The vulnerability CVE-2022-32893 poses a significant threat to the privacy and security of users' data, potentially allowing attackers to execute arbitrary code on a vulnerable device. Apple has released security updates to address the issue, but users must take action to protect their devices.
In this blog post, we'll delve into the details of CVE-2022-32893 and explain what the vulnerability is about, its risks, and how InvGate Asset Management can help simplify Patch Management by enabling you to quickly detect any devices impacted by CVE-2022-32893 or other vulnerabilities quickly.
If you're an Apple user, read on to learn more about how you can keep your devices safe and secure!
About CVE-2022-32893
CVE-2022-32893 is a critical vulnerability that affects the iOS, iPadOS, and macOS operating systems. It is a use-after-free vulnerability in the WebKit browser engine that could allow an attacker to execute arbitrary code on a vulnerable device.
If left unpatched, this vulnerability could allow an attacker to execute arbitrary code on a vulnerable device. This could lead to the attacker gaining access to sensitive information or taking control of the device.
Apple has released security updates for iOS, iPadOS, macOS, and Safari to address CVE-2022-32893. The latest versions that include the patch are iOS 15.6.1, iPadOS 15.6.1, and macOS Monterey 12.5.1.
How to find devices exposed to CVE-2022-32893
InvGate Asset Management can help you quickly detect any devices that the CVE-2022-32893 vulnerability has impacted. To do so, you should follow these steps:
- Open InvGate Asset Management and go to the Explorer tab.
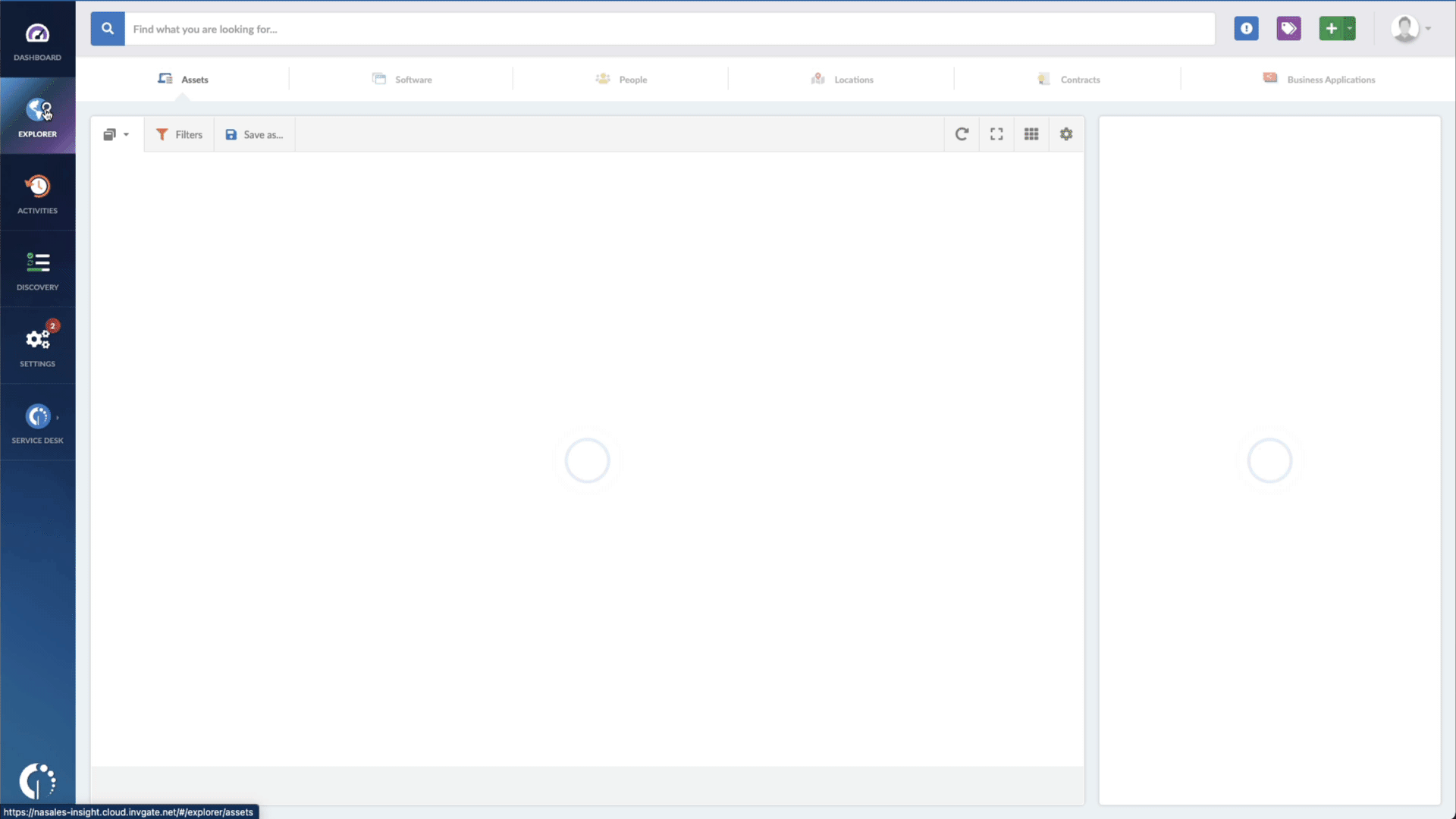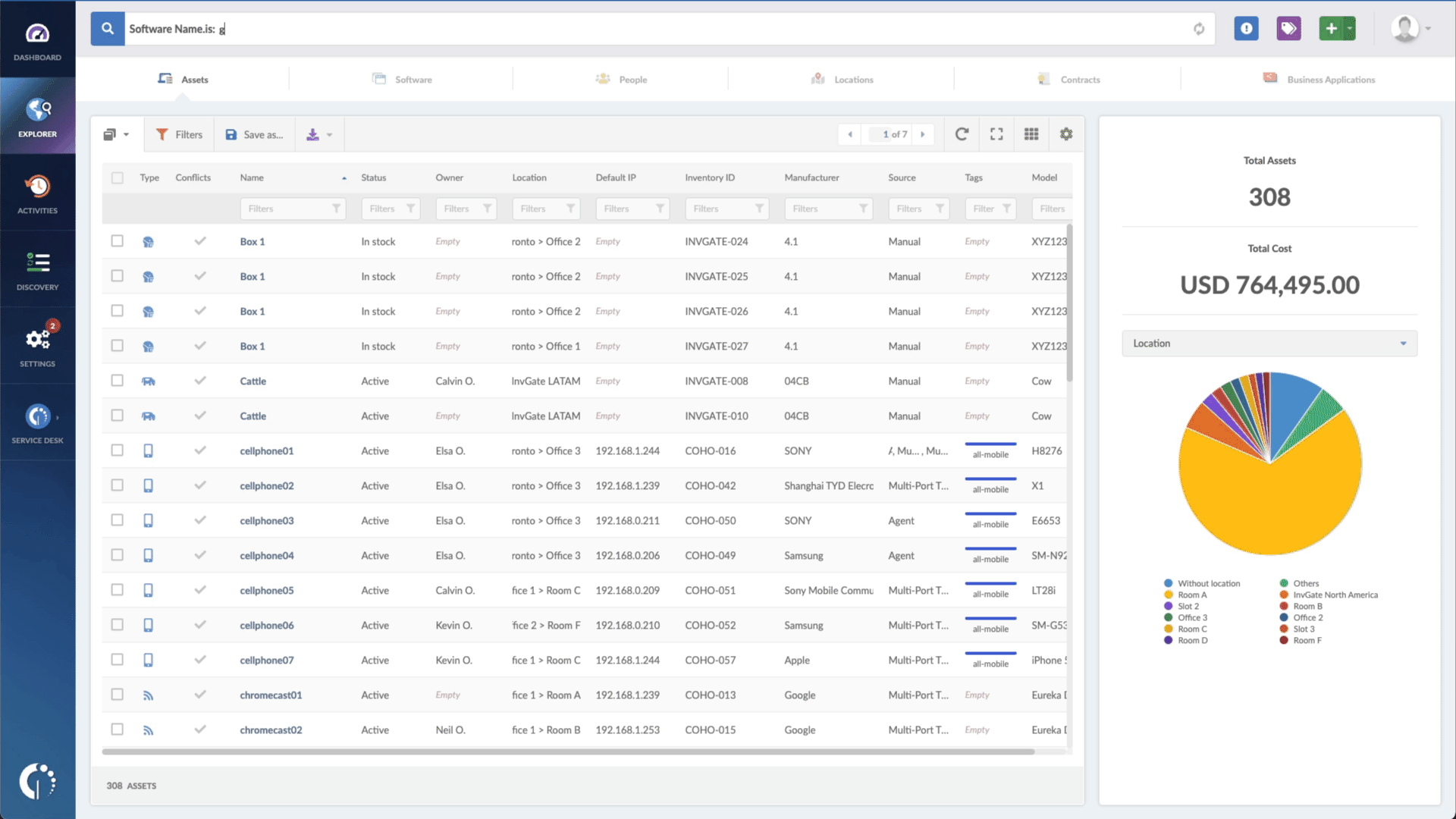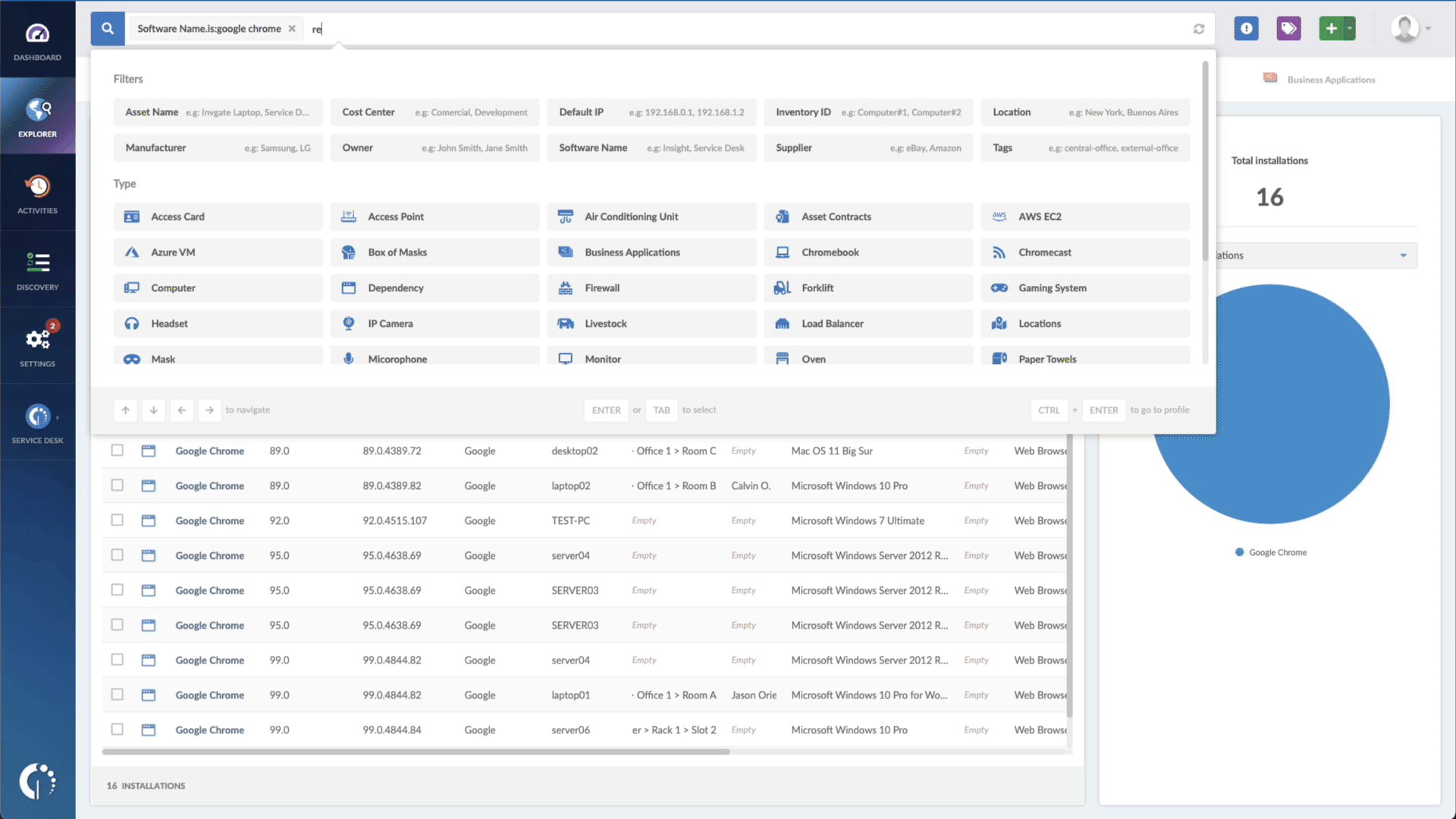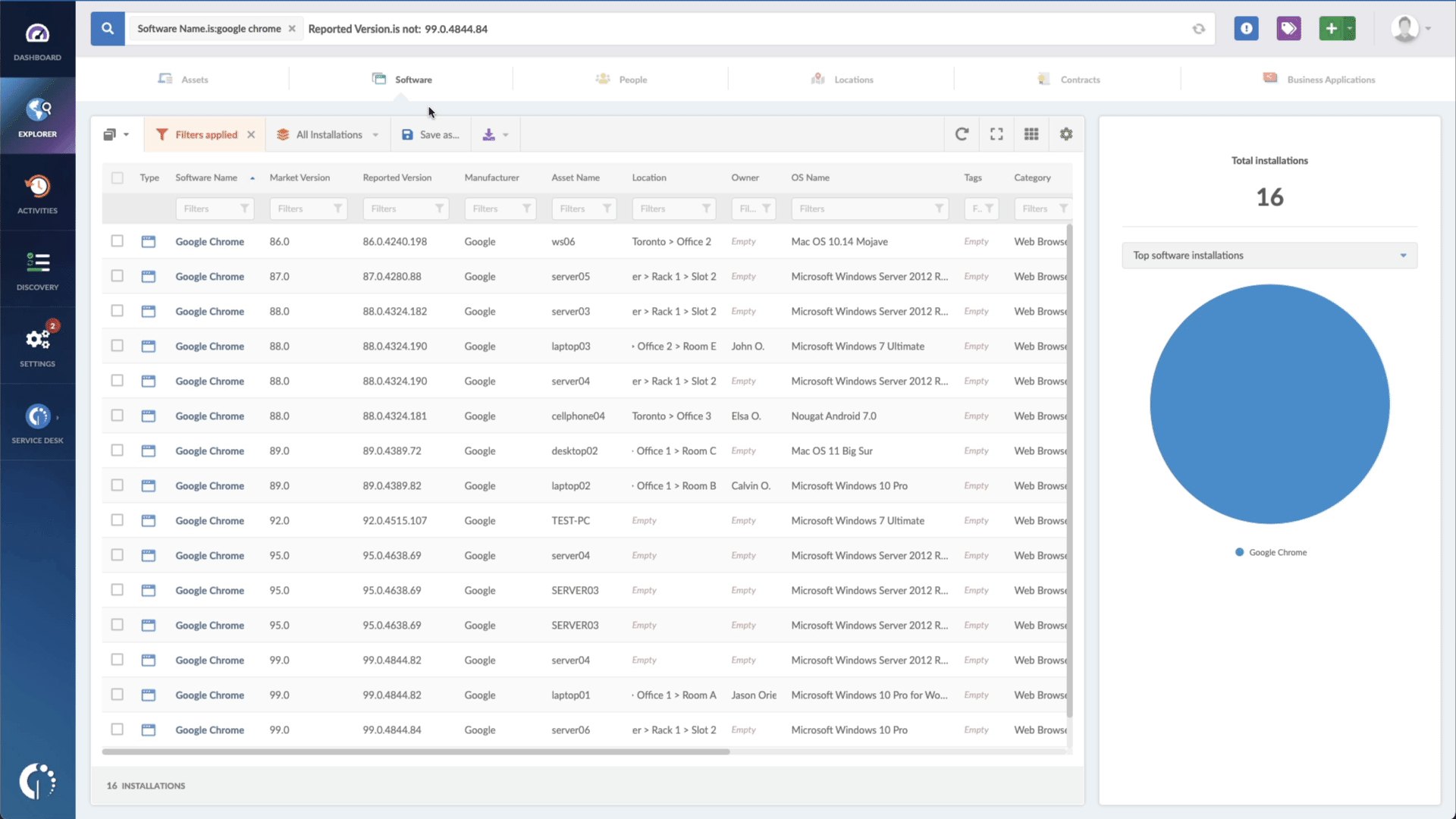
