In today's digital landscape, safeguarding your systems against security vulnerabilities is paramount. One such vulnerability that demands immediate attention is the Windows Common Log File System (CLFS) driver elevation of privilege vulnerability, known as CVE-2022-37969.
In this article, we’ll delve into the details of the CVE-2022-37969 vulnerability, its implications, and how InvGate Asset Management simplifies Patch Management.
Read more to learn about CVE-2022-37969. Don't leave your network vulnerable—act now to safeguard your organization against potential threats.
About CVE-2022-37969
CVE-2022-37969 is a local privilege escalation vulnerability in the Windows Common Log File System (CLFS) driver. It allows an attacker who has access to a vulnerable system to elevate their privileges to SYSTEM.
How does CVE-2022-37969 work?
The vulnerability is caused by a flaw in the way that the CLFS driver handles certain requests. An attacker can exploit this vulnerability by creating a specially crafted log file that can be opened by the CLFS driver. When the driver opens the file, it will be vulnerable to arbitrary code execution.
What are CVE-2022-37969 risks?
An attacker who successfully exploits this vulnerability could gain SYSTEM privileges on the vulnerable system. This allows to do anything a user with SYSTEM privileges could do, including installing malware, stealing data, or taking control of the system.
Is CVE-2022-37969 fixed?
Yes, Microsoft has released a security update that addresses CVE-2022-37969, available for all supported versions of Windows. Users are urged to apply it as soon as possible.
How to find devices exposed to CVE-2022-37969
To efficiently detect devices that are impacted by the CVE-2022-37969 vulnerability, InvGate Asset Management offers a robust solution. The following guidelines outline the steps to be taken:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Microsoft Windows” to filter all Windows devices.
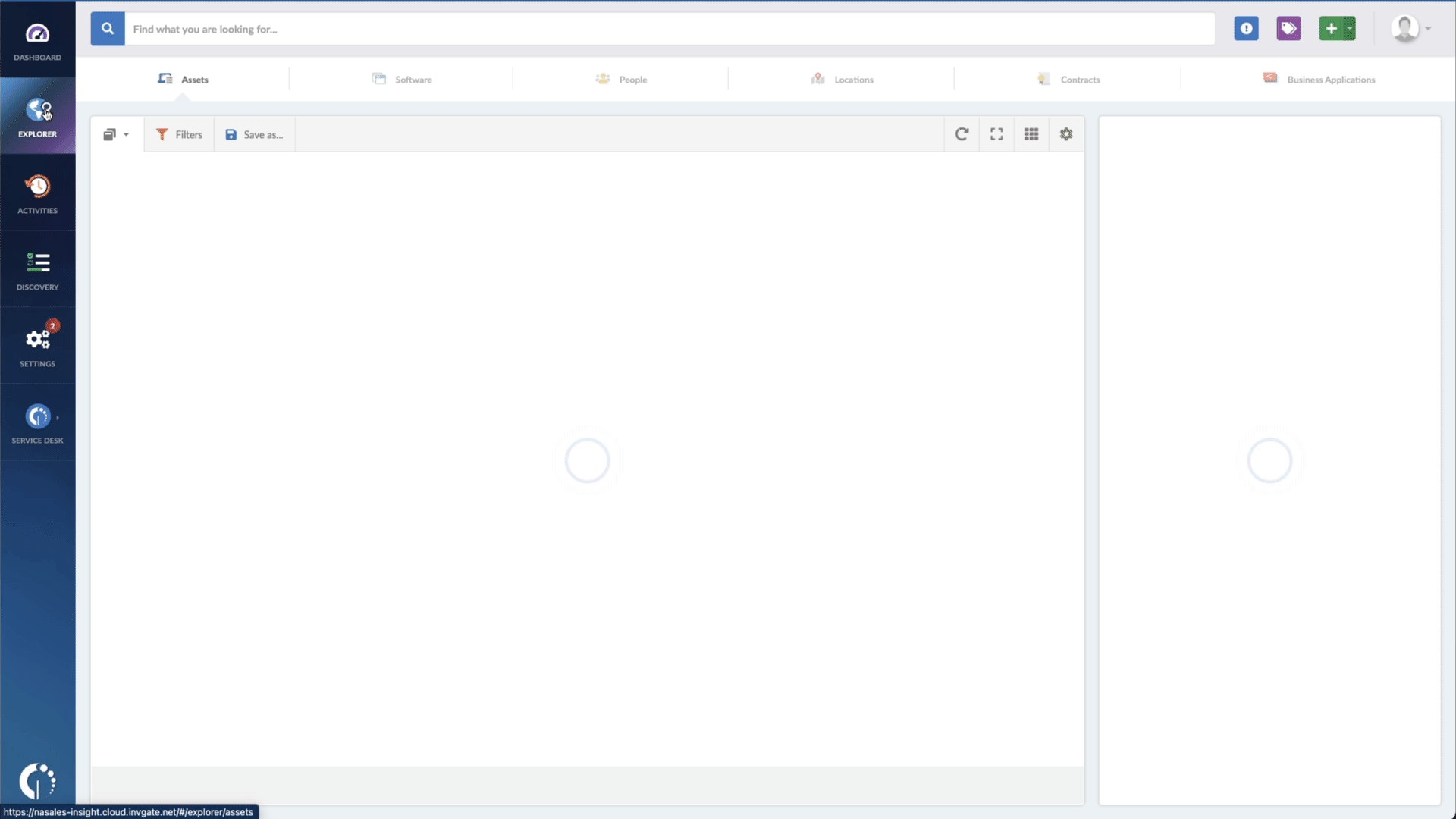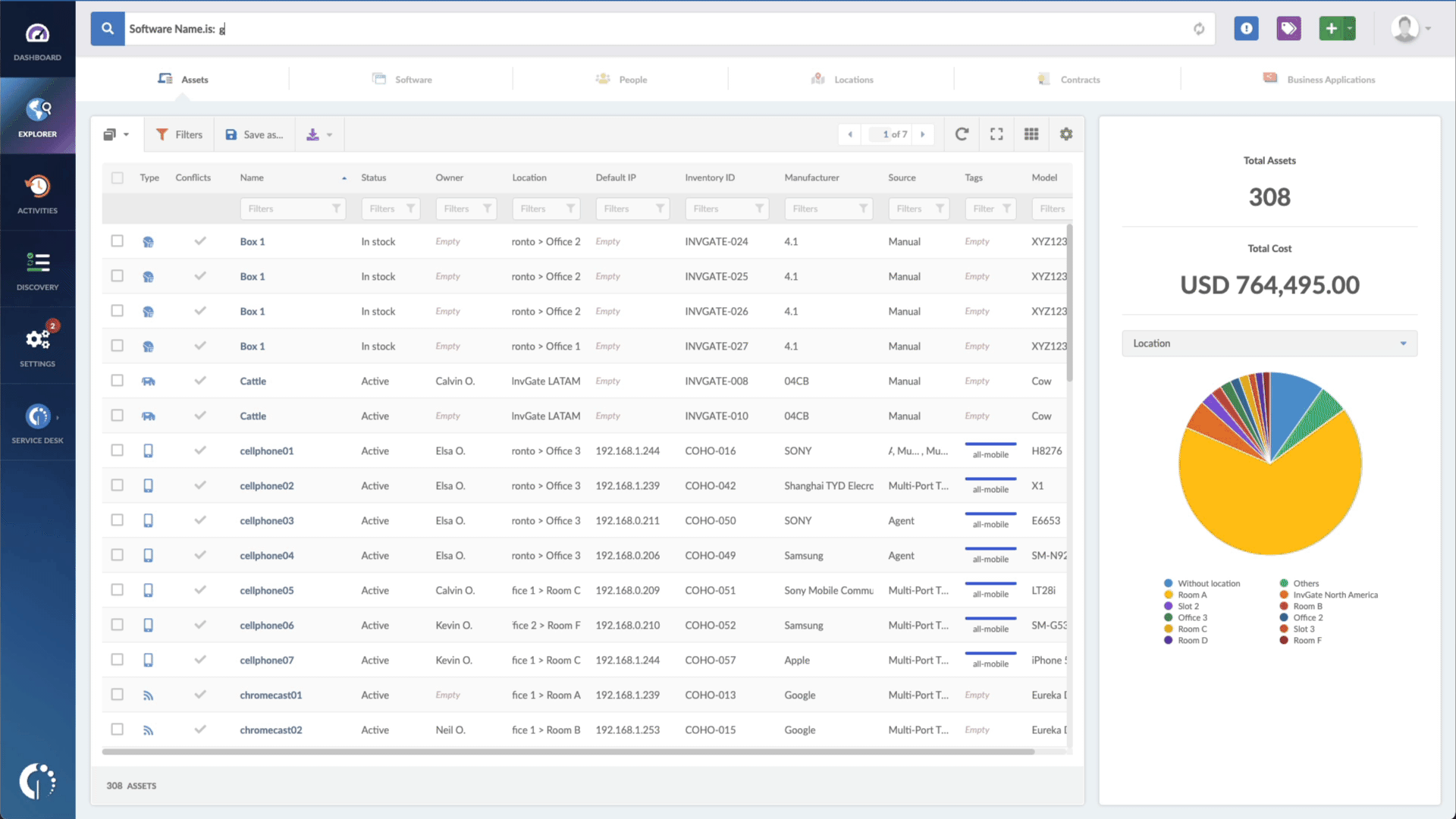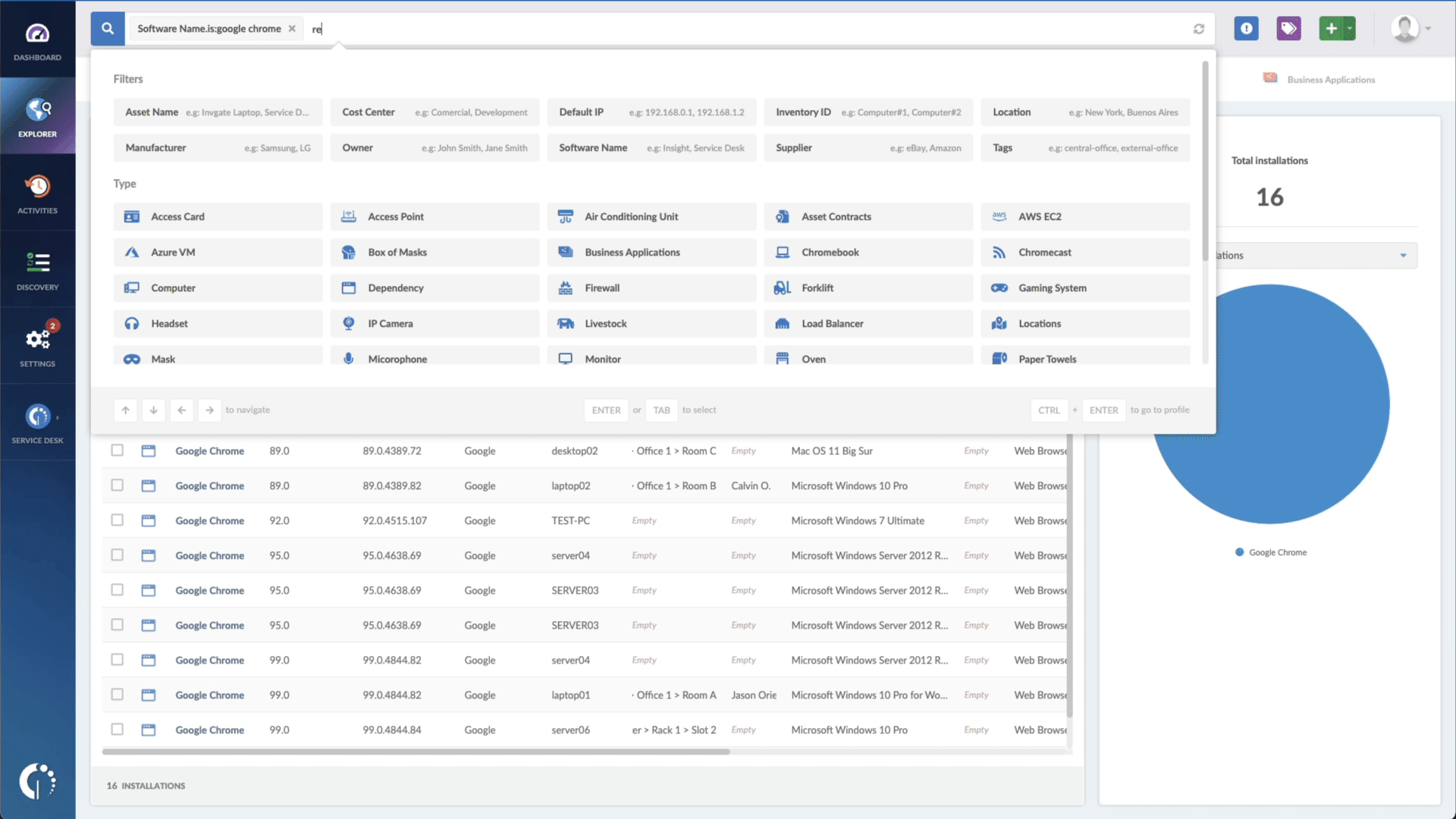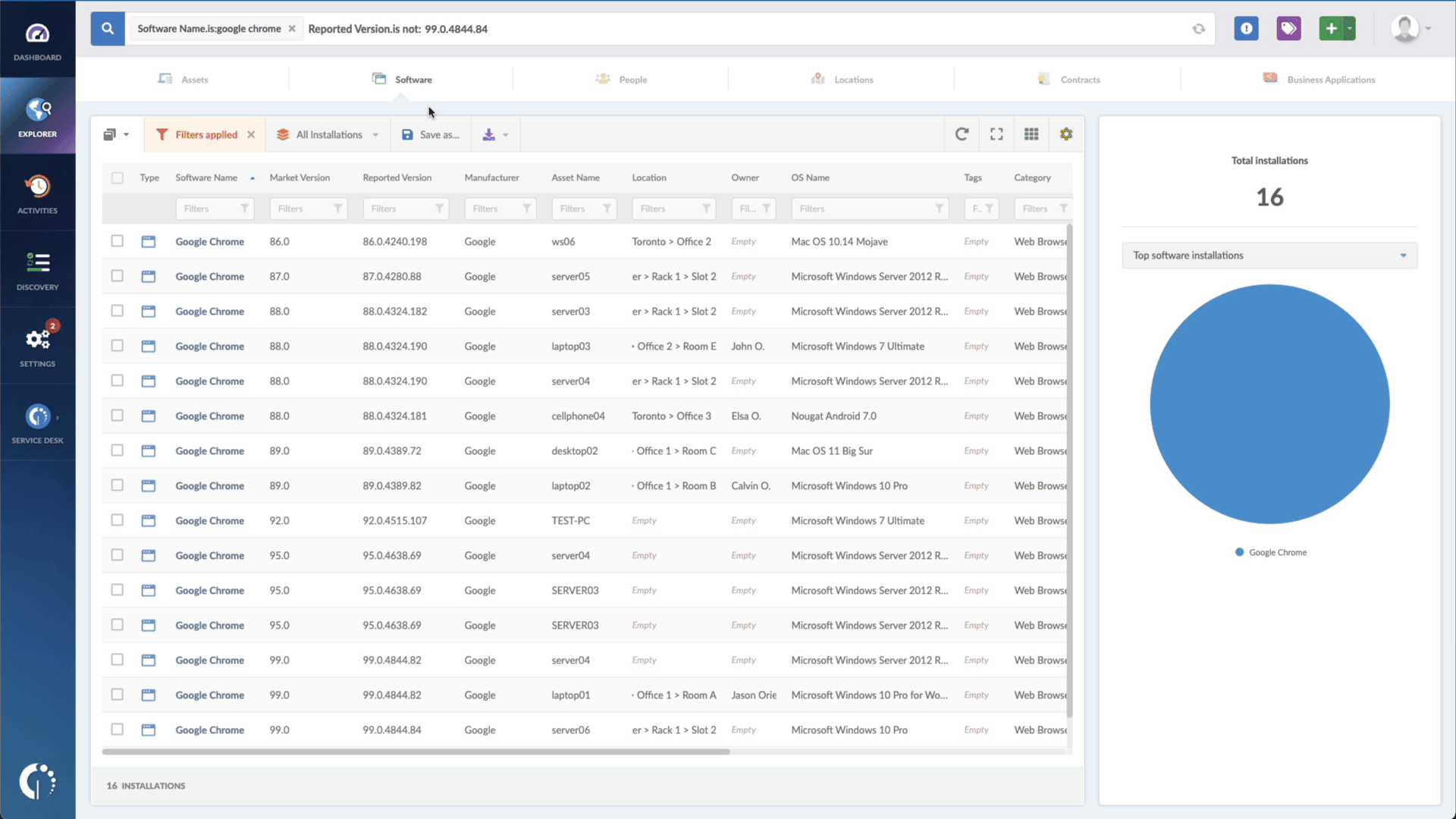
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 10 for 32-bit Systems, it's KB5017327).
The bottom line
In summary, CVE-2022-37969 represents a critical vulnerability in the Windows Common Log File System (CLFS) driver that allows for privilege escalation. Without applying the necessary patch, systems remain vulnerable to unauthorized access and potential compromise, posing significant risks to confidentiality and system integrity.
InvGate Asset Management provides a valuable solution to simplify Patch Management by swiftly identifying devices affected by vulnerabilities like CVE-2022-37969. To experience the benefits of InvGate Asset Management, request a 30-day free trial today.
















