As technology continues to advance, ensuring the security of our devices becomes increasingly crucial. A critical vulnerability, known as CVE-2022-22620, has been identified in both iOS and macOS, posing a significant risk to Apple device users.
In this article, we’ll provide a comprehensive overview of the CVE-2022-22620 vulnerability, including how it works, its risks, and how InvGate Asset Management can simplify the process of identifying and patching devices affected by CVE-2022-22620.
Read on to discover how to safeguard your devices against the CVE-2022-22620 vulnerability and ensure a robust defense against potential cyber threats.
About CVE-2022-22620
CVE-2022-22620 is a use-after-free vulnerability in the History API in Safari. This vulnerability allows an attacker to execute arbitrary code on a victim's system by crafting a malicious web page.
How does CVE-2022-22620 work?
The vulnerability is caused by a flaw in the way that the History API handles memory. An attacker can exploit this vulnerability by creating a malicious web page that contains a specially crafted History object. When the victim opens the malicious web page, the History API will be vulnerable to arbitrary code execution.
What are CVE-2022-22620 risks?
An attacker who successfully exploits this vulnerability could execute arbitrary code on the victim's system, allowing it to steal data, install malware, or take control of the victim's system.
Is CVE-2022-22620 fixed?
Yes, Apple has released a security update that addresses CVE-2022-22620, available for all supported versions of Safari. Users are urged to apply this security update as soon as possible.
The following are the security updates that address CVE-2022-22620:
