The CVE-2022-20968 vulnerability is a critical security threat that could compromise the data of the Cisco IP Phones 7800 and 8800 Series, making them a prime target for cybercriminals looking for vulnerabilities to exploit.
Cisco has since released a patch for this vulnerability, which should be applied as soon as possible to mitigate the risk of a successful attack. However, identifying all the vulnerable devices in a network can be a daunting task for IT professionals. That's where InvGate Asset Management comes in - it simplifies Patch Management by quickly identifying devices affected by CVE-2022-20968 and prioritizing the patching process.
In this blog post, we’ll provide an overview of the CVE-2022-20968 vulnerability, including its risks, the updated software version to mitigate it, and how InvGate Asset Management can simplify the patch management process.
Ready to learn more about this critical vulnerability and how to protect your organization's devices? Read on to find out more!
About CVE-2022-20968
A vulnerability known as CVE-2022-20968 was identified within the Cisco Discovery Protocol processing feature of Cisco IP Phone 7800 and 8800 Series firmware. It could allow an unauthenticated, adjacent attacker to cause a stack overflow on the affected device.
Cisco IP Phones are widely used in business environments and offer a range of features including high-quality voice and video communication, messaging, and conferencing capabilities.
This vulnerability is due to insufficient input validation of received Cisco Discovery Protocol packets. An attacker could exploit this vulnerability by sending crafted Cisco Discovery Protocol traffic to an affected device. A successful exploit could allow the attacker to cause a stack overflow, resulting in possible remote code execution or a denial of service (DoS) condition on the affected device.
CVE-2022-20968 affects the following Cisco products:
- IP Phone 7800 Series
- IP Phone 8800 Series (except Cisco Wireless IP Phone 8821)
