With the recent identification of the CVE-2022-36067 vulnerability in the vm2 JavaScript sandbox library, the security and integrity of systems have become a paramount concern. Safeguarding your systems from this vulnerability is crucial to maintain the confidentiality and integrity of your data.
In this article, we’ll explore the intricacies of the CVE-2022-36067 vulnerability, shedding light on its potential risks and emphasizing the significance of promptly addressing the issue. Regarding this, InvGate Asset Management simplifies the Patch Management process and secures affected systems.
Continue reading to stay updated on the details of the CVE-2022-36067 vulnerability. It's time to take the necessary steps to safeguard your valuable data.
About CVE-2022-36067
CVE-2022-36067 is a critical remote code execution vulnerability in the vm2 sandbox library.
vm2 is a popular JavaScript sandbox library that enables developers to create controlled environments for executing untrusted code. With approximately 17.5 million monthly downloads, vm2 is highly utilized in the JavaScript ecosystem.
CVE-2022-36067 has a CVSS score of 10.0, which is the highest possible score. The vulnerability allows an attacker to bypass the sandbox protections and execute arbitrary code on the host system.
How does CVE-2022-36067 work?
The vulnerability is caused by a flaw in the way that vm2 handles the Module object. The Module object is used to represent a loaded module in the sandbox. The vulnerability allows an attacker to create a malicious Module object that can bypass the sandbox protections. Once the malicious module is loaded, the attacker can execute arbitrary code on the host system.
What are CVE-2022-36067 risks?
