VMware unveiled a critical remote code execution vulnerability, CVE-2022-22954, that impacts VMware Workspace ONE Access and Identity Manager.
Exploiting this vulnerability could allow attackers to gain complete control over systems, leading to data theft, malware installation, and operational disruption. Organizations must apply the patches promptly to protect their devices.
In this article, we’ll provide comprehensive insights into the CVE-2022-22954 vulnerability, its associated risks, and the measures available to safeguard vulnerable systems, including the use of InvGate Asset Management to simplify Patch Management.
Read on to learn how to protect your organization from potential threats.
About CVE-2022-22954
CVE-2022-22954 is a server-side template injection vulnerability in VMware Workspace ONE Access and Identity Manager that can be triggered by a malicious actor with network access to achieve remote code execution (RCE).
The vulnerability, that has been exploited in the wild, has a CVSSv3 base score of 9.8, which is considered to be critical.
CVE-2022-22954 can be exploited by sending a specially crafted HTTP GET request to a vulnerable server resulting in RCE on the server.
What are CVE-2022-22954 risks?
An attacker who successfully exploits the vulnerability could take complete control of a vulnerable system, allowing them to steal data, install malware, or disrupt operations.
Is CVE-2022-22954 fixed?
Yes, VMware has released patches for CVE-2022-22954. Organizations that use VMware Workspace ONE Access or Identity Manager should apply them as soon as possible to protect their systems from attack.
