Informed on April 2022, the CVE-2022-29799 vulnerability in the networkd-dispatcher service has the potential to compromise Linux systems. It exposes the systems to arbitrary command execution by exploiting flaws in file path handling.
In this article, we’ll provide an overview of CVE-2022-29799, its implications, and how InvGate Asset Management simplifies the Patch Management process and secures affected systems.
Read on to learn more about the risks, mitigation steps, and effective vulnerability management with InvGate Asset Management.
About CVE-2022-29799
CVE-2022-29799 is a directory traversal vulnerability in the networkd-dispatcher service. This vulnerability allows an attacker to execute arbitrary commands on the system by exploiting a flaw in the way that networkd-dispatcher handles file paths.
How does CVE-2022-29799 work?
The vulnerability exists because the networkd-dispatcher service does not properly sanitize file paths that are passed to it. This flaw allows an attacker to specify a path that is outside of the "/etc/networkd-dispatcher" base directory. If the attacker successfully exploits this vulnerability, they can execute arbitrary commands on the system with the privileges of the networkd-dispatcher service.
The networkd-dispatcher is a Linux service that manages network events and triggers scripts or actions in response to changes in network configuration. It works with systemd-networkd to handle network devices and connections.
What are CVE-2022-29799 risks?
If a system is not patched for CVE-2022-29799, an attacker could exploit the vulnerability to execute arbitrary commands on the system, allowing them to take control of the system, steal data, or install malware.
Is CVE-2022-29799 fixed?
Yes, the vulnerability can be mitigated by updating the Linux systems to the latest version of the software.
How to find devices exposed to CVE-2022-29799
Using InvGate Asset Management, you can quickly determine which devices are impacted by the CVE-2022-29799 vulnerability. Here's a guide on how to proceed:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Linux” to filter all Linux devices.
