As cyber threats continue to evolve, keeping your systems up-to-date is crucial. On October 11th, 2022, Microsoft issued a statement warning users of a critical vulnerability in Windows COM+ Event System Service, known as CVE-2022-41033.
This exploit is an elevation of privilege (EoP) vulnerability in the Windows COM+ Event System Service. It enables system event notifications for COM+ component services. In this article, we'll provide a comprehensive overview of CVE-2022-41033, including what it is, its risks, and how InvGate Asset Management simplifies Patch Management and helps identify vulnerable devices.
Don't wait until it's too late. Learn how to protect your systems from CVE-2022-41033!
About CVE-2022-41033
CVE-2022-41033 is a vulnerability in the Windows COM+ Event System Service. The vulnerability, which has a CVSS score of 7.8, can be exploited by executing a specially-crafted program to execute arbitrary code with higher privileges.
An authenticated attacker could exploit it to elevate privileges on a vulnerable system and gain SYSTEM privileges.
All versions of Windows from Windows 7 and Windows Server 2008 onwards are susceptible to this exploit. Microsoft released a security update to address it on October 11th, 2022, as part of its monthly "Patch Tuesday" release cycle. Installing it as soon as possible is essential to mitigate the risk of exploitation.
How to find devices exposed to CVE-2022-41033
InvGate Asset Management enables quick detection of devices that the CVE-2022-41033 vulnerability has impacted. Follow these instructions to identify affected devices:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is Windows” to filter all Windows devices.
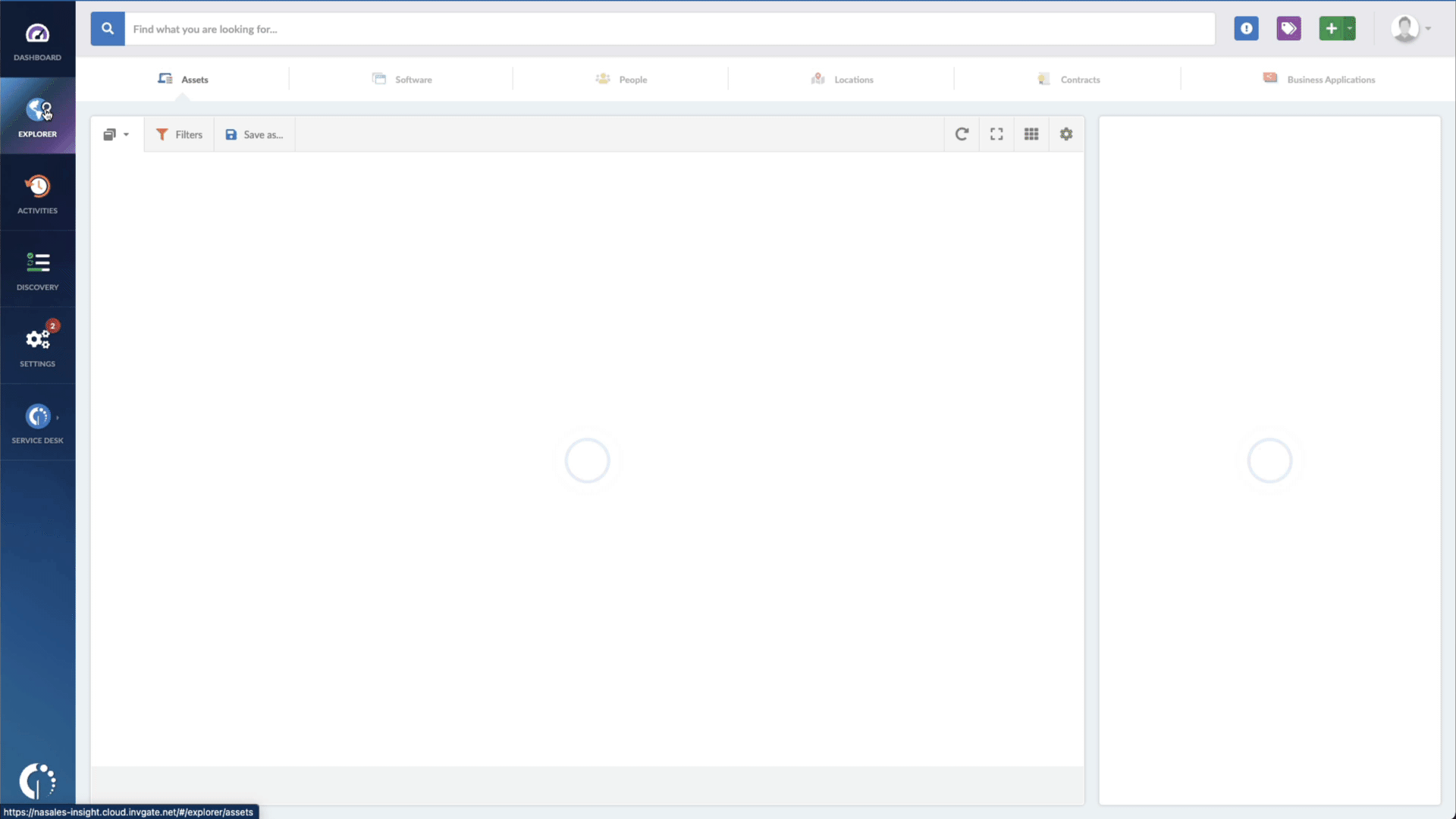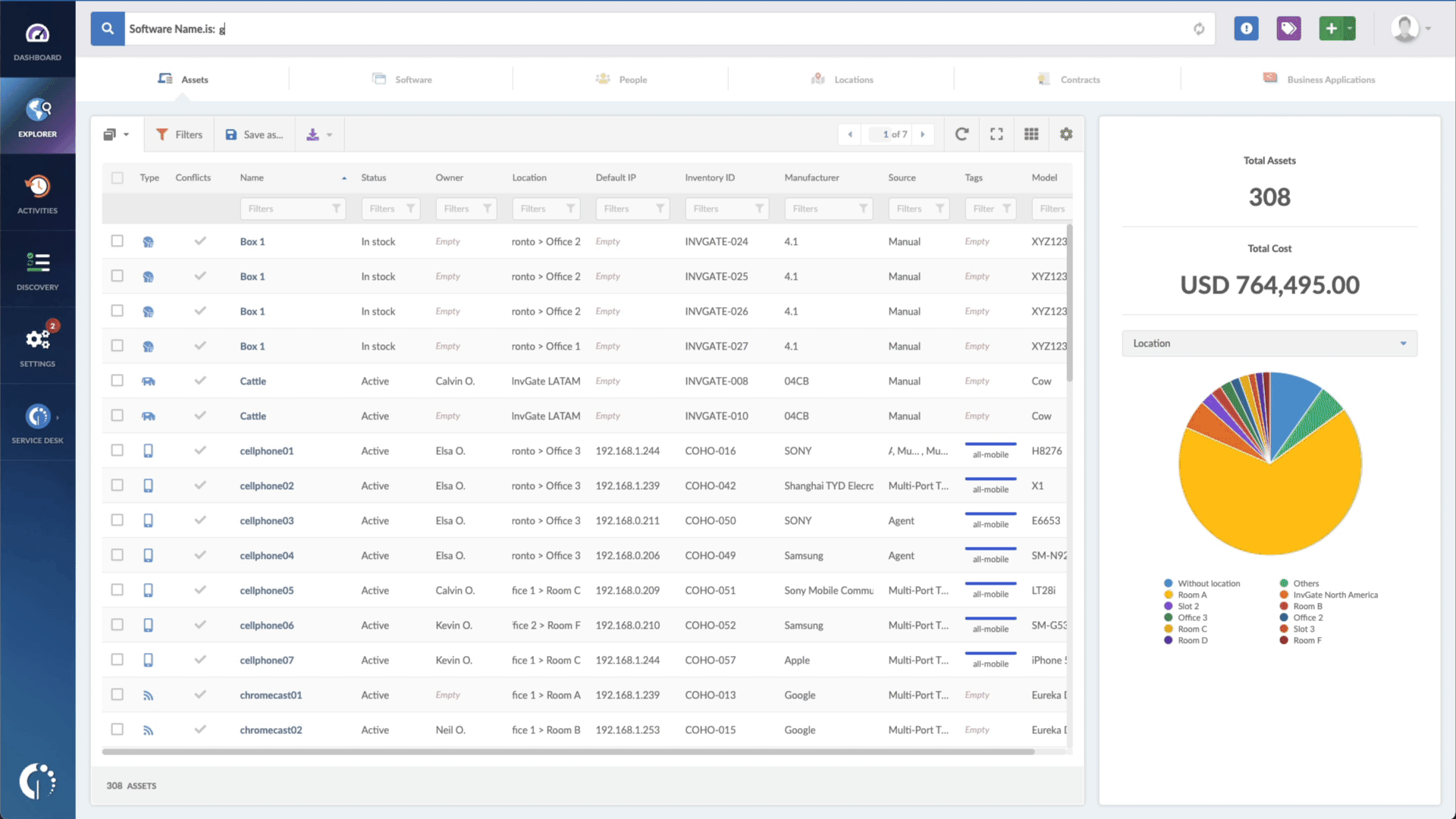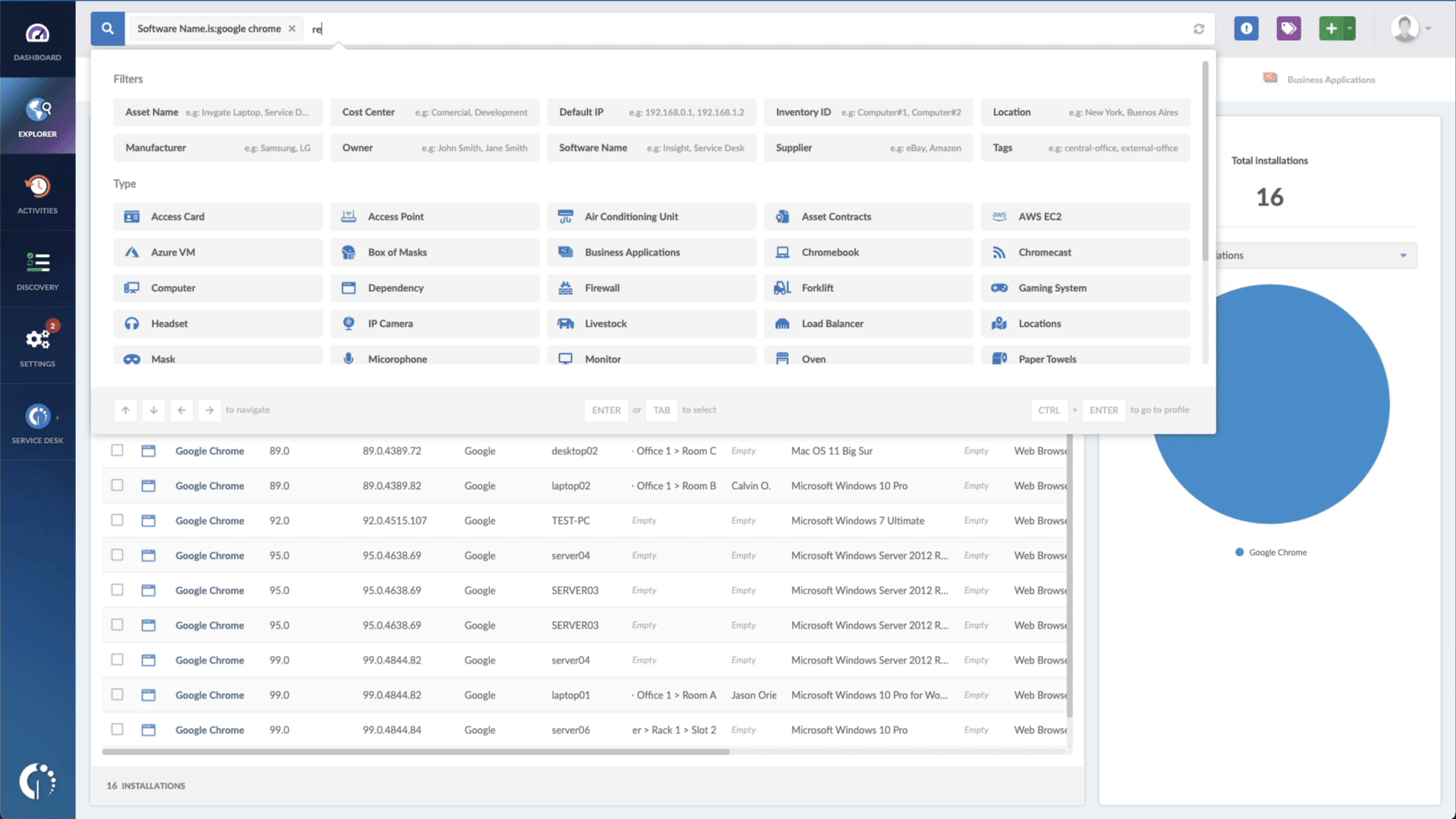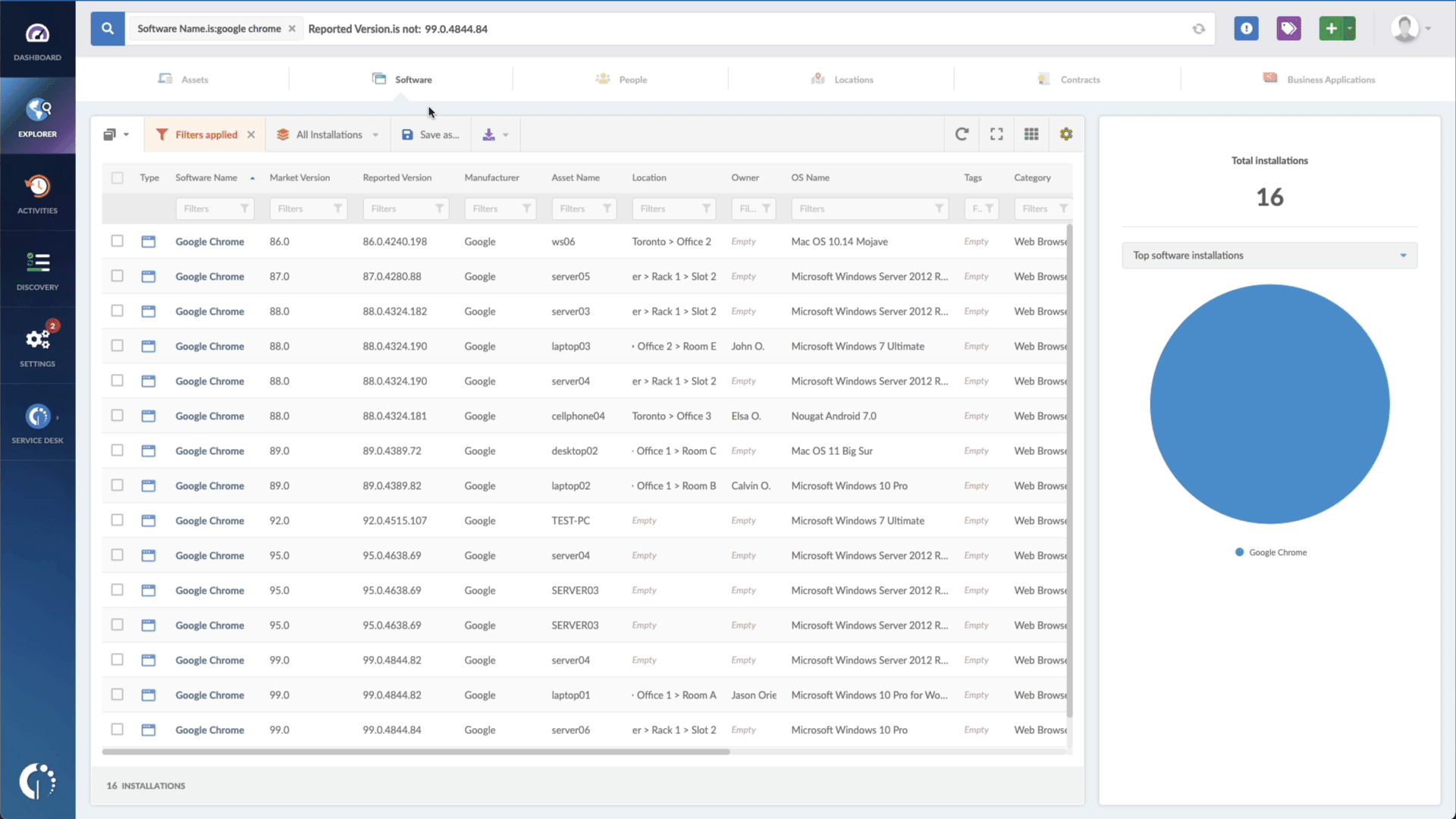
