Discovering and promptly addressing software vulnerabilities is crucial for maintaining the security of your systems. One such critical vulnerability that requires immediate attention is CVE-2022-24521, a Common Log File System (CLFS) driver elevation of privilege vulnerability.
To safeguard your organization's infrastructure, it is essential to understand the nature of this vulnerability, its potential impact, and the steps needed to mitigate the risks effectively.
In this article, we’ll provide comprehensive information about the CVE-2022-24521 vulnerability, including how it works, its potential risks, and how InvGate Asset Management can help simplify Patch Management.
Don't leave your organization's systems exposed to the risks posed by the CVE-2022-24521 vulnerability. Stay informed and take proactive measures to safeguard your infrastructure. Continue reading to learn more!
About CVE-2022-24521
CVE-2022-24521 is a Windows Common Log File System (CLFS) driver elevation of privilege vulnerability. It allows attackers to elevate their privileges to SYSTEM on a vulnerable system.
The vulnerability is caused by a logical error in the CLFS driver. When the driver is processing a log block, it does not properly validate the size of the block. This can allow an attacker to craft a malicious log block that is larger than the driver expects. When the driver attempts to process this malicious block, it will overwrite memory that it is not supposed to, which can lead to an elevation of privilege.
CVE-2022-24521 affects the following Windows versions:
- Windows 7 SP1
- Windows Server 2008 R2 SP1
- Windows 8.1
- Windows Server 2012 R2
- Windows 10 (all versions)
- Windows Server 2016
- Windows Server 2019
- Windows 11
- Windows Server 2022
If you do not patch CVE-2022-24521, an attacker could gain complete control over your system, including the ability to read, write, and delete files, install programs, and modify system settings.
How does CVE-2022-24521 work?
