In today's interconnected world, network security plays a pivotal role in safeguarding sensitive data and mitigating cyber threats. However, vulnerabilities can emerge, compromising the effectiveness of security systems. One such vulnerability that requires immediate attention is CVE-2022-3236, affecting Sophos Firewall.
In this article, we’ll delve into the details of CVE-2022-3236, its potential risks, and how InvGate Asset Management simplifies the Patch Management process.
Read on to learn more about this critical vulnerability and how you can protect your systems effectively.
About CVE-2022-3236
CVE-2022-3236 is a code injection vulnerability in the Sophos Firewall User Portal and Webadmin. It affects all versions of Sophos Firewall v19.0 MR1 (19.0.1) and older.
An attacker can exploit this vulnerability to execute arbitrary code on the affected firewall.
The vulnerability exists in the way that the Sophos Firewall handles user-supplied input. When an attacker sends a specially crafted request to the User Portal or Webadmin, they can trick the firewall into executing arbitrary code.
What are CVE-2022-3236 risks?
An attacker could use this vulnerability to gain full control of the affected firewall, allowing them to steal sensitive data, disrupt operations, or even take the firewall offline.
Is CVE-2022-3236 fixed?
Yes, Sophos has released a patch for CVE-2022-3236, and users should install it as soon as possible to protect their systems from this vulnerability.
According to the Sophos Security Advisory, the following versions have been patched for the CVE-2022-3236 vulnerability:
