In the ever-evolving landscape of cybersecurity, it is vital for organizations to remain vigilant against potential vulnerabilities and ensure the protection of their critical systems and data. One such vulnerability, known as CVE-2022-31706, has recently been identified in VMware vRealize Log Insight, a popular log management and analysis solution.
The exploit poses serious risks to the security of log files and sensitive information stored within the system. To address this critical issue, VMware has released an official statement regarding the vulnerability, emphasizing the urgency of patching and safeguarding your log management infrastructure.
In this article, we’ll delve into the details of CVE-2022-31706, its implications, and how InvGate Asset Management can simplify Patch Management.
Ready to learn more? Let's dive in and ensure the safety of your log management environment.
About CVE-2022-31706
CVE-2022-31706 is a directory traversal vulnerability in VMware vRealize Log Insight. It affects all versions of vRealize Log Insight up to and including 7.4.2.
An unauthenticated attacker can exploit this vulnerability to inject arbitrary files into the affected appliance, which could lead to remote code execution.
The vulnerability exists in the way that vRealize Log Insight handles user-supplied input. When an attacker sends a specially crafted request to the appliance, they can trick the appliance into writing arbitrary files to a writable directory. This could then be used to execute malicious code on the appliance.
What are CVE-2022-31706 risks?
The risks of CVE-2022-31706 are significant. An attacker could use this vulnerability to gain full control of an affected appliance, which could allow them to steal sensitive data, disrupt operations, or even take the appliance offline.
Is CVE-2022-31706 fixed?
Yes, VMware has released a patch for CVE-2022-31706 and ssers should install it as soon as possible to protect their systems from this vulnerability. The latest version that includes the patch is v8.10.2.
