As cybersecurity threats evolve and become more sophisticated, staying vigilant and keeping your systems up-to-date is critical. Recently, a vulnerability in macOS and iOS devices, known as CVE-2022-32917, was discovered.
This vulnerability can allow attackers to control the targeted device completely, making it a significant threat to users' cybersecurity. In this article, we’ll provide an in-depth overview of CVE-2022-32917, including what it is, its associated risks, how to identify devices exposed to it with InvGate Insight, and how to patch them to ensure your systems are secure.
Keep reading if you're concerned about your device's security and want to learn more about CVE-2022-32917!
About CVE-2022-32917
CVE-2022-32917 is a zero-day vulnerability that affects Apple's macOS and iOS operating systems. The vulnerability may allow a malicious application to execute arbitrary code with kernel privileges.
It exists in the XNU kernel, which is used by both macOS and iOS. An attacker can exploit this vulnerability by sending a maliciously crafted audio file to the victim, which could be delivered through email, messaging apps, or any other file transfer.
The risk of not patching this vulnerability is significant as it allows an attacker to control the targeted device completely. Once the attacker has executed arbitrary code with kernel-level privileges, they can steal sensitive data, install malware, and control the device remotely.
Apple has released patches for this vulnerability in its latest macOS and iOS updates: macOS 12.6 (Monterey), macOS 11.7 (Big Sur), iOS 16, iOS 15.7, and iPadOS 15.7.
