Cybersecurity threats are rising, and vulnerabilities like CVE-2022-41091 further underscore the need for businesses and individuals to stay vigilant. On November 8th, 2022, Microsoft stated this critical vulnerability, potentially allowing attackers to bypass the “Mark of the Web” (MOTW) security feature.
In this article, we’ll provide an overview of the CVE-2023-21674 vulnerability, including what it is, the associated risks, and how to identify vulnerable devices in your network with InvGate Asset Management. We will also discuss the steps you can take to patch your systems and keep them secure.
If you're concerned about your device's security, keep reading to learn more about CVE-2023-21674 and how to protect your systems.
About CVE-2022-41091
CVE-2022-41091 is a Windows zero-day vulnerability that allows attackers to bypass the “Mark of the Web” (MOTW) security feature. This feature was designed to prevent malicious code from running on a system by restricting the execution of files downloaded from the internet. MOTW appends a metadata tag to downloaded files that identify the source of the download, and if the file is from an untrusted source, Windows will block it from executing.
However, the CVE-2022-41091 vulnerability allows attackers to bypass the MOTW feature by using specially crafted file paths that trick Windows into thinking the file was downloaded from a trusted source.
The risk of not patching this vulnerability is significant. Attackers can create and distribute malicious files using phishing emails, social engineering tactics, or by compromising legitimate websites to download them to users' systems. Once downloaded, attackers can use this exploit to bypass the MOTW security feature and execute the malicious code, leading to a potential breach of sensitive data, system hijacking, and other forms of cyberattacks.
Microsoft released a patch for this vulnerability as part of its November 2022 Patch Tuesday updates. Windows users are advised to ensure that their systems are updated with the latest patches to prevent exploitation of this vulnerability. They should also avoid downloading files from untrusted sources or clicking on suspicious links to reduce the risk of downloading malicious files.