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 10 Version 1607 for 32-bit Systems, it's KB5018411).
Other vulnerabilities
Another vulnerability that requires urgent attention is CVE-2022-37968, which has the highest possible CVSS rating of 10.0. This exploit allows attackers to gain control over Azure Arc-enabled Kubernetes clusters and could also affect Azure Stack Edge devices.
To exploit this remotely, the attacker must know the randomly generated DNS endpoint for the Kubernetes cluster. It is advised to enable auto-upgrades or manually update to the latest version by running the appropriate commands in the Azure CLI.
CVE-2022-38048 is another vulnerability that requires quick patching. It is a Microsoft Office RCE flaw that could trigger even with user interaction. Although Microsoft rarely considers Office flaws critical, this one is an exception as it could lead to passing an arbitrary pointer to a free call, making further memory corruption possible.
The bottom line
The CVE-2022-41033 vulnerability in the Windows COM+ Event System Service poses a significant risk to organizations that fail to patch affected systems promptly. With a CVSS score of 7.8, this vulnerability can be exploited remotely by attackers to gain complete control over a compromised system, steal sensitive data, and launch further attacks.
To mitigate the risk of exploitation, organizations should promptly update their systems with the latest security patch released by Microsoft as part of the October 2022 "Patch Tuesday" cycle.
InvGate Asset Management can help organizations identify devices vulnerable to this and other known vulnerabilities. The platform's easy-to-use interface lets users quickly identify vulnerable devices and prioritize remediation efforts to ensure the network remains secure.
Request a 30-day free trial to protect your systems against the latest threats!