CVE-2022-40684, a critical vulnerability affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager products, emerged on October 2022 as a significant concern for organizations relying on these solutions for network security.
In this article, we’ll provide you with comprehensive information about CVE-2022-40684, including its impact, affected versions, and how InvGate Asset Management can help you to safeguard your network from potential exploitation.
Read on to learn more about CVE-2022-40684 and secure your network against potential risks.
About CVE-2022-40684
CVE-2022-40684 is a critical vulnerability in Fortinet FortiOS, FortiProxy, and FortiSwitchManager products. The vulnerability allows an unauthenticated attacker to bypass authentication and perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
It affects:
- FortiOS versions: 7.2.1, 7.2.0, 7.0.6, 7.0.5, 7.0.4, 7.0.3, 7.0.2, 7.0.1, 7.0.0
- FortiProxy versions: 7.2.0, 7.0.6, 7.0.5, 7.0.4, 7.0.3, 7.0.2, 7.0.1, 7.0.0
- FortiSwitchManager versions: 7.2.0, 7.0.0
How does CVE-2022-40684 work?
The vulnerability is caused by a flaw in the way that Fortinet products handle HTTP requests. The flaw allows an attacker to bypass the authentication mechanism and send requests to the administrative interface as if they were authenticated. Thus, the attacker could perform a variety of actions, including:
- Changing the configuration of the device.
- Deleting or modifying files.
- Installing malware.
- Denial of service attacks.
What are CVE-2022-40684 risks?
An attacker who exploits this vulnerability could gain full control of your Fortinet device and perform actions like:
- Change the configuration of your network.
- Expose your network to the internet.