An attacker could exploit the vulnerability to gain full control of a vulnerable system, allowing them to steal data, install malware, or disrupt services.
Is CVE-2022-36067 fixed?
Yes, the vulnerability has been patched in vm2 version 3.9.11. Users should upgrade to the latest version to protect themselves from this exploit.
How to find devices exposed to CVE-2022-36067
By leveraging InvGate Asset Management, you can quickly pinpoint devices that are susceptible to the CVE-2022-36067 vulnerability. To assist you in this process, here is a step-by-step guide to follow:
- Open InvGate Asset Management and go to the Explorer tab.
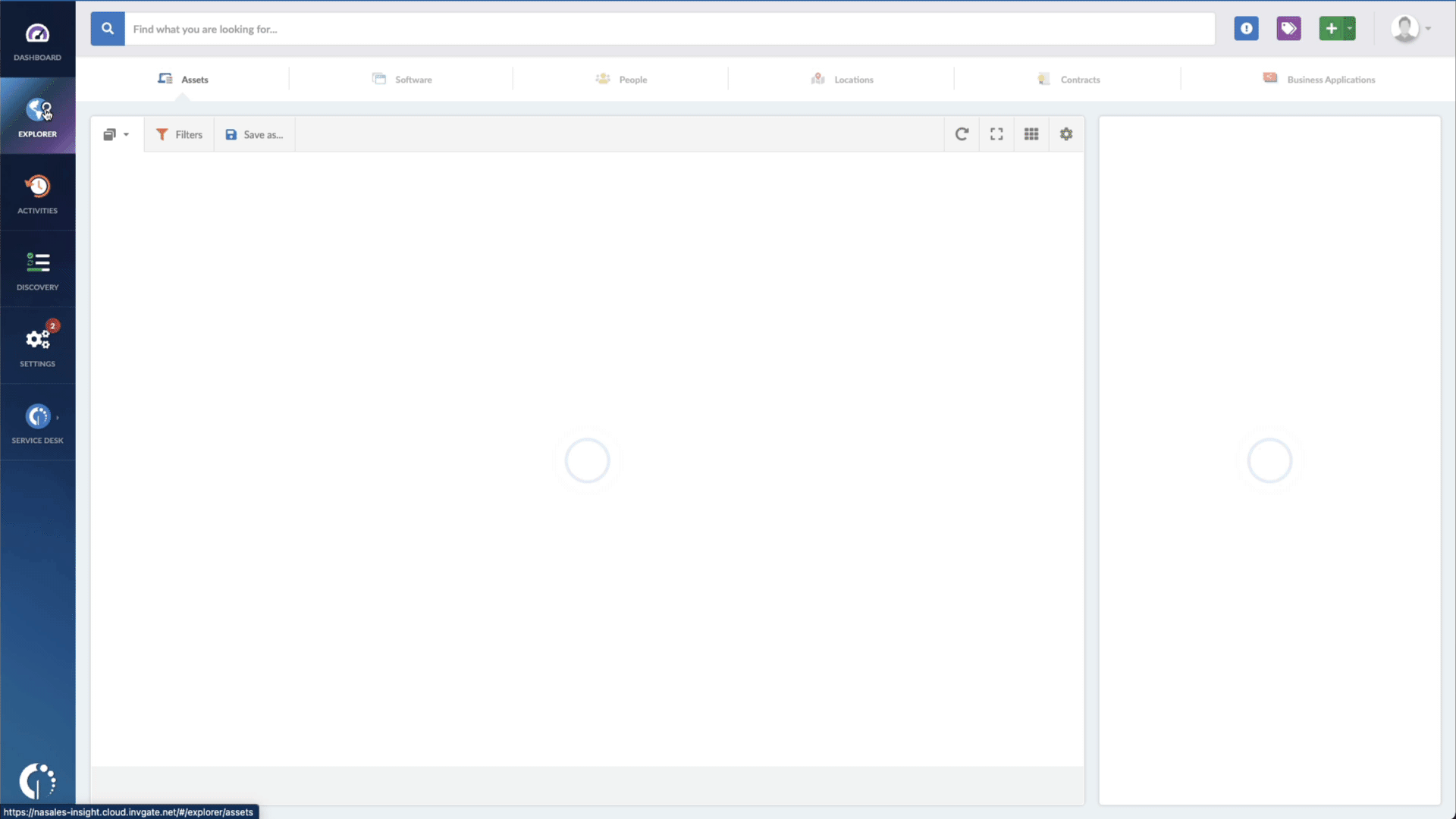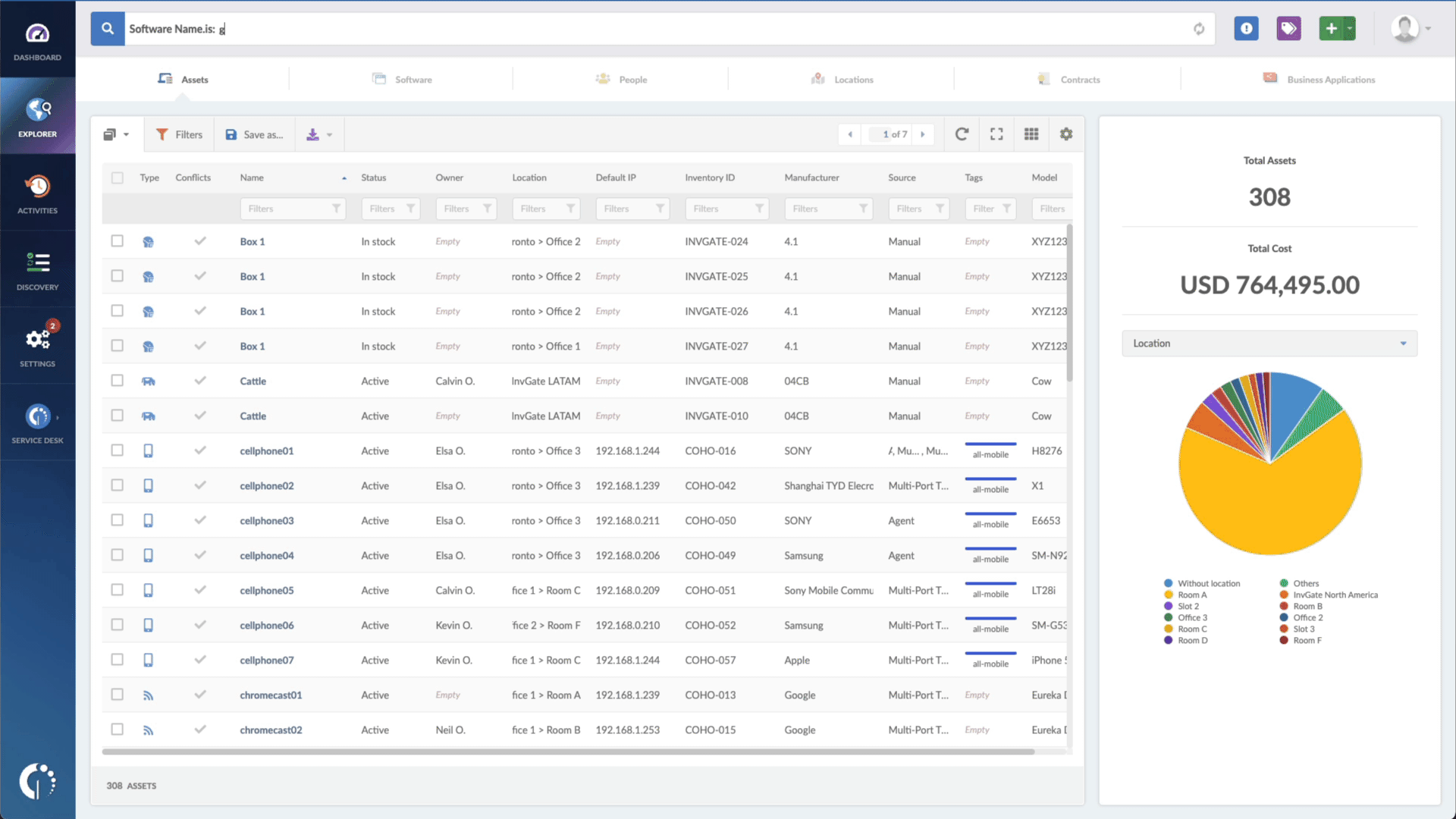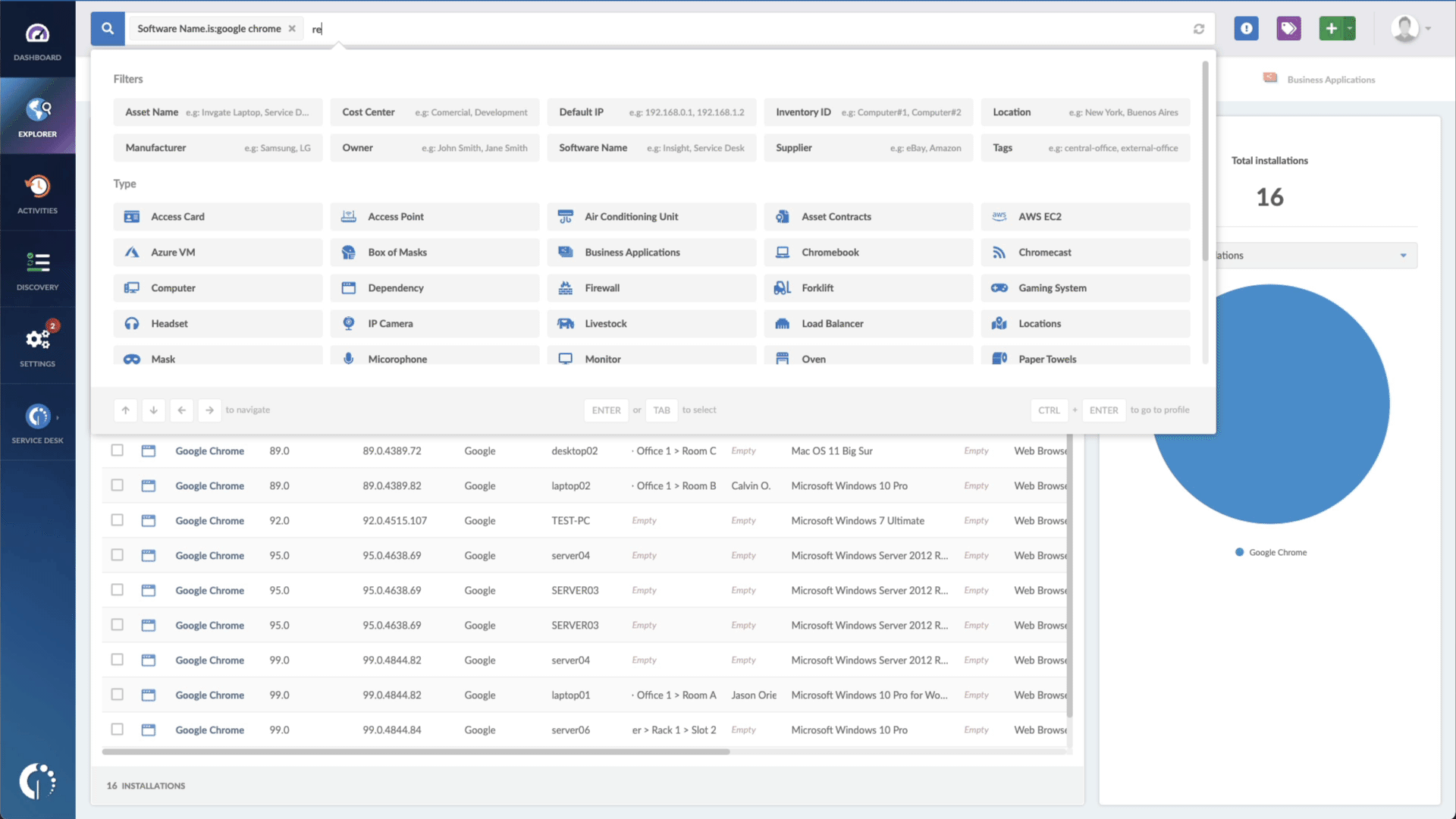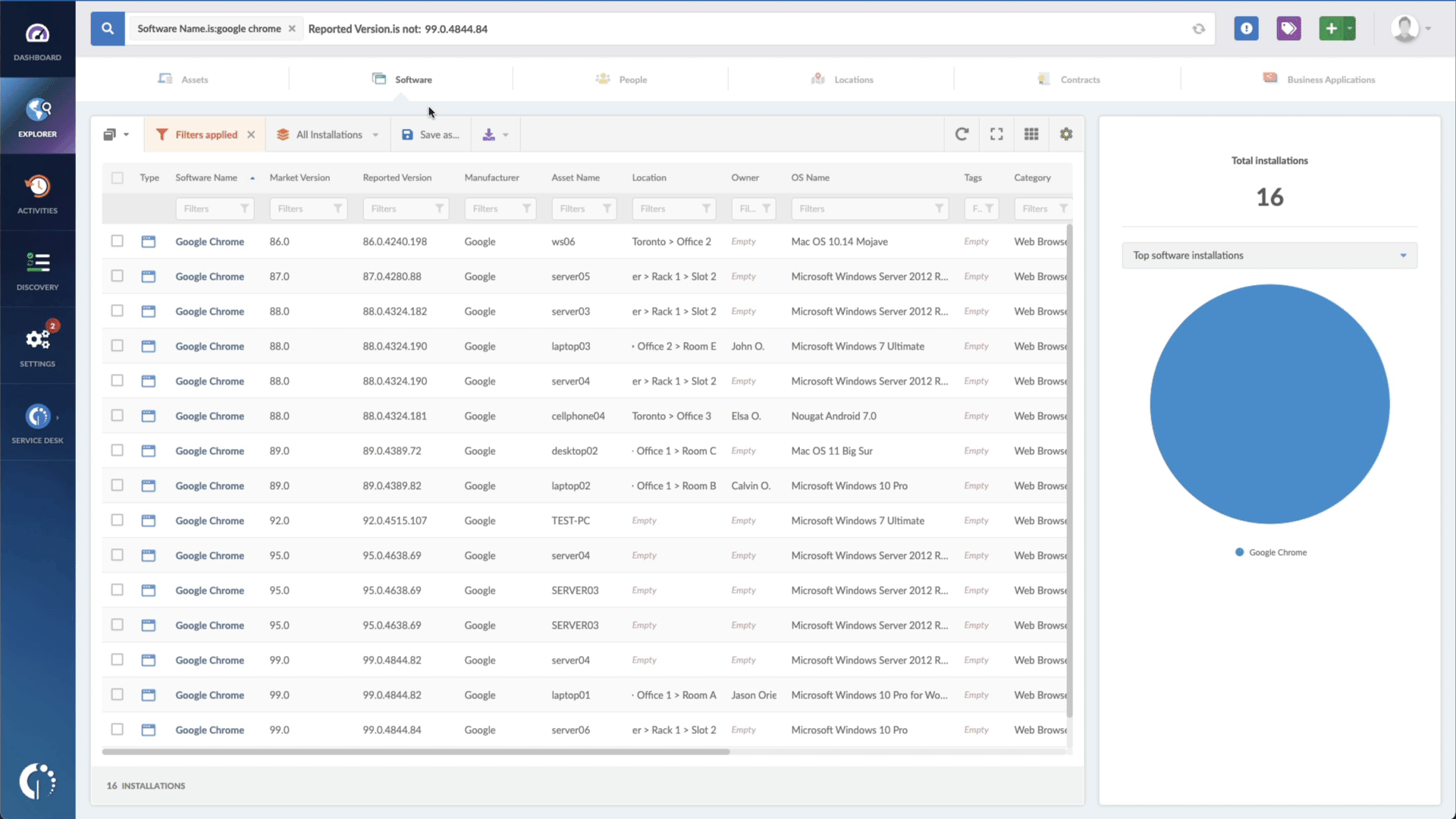
- Type in the Search bar “Software name, is:vm2” to filter all devices with this library.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste vm2’s patched version (3.9.11).
The bottom line
The CVE-2022-36067 vulnerability in the vm2 sandbox library poses a significant risk to systems executing untrusted JavaScript code.
However, with the release of the patched version 3.9.11, users can protect their applications and systems from this security flaw.
To simplify the Patch Management process and identify devices that could be affected by CVE-2022-36067, InvGate Asset Management offers a powerful solution, allowing you to swiftly scan your network and identify devices that may be vulnerable to this particular exploit.
Don't leave your systems exposed to potential threats. Request a 30-day free trial and experience firsthand how InvGate Asset Management enhances the security of your network.