How to find devices exposed to CVE-2022-41091
If you are concerned about the CVE-2022-41091 vulnerability and want to determine if your devices are affected, InvGate Asset Management provides a fast and efficient solution. The following steps can guide you through the process:
- Open InvGate Asset Management and go to the Explorer tab.
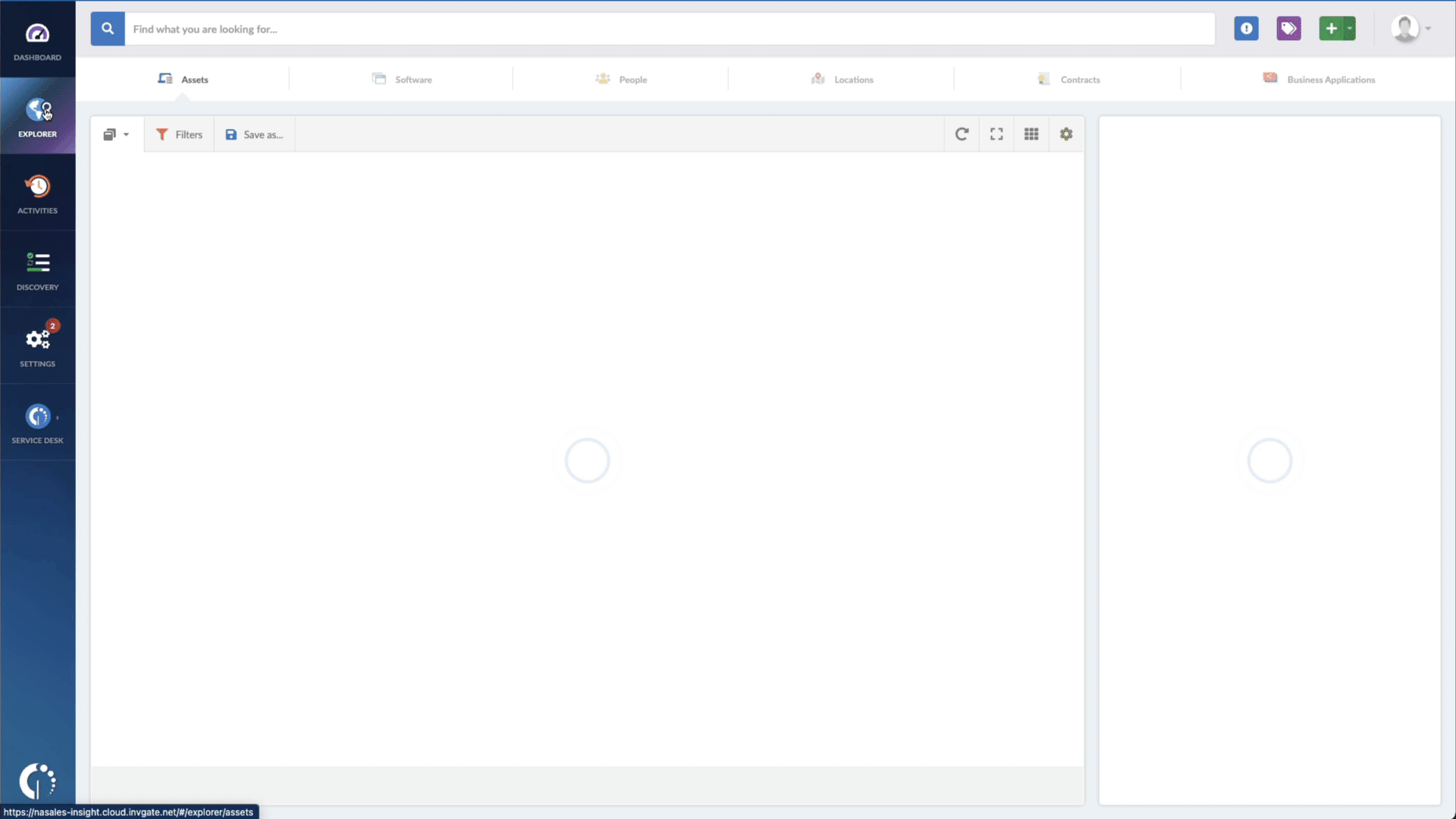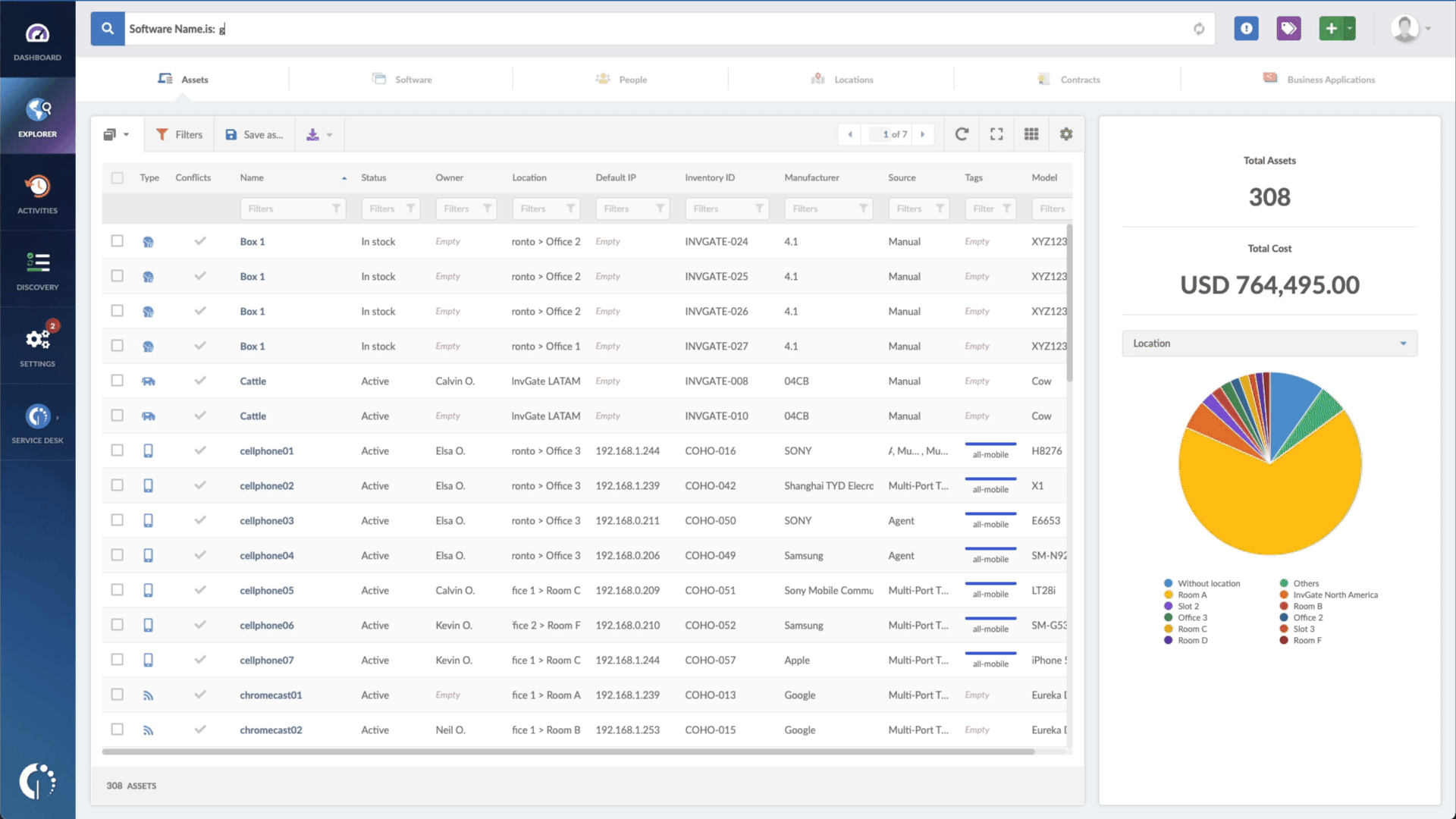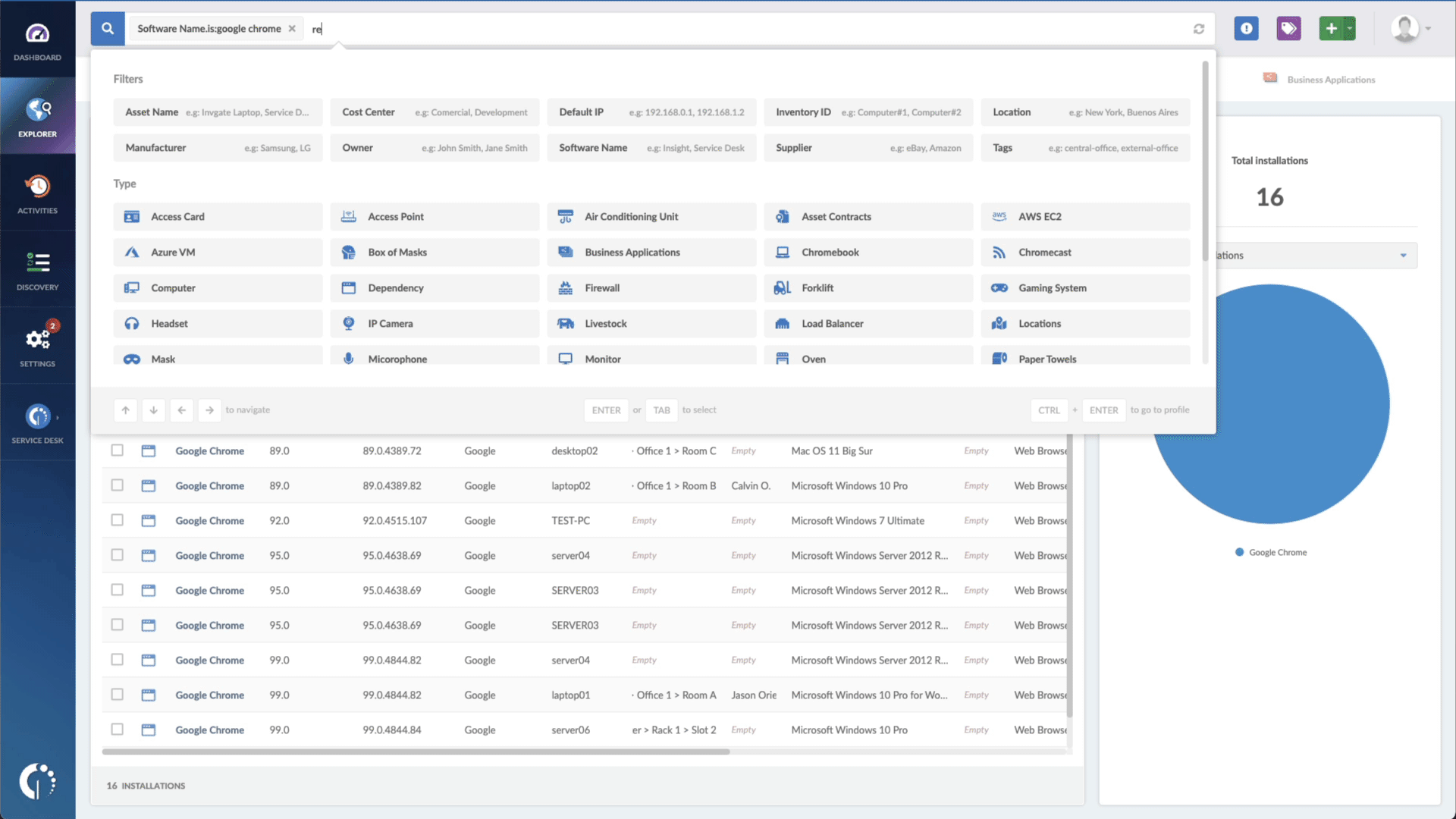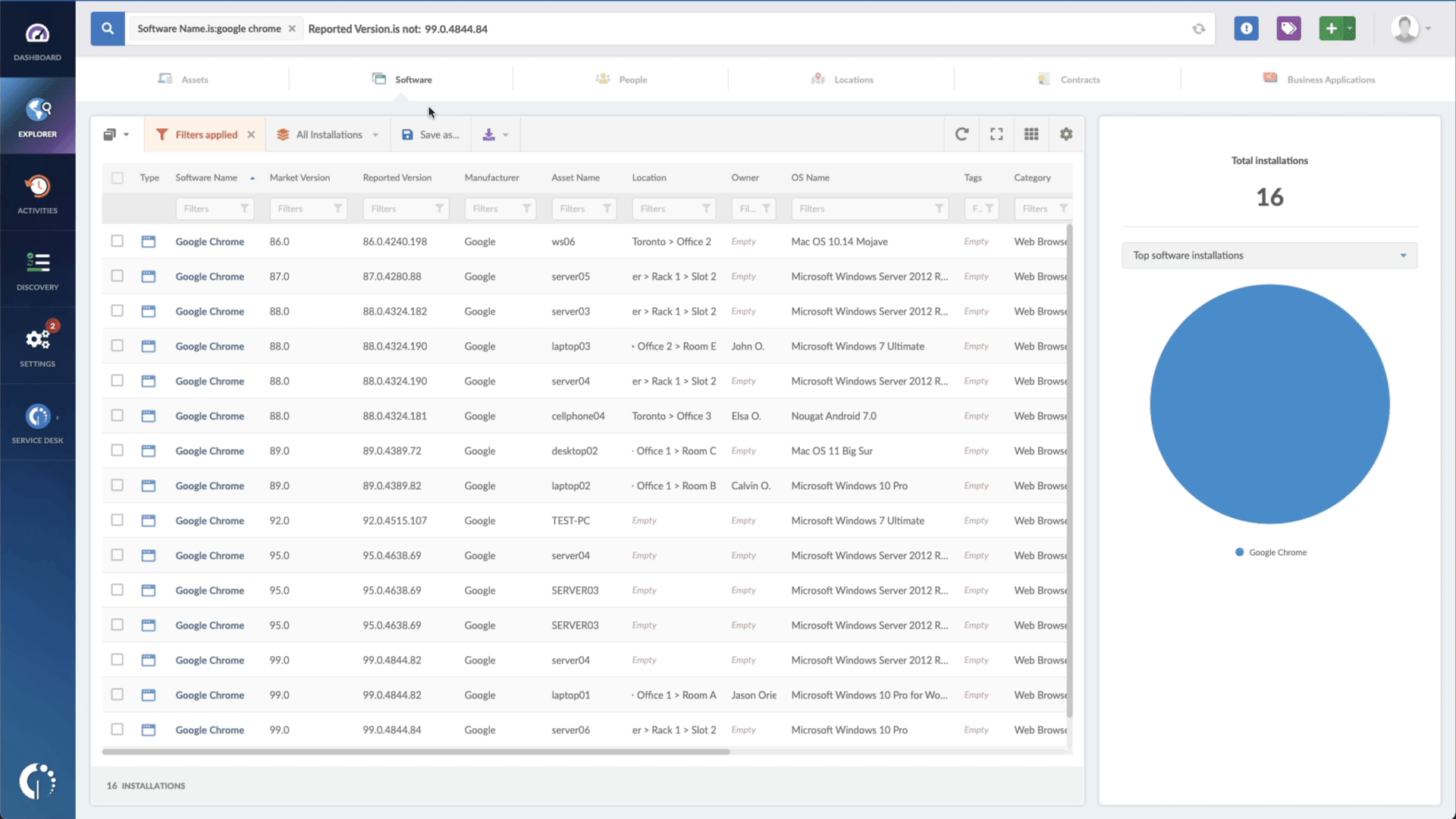
- Type in the Search bar “Software name, is:Windows” to filter all Windows devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your operating system, you’ll find the security update number on Microsoft’s webpage).
Other considerations
Aside from CVE-2022-41091, there has been another critical vulnerability in the Windows Mark of the Web Security Feature Bypass: the CVE-2022-41049.
Like CVE-2022-41091, it allows attackers to bypass the MOTW security feature in Windows and execute arbitrary code on the affected system. Microsoft has released a patch to address this vulnerability, and users are advised to update their systems to the latest software version to mitigate the risk.
The bottom line
The CVE-2022-41091 vulnerability poses a significant threat to Windows users, allowing attackers to bypass the MOTW security feature and execute malicious code on vulnerable systems. Microsoft has released a patch to address this vulnerability, and users are advised to update their systems to the latest software version as soon as possible.
InvGate Asset Management simplifies the process of identifying devices in a network that are vulnerable to CVE-2022-41091 and other security threats. With its user-friendly interface and functions, InvGate Asset Management helps users save time and effort in securing their systems.
If you want to ensure your systems are secure and protected from CVE-2022-41091 and other vulnerabilities, we encourage you to try InvGate Asset Management's 30-day free trial and see how it can help you streamline your Patch Management process.