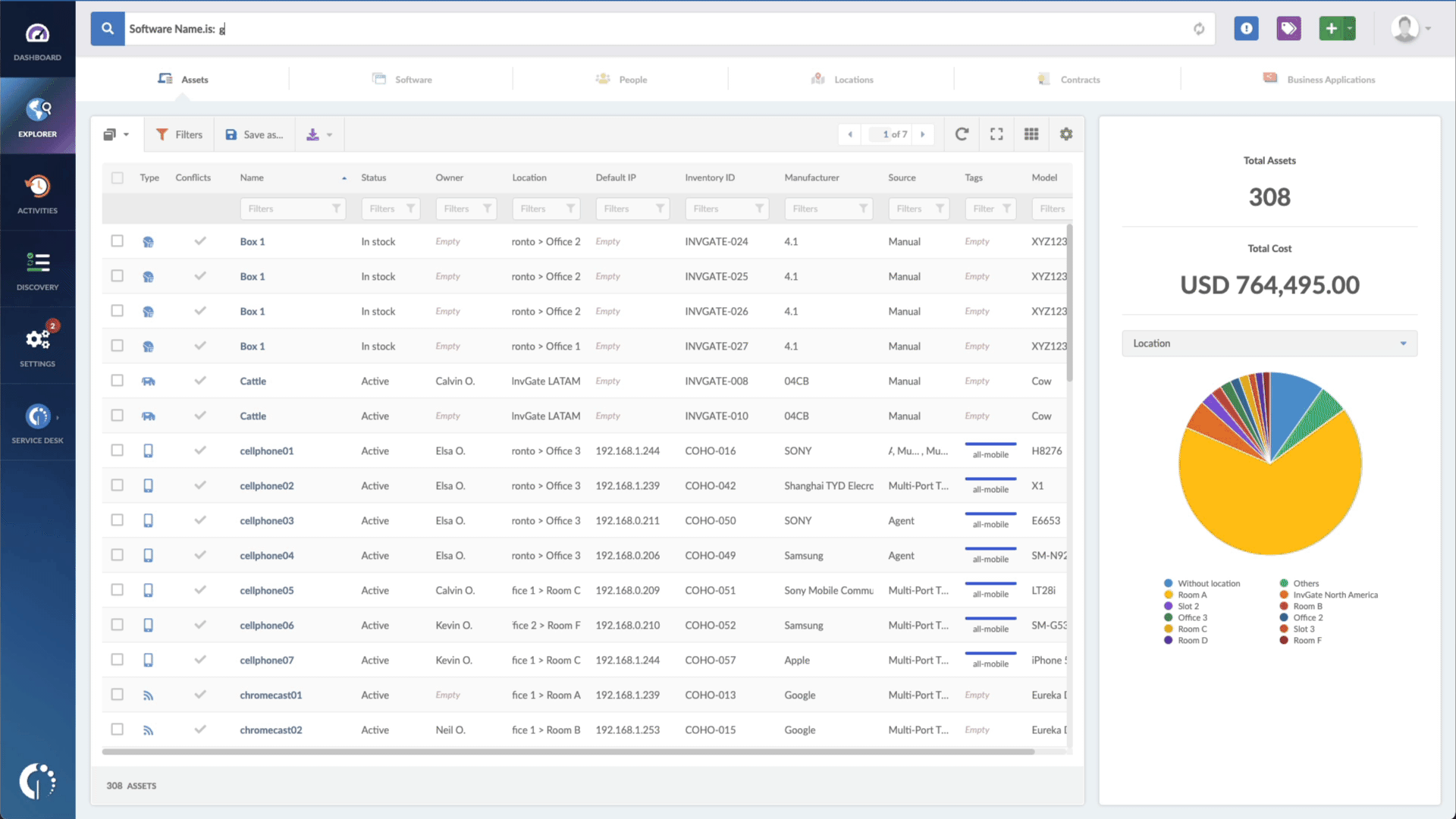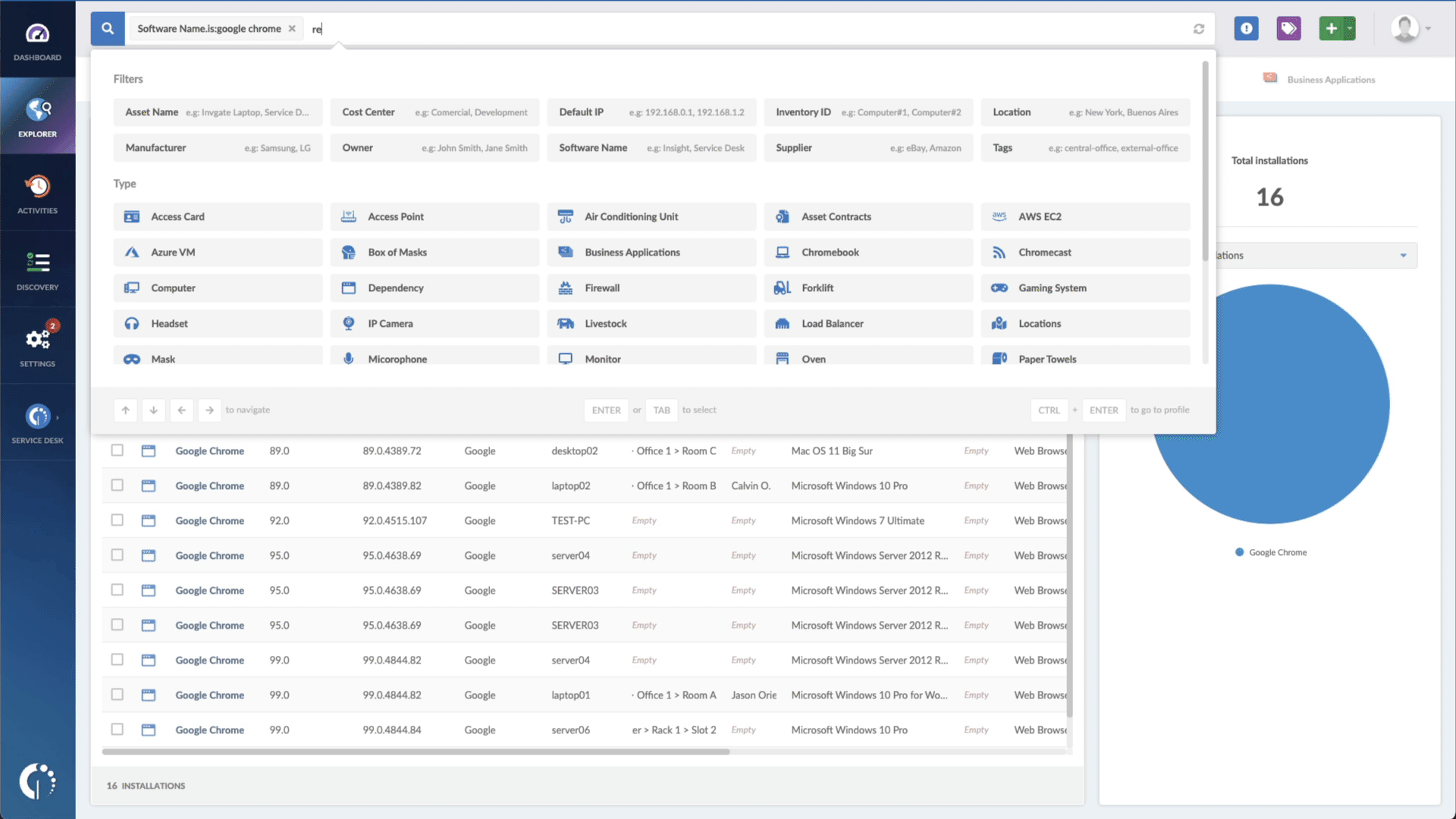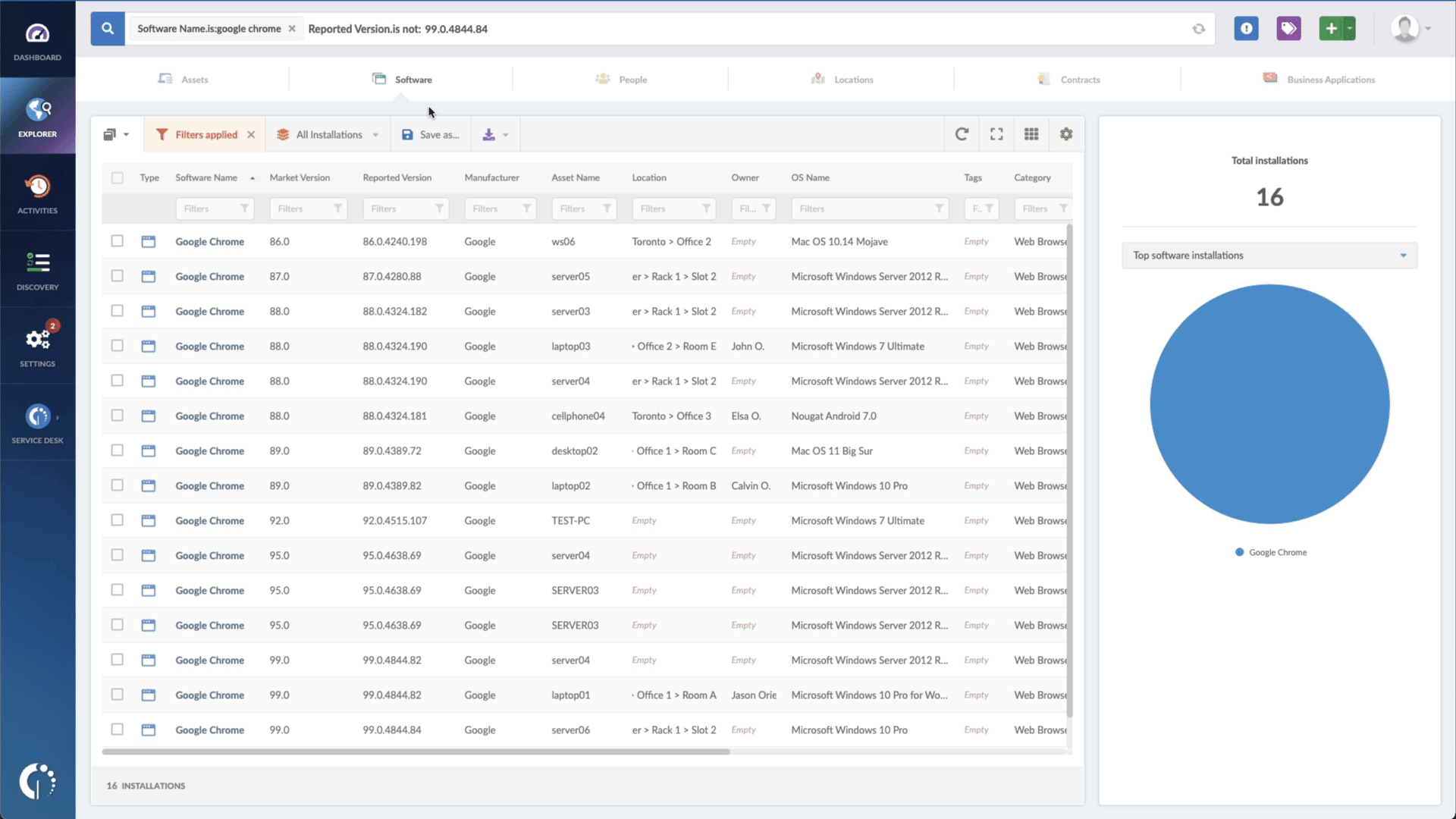
- Type in the Search bar “Software name, is:ManageEngine” to filter all devices with this product.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Zoho’s patched version (depending on your product, you’ll find the security update number on ManageEngine’s webpage).
The bottom line
The CVE-2022-47966 vulnerability found in ManageEngine software exposes organizations to significant risks, including remote code execution and potential compromise of their systems. The urgency to address this vulnerability cannot be overstated. By promptly updating the affected software to the latest version, which includes the necessary security patch, organizations can protect their IT infrastructure and sensitive data from potential attacks.
InvGate Asset Management offers a valuable solution to assist in identifying devices affected by CVE-2022-47966 and simplify patch management.
To experience the benefits of InvGate Asset Management and proactively manage vulnerabilities like CVE-2022-47966, request a 30-day free trial. Safeguard your organization's security by taking proactive steps today!