The exploit for this vulnerability is relatively simple. An attacker can create a malicious log file that contains a crafted log block. When the victim opens the malicious file, the driver will be tricked into overwriting memory that it is not supposed to, leading to an elevation of privilege.
Is CVE-2022-24521 fixed?
Yes, Microsoft has released a patch for this vulnerability. To apply the patch, users should install the latest updates for their Windows operating system.
How to find devices exposed to CVE-2022-24521
To quickly detect devices that may be impacted by the CVE-2022-24521 vulnerability, InvGate Asset Management offers a convenient solution. Follow the steps below to identify affected devices efficiently:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:Windows” to filter all Microsoft Windows devices.
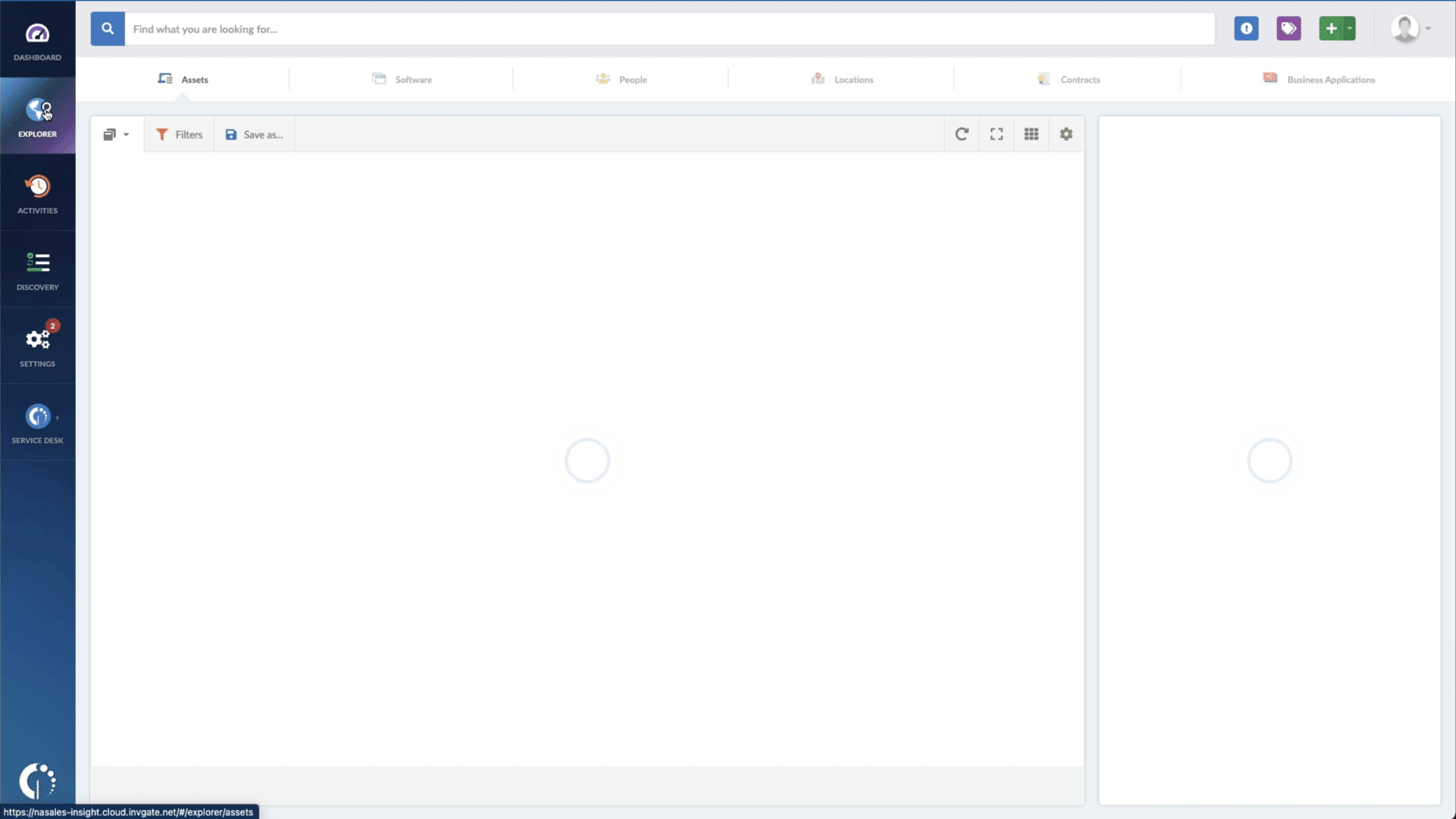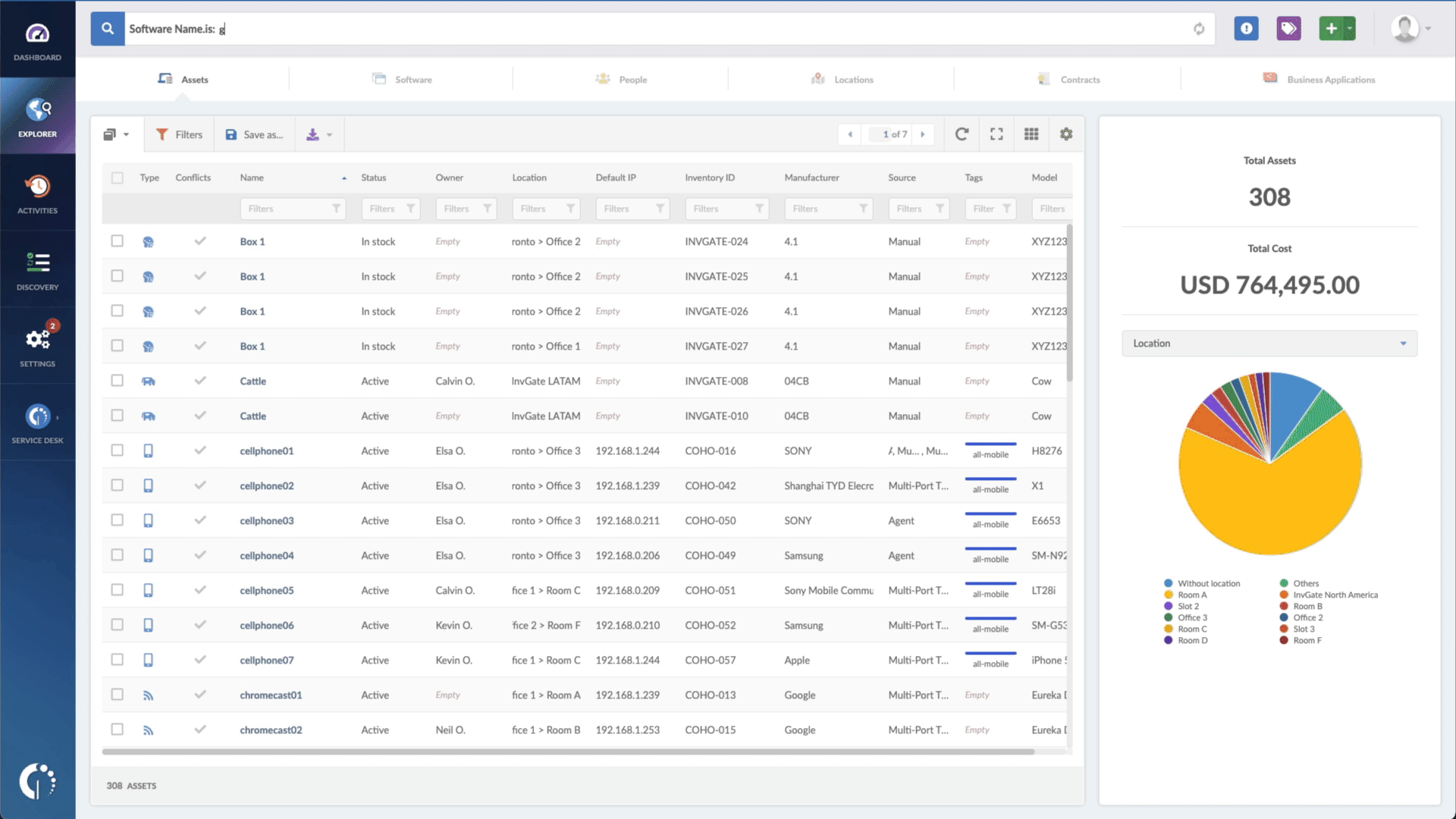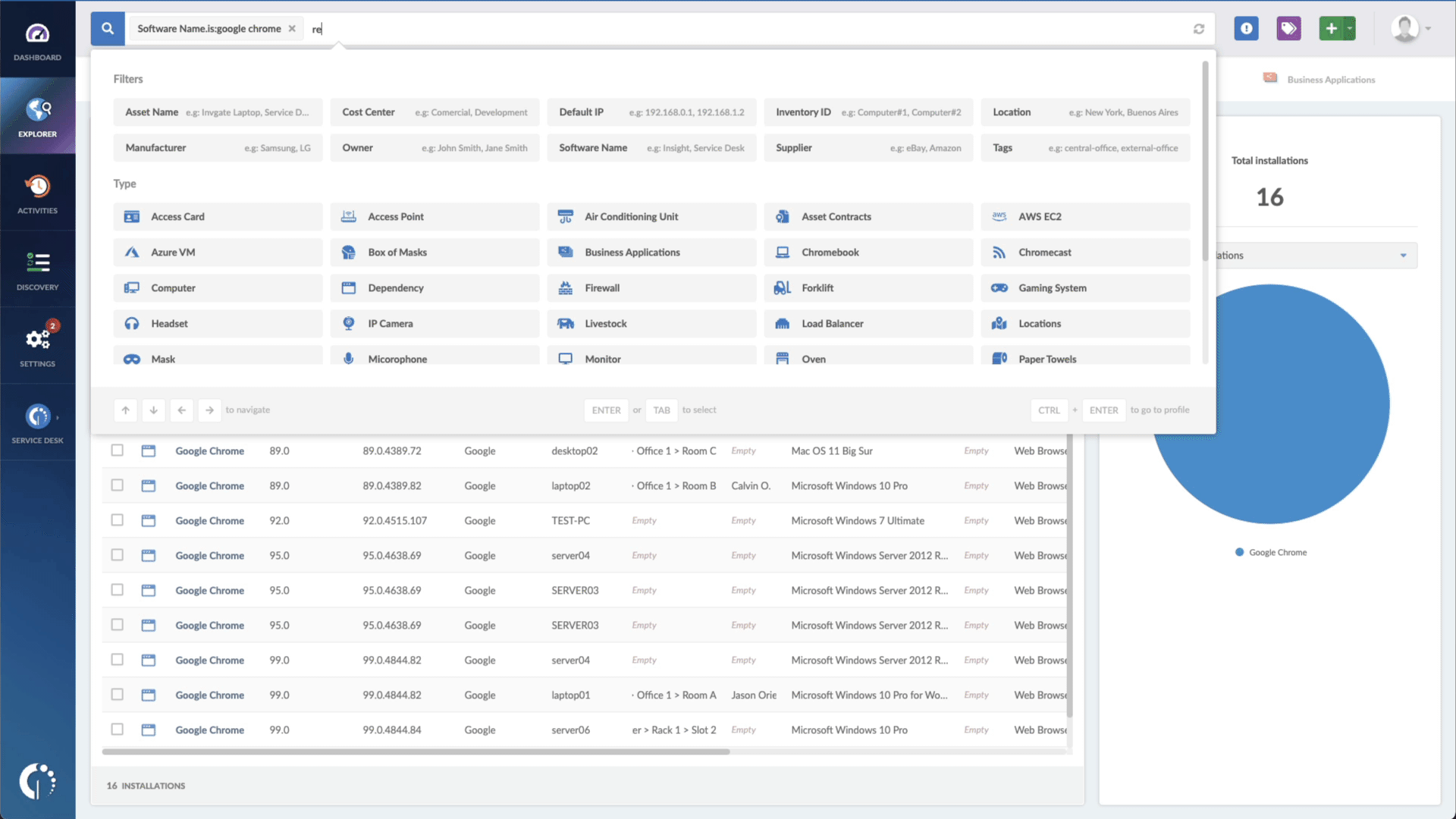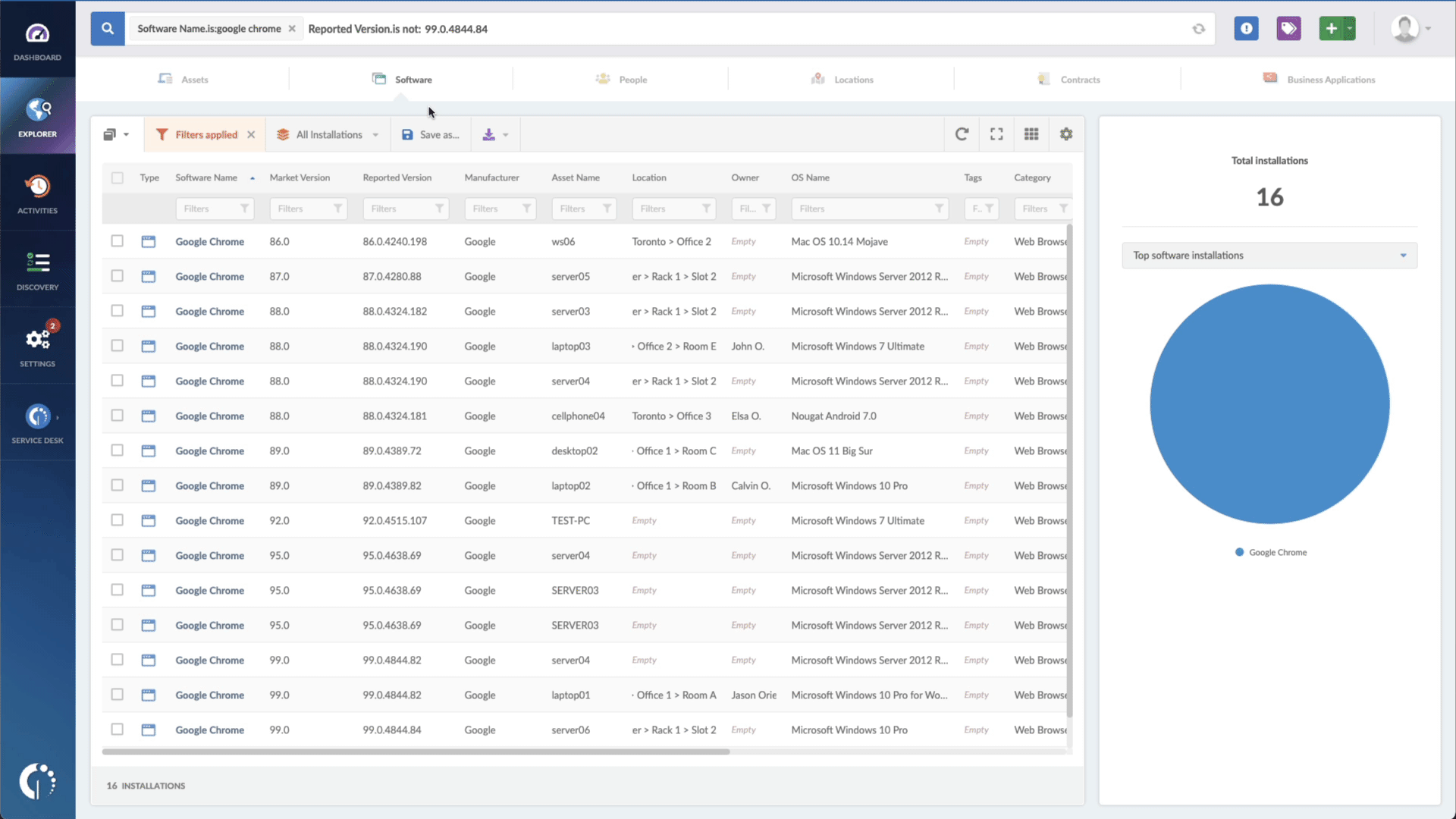
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Microsoft’s patched version (depending on your product, you’ll find the security update number on Microsoft’s webpage. For example, for Windows 8.1 for 32-bit systems, it's KB5012670).
The bottom line
The CVE-2022-24521 vulnerability in the Windows Common Log File System driver poses a significant risk to the security of systems running unpatched versions of Windows. However, by promptly applying the necessary security updates, users can mitigate these risks and ensure the integrity of their systems.
To simplify the Patch Management process and effectively address vulnerabilities like CVE-2022-24521, InvGate Asset Management provides a powerful solution. With InvGate Asset Management, you can swiftly identify devices that may be affected by the vulnerability and take appropriate action.
Take advantage of InvGate Asset Management's capabilities today by requesting a 30-day free trial. Discover how it simplifies patch management and enhances the security of your network. Don't leave your systems exposed to risks—leverage InvGate Asset Management to protect your organization's infrastructure proactively.