- v18.0 MR3, MR4, MR5, and MR6
- v17.5 MR12, MR13, MR14, MR15, MR16, and MR17
- v17.0 MR10
- v18.5 MR5 (18.5.5)
- v19.0 MR2 (19.0.2)
- v19.5 GA1
How to find devices exposed to CVE-2022-3236
To quickly detect devices that are impacted by the CVE-2022-3236 vulnerability, InvGate Asset Management offers an efficient solution. Follow these instructions:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Sophos Firewall” to filter all devices with this software.
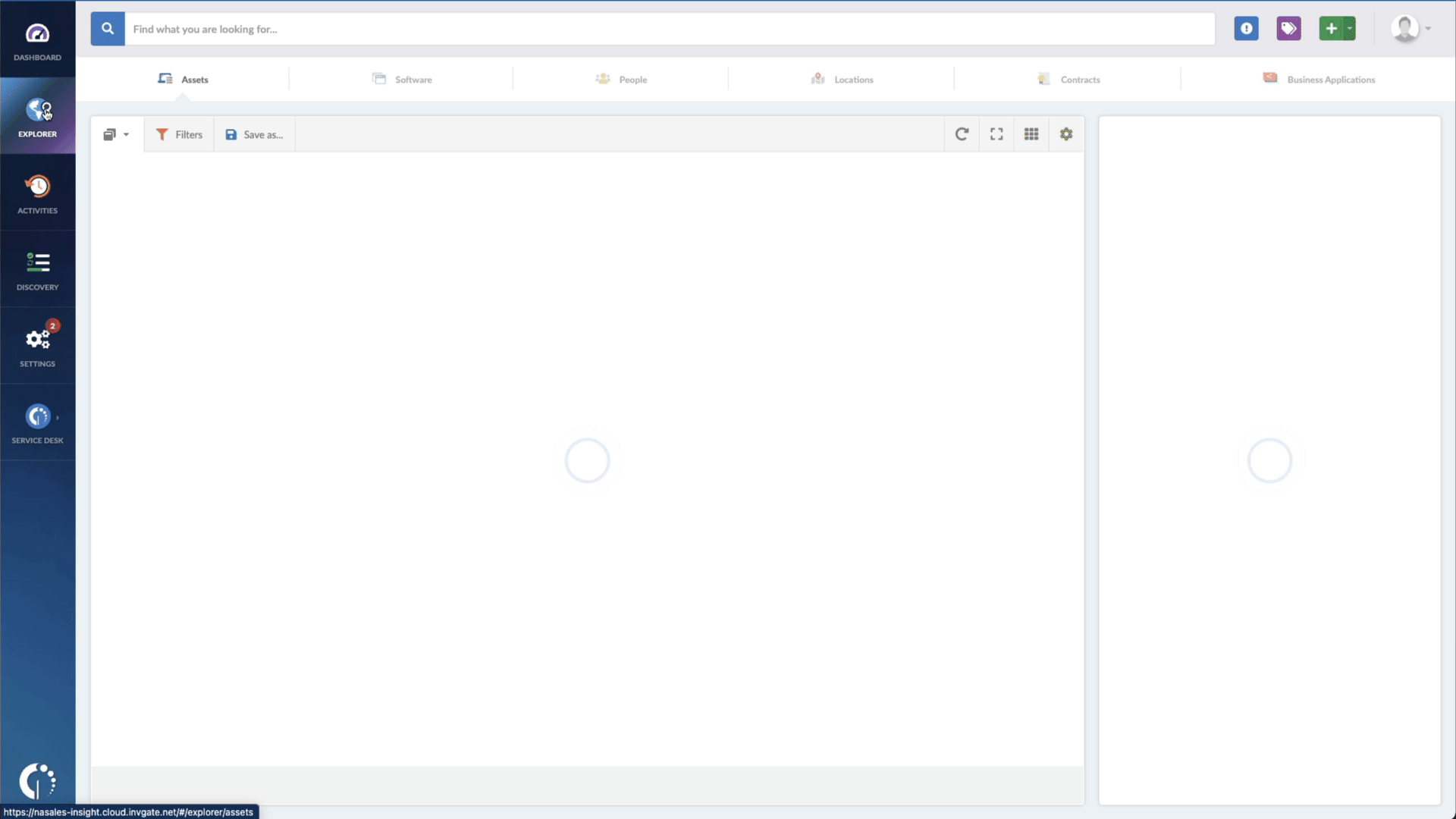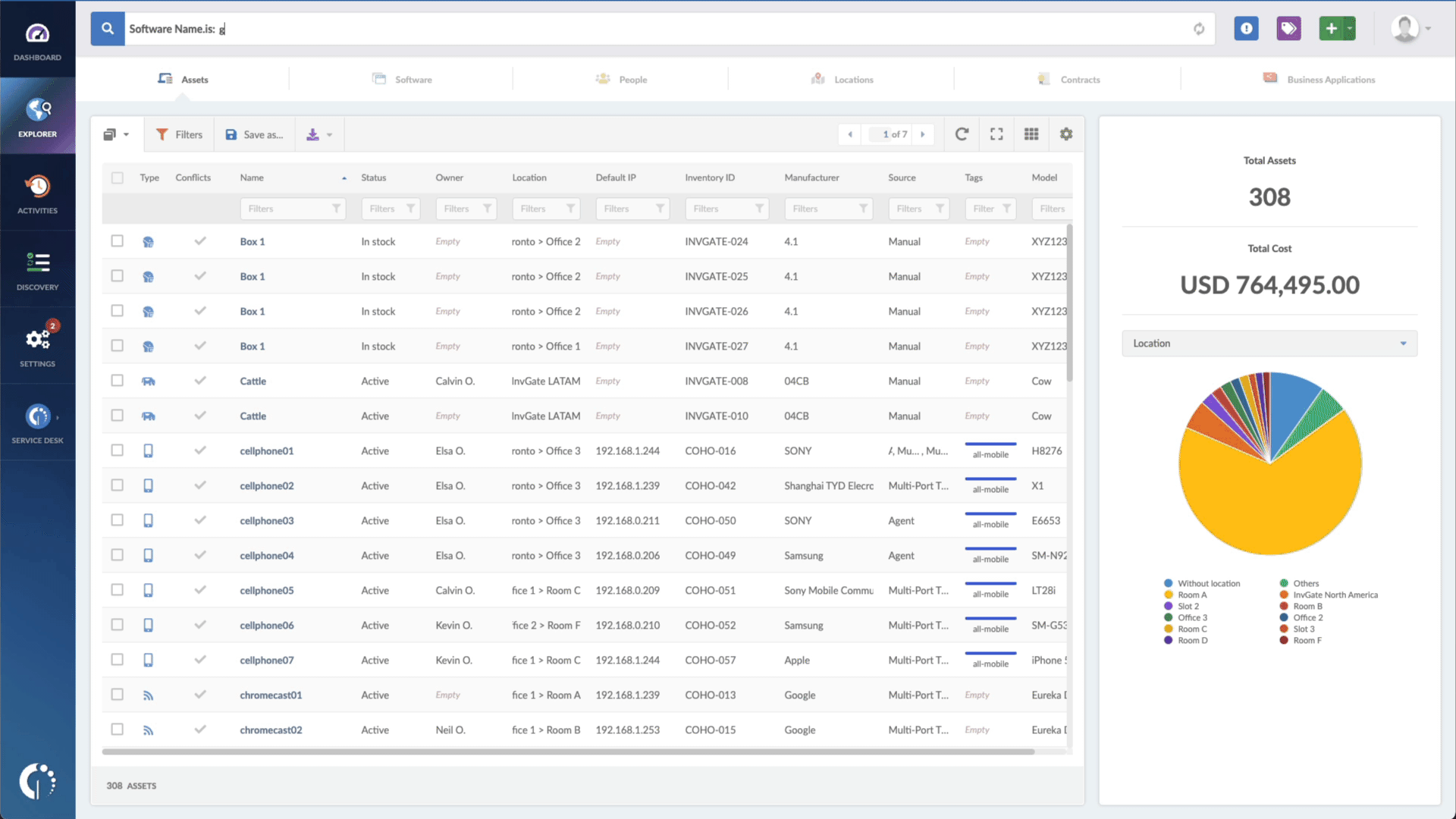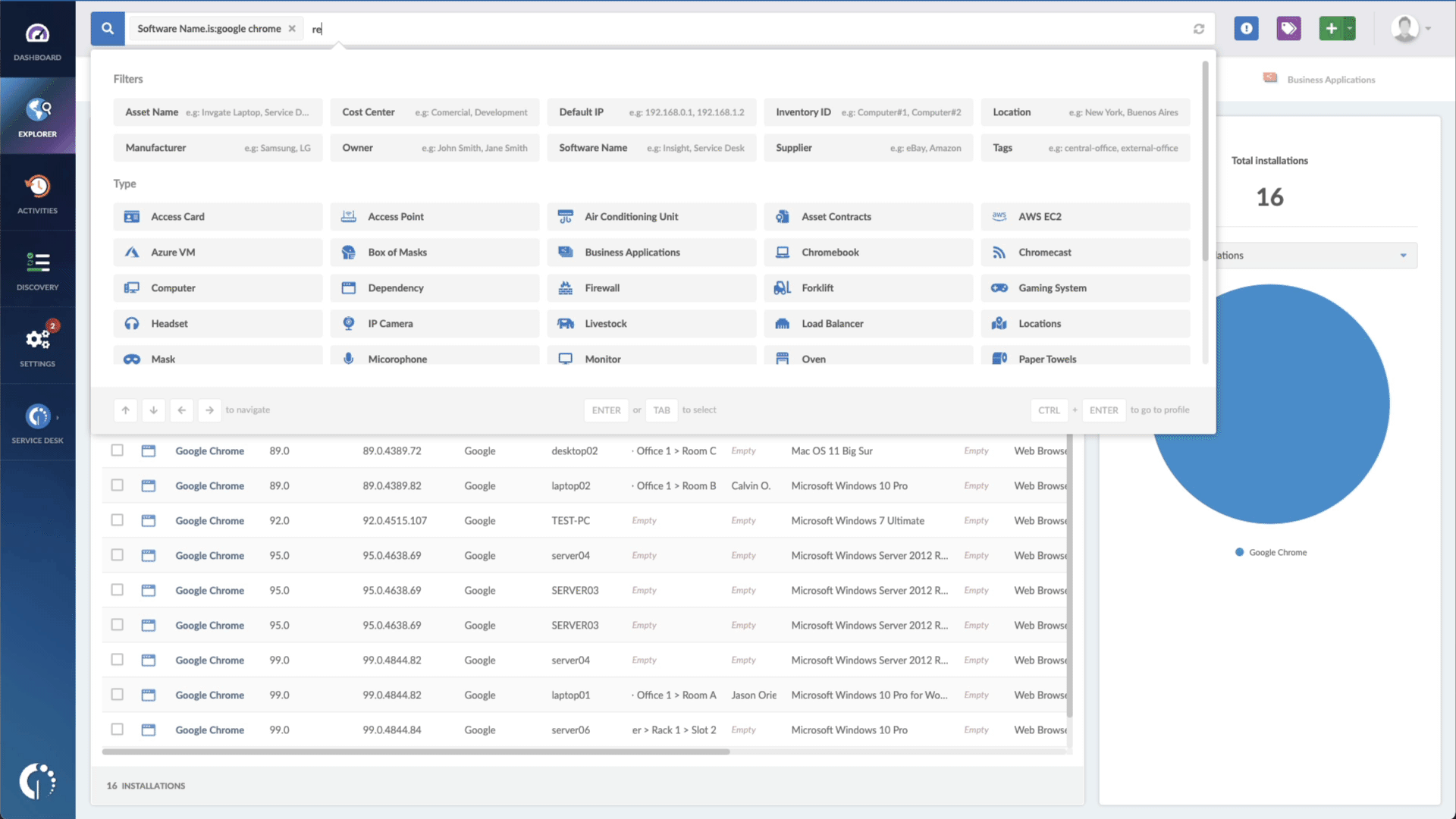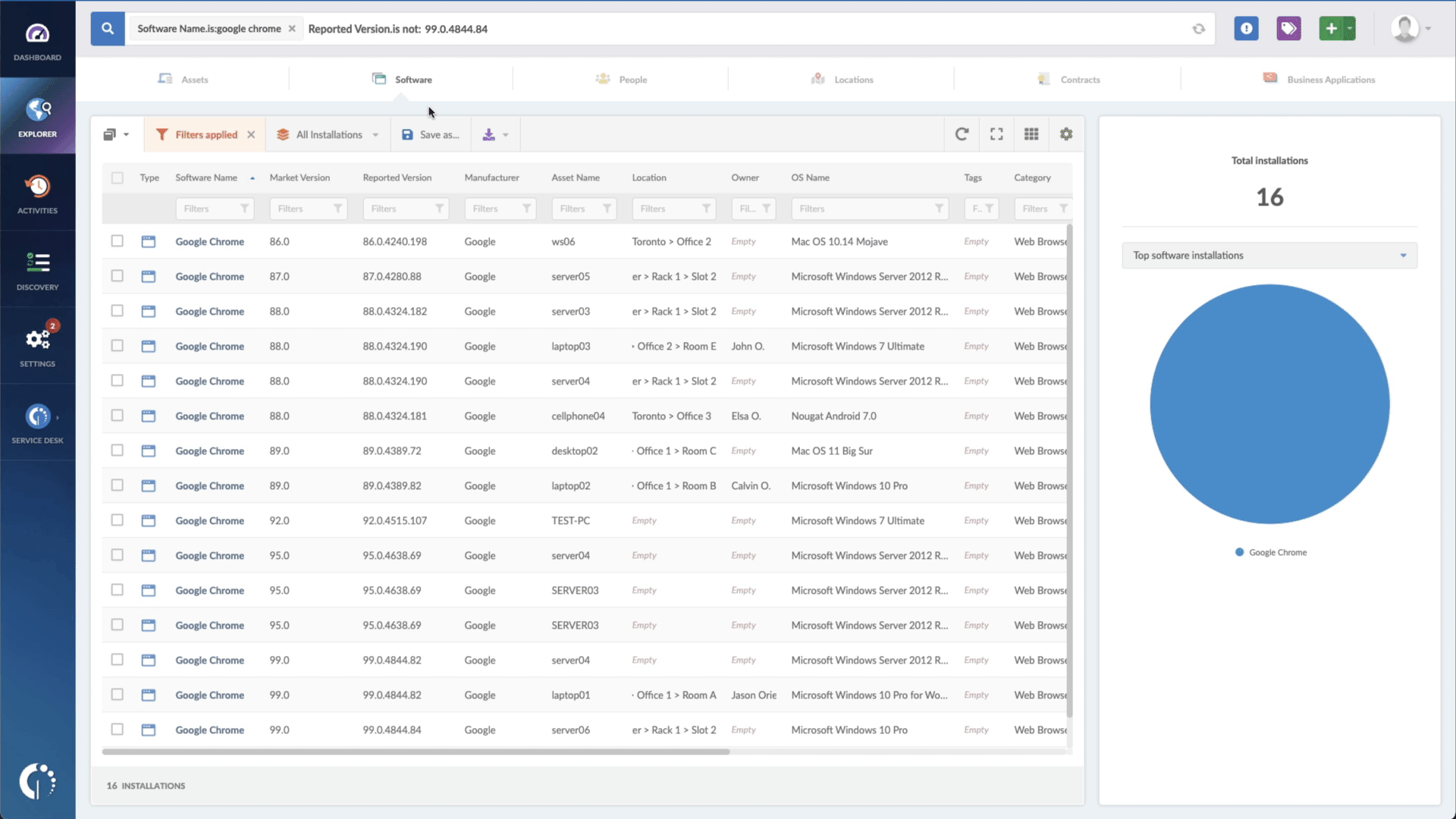
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Sophos’ patched version (mentioned above).
The bottom line
The CVE-2022-3236 vulnerability in Sophos Firewall exposes organizations to significant risks, including unauthorized code execution and potential network compromise. To safeguard against this threat, it is crucial to apply the patch provided by Sophos promptly.
InvGate Asset Management offers a valuable solution for organizations seeking to efficiently manage the patching process and identify devices vulnerable to CVE-2022-3236. By leveraging InvGate Asset Management's capabilities, users can swiftly detect and assess the impact of this vulnerability across their network infrastructure.
To experience the benefits of InvGate Asset Management firsthand, request a 30-day free trial today. Take proactive measures to enhance your network's security and protect against potential exploits!
