- Type in the Search bar “Software name, is:iOS” (or iPad, or macOS) to filter all Apple devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version (iOS 15.6.1, iPadOS 15.6, and macOS 12.5.1).
Another vulnerability to note
Aside from CVE-2022-32893, there is another critical vulnerability that affects Apple's products, namely CVE-2022-32894. It is an out-of-bounds write issue that was addressed with improved bounds checking. The vulnerability could allow an application to execute arbitrary code with kernel privileges. The kernel privileges are the highest possible privileges, so an attacker could take complete control of a system by exploiting this vulnerability.
Apple has released security updates for iOS, iPadOS, and macOS to address CVE-2022-32894. The issue is fixed in iOS 15.6.1, iPadOS 15.6.1, and macOS Monterey 12.5.1.
The bottom line
CVE-2022-32893 is a critical vulnerability that affects Apple's iOS, iPadOS, and macOS operating systems, posing a significant risk to the privacy and security of users' sensitive information. The vulnerability could allow an attacker to execute arbitrary code on a vulnerable device, leading to the theft of sensitive data or the complete compromise of the device. Therefore, affected device users must update their software to the latest versions that include the patch (iOS 15.6.1, iPadOS 15.6.1, and macOS Monterey 12.5.1).
The good news is that InvGate Asset Management can help simplify Patch Management by enabling users to quickly detect any devices that have been impacted by CVE-2022-32893 or any other vulnerabilities.
If you're concerned that your devices may be vulnerable to CVE-2022-32893 or other security risks, we recommend trying InvGate Asset Management's 30-day free trial. By doing so, you can explore the platform's capabilities and easily search for vulnerable devices in your network. Don't wait until it's too late – take action today to protect your devices and your data!