Here are some additional tips for protecting your systems from CVE-2022-31706:
- Keep your software up to date.
- Use strong passwords and enable multi-factor authentication.
- Be careful about what websites you visit and what files you open.
- Use a firewall and antivirus software.
- Back up your data regularly.
- By following these tips, you can help to protect your systems from CVE-2022-31706 and other vulnerabilities.
How to find devices exposed to CVE-2022-31706
To quickly detect devices that are impacted by the CVE-2022-31706 vulnerability, InvGate Asset Management provides an efficient solution. Follow the steps below to initiate the process:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:vRealize Log Insight” to filter all devices with this software.
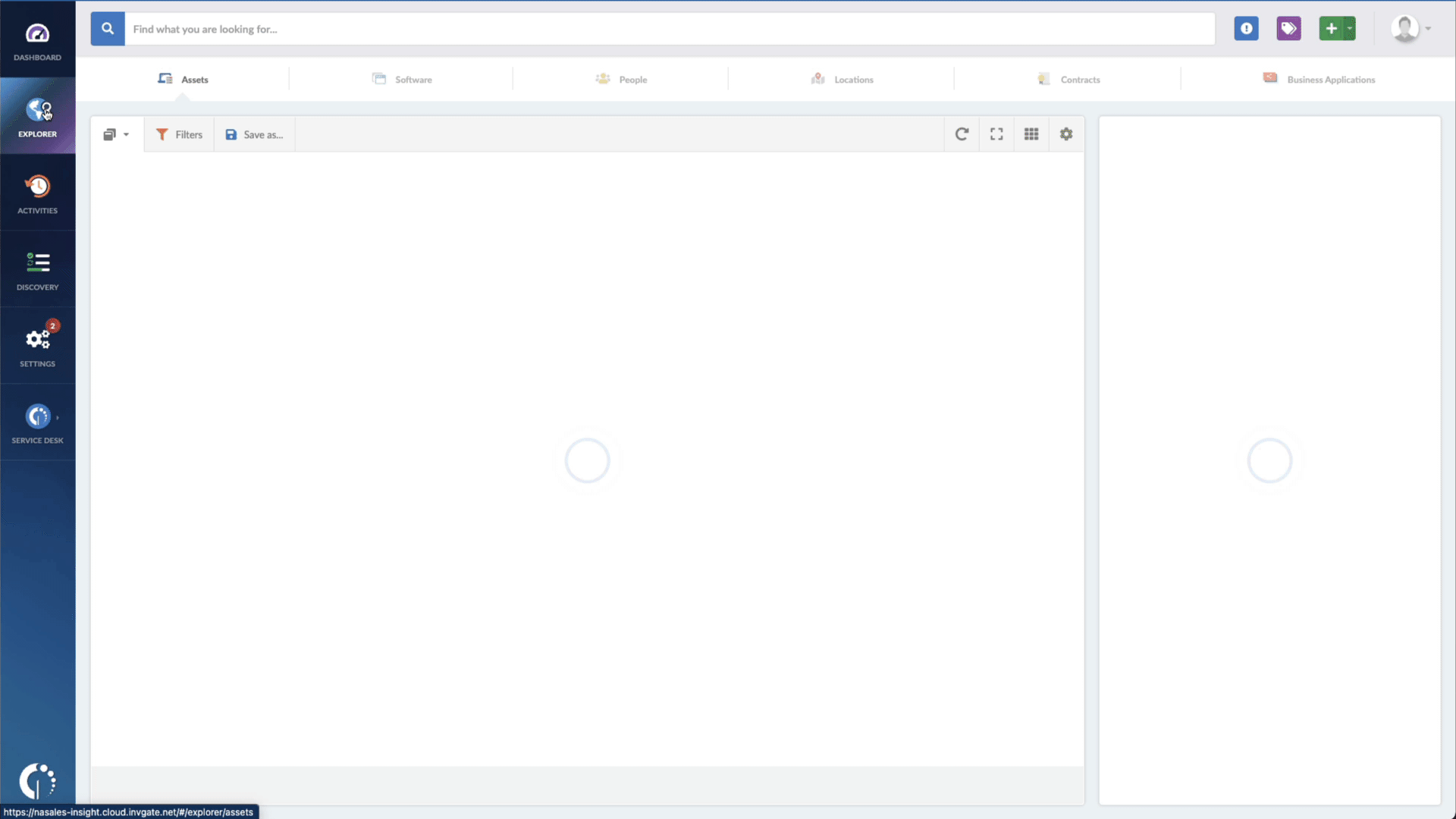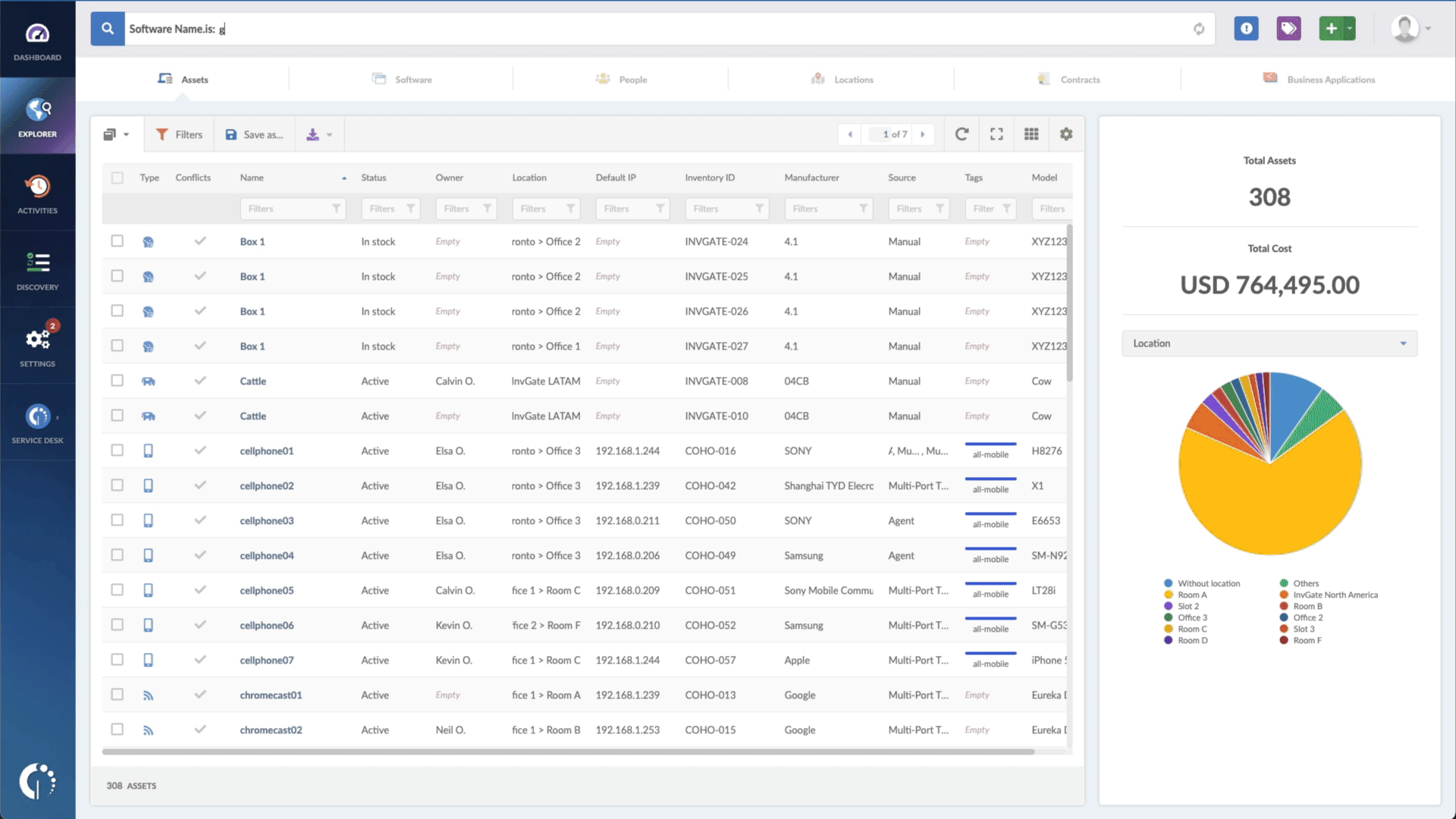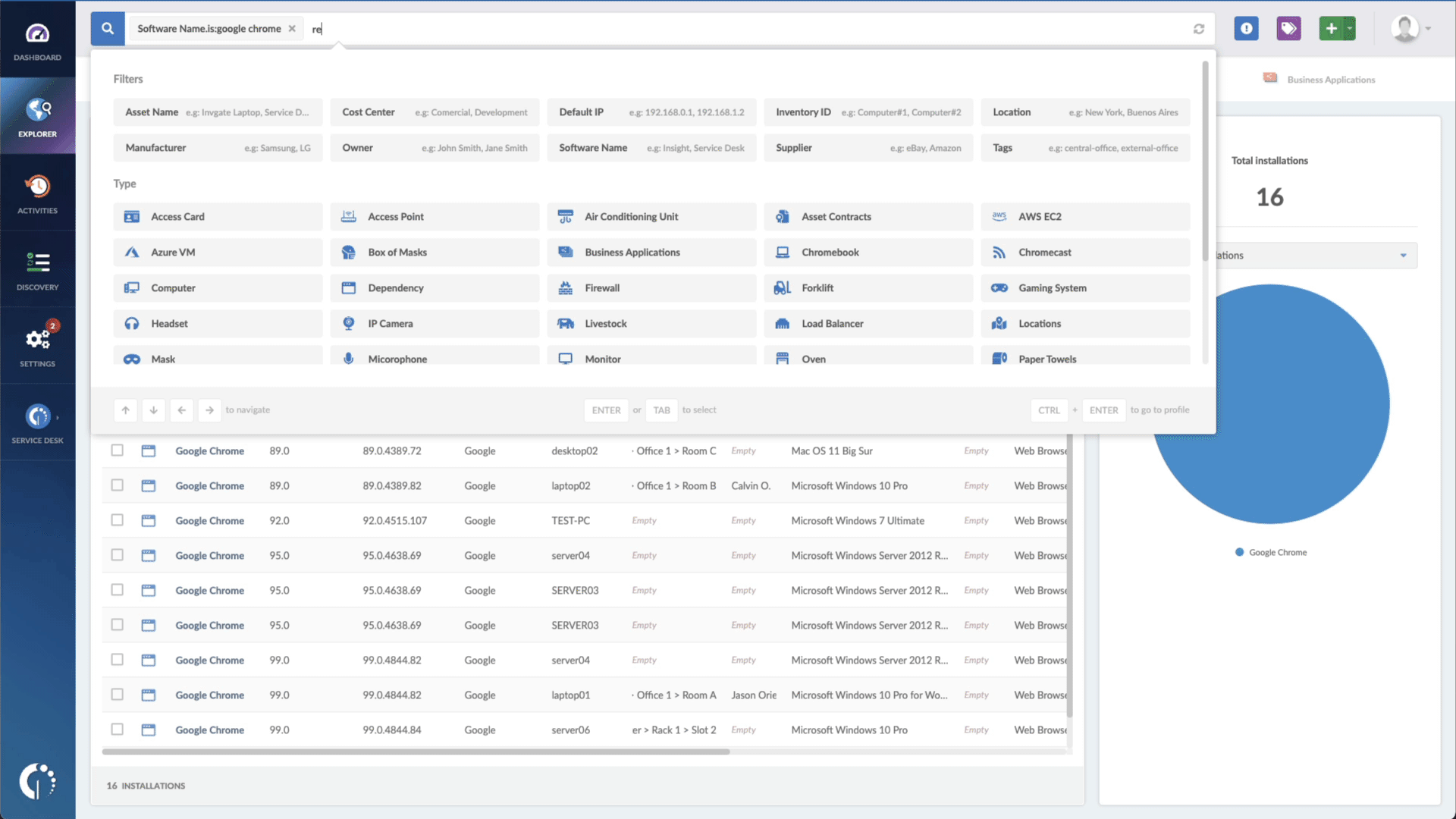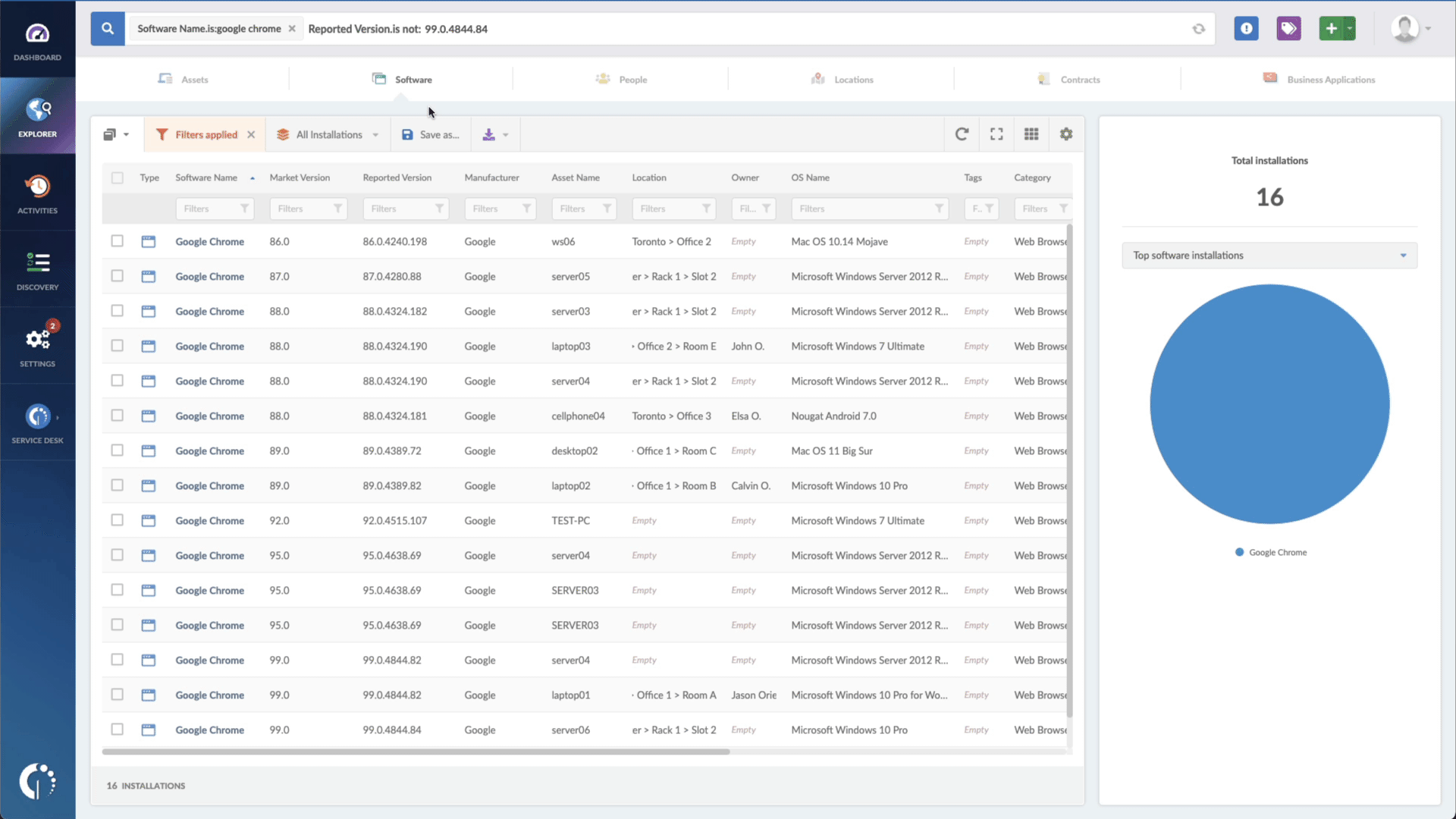
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste VMware’s patched version (v8.10.2).
The bottom line
The CVE-2022-31706 vulnerability in VMware vRealize Log Insight poses a significant risk to organizations utilizing this log management solution. It allows unauthorized access to sensitive log files and can potentially lead to the exposure of critical information. To mitigate these risks, it is essential to promptly patch the software. The latest version, 8.10.2, includes the necessary fixes to address this vulnerability.
Managing patches across a network of devices can be a complex task, but InvGate Asset Management offers a streamlined solution. With InvGate Asset Management, organizations can swiftly identify devices affected by CVE-2022-31706 and other vulnerabilities, simplifying the patch management process.
To experience the capabilities of InvGate Asset Management firsthand, request a 30-day free trial. Don't leave your log management vulnerable to exploitation—take proactive steps to protect your data and systems.