Cisco has released a patch to address this vulnerability. It is fixed in the firmware v14.2(1). Users are strongly advised to apply the update as soon as possible to reduce the risk of exploitation. In addition, users are encouraged to review their security policies and network configurations to ensure they are well protected against potential threats.
How to find devices exposed to CVE-2022-20968
InvGate Asset Management allows for quickly identifying devices that may be affected by the CVE-2022-20968 vulnerability. The following are the recommended steps to take:
- Open InvGate Asset Management and go to the Explorer tab.
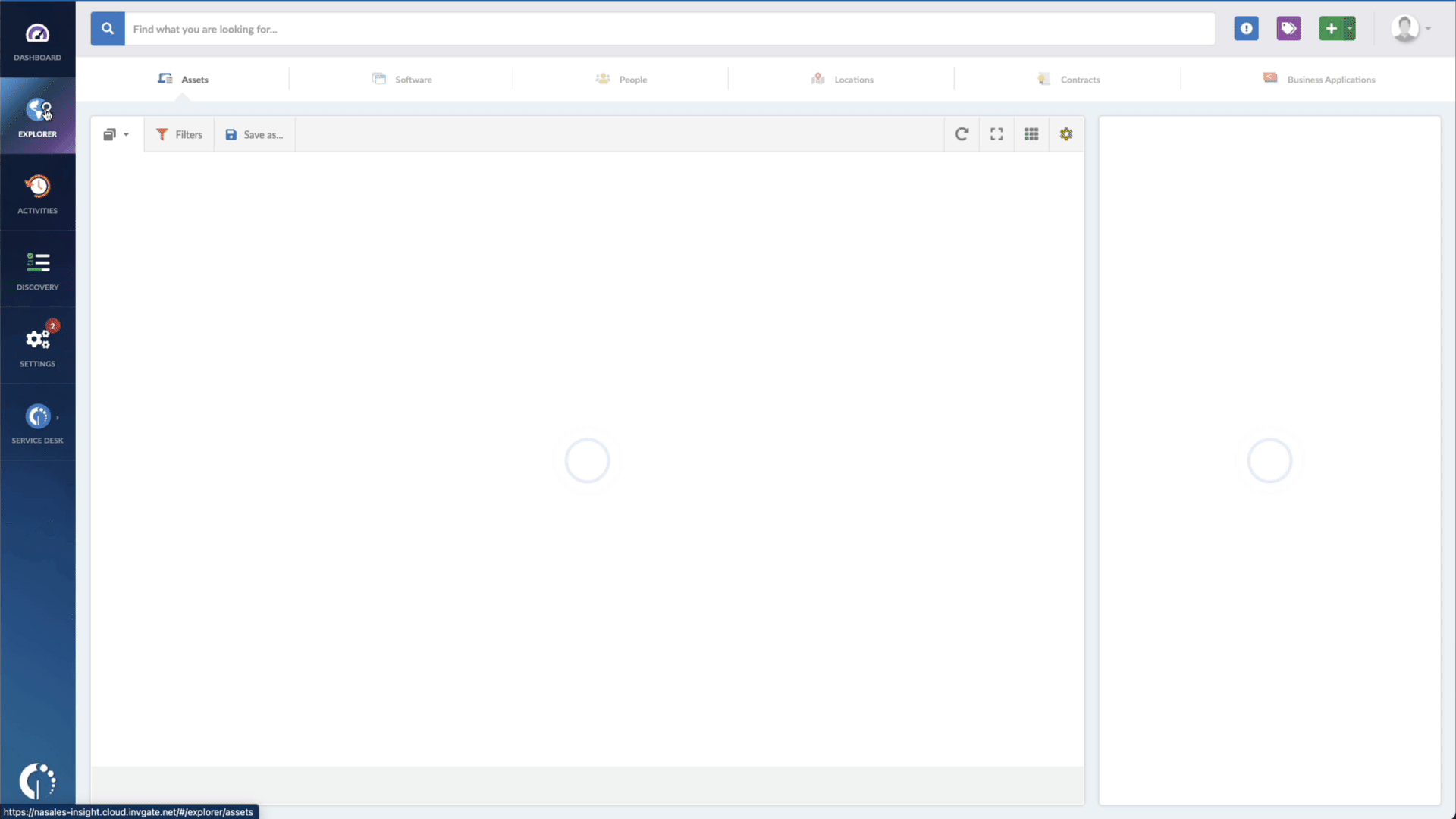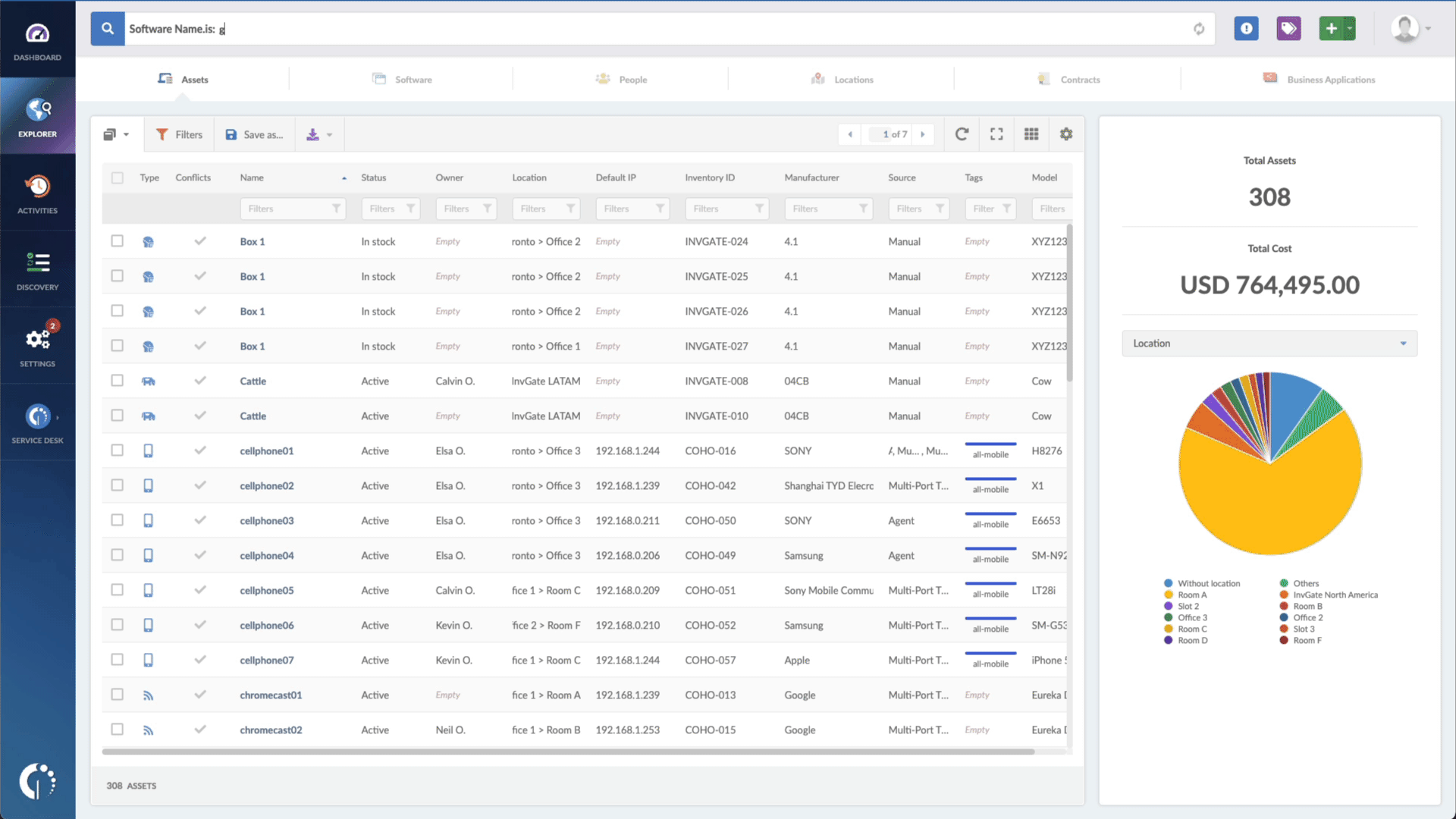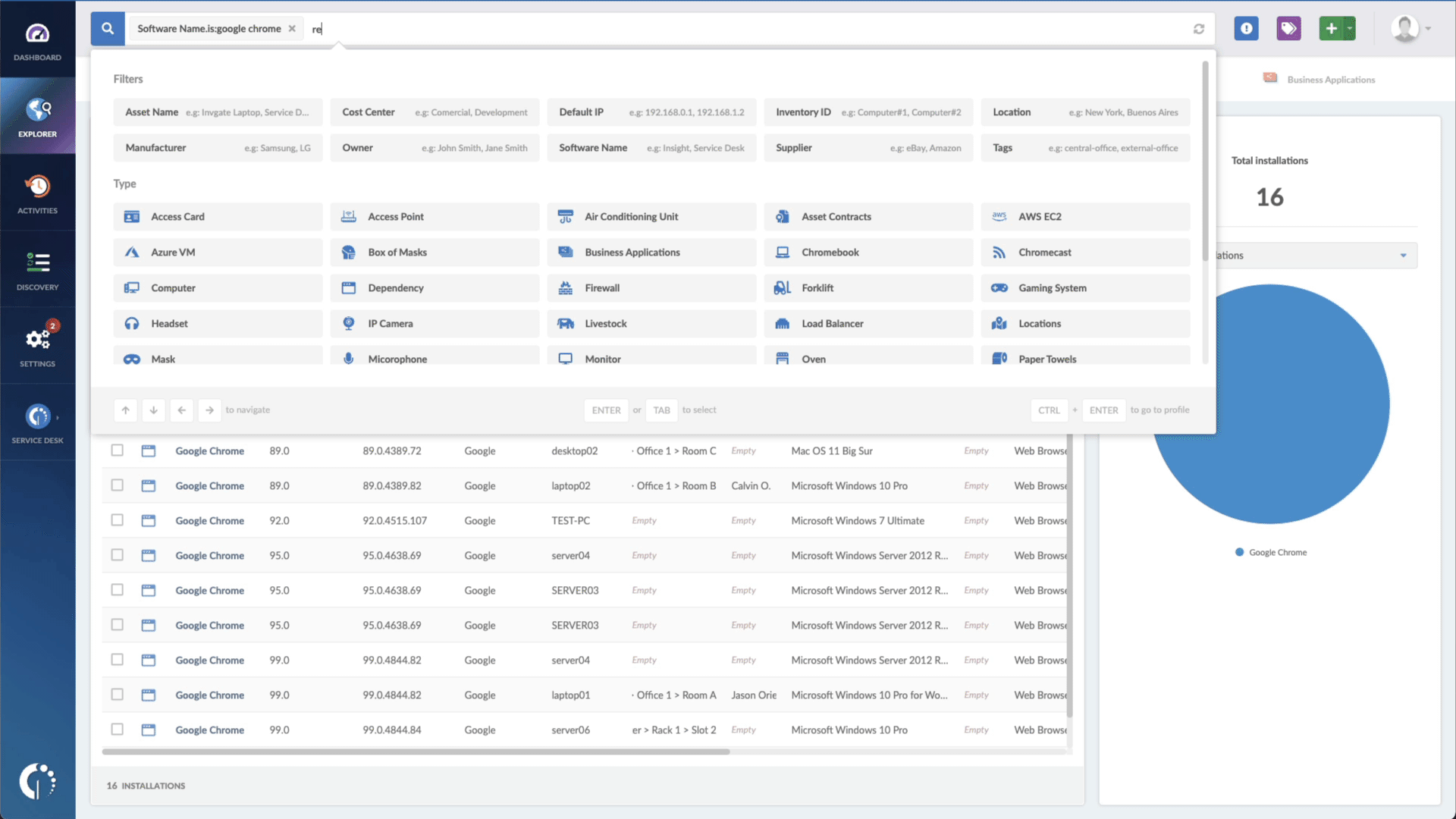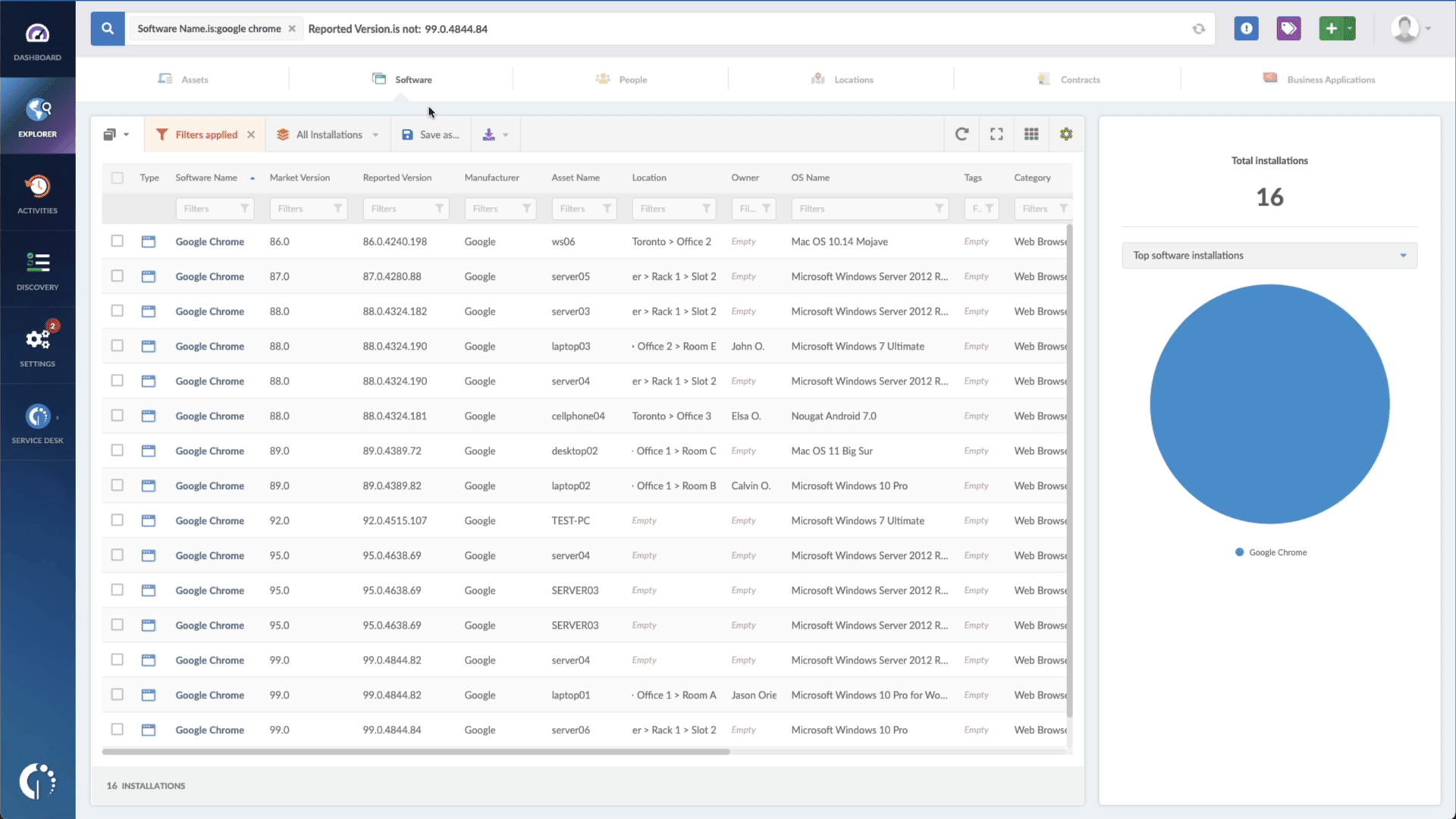
- Type in the Search bar “Software name, is:7800 Series” or “Software name, is:8800 Series” to filter all IP Phones devices.
- Add another filter to the Search bar to see all devices missing the security patch. To do that, add the following filter: “Reported version, is not:” and paste Cisco’s patched version (14.2(1)).
The bottom line
The CVE-2022-20968 vulnerability in Cisco IP Phones poses a severe security risk to businesses that use these devices for communication. Successful exploitation of this vulnerability could lead to remote code execution or a denial of service (DoS) condition on the affected device.
Fortunately, Cisco has released a patch to address this vulnerability, which should be applied immediately to protect against potential attacks. The updated software version is 14.2(1).
To simplify Patch Management and speed up the process of identifying vulnerable devices, you can leverage the capabilities of InvGate Asset Management. With InvGate Asset Management, you can quickly identify devices affected by the CVE-2022-20968 vulnerability and prioritize patching accordingly, reducing the risk of a successful attack.
If you're interested in trying InvGate Asset Management, request a 30-day free trial today and search for the devices in your network that might be affected by this vulnerability. Don't wait for a cyberattack to happen – take proactive measures to secure your devices and protect your business.