- Steal sensitive data.
- Disrupt your business operations.
Is CVE-2022-40684 fixed?
Yes, Fortinet released software updates that include the necessary fixes. If you are using Fortinet FortiOS, FortiProxy, or FortiSwitchManager products, you should immediately install the patch for CVE-2022-40684.
The software versions that include the patch are:
- FortiOS version 7.2.2 or above, or version 7.0.7 or above
- FortiProxy version 7.2.1 or above, or 7.0.7 or above
- FortiSwitchManager version 7.2.1 or above
How to find devices exposed to CVE-2022-40684
With InvGate Asset Management you can promptly detect the devices that have been impacted by the CVE-2022-40684 vulnerability. The following instructions outline the process to take:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Fortinet FortiOS” (or FortiProxy, or FortiSwitchManager) to filter all devices with these products.
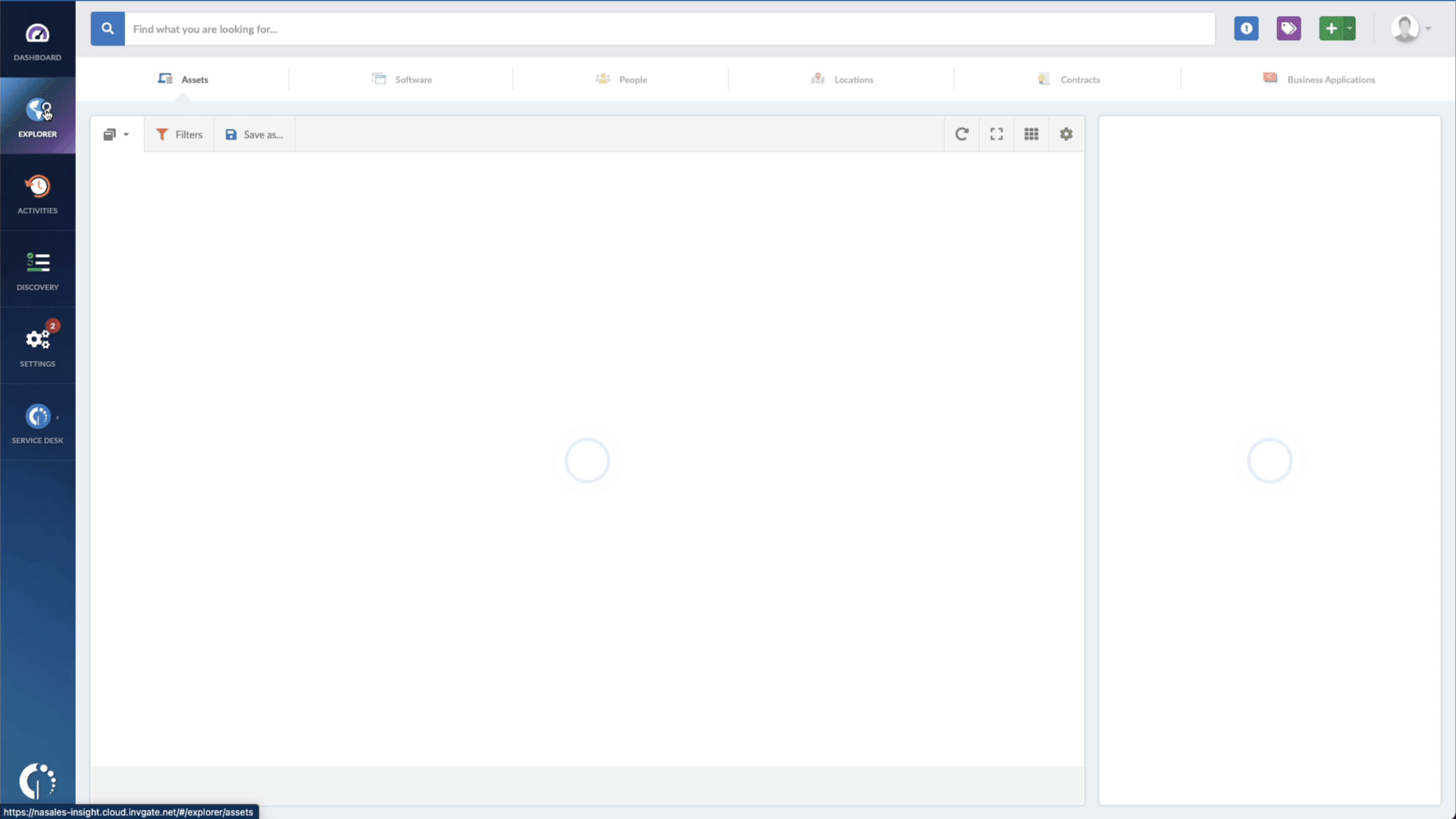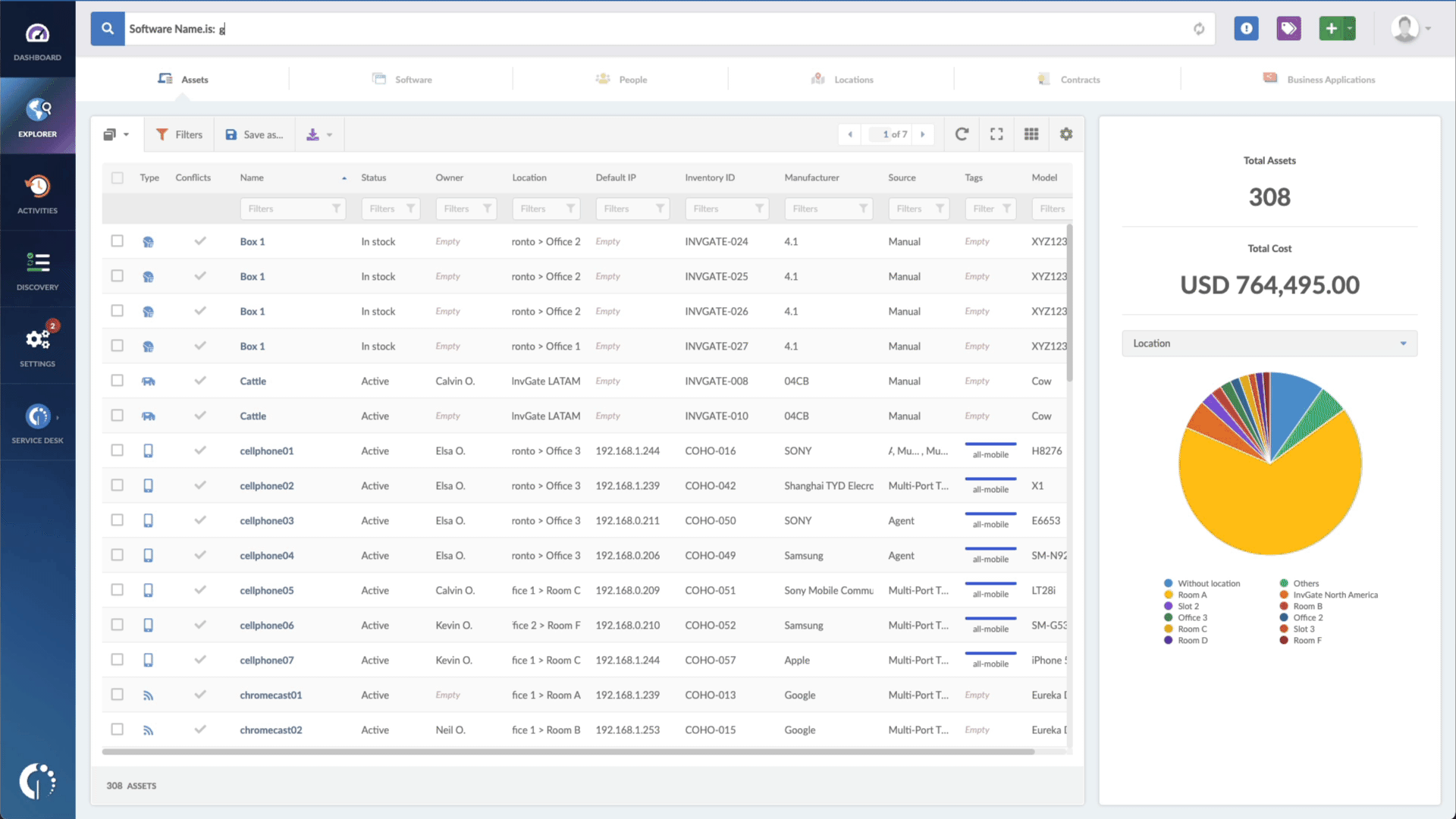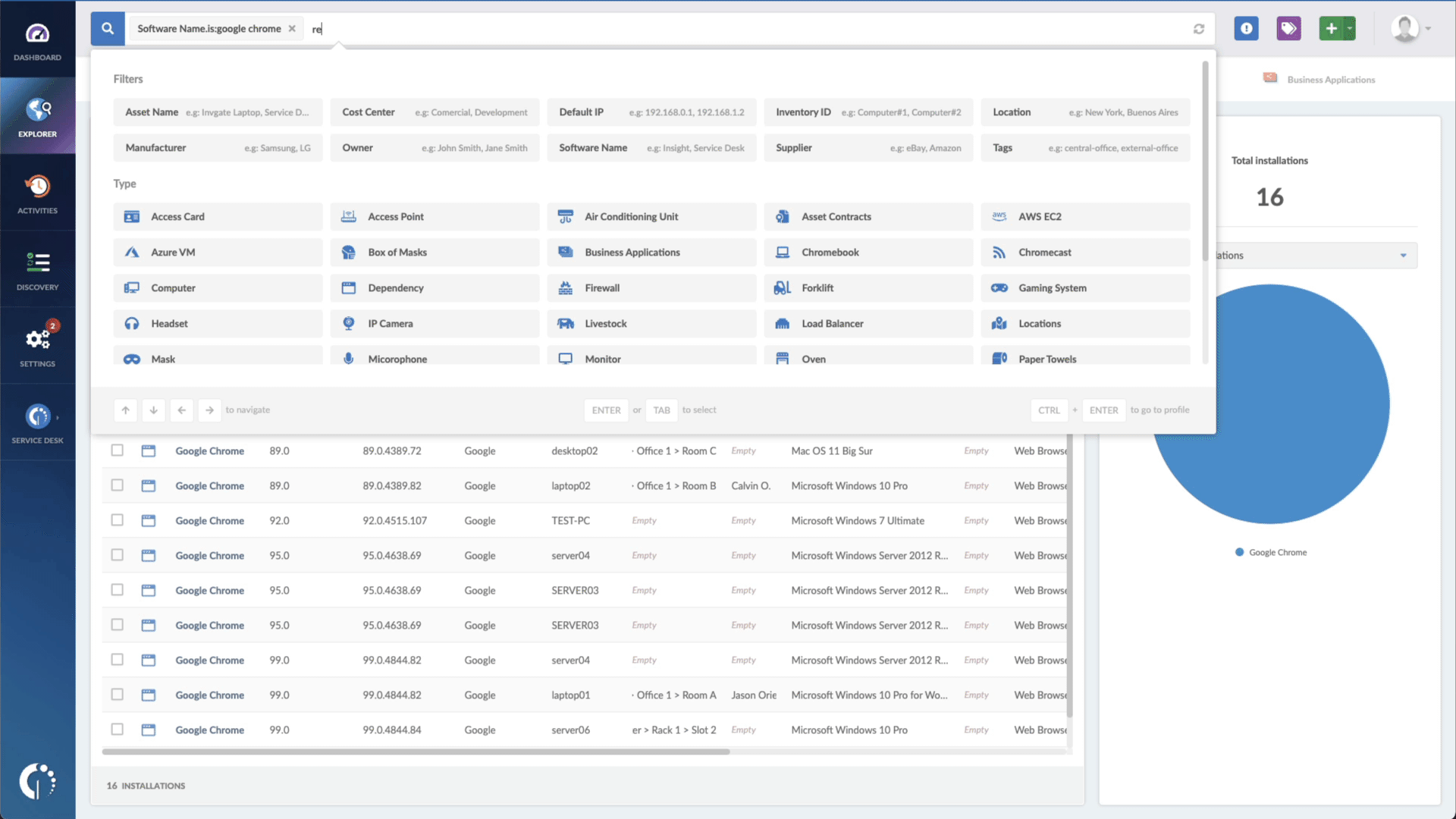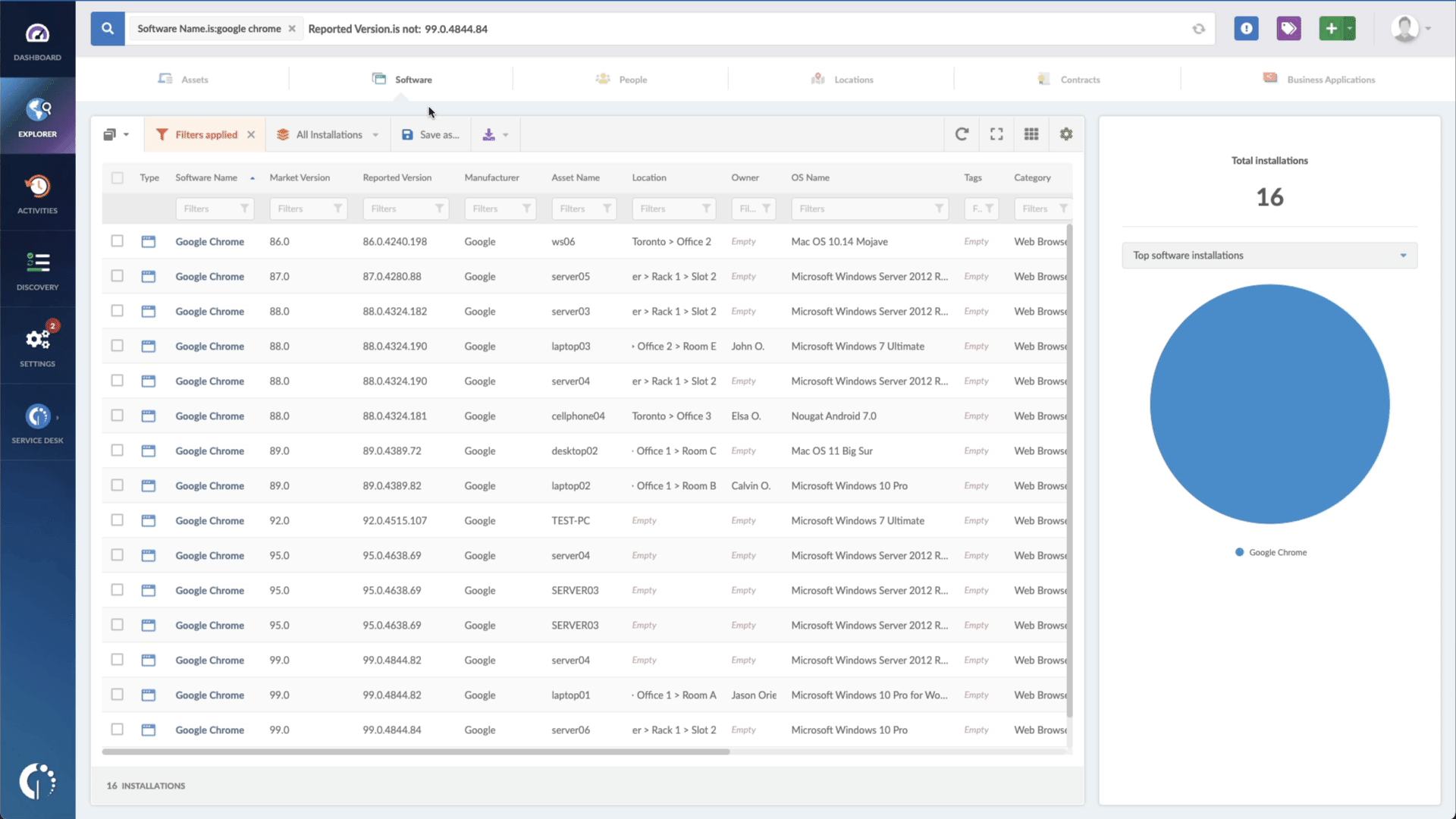
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Fortinet’s patched version (mentioned above).
The bottom line
CVE-2022-40684 is a critical vulnerability impacting Fortinet FortiOS, FortiProxy, and FortiSwitchManager products. This flaw enables unauthorized individuals to bypass authentication and carry out malicious activities on the administrative interface.
However, Fortinet has released software updates to address this vulnerability, ensuring the security of their products. To simplify the process of identifying vulnerable devices and Patch Management, InvGate Asset Management offers an efficient solution. Request a 30-day free trial today and safeguard your organization's assets.