- macOS Monterey 12.2.1
- iOS 15.3.1
- iPadOS 15.3.1
- Safari 15.3
How to find devices exposed to CVE-2022-22620
To quickly detect devices that are impacted by the CVE-2022-22620 vulnerability, InvGate Asset Management comes in handy. Follow these instructions:
- Open InvGate Asset Management and go to the Explorer tab.
- Type in the Search bar “Software name, is:iOS” or “Software name, is:imacOS” to filter all Apple devices.
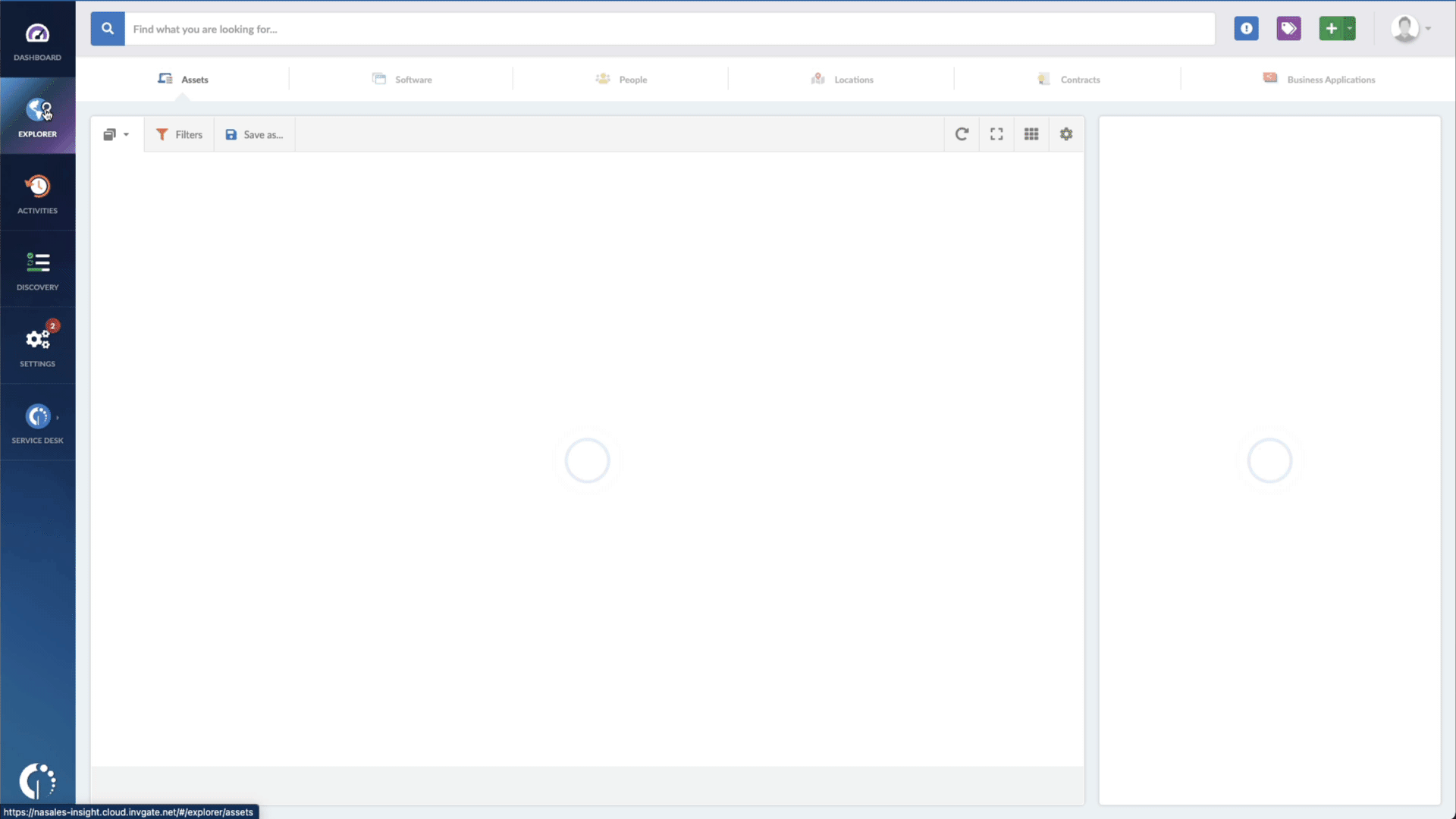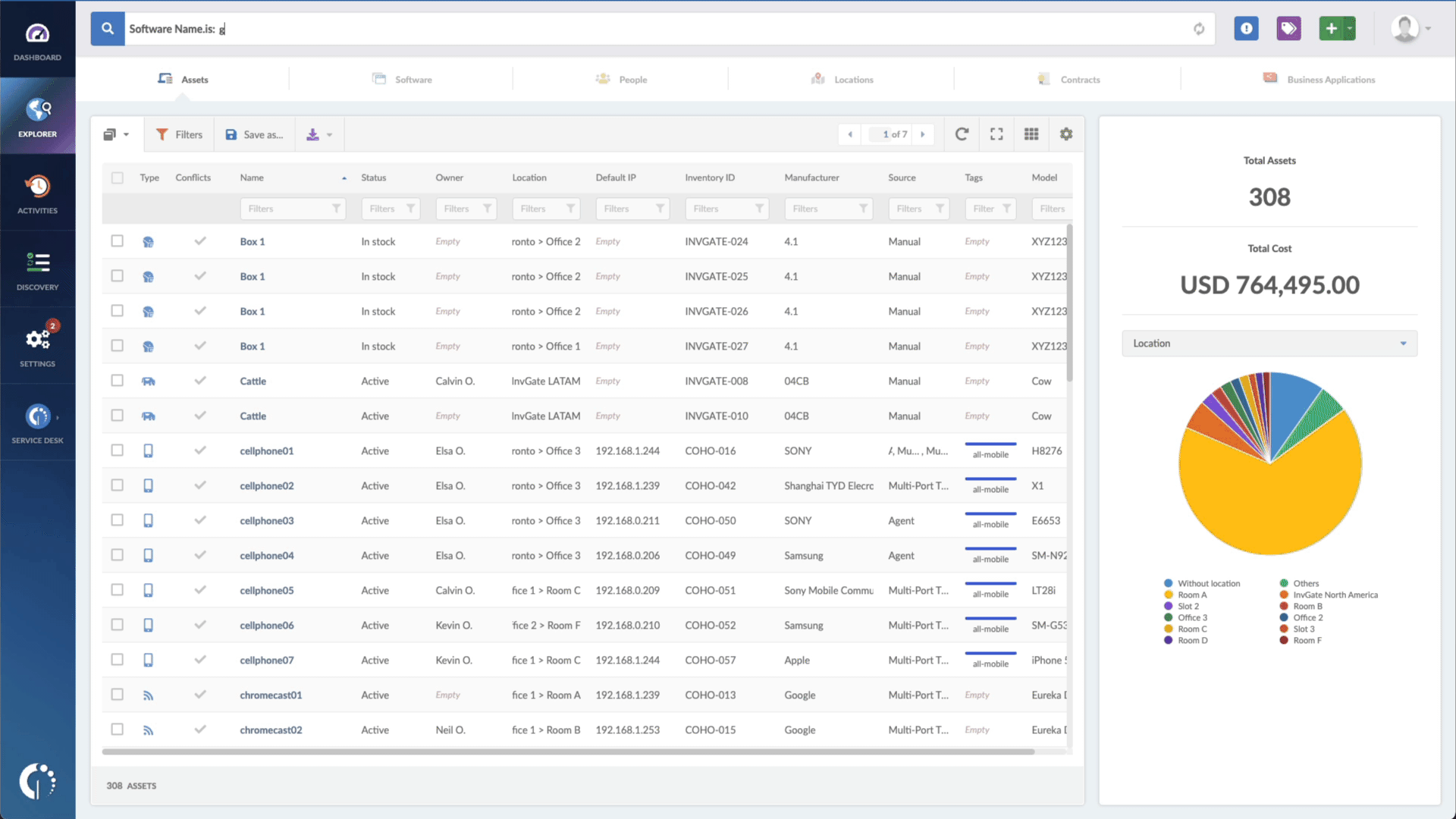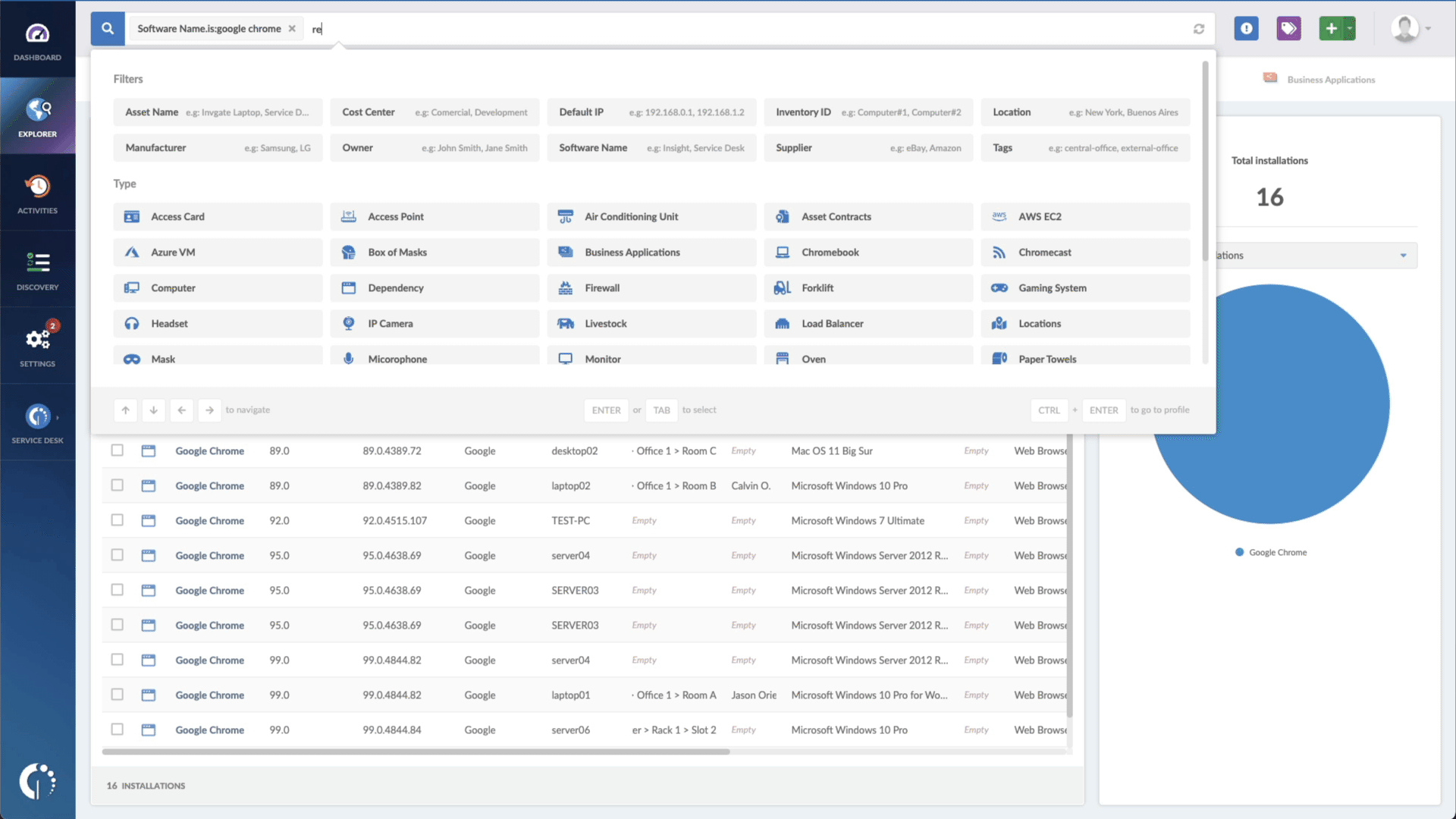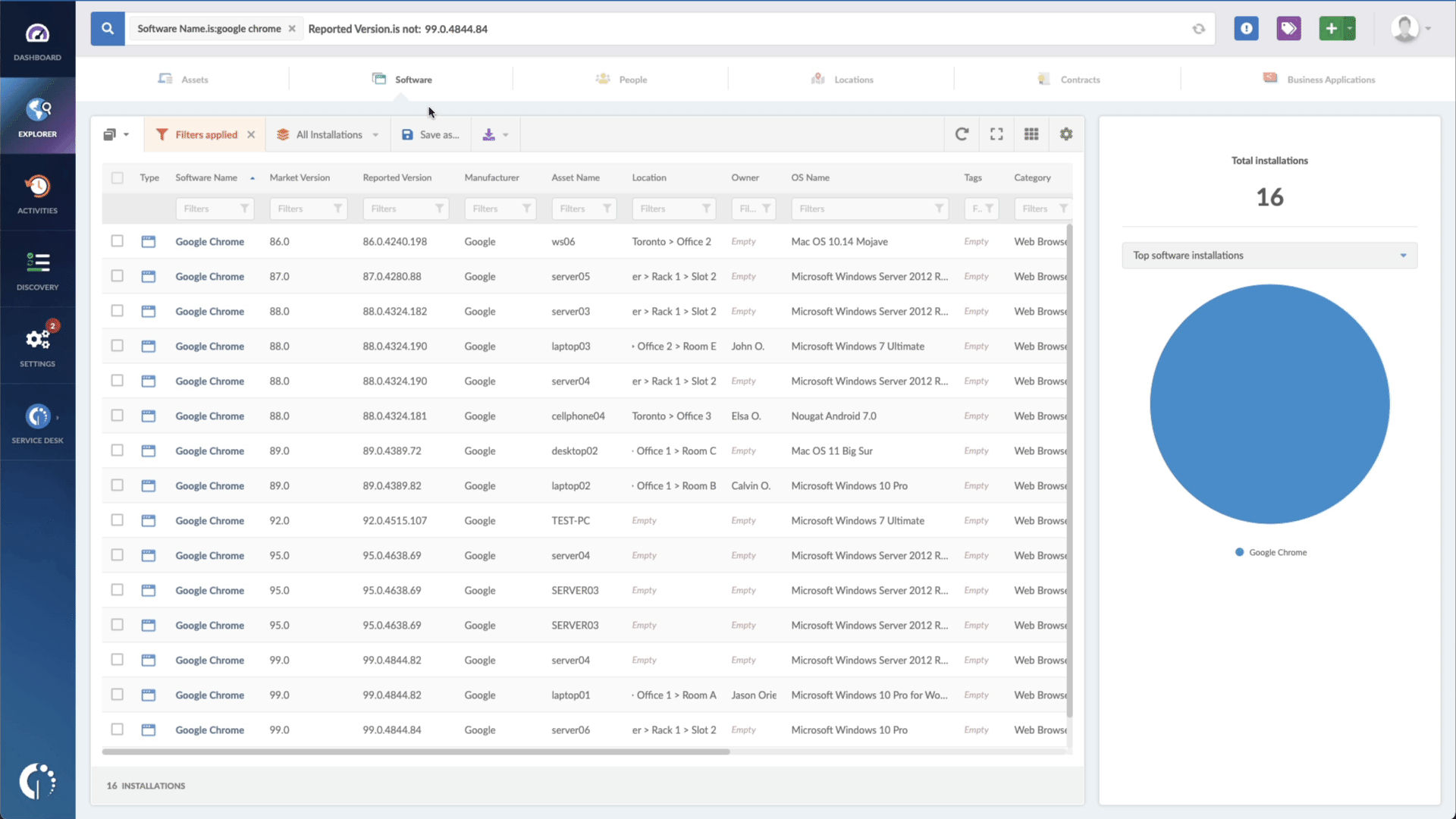
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Apple’s patched version (mentioned above).
The bottom line
In conclusion, the discovery of the CVE-2022-22620 vulnerability in iOS and macOS has raised significant concerns regarding the security of Apple devices. Failing to patch this vulnerability exposes users to various risks, including unauthorized access to personal data, installation of malware, and potential control of the compromised device.
To safeguard against this critical vulnerability, it is crucial for users to update their devices to the latest software versions. To simplify the Patch Management process and identify devices affected by CVE-2022-22620 with ease, InvGate Asset Management offers a powerful solution. With InvGate Asset Management, you can swiftly scan your network and identify devices that are vulnerable to this exploit.
Don't wait until it's too late. Take proactive steps to protect your Apple devices from the risks posed by CVE-2022-22620 and other vulnerabilities. Request a 30-day free trial of InvGate Asset Management today and gain comprehensive visibility into your network's security posture.