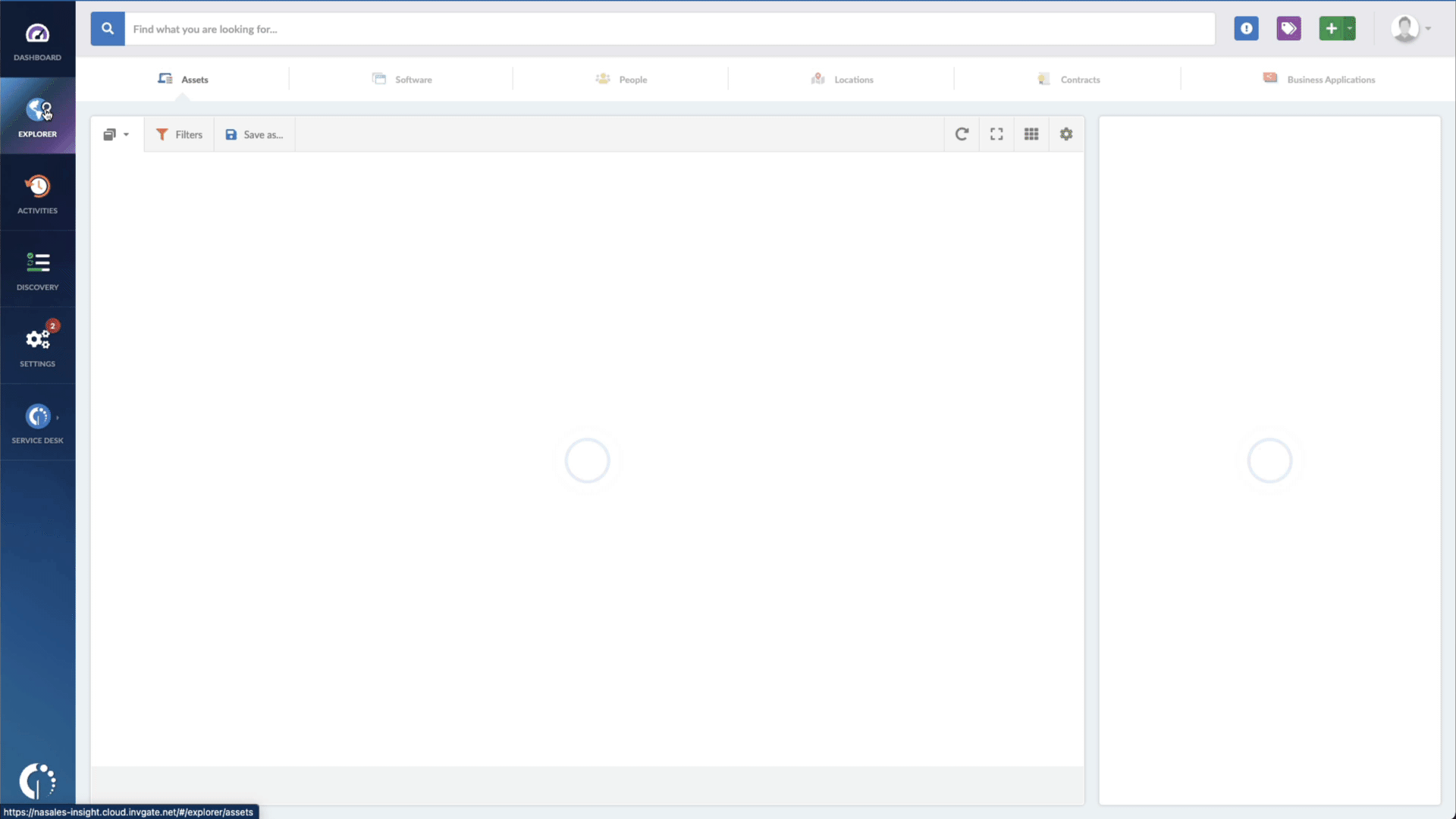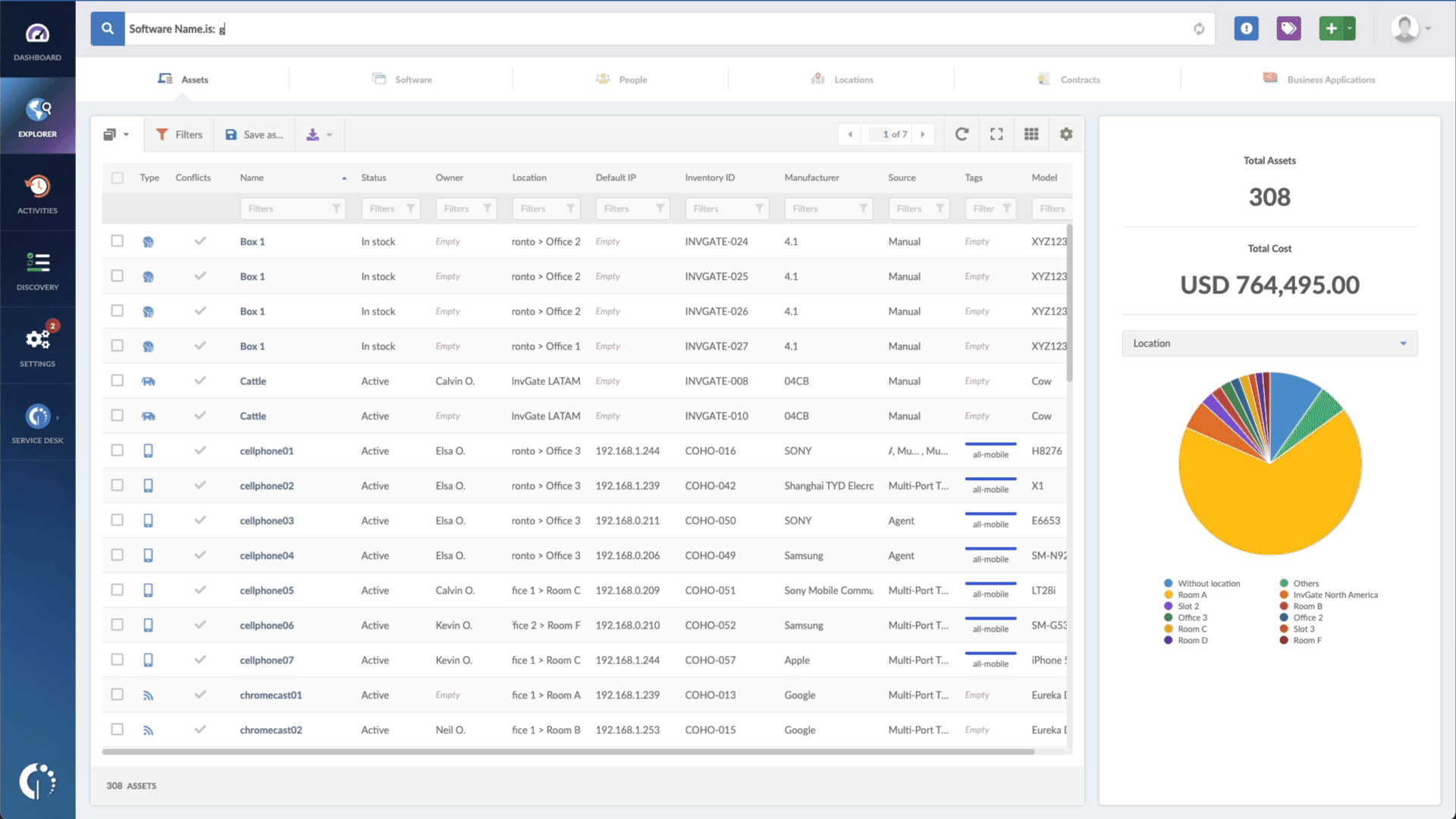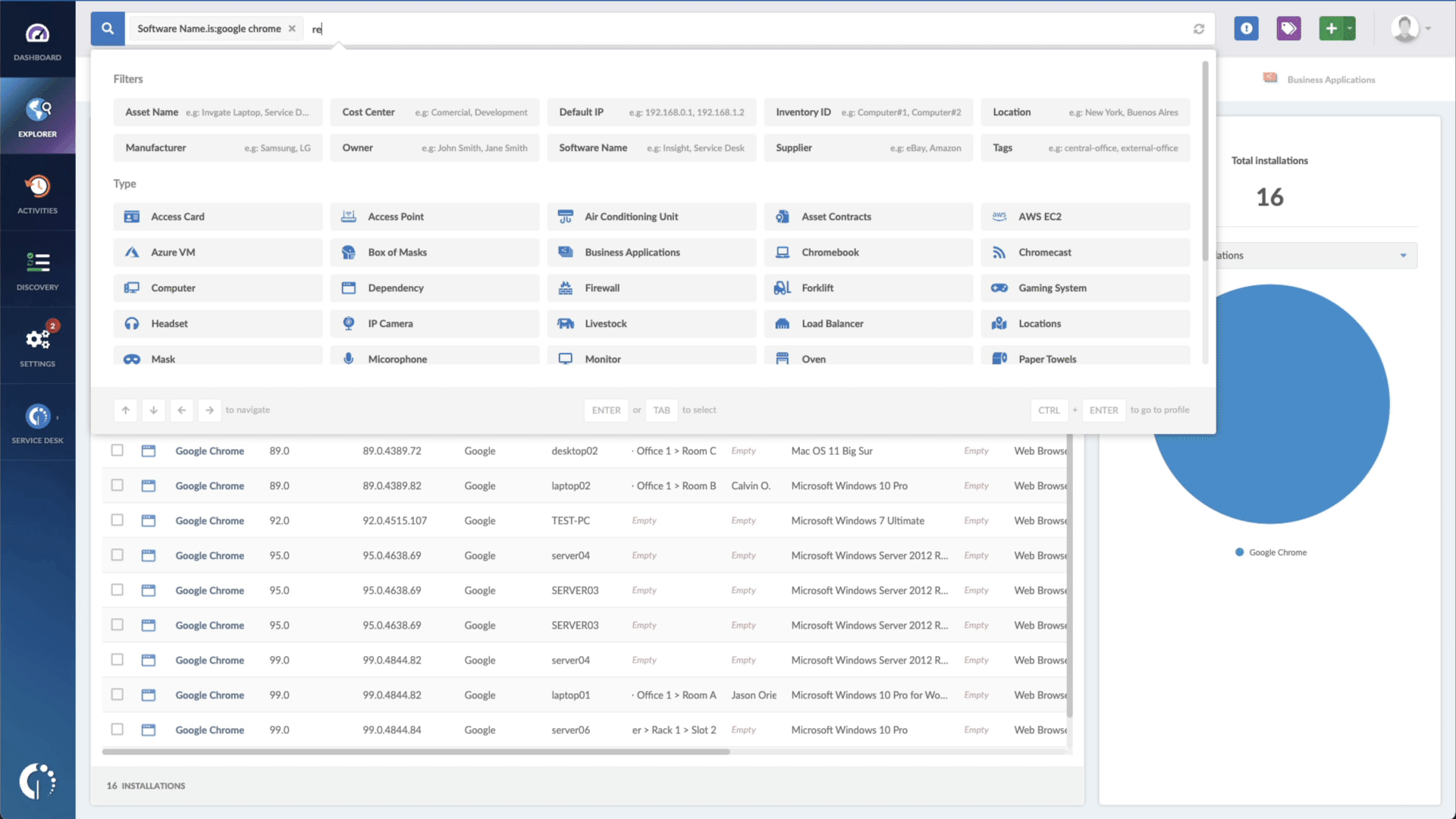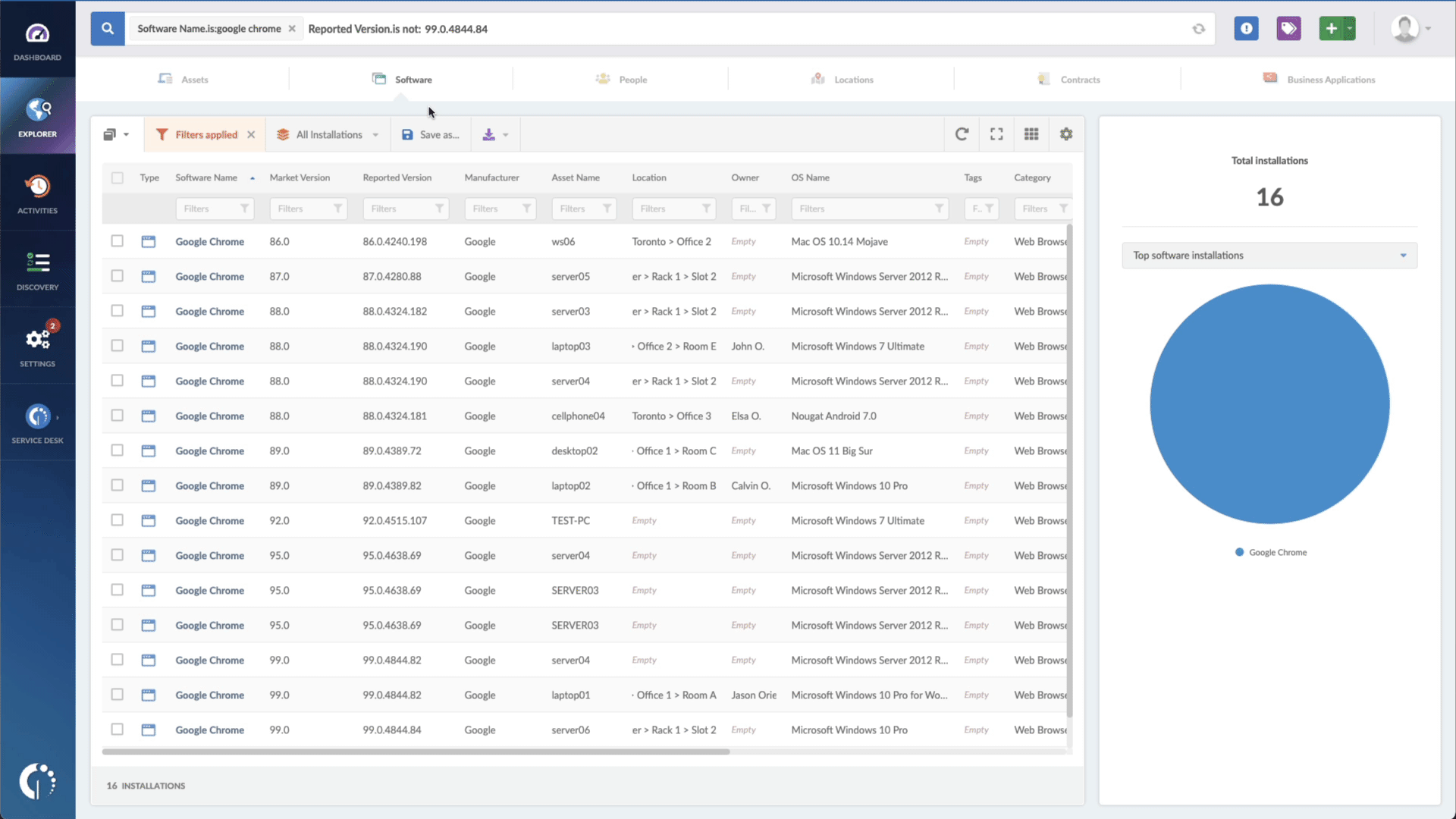
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste the patched version (Ubuntu 22.04.2 LTS).
The bottom line
CVE-2022-29799 poses a significant security threat to Linux systems, allowing attackers to execute unauthorized commands and potentially compromise sensitive data.
To safeguard your infrastructure, it is crucial to update your systems to the latest software version promptly.
InvGate Asset Management simplifies the process of vulnerability detection, enabling you to identify devices at risk and take appropriate action quickly. Request a 30-day free trial today and ensure the security of your network.
