How to find devices exposed to CVE-2022-22954
With InvGate Asset Management you can quickly find devices that are exposed to the CVE-2022-22954 vulnerability. Here are the instructions to proceed with:
- Open InvGate Asset Management and go to the Explorer tab.
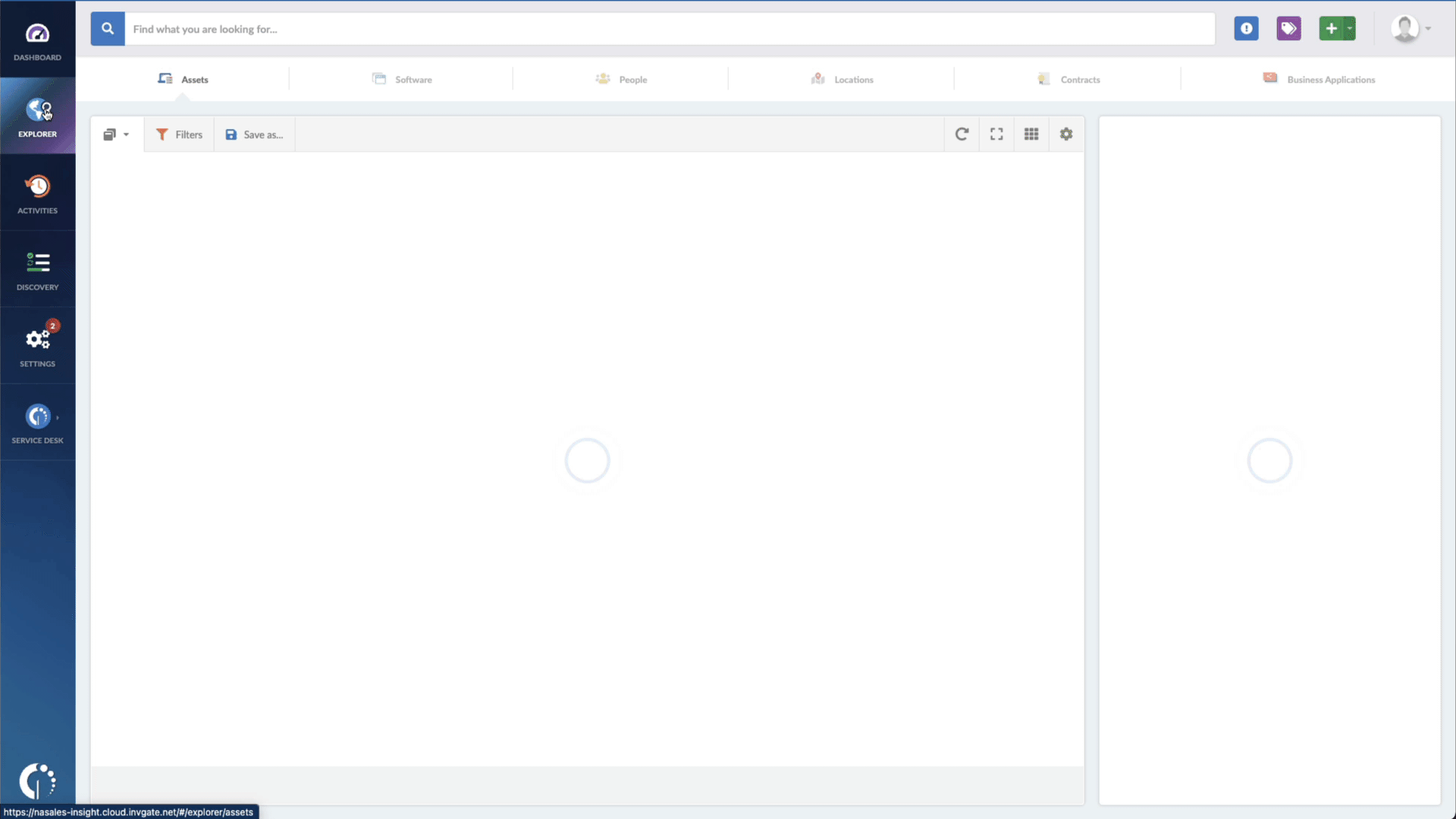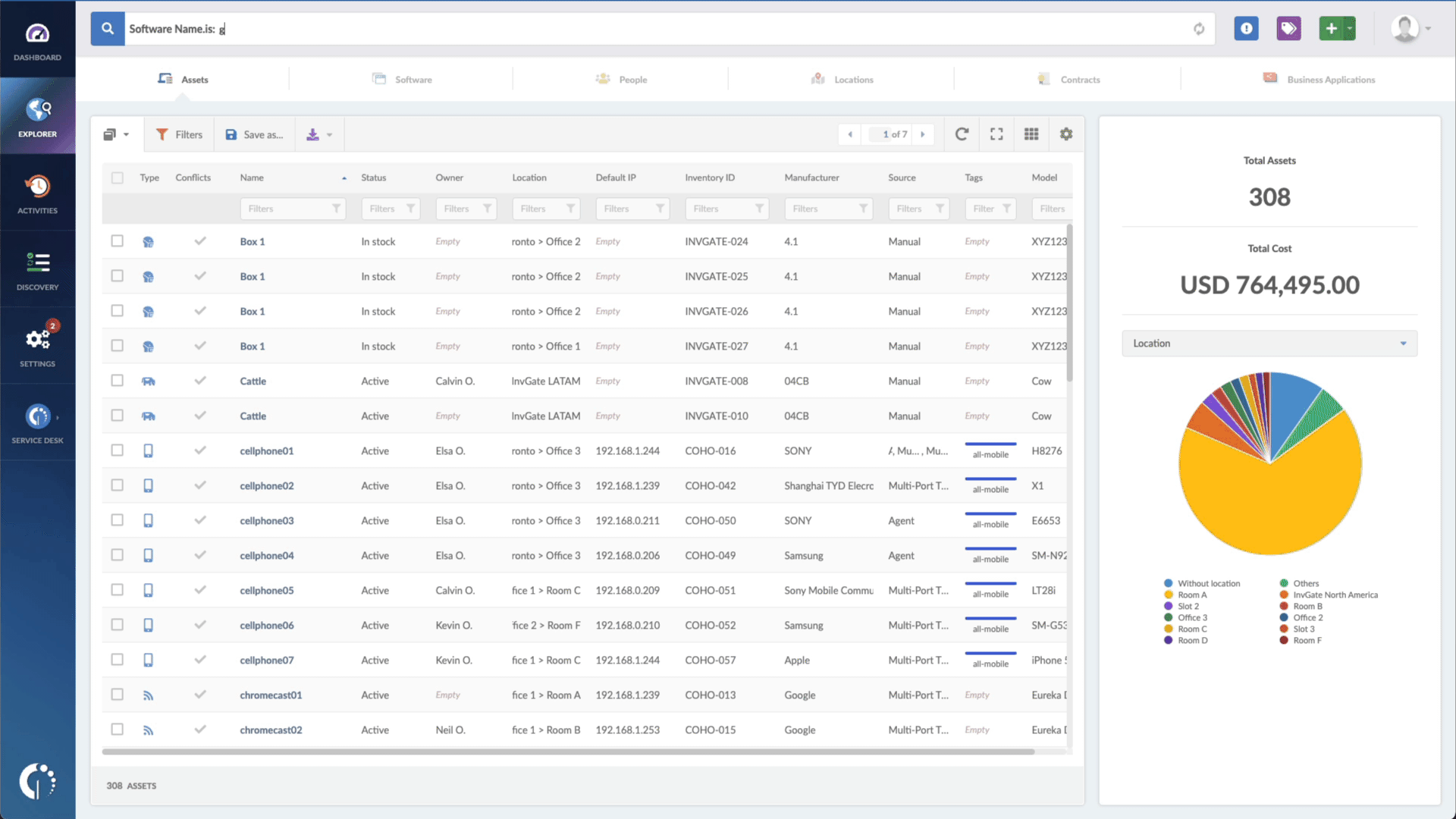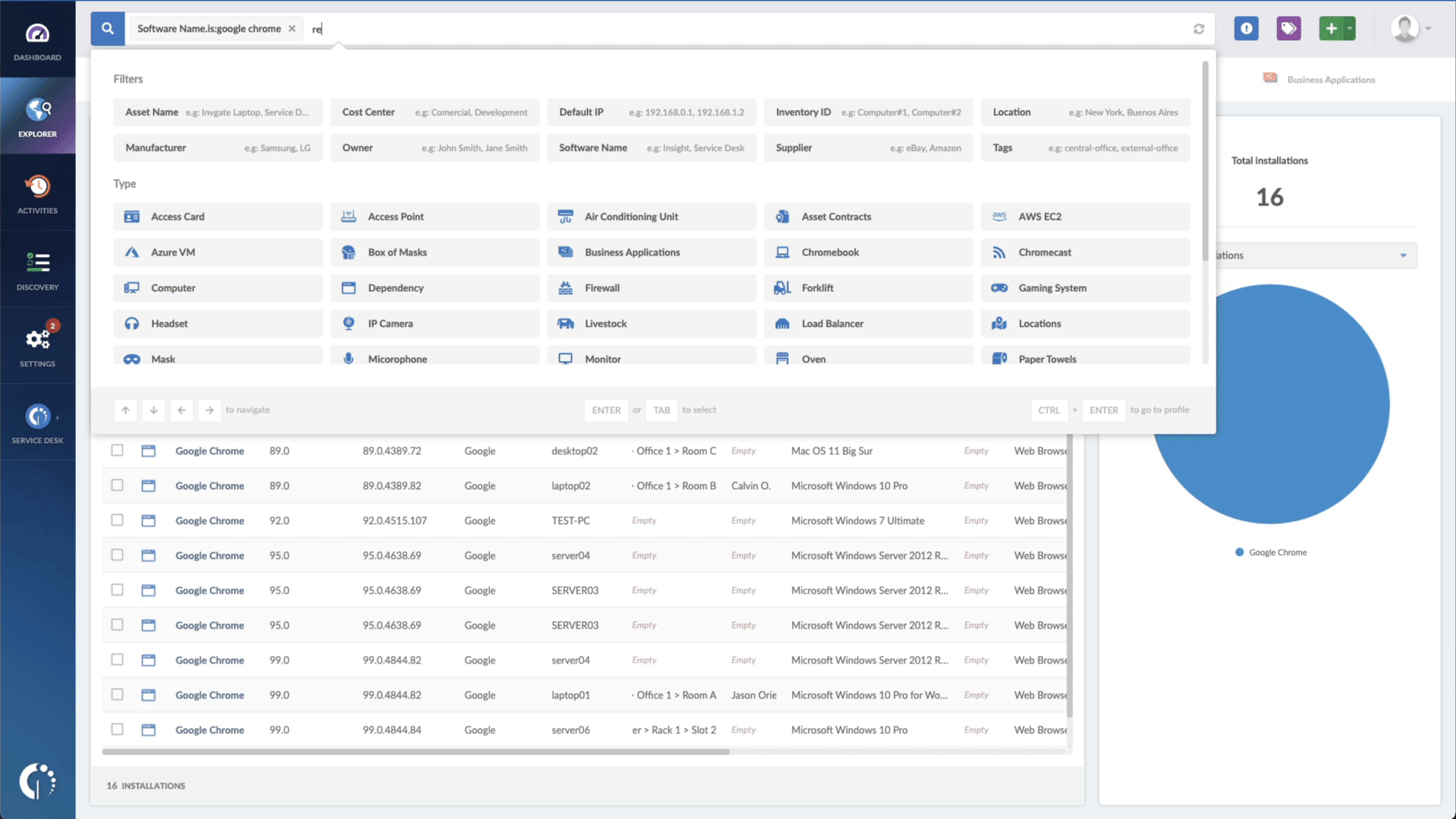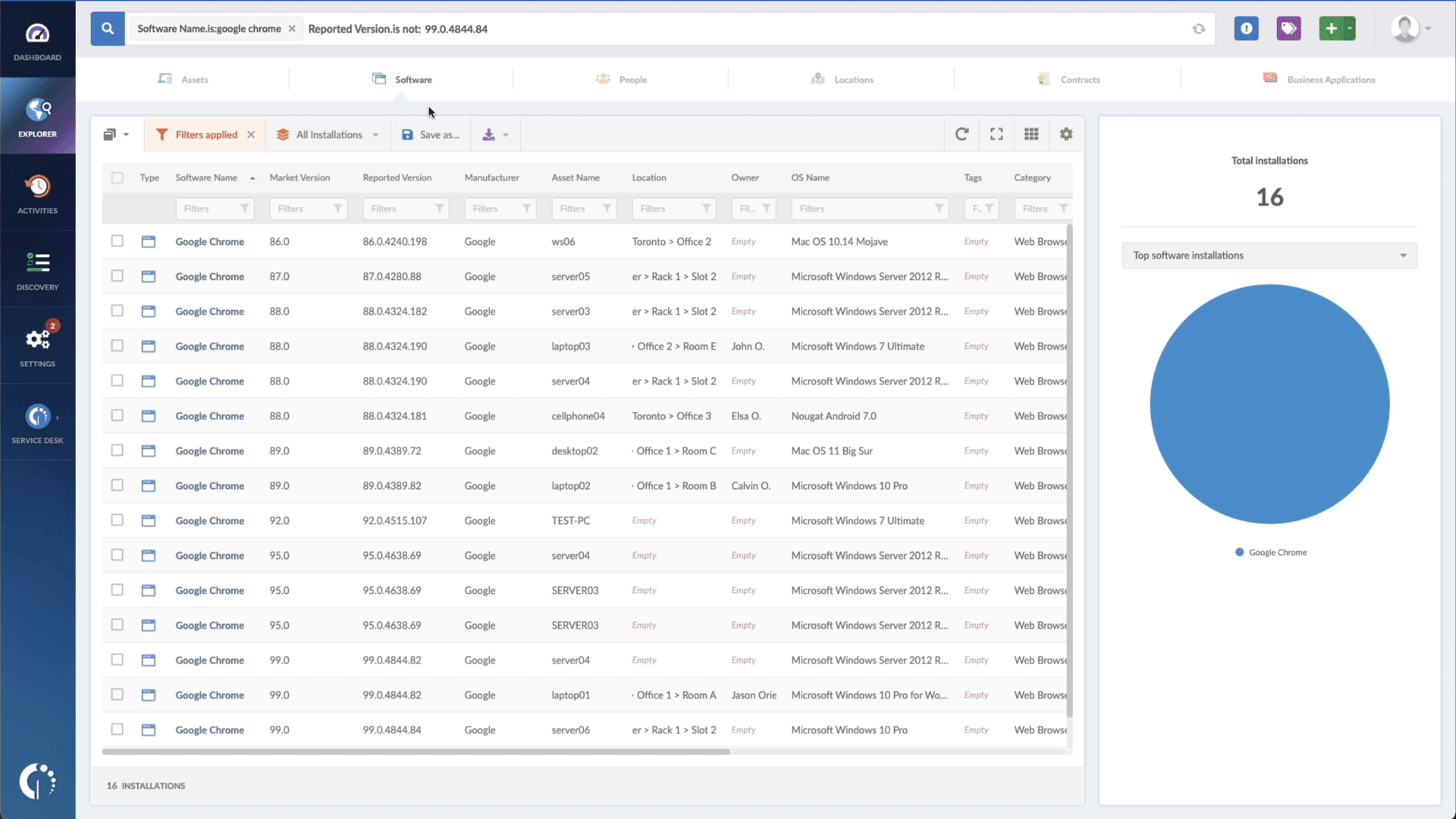
- Type in the Search bar “Software name, is:VMware Workspace ONE Access” or “Software name, is:VMware Identity Manager” to filter all devices with these software programs.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste VMware’s patched version (depending on your product, you’ll find the security update number on VMware’s webpage).
The bottom line
CVE-2022-22954 is a critical remote code execution vulnerability found in VMware Workspace ONE Access and Identity Manager. Exploiting this vulnerability could allow attackers to gain complete control over systems, leading to data theft, malware installation, and operational disruption.
VMware has released patches to address this issue, and organizations are urged to apply them promptly for protection.
InvGate Asset Management offers a solution to identify devices exposed to CVE-2022-22954 easily, simplifying the patch management process. To experience its capabilities, request a 30-day free trial today and begin searching for vulnerable devices within their network.
