It is highly recommended that all users update their devices to the latest version as soon as possible to protect them from this vulnerability.
How to find devices exposed to CVE-2022-32917
InvGate Asset Management can quickly and promptly detect any devices that the CVE-2022-32917 vulnerability has impacted. You can take the following steps to achieve this:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:macOS” or “Software name, is:iOS” to filter all Apple devices.
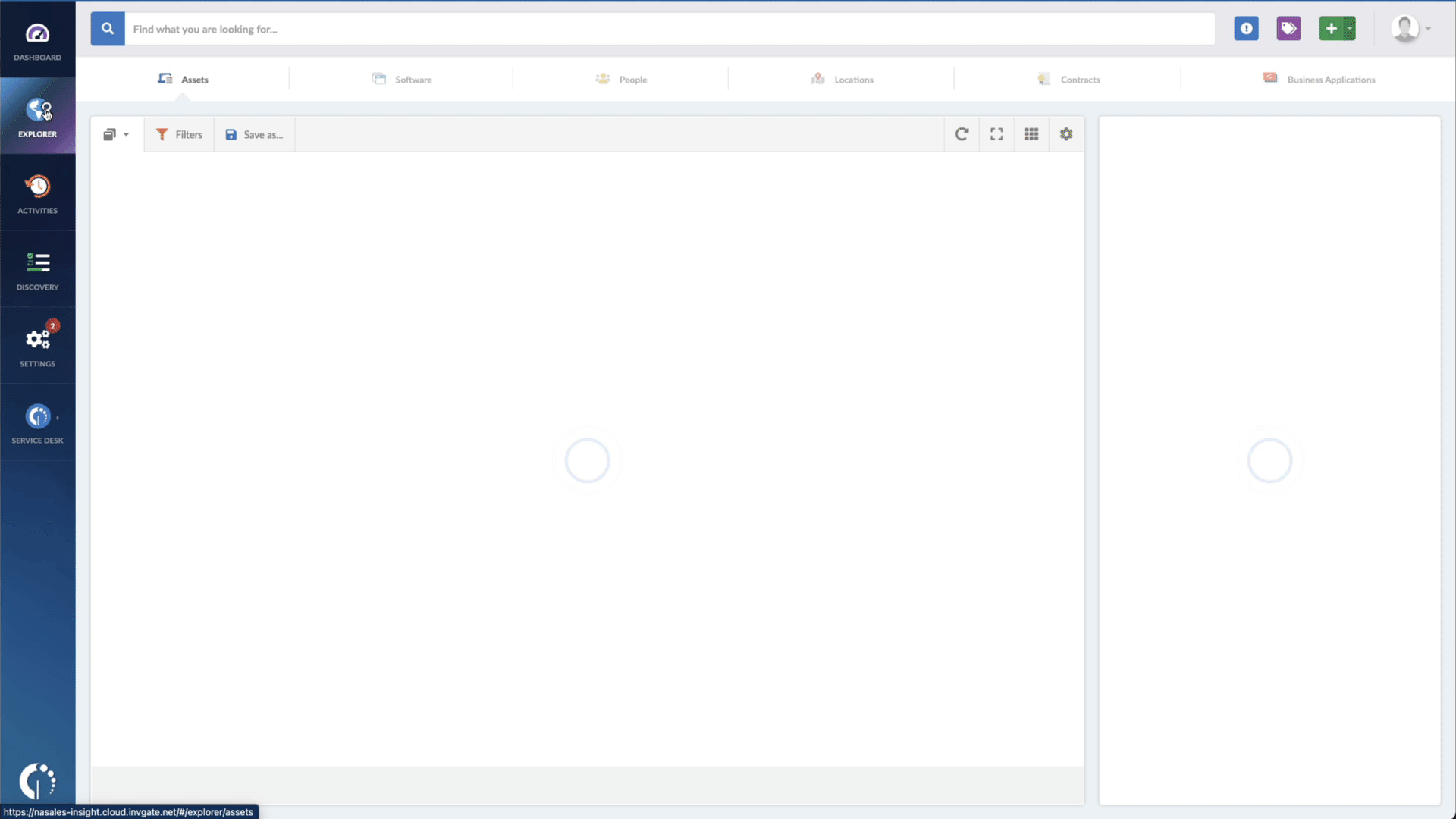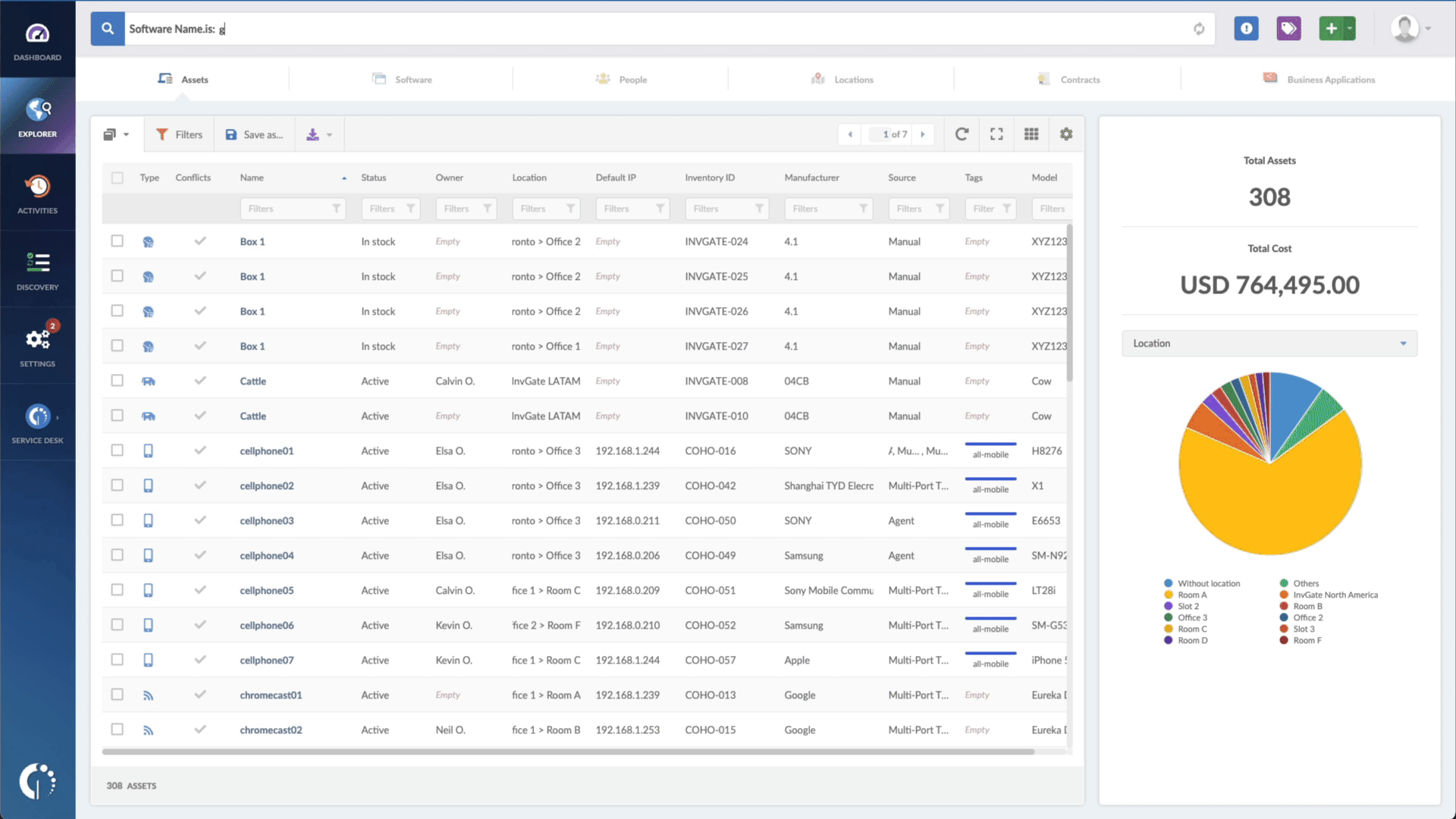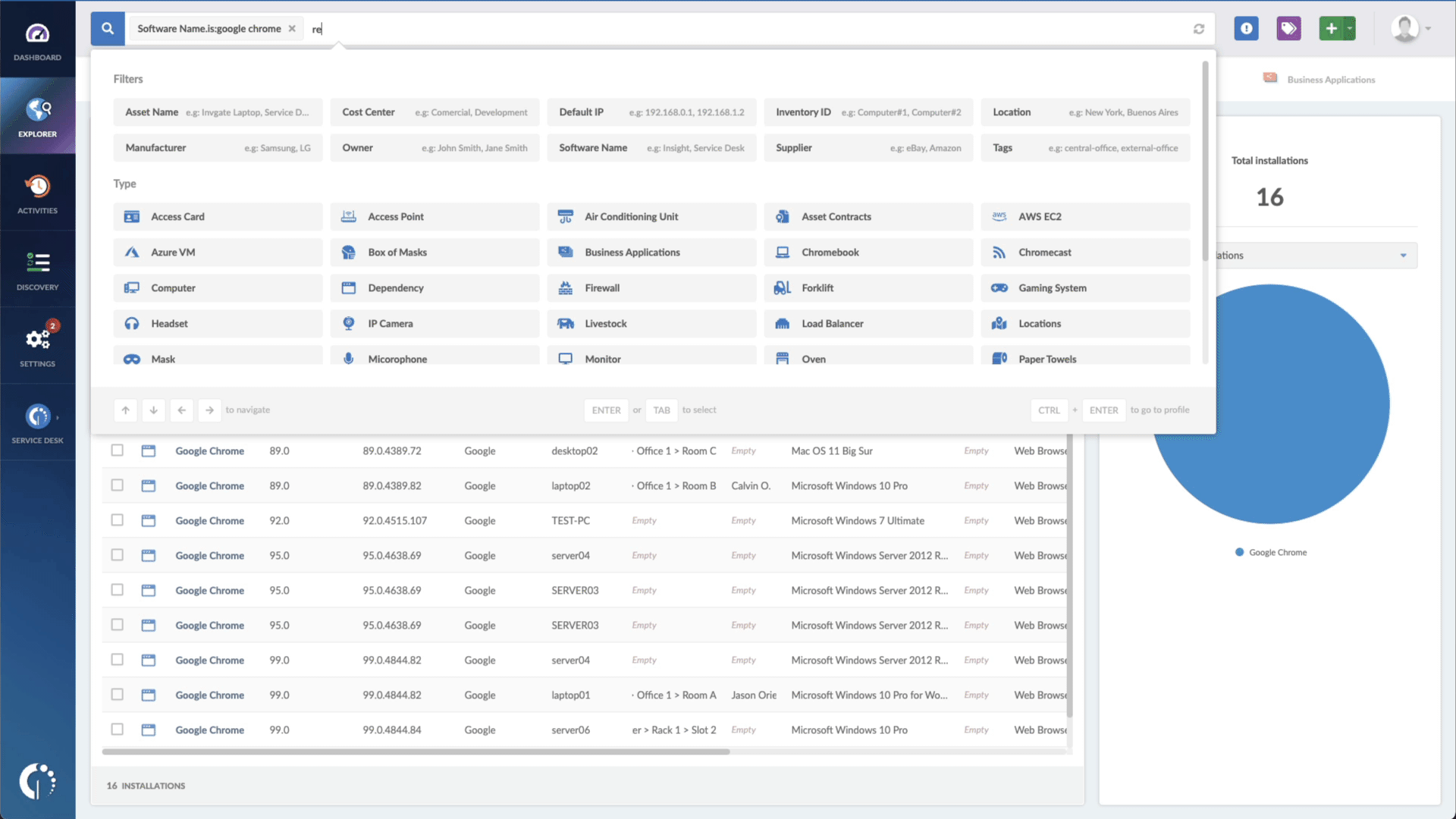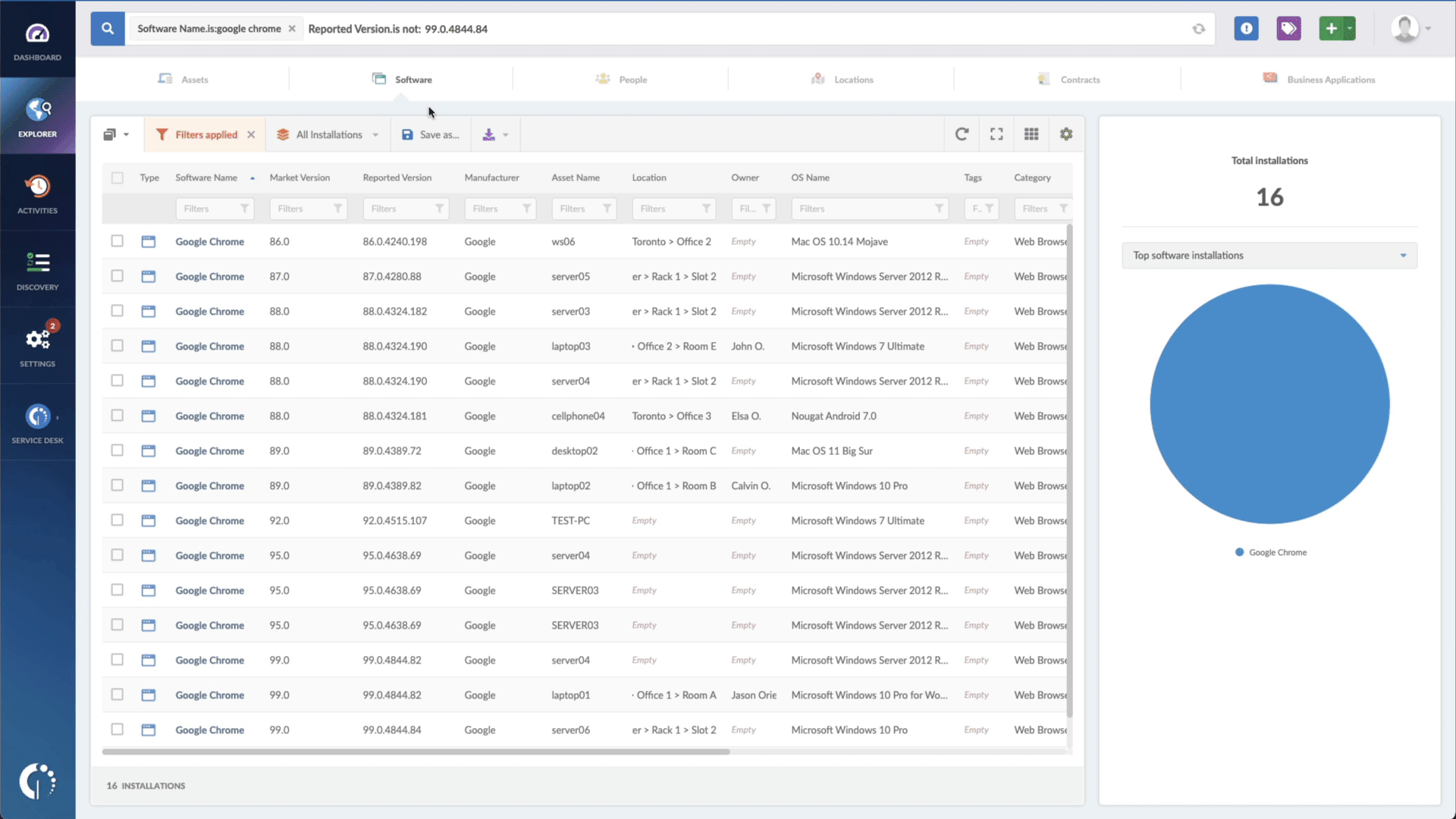
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version - macOS 12.6 (Monterey), macOS 11.7 (Big Sur), iOS 16, and iOS 15.7 and iPadOS 15.7.
The bottom line
The CVE-2022-32917 vulnerability poses a significant threat to macOS and iOS devices, allowing attackers to gain complete control over the targeted device. Users must update their devices to the latest software version, which includes the necessary patch to mitigate this vulnerability. Failure to patch the vulnerability could result in sensitive data loss, malware infections, and remote device control by malicious actors.
InvGate Asset Management simplifies patch management by allowing users to quickly identify any devices that have not been updated to the latest software version, putting them at risk of exploitation.
Request InvGate Asset Management's 30-day free trial today to protect your devices from the latest threats!
















